Free online file converters have been around for decades, with users around the world using them to convert images, edit PDFs, and download videos.
Naturally, uploading and downloading files on these sites has always been dangerous. However, the FBI has now issued a new warning saying that threat actors are increasingly using these tools to spread malware.
FBI Denver sounds the file conversion alarm
Recently, the FBI Denver Field Office issued a warning on the use of free file-converting tools. The FBI said that criminals are using free online document converter tools and websites to load malware onto victims’ computers, leading to identity theft and even ransomware attacks.
Speaking to local news media, Denver7, Assistant Special Agent at the FBI’s Denver field office, Marvin Massey, said that this scam is now “rampant” across the United States.
Massey spoke about why this threat has come to the FBI’s attention now despite file conversion site scams being around for years.
“This is a scam we’re seeing across the country, and it’s becoming rampant,” said Massey. “Within Colorado, we had an incident here as recently as 2 weeks ago within the Denver metro area.”
Signs that your device — or even your business — could have been infected by malware from these sites include antivirus and anti-malware warnings, your browser flagging content, or devices acting up suspiciously.
Another sign of a breach is the inability to access banking accounts or other online accounts, Agent Massey explained. Also, be on the lookout for modified passwords or configuration changes.
This is how the convert-your-file-for-free scam works
According to the FBI, file conversion schemes work by impersonating fully functional, free conversion services via websites or apps. While the conversion tool will do the work — effectively converting the file you want to convert — it will also bundle or integrate malicious code or malware into the final converted file.
You might successfully convert a .doc file to a .pdf, join several videos together, or convert an image, but what you get in return may contain malware. This could be anything from spyware to trackers to information stealers or even ransomware.
Given that file conversions are heavily used in business environments, this threat has the potential to spread across an organization rapidly.
Moonlock checked some of the websites associated with this threat and found that visiting the sites alone, even without uploading or downloading anything, can be a risk. These sites contain common but harmful fishy code (more on that in the sections below).
What can the malware do?
As mentioned, using one of these malicious file-converting tools has risks. Cybercriminals could integrate malware into the download and use it to:
- Steal personal identifying information (social security numbers, dates of birth, phone numbers, etc.)
- Compromise your banking information
- Drain your e-wallets and steal your cryptocurrency information (seed phrases, wallet addresses, tokens, etc.)
- Steal other personal information, including email addresses
- Deploy a browser stealer and exfiltrate data stored in your browser, including auto-complete data, passwords, financial data, and your online history, cookies, and data
- Install a backdoor to load malware
- Distribute malware laterally across networks and contacts
- Load spyware or other malware and launch ransomware
“Unfortunately, many victims don’t realize they have been infected by malware until it’s too late, and their computer is infected with ransomware or their identity has been stolen,” said the FBI in its press release.
Moonlock found that visiting these sites can also lead to other risks, including redirects to other malicious sites, phishing, espionage, and exposure of your personal data.
Malwarebytes provides IoCs to go with the FBI’s report: Block these sites
While the FBI’s official press release does not include any website address linked to this campaign or scam trend, Malwarebytes released a list of indicators of compromise (IoCs). They described the IoC list as “some recent examples of domains involved in this type of scam.”
IoCs include:
- mageconvertors[.]com (phishing)
- Convertitoremp3[.]it (riskware)
- Convertisseurs-pdf[.]com (riskware)
- Convertscloud[.]com (phishing)
- Convertix-api[.]xyz (trojan)
- Convertallfiles[.]com (adware)
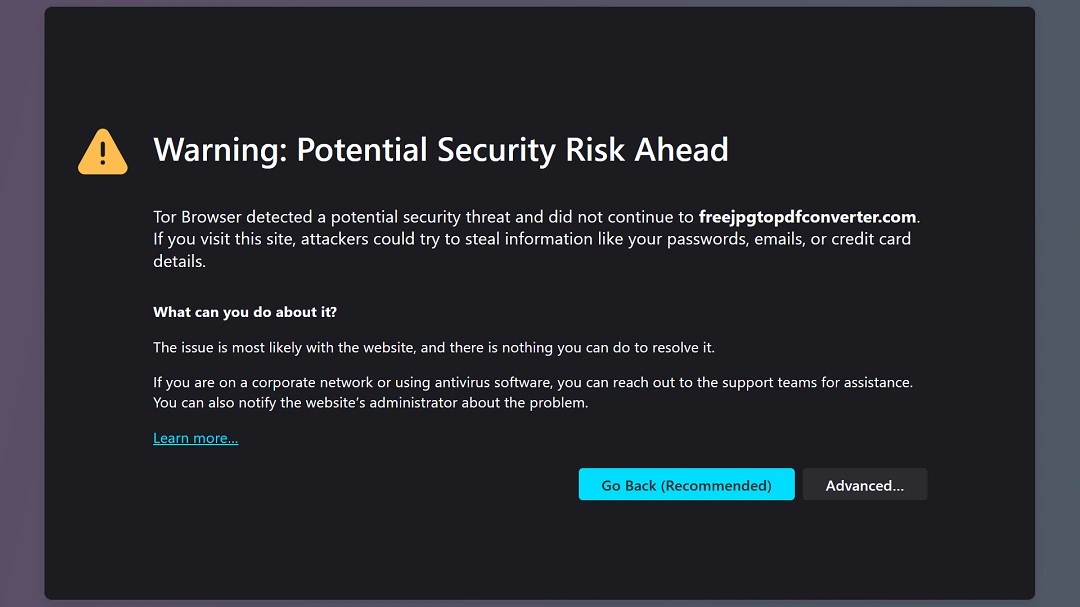
- Freejpgtopdfconverter[.]com (riskware)
- Primeconvertapp[.]com (riskware)
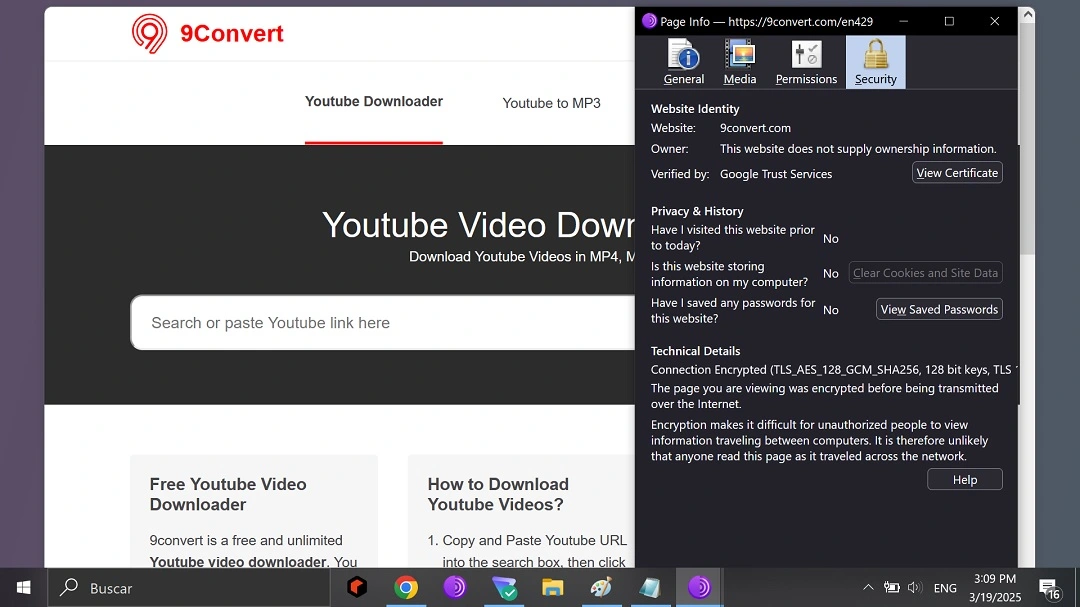
- 9convert[.]com (riskware)
- Convertpro[.]org (riskware)
Some of these sites are long gone and offline. Others have been flagged by security vendors and browsers. However, some are more sophisticated and continue to be live.
Moonlock looked into a couple of these sites. What follows are some of the highlights of what we found.
A closer look at some IoCs and their behaviors
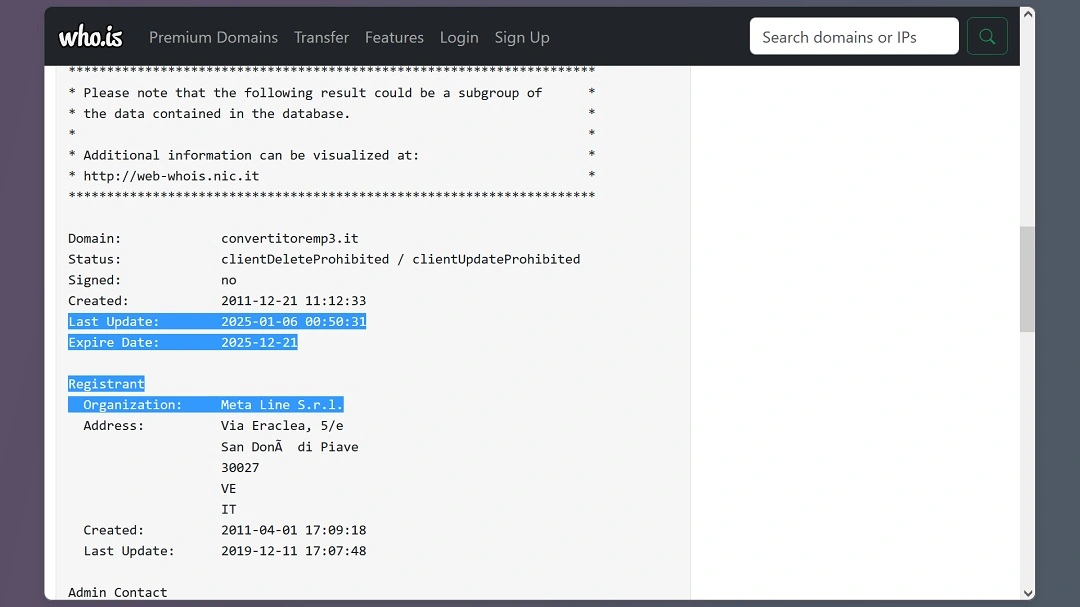
Assistant FBI Special Agent Marvin Massey told local Denver media that many of the criminals behind these scams are operating from overseas. Moonlock analysis of some of the IoCs in the list provided by Malwarebytes seems to confirm this statement. At least 2 sites are linked to internet servers in Italy and Germany.
It’s worth noting that these European servers may be used by cybercriminals located elsewhere. However, the presence of German and Italian languages on these sites shows that the targets of this scam could very well go beyond the United States and be of international concern.
For example, the site convertitoremp3[.]it is written in Italian. The site is not secure. It has certificate “errors,” and while it is flagged by some browsers, it can still be accessed by others.
We found that even when not downloading the file conversion software promoted and distributed by the site mentioned above, users are still at risk of exposing their personal data.
The site (as the image below shows) runs a Canva Data Extraction technique. This is used to gather information about your system, device, and other data.
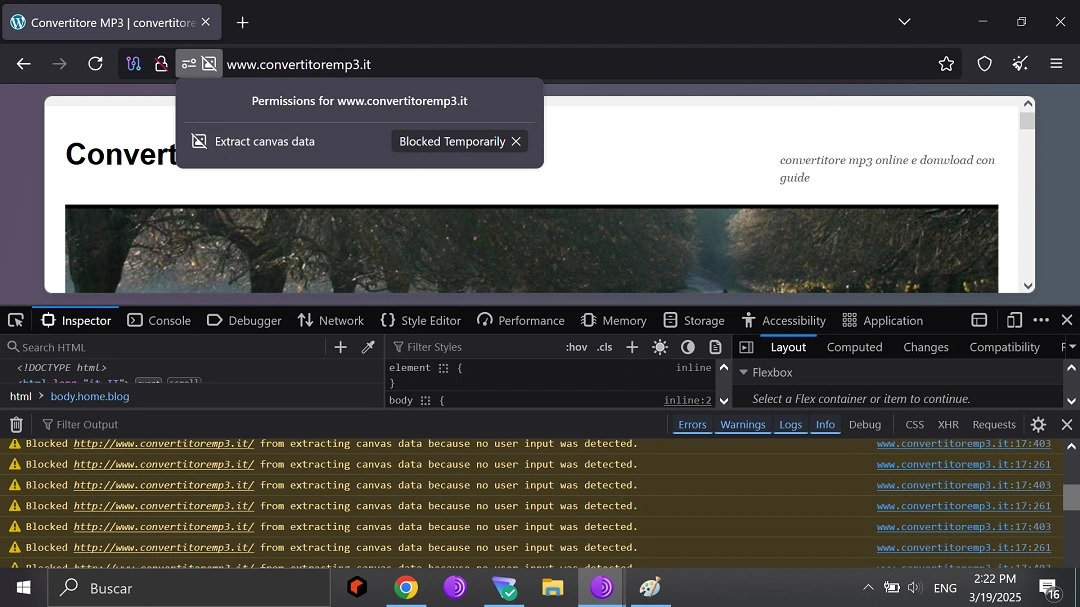
Canva data extraction is not a malicious feature. It is used by browsers to manage renders, fonts, graphs, etc. However, it can also gather your information by asking your browser to draw an invisible image or text on a “canvas” (an HTML5 element) and then reading the output.
The site we analyzed generated a unique “fingerprint” of a victim’s setup. This fingerprint can be used to track victims across websites, even if they block cookies or use a VPN.
When examining the site using Tor, the browser detected that the site was attempting to extract canvas data without user interaction. This is suspicious behavior and often a sign of tracking or potentially malicious intent.
We also found that several sites in the IoC list have suspicious redirects. For example, when loading the flagged phishing page Convertscloud[.]com, it automatically redirects to https://cloudconvert[.]com/register. There, we found a fishy JavaScript.
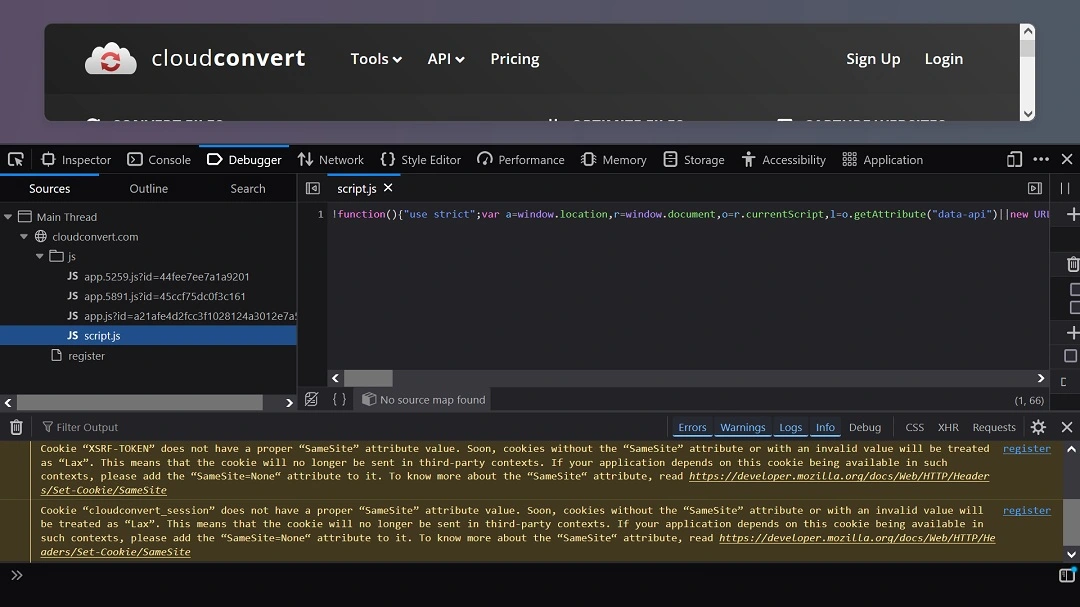
The script (shown partially in the image above) sets up data collection automatically, simply when a visitor lands on the redirect.
Here’s how it works:
- The script grabs your current URL (a=window.location), document details (r=window.document), and the script’s own source (o=r.currentScript).
- It then pulls a data-api attribute — or defaults to a URL ending in /api/event. This looks like a tracker endpoint.
- The script also verifies if you are running automation tools like PhantomJS, Nightmare, Webdriver (used in browser automation), or Cypress. If it detects them, it cancels the event tracking (return s(null,e)), likely to avoid researchers or bots catching on.
- The script collects info such as previous websites you visited, metadata, and extra tracking data. It then uses an outdated AJAX call, which phishers have been known to use to avoid tracking detection. The page also manipulates browser history manipulation functions and avoids bots and automation detection, which is common on phishing sites.
This site’s code is compressed and obfuscated into a long blob, mixes different libraries, and includes some custom code. This could be a sign of malware payload loading and distribution or other malicious commands.
Another site, Imageconvertors[.]com, also redirects visitors, leading to www.above.com/marketplace/imageconvertors[.]com. This site seems to be designed to steal personal account data. The site 9convert[.]com/en429 seems to be optimized for mobile, which could mean that the scammers are capable of cross-device targeting.
Some of the sites we checked have been active for decades. However, they have all been recently updated. This could mean the sites themselves were hijacked and taken over by cybercriminals, also a common technique.
How to stay safe from this scam and similar threats
There are several tips that can help you steer clear of this type of threat. First of all, if your browser flags a site as dangerous, do not ignore the warning. Most of these sites are flagged by browsers like Google.
Additionally, a professional and trusted anti-malware tool will detect attempted malware downloads, along with other suspicious requests from websites. Choose a strong anti-malware solution and keep it running in the background if you don’t have one already. Checking the certificates of sites is also recommended.
If you happen to come across one of these sites, the FBI Denver Field Office wants to talk with you. They are encouraging victims or attempted victims of this type of scheme to report it to the FBI Internet Crime Complaint Center at www.ic3.gov.
Do not allow permissions or install browser extensions you do not trust. When using a file conversion service, do your research and choose the best option based on reputation and security.
For those who want to strengthen their business’s cybersecurity, make sure your IT and security team blocks the IoCs linked to this threat and keep your staff updated on the cybercriminal’s trends.
Finally, as the FBI said in its press release, take a breath and think things through before you use these sites.
“The one thing that I would ask people to do when they’re doing things online is to kind of take a pause before they actually download or use one of these kinds of file converters,” said Assistant Special FBI Agent Massey.






