It’s only been months since the FBI and its international partners shut down the 911 S5 botnet monster that controlled over 600,000 IPs. Now, a new player is aiming to take the global botnet throne — Gorilla Botnet.
NSFOCUS sounds the alarm as Gorilla Botnet goes on a rampage
On September 29, NSFOCUS, the Beijing-based cybersecurity company, reported that its Global Threat Hunting System had identified and monitored a new botnet family calling itself Gorilla Botnet.
NSFOCUS said that the botnet entered an “unusually active state” starting on September 4 and continued relentlessly until September 27. In that time frame, the botnet issued more than 300,000 attack commands, with “a shocking attack density.”
The attack(s) may have been a demonstration of capabilities or a classic proof of concept test used by threat groups to gain a reputation in the dark web marketplace.
The big problem that the world has today with botnets is their ability to flood sites with immense traffic. This may not sound like much of a threat for a small e-market shop or a business card-style website, but when governments or organizations like airports or hospitals are hit with distributed denial-of-service (DDoS) attacks, the damage can be severe.
Who was affected by Gorilla Botnet?
NSFOCUS identified Gorilla Botnet attacks in over 100 countries, including China, with 20% of all attacks, followed by the United States (19%), Canada (16%), and Germany (6%). Russia is not listed as an impacted country, but our examination geolocated possibly infected hosts in Russia.
Organizations that felt the sting of Gorilla include universities, government websites, banks, and the telecommunications, gaming, and gambling sectors.
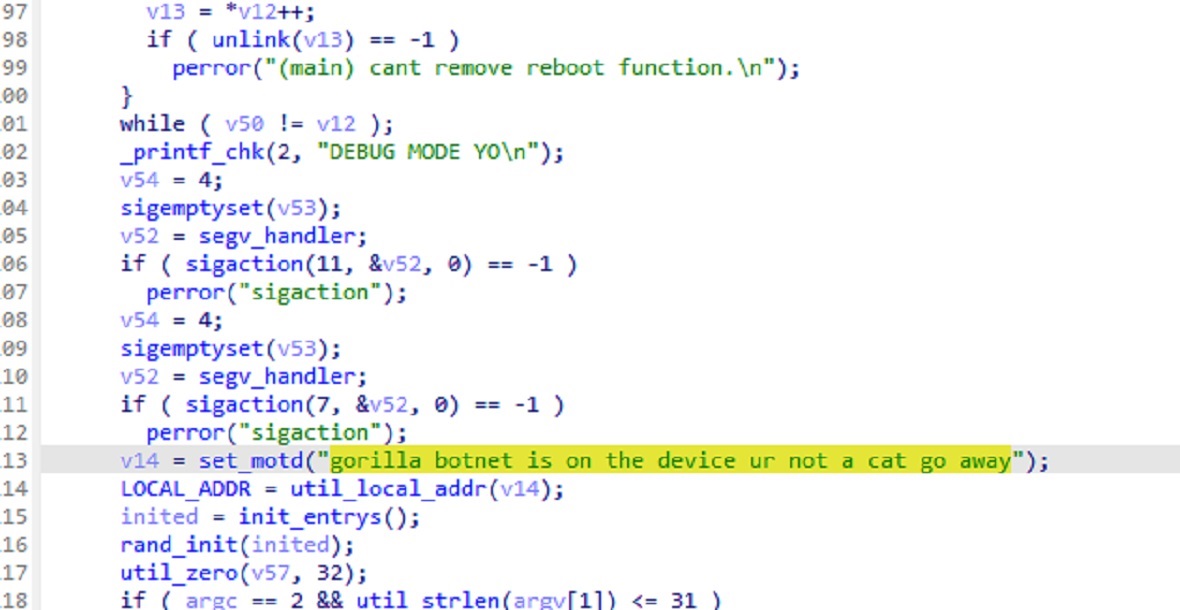
“Gorilla Botnet supports multiple CPU architectures such as ARM, MIPS, x86_64, and x86, and is a modified version of the Mirai source code,” NSFOCUS researchers said.
Gorilla (botnet) uses encryption algorithms to hide information for analysis and evasion, and simultaneously maintains successful long-term control over IoT devices and cloud hosts.
Network scanning tools can still find various pieces of information on hosts linked to Gorilla Botnet. However, it’s possible that these hosts are not actually infected with the malware or running malicious activity. With 300,000 IPs under its belt, analyzing the network is time- and resource-consuming, as well as painfully challenging.
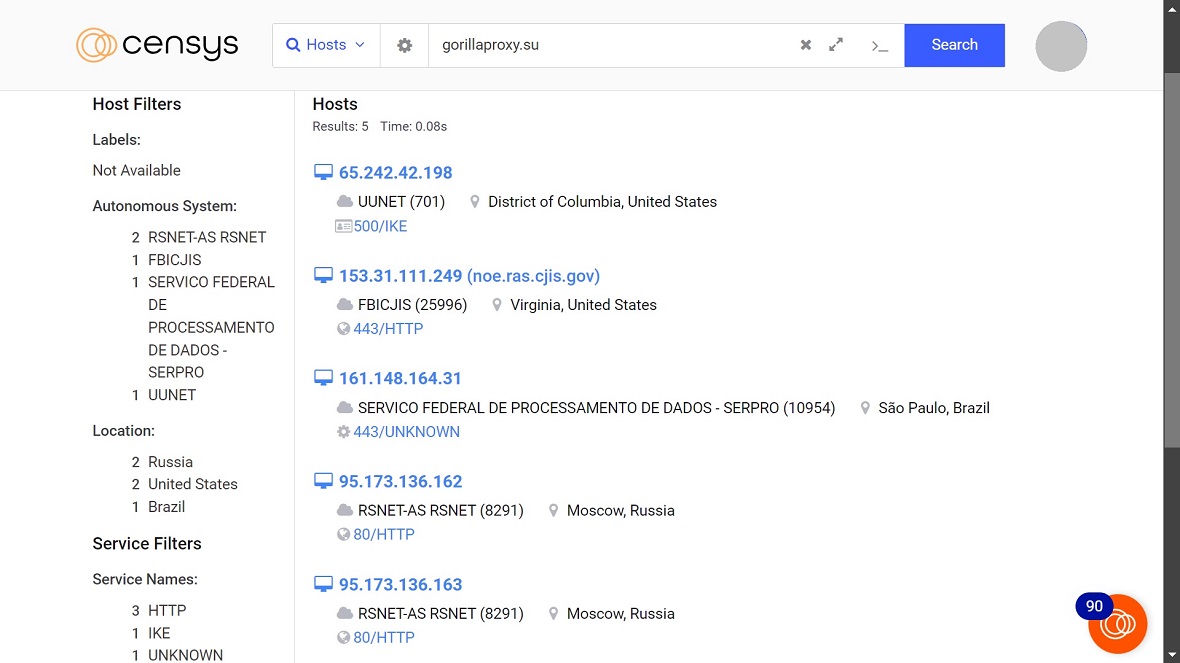
A look at hosts and related information does reveal certain elements of this botnet. Naturally, this is a large-scale bot deployed globally. Moonlock’s examination of hosts also shows government infrastructure on the list, as well as cloud servers and other targets.
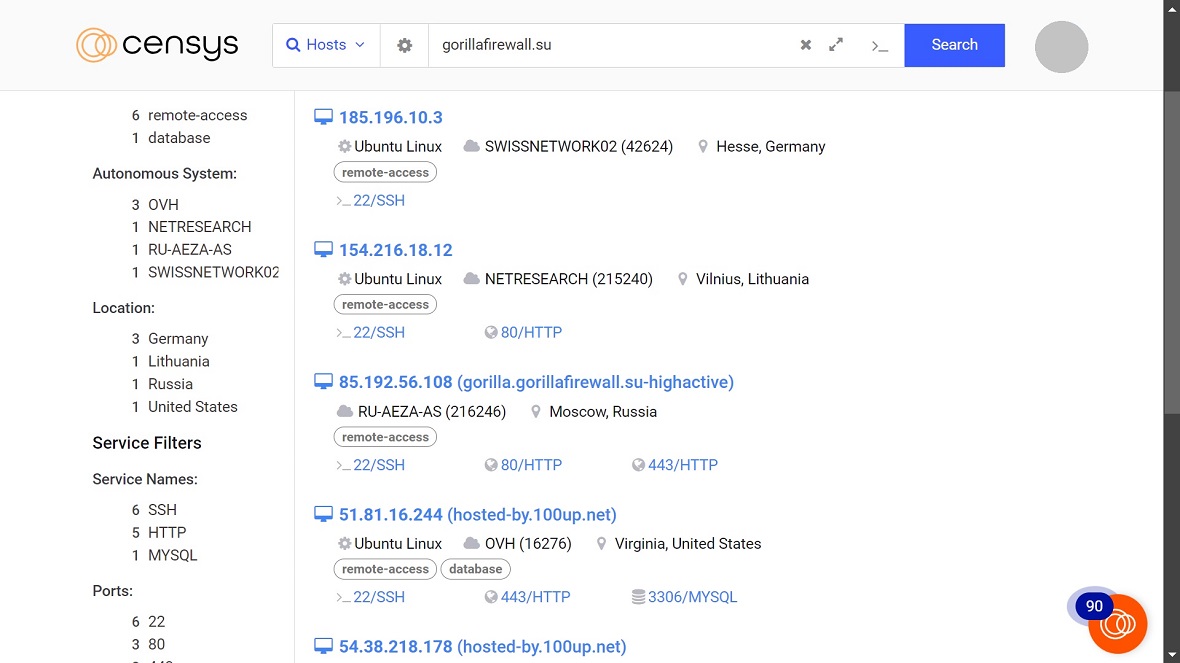
The Gorilla Botnet operators may be using a variety of network providers to distribute their malware and communicate with infected devices.
“GorillaBot has 5 built-in command and control (C&C) servers; upon running, it randomly selects 1 to connect to, establishes a connection with the server using the same online process as Mirai, then waits to receive commands,” NSFOCUS said.
The Gorilla Botnet goes after critical infrastructure sectors
NSFOCUS revealed what Gorilla can do, and it’s impressively dangerous. When it issued over 300,000 DDoS attack commands on September 2024, it hit a daily peak of over 20,000 commands.
“From the timing of the attacks, Gorilla Botnet sent out commands continuously over 24 hours, with a relatively even distribution of commands,” NSFOCUS said.
Those operating the botnet — which is more than likely being rented out as DDoS-as-a-service — have no problem going after critical infrastructure. These are areas that, when hit, impact the population. Examples include healthcare, water and sanitation, energy, and transportation.
NSFOCUS reported that Gorilla botnet had launched attacks against more than 40 organizations linked to these critical sectors in the past month alone.
The NSFOCUS full report reveals the attack methods that Gorilla Botnet tends to use, including UDP Flood (41%), followed by ACK BYPASS Flood (24%), and VSE Flood (12%), and how UDP protocols allow IP spoofing and generate high traffic.
NSFOCUS sample analysis led them to believe that Gorilla Botnet may be linked in some way with Keksec Group. This threat group specializes in DDoS and is known for operating multiple botnets, including EnemyBot, which is based on Gafgyt and Mirai.
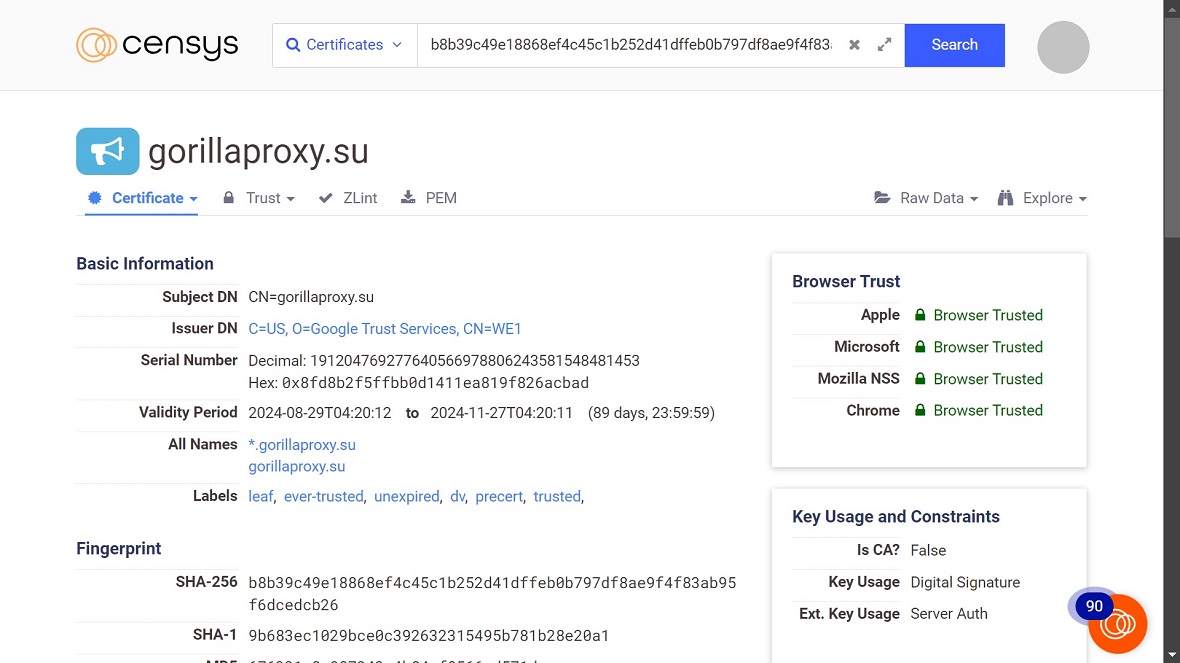
Who operates the Gorilla Botnet?
Moonlock did a quick search on Telegram for Gorilla Botnet accounts. While we found several channels related to the Gorilla botnet, 1 account that linked to other accounts jumped out right away — Gorilla C2 @friedgorilla.
The @friedgorilla account included posts announcing that the channel was being abandoned because “we left the administrative permissions over this (Telegram) channel far too open.”
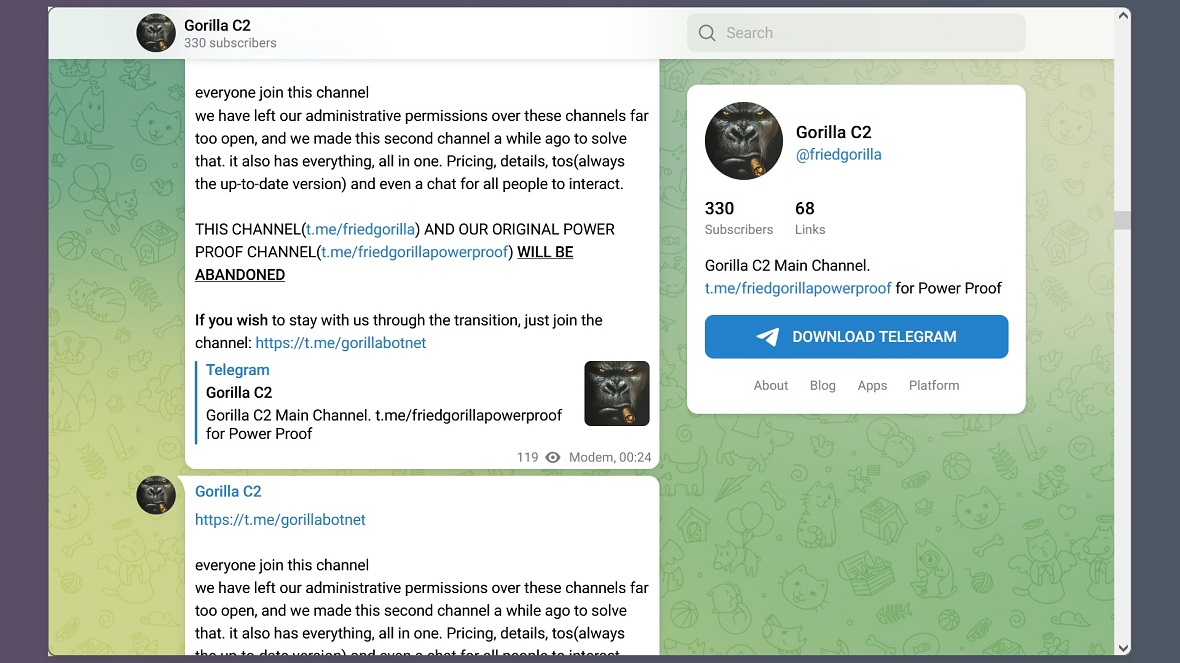
The @friedgorilla channel was created on July 24, 2023, and it’s been abandoned since late 2023. All the time, it has been promoting what appears to be botnet malware.
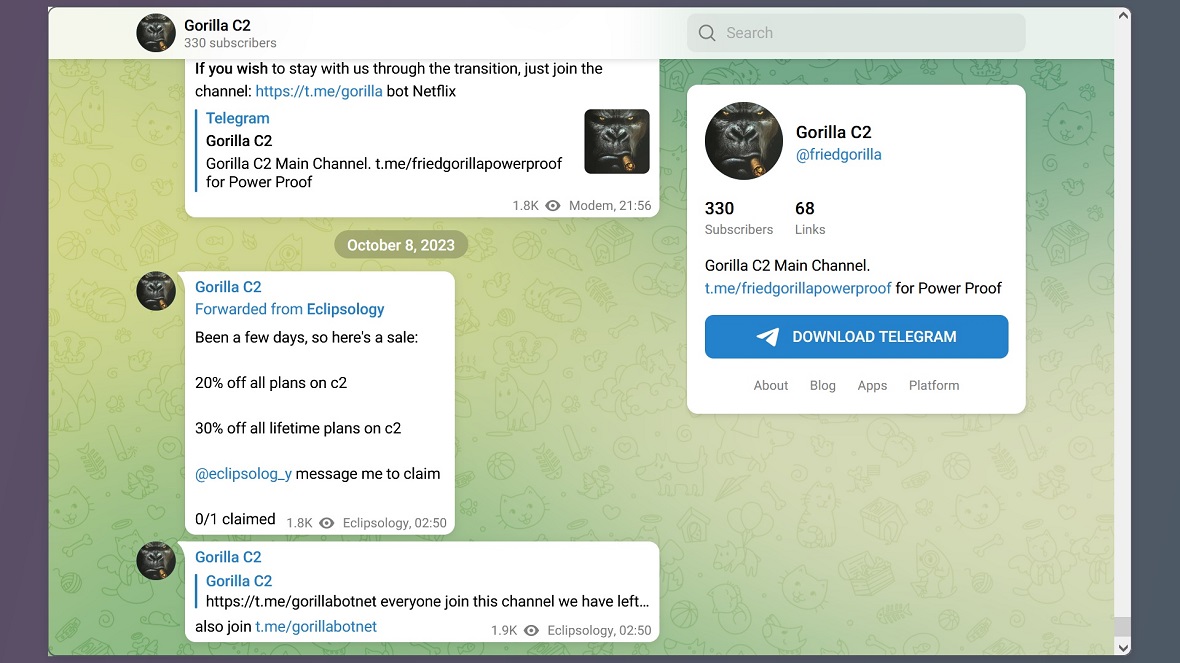
The account also included posts with sales and promotions with discounts (for alleged malware), as well as a link to another account, t[.]me/friedgorillapowerproof, for “Power Proofs.” That channel, too, was abandoned.
Posts on the abandoned channel also redirected users to another Telegram user @modem_bypass channel. This channel has a note that reads “(NOT ACTIVE PLEASE MESSAGE ADMIN TO BUY/HELP).”
The title of this new “inactive” Telegram channel is “Gorilla Botnet.”
Identifying botnet operators is a complex task that typically requires collaboration between security researchers, law enforcement agencies, and threat intelligence organizations.
The likelihood of determining an operator simply by looking at a single domain name or host list is low. Therefore, Moonlock calls for further investigations to focus on the operators behind Gorilla Botnet.
How to protect yourself from Gorilla Botnet and other botnet monsters
In the ever-evolving digital world, where threats lurk around every corner, it’s crucial to equip yourself with the necessary tools and knowledge to stay safe. Gorilla Botnet, a menacing force in the cyber realm, underscores the urgency of safeguarding your digital assets.
To shield yourself from falling into the clutches of such digital monsters, consider keeping a close eye on your digital attack surface, operating systems, apps, devices, and security patches. Additionally, use unique passwords and MFA. Botnets spread fast, so make sure you are not downloading or clicking on things you shouldn’t be.
It is always a good idea to run a professional anti-malware solution and execute deep scans periodically to make sure your devices are not infected. Finally, always keep updated on cybersecurity news to understand where and when the wave will break.