2024 has been a historical election year. About half of the global population hit the polls in 64 countries, including the United States, several European countries, India, Mexico, and Taiwan, reshaping policies and politics around the world.
From weaponized social media manipulation and misinformation campaigns to DDoS attacks, web defacement, data leaks, and AI-generated phishing and deepfakes, the 2024 elections posed major challenges for cybersecurity.
In this report, Moonlock spoke to experts and analyzed election-linked cybersecurity incidents in an effort to understand how nation-state actors, hacktivists, and cybercriminals behave when it’s time for the people to vote.
The state of the global election threat landscape
As Mandiant — Google’s cybersecurity subsidiary — warned in April 2024, elections in 2024 attracted a wide range of threat actors. While the dominant players were undoubtedly state-sponsored actors, with Russia, China, North Korea, and Iran identified as the most powerful and active, hacktivists and domestic actors also played a role.
AI-driven social media manipulation campaigns set a new bar for election security teams
The level of risk across the global election threat landscape pressured government agencies and cybersecurity teams around the world. This change requires a comprehensive understanding of how to respond to a wide range of threats, including new AI-powered social media manipulation.
Moonlock spoke to Yashwant Aditya, Senior Network Security Consultant at the Lenovo Group company LPS. Aditya told Moonlock that election interference has become more sophisticated and multifaceted in recent years.
“There’s been an increased use of AI and deepfakes, with adversaries leveraging artificial intelligence to create more convincing disinformation campaigns,” Aditya said.
There’s been an increased use of AI and deepfakes, with adversaries leveraging artificial intelligence to create more convincing disinformation campaigns.
Yashwant Aditya, Senior Network Security Consultant at LPS, a Lenovo Group company
“The main actors behind election interference are typically nation-states, with Russia, China, and Iran being the most prominent.”
United States elections: The unraveling Salt Typhoon operation
In the lead-up to the presidential US elections, as federal law enforcement agencies warned, nation-state actors unleashed waves of misinformation and disinformation attacks. These attacks were executed with the intention of eroding public confidence in the democratic processes. The campaigns were mostly run by Russian-linked operatives who, at times, leveraged US domestic assets.
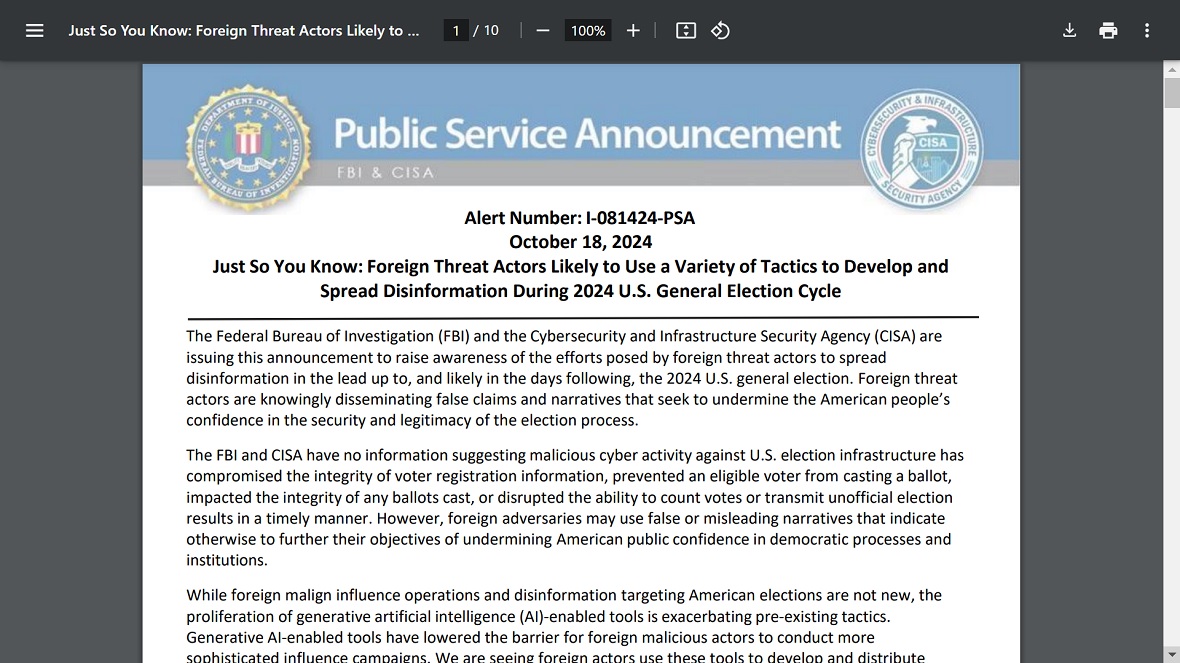
However, of all of the 2024 US election security incidents, one stands out as being exceedingly bold and sophisticated. The Wall Street Journal described this particular hack as “a devastating counterintelligence failure.”
On October 11, 2024, The Wall Street Journal reported that the cyberespionage threat actor Salt Typhoon — linked to China — had breached and gained access to US government wiretapping systems and data. The threat actor gained access to the system by hacking major US telecommunications operators, including T-Mobile, AT&T, and Verizon.
Recently, the FBI announced it was investigating a possible Chinese hack into the iPhones of 2 presidential campaign officials. These are believed to be linked to the same cyberattack.
What the threat actor did inside these telecom systems and inside the federal wiretapping system is yet unknown. It is also unclear how long the threat actor persisted inside the systems. Experts warn that modifications could have been made, backdoors could have been deployed, and sensitive data is surely compromised.
A shift in focus targeting high-value officials
Other nation-state threat actors who launched cyberattacks against US elections include Russia and Iran. Attackers from Iran also hacked the Trump presidential campaign.
“The focus (of cyberattacks) has shifted towards targeting specific campaigns and officials, as evidenced by the alleged Chinese hacking of presidential campaign officials’ iPhones,” Aditya from Lenovo Group told us.
“China focuses on influencing down-ballot races and targeting specific anti-China politicians,” Aditya added. “Iran has also been involved in hack-and-leak operations targeting presidential campaigns.”
Aditya said that the volume of foreign interference in the 2024 US election surpassed that of both 2016 and 2020.
India elections see large-scale dark web voter data leaks and social media public opinion manipulation
The 2024 elections in India saw 2 main waves of attacks. These were dark web voter and citizen data leaks and large-scale social media manipulation.
Researchers from Resecurity found that cyberattacks in India increased 300% after #OpIsrael and the protests in the ongoing Israel-Gaza crisis.
Resecurity found that multiple hacktivist groups stole personal identifiable information (PII), data, and credentials of Indian voters and citizens. They then published it on the dark web.
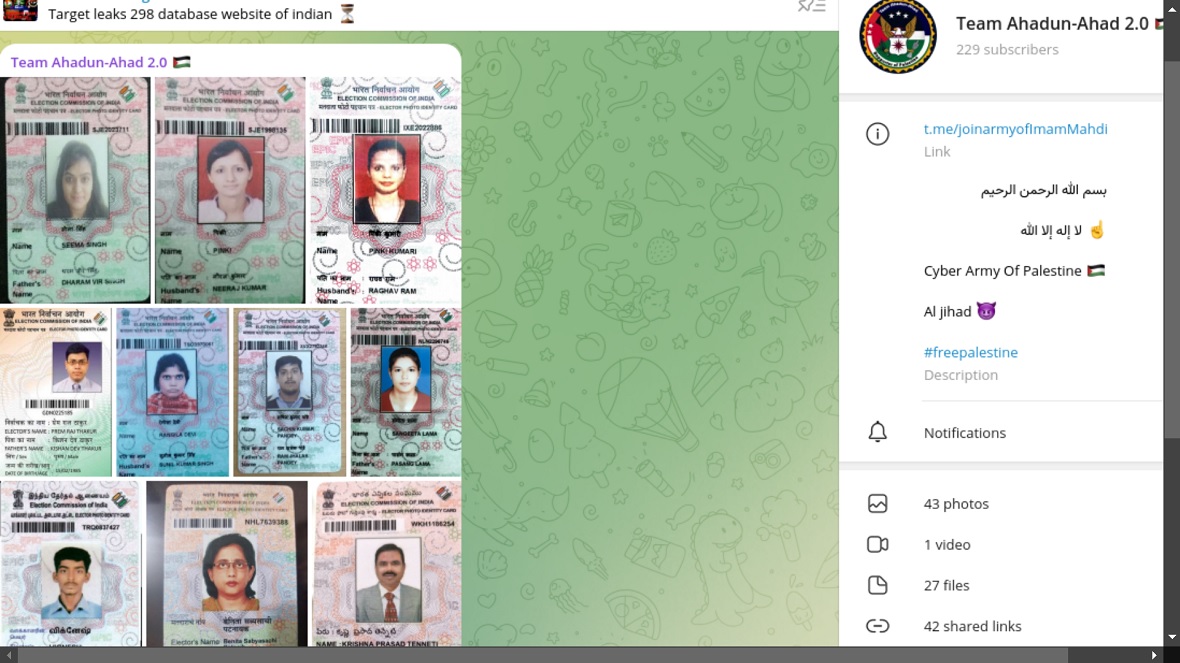
The most active groups participating in these attacks include Anon Black Flag from Indonesia, Anonymous Bangladesh, the Morocco Black Cyber Army, and the Islamic Cyber Team. These groups have targeted local law enforcement. They have also targeted the government, healthcare, financial, and private sectors of India to create narratives during election times.
The exfiltration of Indian citizen data is believed to have been accomplished using popular information stealers like Lumma, RedLine, Nexus, and Medusa.
The threat actors are believed to have foreign or external support. Using the stolen data, they created several public opinion manipulation campaigns that targeted the Indian government, the Prime Minister, and others. Additionally, malicious social media narratives were used to create tensions among the Indian and Muslim populations.
Mexico hit with over 400 DDoS attacks on election day
During Mexico’s general election, held on June 2, 2024, the country saw 2 important DDoS attacks. The first occurred during a televised presidential debate. The second was on election day, targeting the Electoral Institute of Mexico City (IECM).
The IECM reported a total of 441 cyber-attacks during the Preliminary Electoral Results Program (PREP) for the Head of Government. The DDoS attacks caused the IECM’s page to crash on election day. It is unclear whether a foreign threat actor was behind the attack.
In the run-up to Mexico’s election day, the website of the right-wing National Action Party (PAN) was also taken offline by a DDoS attacker during a televised presidential debate.
European Union elections and the “Russian Hybrid War”
The 2024 European Parliament elections took place between June 6 and June 9, 2024. Cyberattacks linked to the election have been attributed to Russia.
In a series of attacks, Russian-linked threat actors attempted to sow division among NATO allies and pressure governments that support Ukraine. Some attacks took place on digital battlefields. Others, such as arson or graffiti campaigns, happened on the streets of Europe and the United Kingdom.
On May 3, 2024, Germany’s Interior Minister disclosed that ATP 28, a threat actor linked to Russia’s GRU, had infiltrated the Social Democratic Party headquarters and the defense, aerospace, and aviation sectors. Five days later, Poland reported similar attacks on government networks.
Kosovo also faced cyberattacks, while France experienced waves of disinformation campaigns, allegedly orchestrated by Russia, before and during the Olympics.
As mentioned, these incidents are linked to “Russia’s broader hybrid warfare strategy” in Europe. The goal? To influence elections and public opinion, undermine NATO support for Ukraine, and sow discord among allies and population groups.
We asked Brian Cute, Chief Operating Officer and Capacity and Resilience Program Director at Global Cyber Alliance, what role social media plays in modern elections.
“Social media is both a delivery and amplification vehicle for attacks,” Cute said. “Social media platforms are designed to feed users and groups the types of content they show interest in; they can serve as an effective delivery vehicle for mis- and disinformation.”
Cute explained that nation-state actors who are looking to influence the outcome of other nations’ elections for their own benefit launch mis- and disinformation campaigns that are designed to discredit certain candidates. They also aim to influence voters’ beliefs about the integrity of elections.
UK and EU government ministers’ data leaked
The road to elections in Europe and the UK also saw a wide range of cyberattacks. On May 30, a dark web inquiry revealed that sensitive personal data of government officials from the British, European, and French Parliaments had been compromised and leaked online.
The data breach occurred weeks before the European and UK elections. Over 1,000 officials were affected, with their emails, passwords, birth dates, and other confidential information exposed.
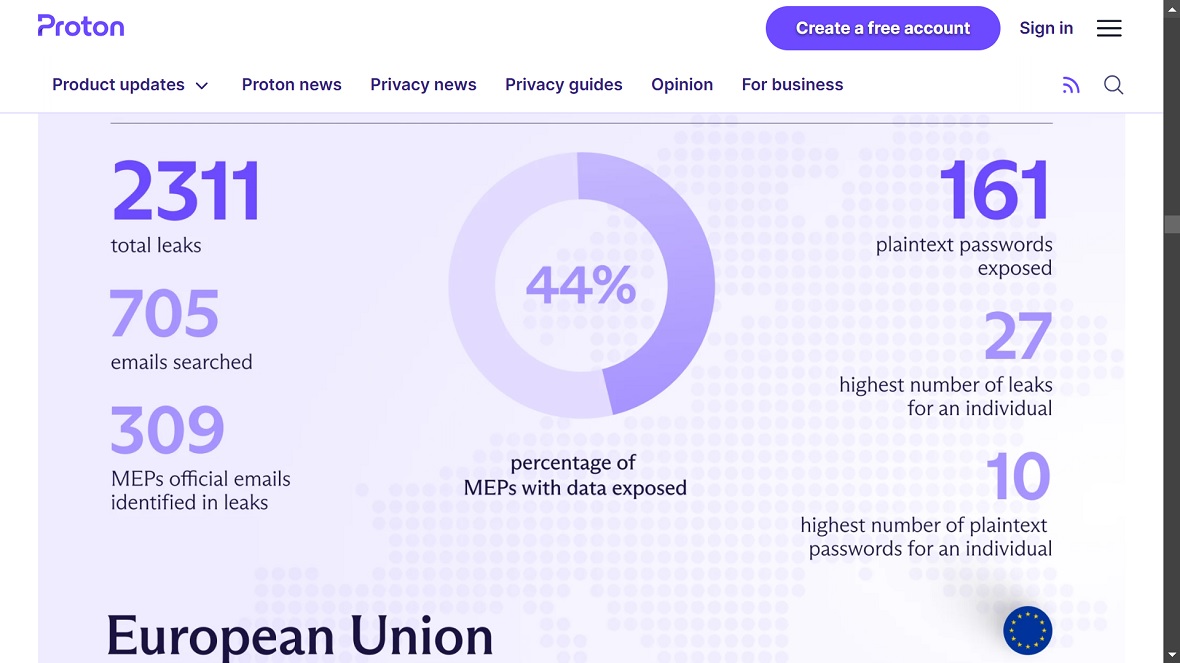
The tactic of accessing sensitive data and releasing it on the dark web for other threat actors to use has become a dangerous trend. With user data and credentials, attackers can launch countless attacks, with increasingly high success rates.
Russia’s claims that “Western Enemies” orchestrated cyberattacks raise eyebrows
Recorded Future reported that as Russia prepared for its presidential election in March, with President Vladimir Putin running against 3 “officially permitted” opponents, the Ministry of Foreign Affairs said hackers from “Western countries” were plotting and executing cyberattacks against Russian election infrastructure.
Russia’s foreign intelligence accused the US of orchestrating cyberattacks against Russia’s voting system, a claim the White House denied. Russian authorities provided no evidence to support their claims of fake news and system breaches. However, the country did ban certain polls, forecasts, and studies that did not meet “government” standards.
Russia also shut down electronic voting in regions where the government claimed that “security could not be guaranteed.” Experts warned that Russia’s election cyberattack claims could be an example of how governments can manipulate cybercriminal trends to criminalize certain issues and behavior to prevent free and fair elections from taking place.
Taiwan and the South China Sea Conflict
Taiwan was “bombarded with cyberattacks ahead of the 2024 elections.” Cybersecurity experts and geopolitical analysts linked the attacks against Taiwan’s critical infrastructure during elections to Chinese threat actors.
Taiwan saw cyberespionage campaigns, DDoS attacks, government website defacing, and social media manipulation. Additionally, security experts say the country unleashed its AI state-of-the-art technology to create narratives.
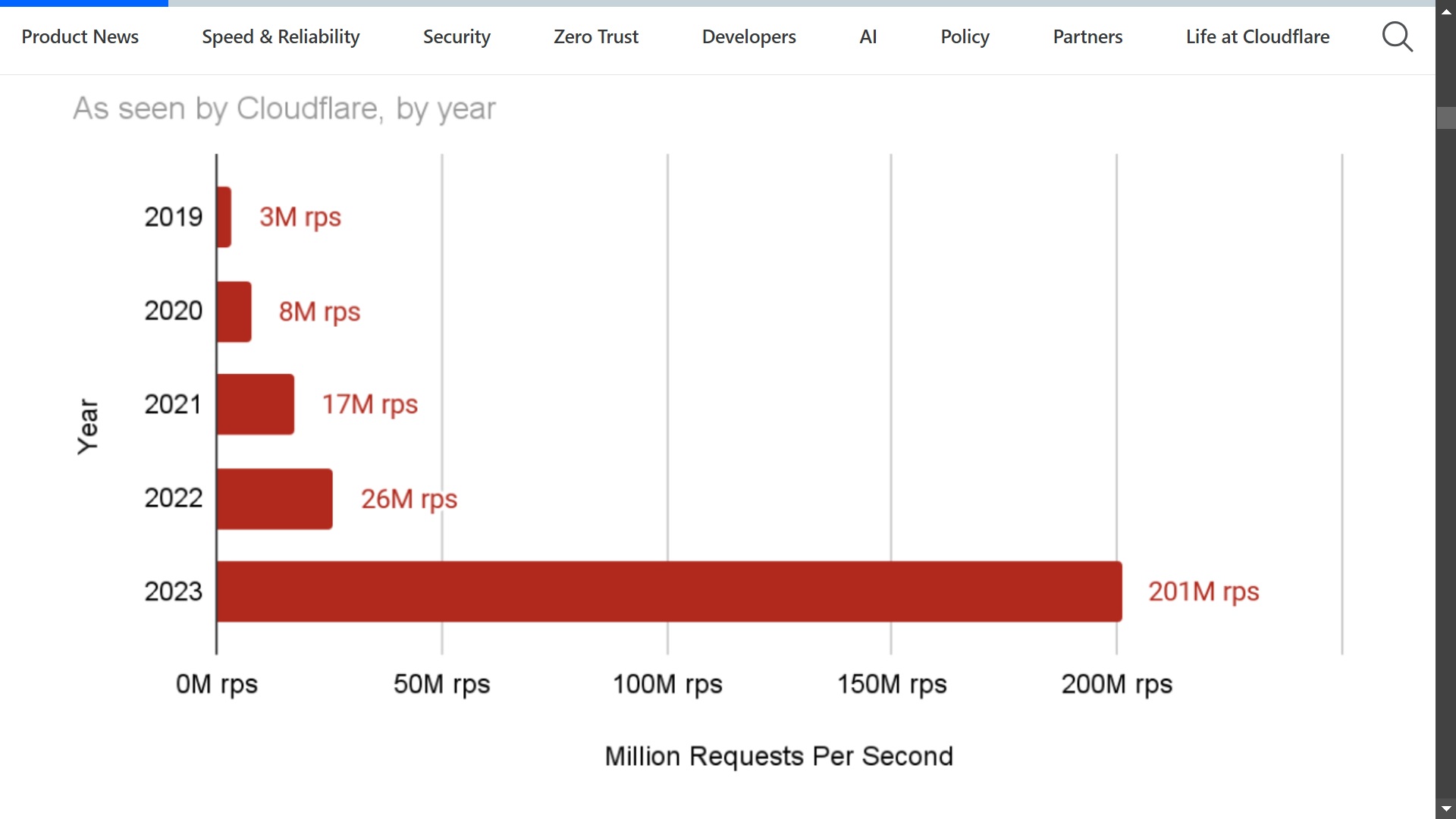
CrowdStrike reported that DDoS attacks against Taiwan in the months prior to the 2024 elections (the end of 2023) surged by 847% compared to 2022, and by 2,858% compared to the previous quarter.
What should governments do to protect elections?
Are governments around the world aware of the level of risk that the current global election threat landscape presents? What exactly should they be doing, especially to deter and shut down foreign actors?
Michael Jung, CFO and Head of Global Business Development at DeepBrain AI, an all-in-one generative AI platform, spoke to us about geopolitics in election times.
“Global conflicts continue to encourage cyber activity across the world, resulting in additional conflicts,” Jung said. “In the geopolitical context, some ways that governments can protect elections are by implementing cloud security to improve visibility, the ability to detect threats, and the incident response speed.”
“To prevent impersonations, political parties can implement strong multi-factor authentication on all devices and continuous identity risk assessments to reduce the risks associated with compromised identities,” Jung said.
Cute from Global Cyber Alliance told us that governments are already taking action. Cute cited the work of the US Cybersecurity and Infrastructure Security Agency, Joint Cyber Defense Collaborative team as a public-private partnership. The partnership proactively gathers, analyzes, and shares actionable cyber risk information for cybersecurity planning, defense, and response.
Cute added that in the US, during this election cycle, federal and state officials were visibly active and communicating with the public when misinformation and disinformation instances were identified, underscoring the importance of rapid response.
A framework for government election security, deterrence, and response
Aditya from Lenovo Group said governments can take several steps to protect election integrity.
These steps include enhancing cybersecurity measures for election infrastructure. They must also implement robust security protocols, promote defense-in-depth and zero-trust approaches, and develop strong incident response plans. The fostering of collaboration between agencies and cybersecurity professionals is also essential.
Aditya explained that investing in public awareness and education about cyber threats and disinformation, and supporting technology innovation to combat AI-based information warfare, are proactive initiatives that governments can invest in to denounce and neutralize foreign interference efforts.
How can citizens prevent cyberattacks from shaping election outcomes?
So what can citizens and voters do? Cute from Global Cyber Alliance said citizens first need to be aware that nation-states and other actors are actively trying to undermine the integrity of elections.
“Second, they need to approach social media and other content related to elections with a healthy sense of skepticism,” Cute said. “Third, they should pause before sharing or amplifying content and seek the source of content to verify its validity before sharing it with friends and networks online.”
Jung from DeepBrain AI said deepfake detection software can generally detect deepfakes with over 90% accuracy. Jung said this software can help citizens compare suspicious content with original data to verify authenticity. “This can be especially helpful as deepfakes become more and more common on social media,” Jung said.
Final thoughts
2024 has been, without a doubt, a major election year for the world. Unfortunately, cybersecurity researchers and experts agree that the number of cyberattacks in election times has also been historical. They also reached a new level of sophistication.
None of these cyberattacks had tragic, preventable consequences, nor are they believed to have impacted the outcome of the elections. However, they are evidence of the types of cyberattacks that already exist. Furthermore, they give us a sense of what is coming.
From social media manipulation to DDoS attacks, data leaks, the dark web, and misinformation, election cyberattacks are dominated by nation-state actors who often turn to domestic groups and hacktivists.
The true extent of the cost and impact that these global cyberattacks have had on governments, businesses, organizations, and citizens — especially among campaigns that sow division, violence, and erode trust — is yet unknown.