In December 2022, Trend Micros researchers noticed important changes in the delivery methods of the IcedID malware. The banking trojan, first discovered in 2017, used to target primarily the customers of financial institutions (e.g., banks, internet banks, credit card providers, and e-commerce websites). Now hackers have begun to abuse the Google pay-per-click (PPC) advertisement network to spread the malware to unaware users.
Attack methodology
The Google ads service allows businesses to display their advertisements to end users to boost sales and increase site traffic. Hackers work to abuse this legitimate service to direct users to their malicious websites through spoofing legitimate domain names.
First, hackers purchase domain names similar to those of legitimate online services or companies. For example, one of the companies targeted in the recent campaign was Adobe. The real domain name of Adobe is adobe.com. To impersonate the company website, hackers have purchased domain names that read similar to it, such as adobesoftware.site or adobeprograms.tech.
Then, hackers have purchased advertisements on Google Ads to drive users to these malicious domains when they search for the target company or online service. For instance, when you search for “Adobe Reader,” sponsored ads appear at the top of the search engine result page. The distinction between the advertisement and the actual search result is minimal. When you click on the ad, you will be redirected to a malicious site that looks identical to the legitimate one.
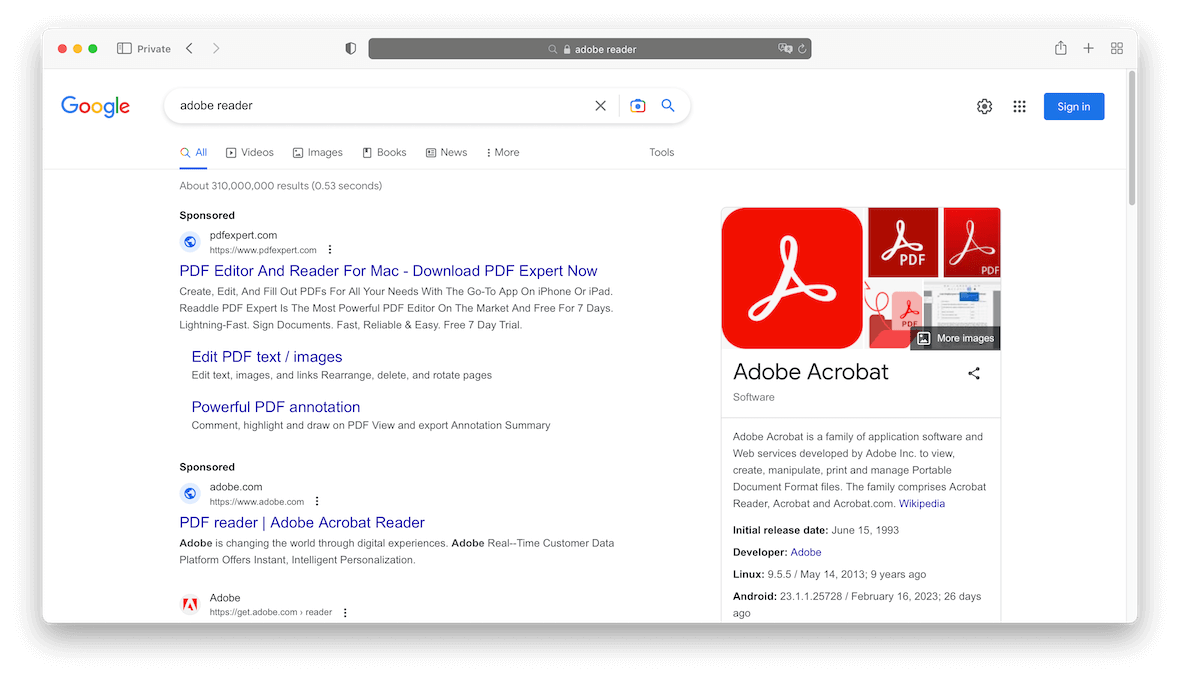
The spoof website is designed to trick users into downloading the IcedID malware, which can then serve as a backdoor for hackers to install additional malware or make the infected device part of a botnet.
How to prevent IcedID from infecting your device
- Be very careful when clicking ad links. Depending on your browser, you might be able to see the domain name above the ad. Alternatively, you can hover your mouse over the link to reveal the actual destination before clicking on it.
- Don’t search for the bank or financial institution you want to access. Type their domain name directly into the web browser address bar.
- Double-check the domain name before taking any action on a website and make sure the domain is secured with the HTTPS protocol.
The IcedID botnet has now returned with new distribution methods. Malvertising abuses legitimate ad networks, such as Google ads, to spread malware. Knowing how to distinguish between legitimate websites and fakes created by hackers is vital for protecting yourself from this threat.