Botnets have been around since the early days of the internet and remain one of the world’s most threatening cybersecurity issues. A cyber botnet has only one basic requirement: an internet connection. Once connected, the possibilities of what it can do are as endless as they are scary. But what are botnet attacks anyway? And what can you do about them?
What is a botnet in cybersecurity?
A simple botnet definition would be to compare it to multiple computers being harnessed together to carry out a specific task. When multiple computers are forcibly co-opted into a network, their combined processing power can be harnessed to launch cyberattacks against other networks.
Each infected computer is known as a “bot” or a “zombie,” and they are all remotely connected by a single device controlled by the botnet’s owner. The owner of each individual computer is often completely unaware of what their machine is being used for.
The most common use of a botnet is to launch distributed denial of service (DDoS) attacks against websites and networks. They are also used to send spam, commit cryptojacking, and steal data.
Who invented botnets?
The oldest botnet dates back to 1988, when Internet Relay Chat (IRC) emerged. IRC is a text-based chat system designed for group communication. In those days, games like Hunt the Wumpus used IRC bots.
By the end of the 1990s, the first search engines had begun using bots to index pages. Online search sites like WebCrawler, AOL, Excite, and the now world-famous Googlebot, created in 1996, were the dominating bots of the time, all working legally.
But as the millennium shifted, malicious bots began to rise. In 2001, EarthLink gained a bad reputation for its spamming practices, sending out billions of emails and becoming responsible for 25% of global spam at the time. By 2006, malicious bots were scaling big time.

How does a device get infected with botnet malware?
Most malware gets into hacked Mac computers by similar methods, and botnets are no different:
- Phishing links and infected email attachments are the most common culprits, as it’s easy to send out vast amounts of spam and hope that a small number of users fall for the ruse.
- Pirated software and “cracks” represent another big source of malware. After embedding the botnet malware into the software, it’s simply uploaded to the pirate site for someone to download and install.
- Unpatched operating systems and software vulnerabilities are another common method of entry. This could be due to the user being too lazy to install updates, or it could be from old, outdated software that no longer has support from the developer. Routers are also another favorite.
- Downloading software and apps from the internet can be a big culprit. If you’re installing something from the App Store or a recognized developer, you’ll likely be fine. But anything else? Stay clear.
- Adware is a big cause of botnets. Clicking on an infected link will lead you straight to malware that’s waiting to jump onto your device.
- Infected USB devices are a bigger problem than you might expect. Never plug any unknown devices into your computer. A USB left lying around could lead to your machine quickly becoming involved in botnet attacks.
How a botnet works
So how do we define botnet malware? The word “botnet” is a combination of the words “robot” and “network,” which precisely describes the nature of a botnet: a robotic network that acts as one.
Many wrongly believe that making a botnet is extremely complicated. Unfortunately, it is not. Cybercriminals usually create botnets by infecting computers, with the most popular method being email phishing campaigns. Users will receive an email and are tricked into auto-installing malware on their computers without their knowledge.
The infection is done in bulk. The bigger the botnet, the more power it has when launching attacks. Once a computer or device is infected, hackers can modify the system so it goes unnoticed and is used at their command. The more advanced botnets can even self-propagate through constant seek-and-infect missions.
Known as botmasters of bot herders, the cybercriminals who control botnets can link any internet-connected devices, from computers to smartphones, IoT devices, smart TVs, smartwatches, and others.
To answer this question, we must ask, what is botnet malware? Botnet malware communicates in the same way legitimate computer programs communicate over the internet. But these ones use a small amount of computer power to avoid detection, and their communications are masked using encryption, access the internet over protocols (like HTTP), and can be coded with algorithms that set their next check-in domain or launch seek-and-infect attacks.
Types and examples of botnet attacks
Botnet networks are created with two structures to launch different types of attacks. The first is a centralized structure where the attacker has a central server that controls all the infected devices. In the second type of structure, attackers create a decentralized network. Each infected device functions as a client and a server, known as a peer-to-peer (P2P) structure. These two types of bot networks can be used to launch the following attacks.
1. Spam botnet attacks
The primary vector of attack in the modern environment is email phishing. This means that the vast majority of attacks work by gaining access to a system through malicious emails. A spam bot network can target a specific organization or may send out millions or even billions of these malicious emails.
A recent example of a spambot is Emotet. About 1.6 million devices make up the Emotet network, which was first detected in 2014. The threat actor behind Emotet is Mummy Spider, which takes month-long pauses between attack operations, during which it perfects the malware and its capabilities with new variants.
To date, authorities have taken down Emotet several times, only to have it return. In January 2021, Europol announced the complete shutdown of the network in a joint operation across the Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada, and Ukraine. However, ten months later, Emotet resumed operations.
2. DDoS attacks
Distributed denial of service attacks (DDoS) are the most common use of botnets. These bot attacks overload a server with web traffic created by zombie devices to crash it or prevent other users from accessing the site.
The Meris bot was responsible for some of the most significant attacks of 2021. Comprised of 250,000 bots, Meris broke the record for most powerful DDoS attack — and then broke the record again, all in a single year. Meris works by sending emails to large companies demanding ransom payments as it launches a DDoS attack.
This malicious network can generate a substantial 17.2 million requests per second (rps). It can also target approximately 50 different websites daily, with an average of 104 unique DDoS attacks. Most of Meris’s attacks target sites in China, Australia, and the United States. It targets banks, financial services, crypto providers, gambling and gaming sites, technology industries, and other sectors.
3. Brute force attacks
Hackers can also force its way into a system by repeating combinations of usernames and passwords using bot networks. These “brute force” attacks can bypass two-factor authentication (2FA) and multi-factor authentication (MFA) security features.
There are several historically famous brute force attacks, some of which affected companies known for having robust security. In 2013, a massive brute force attack breached 25,000 Club Nintendo forum members’ accounts. The attack executed 15.4 million login attempts to gain access.
GitHub was also hit by an attack in 2013. Login attempts were executed from about 40,000 different IP addresses. Although GitHub never disclosed the total number of affected accounts, the event is still considered one of the largest in history. And in 2015, more than 21 million Alibaba Group accounts were compromised. In this attack, criminals used a combination of 99 million usernames and passwords to force their way into accounts.
Signs that your computer may be infected with botnet malware
Botnets are good at hiding. They use a low amount of computer resources and can even modify features to conceal themselves better. Here are four signs that can help with detecting botnets.
1. Suspicious computer performance
You might be part of a malicious network if you notice that your computer is acting strangely. For example, if your computer fans suddenly kick in, or if you notice your hard drive is in use or your computer is unexpectedly slow, these may be red flags. Your computer may also crash suddenly, be slow to restart, or fail to shut down.
2. Slow internet
If there’s anything bots are hungry for, it’s an internet connection. If you notice that your internet is slower than usual, not downloading files, failing to upload files, or failing to send out emails and messages, you might consider checking for malware. Remember that bots can infect all devices, even your wireless router, so check to see if it is excessively active.
3. Spam emails and strange messages
Have you recently received one or several suspicious emails or messages asking you to download or click on a file, add extensions, or update your system or programs? This is a clear sign that you should check for malware.
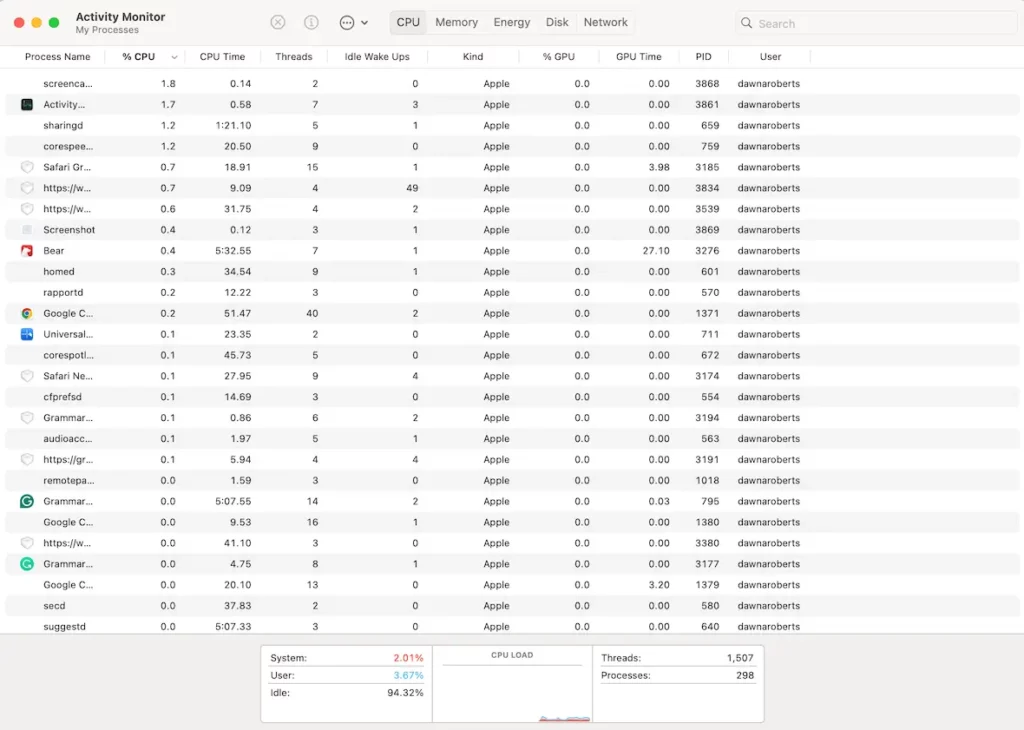
4. Task Manager activity
Open the Task Manager and check for RAM usage and total computer power available. If you see them running at a total 100% capacity, check to see if any strange process is running. It could be part of botnet malware.
5. Failure to update
Botnets will often prevent you from updating your smartphone or your computer. Malware wants to avoid new security updates and patches because it uses existing vulnerabilities as doorways to prevent detection. If your device ever fails to update, always check it for malware.
How to remove botnet malware
When checking and removing malware like botnets from your Mac, it’s best to know the most effective and fastest methods to get rid of the botnet. Your first step should be to immediately disconnect your MacBook from the internet. In other words, isolate the threat so you can then destroy it.
Stop your device from syncing and put a halt to cloud backups. Otherwise, you’re just going to spread the botnet to other devices and increase the risk of them infecting other computers.
Next, it’s time to go on the offensive. The fastest botnet removal process uses a powerful and lightweight tool called Moonlock. It is a security app for Mac computers and a highly efficient botnet scanner that will detect and defeat botnet infections.

After signing up for the free trial, installing the app, and clicking Malware Scanner in the sidebar, just do the following to begin the botnet detection process:
- Choose the Deep scan mode.
- Click the Scan button to send Moonlock on its botnet detection journey. It will start methodically searching your Mac, looking for all botnet traces, as well as any other malware that the botnet brought along.
- When the botnet files have been found, Moonlock will put them all into Quarantine. Tick all threats and click Remove.
- To make absolutely sure that every malware is detected and neutralized, make sure that real-time protection is on. Go to Home > Explore and check the status in the top right corner.
Once all that’s done, you then need to determine the source of the botnet infection. Did you click on a link? Did you install dodgy software? Are you a bit behind with your security patch updates? Isolate the cause and make sure it doesn’t happen again.
If you installed suspicious software, delete it. If it was an unpatched vulnerability, install all updates immediately.
Next, go to Activity Monitor and look for any suspicious processes that are consuming a large amount of CPU. Shut them down.
If all else fails, you may end up having to wipe and reinstall the operating system. Thankfully, Apple has made this process faster and easier than it once was. The upside is that the botnet malware will be gone forever. You may also be forced to delete your iCloud backups if the botnet infection gets in there.
How to prevent botnet malware attacks on your device
Once the botnet is gone, it’s best to get proactive to prevent future botnet attacks. Follow this strict list of guidelines.
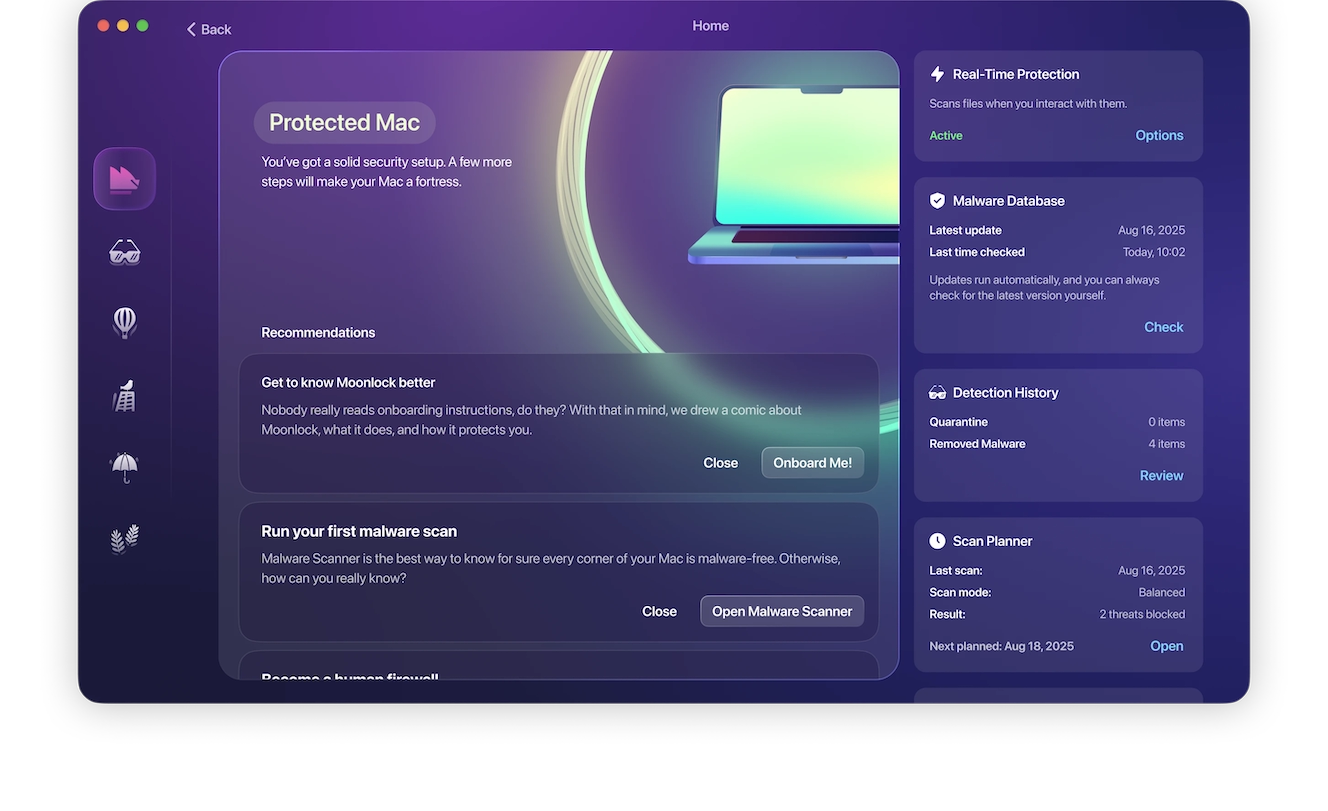
Run regular scans with Moonlock
As we said before, the best botnet protection tool you can have is Moonlock. Schedule weekly scans or twice-weekly scans to stay on top of any malware threats that have managed to get into your device.
- Open Moonlock and click Explore.
- In the righthand column of monitors, find Scan Planner. Click Open.
- Click Plan a Scan and choose the scan type, time, and frequency of scheduled scans.
- Once you’re done setting your preferences, hit Save. Now, scans will run automatically, taking this task off your mental to-do list.
Always install software updates as quickly as possible
Malware loves vulnerabilities, but installing patches in a timely manner will put an end to that possibility. Check System Settings > General > Software Update to see if anything is waiting for you.
Enable the firewall and FileVault
Fortunately, macOS gives you some powerful free security tools — but you have to remember to switch them on. By going to System Settings > Privacy & Security, you can enable the firewall and FileVault, which provides a fierce defense against unwanted intruders.
Make sure your router is properly configured
Routers are also a potential weak point. Particular emphasis should be placed on updating the firmware, putting a password on the router, and closing any ports that you won’t be using. Also, make sure that you’re using good encryption: WPA2 or WPA3.
Don’t click links or download attachments
Obviously, if a family member or trusted friend sends you a link or an attachment, then all is good. If, however, a complete stranger sends you something, don’t open it under any circumstances.
The problem of malware is only getting worse. And as operating systems and software developers get better with their security functions, malware evolves almost immediately.
It’s a constant fight to stay one step ahead of the scammers, hackers, and cybercriminals, but by employing some solid, bulletproof tips, you can lessen your chances of being infected by a botnet and becoming an unwilling participant in the next DDoS attack.