SentinelOne has released a report on a new infostealer targeting Apple’s latest OS release, macOS 14 Sonoma. The malware can not only steal passwords and browser data but can also empty crypto wallets. This infostealer was dubbed Realst because it is written using the Rust programming language.
As a trojan, the Realst infostealer hides its identity behind malicious blockchain games. SentinelOne, continuing the research that security expert iamdeadlyz did earlier in the month, identified and analyzed 59 malicious Mach-O Mac executable files.
How the Realst infostealer spreads and breaches devices
Realst spreads primarily through two methods, both of which are sophisticated and deceptive. The first strategy used by the cybercriminals behind Realst is to advertise fake blockchain games on malicious websites. The names of these fake games include Brawl Earth, WildWorld, Dawnland, Destruction, Evolion, Pearl, Olymp of Reptiles, and SaintLegend.
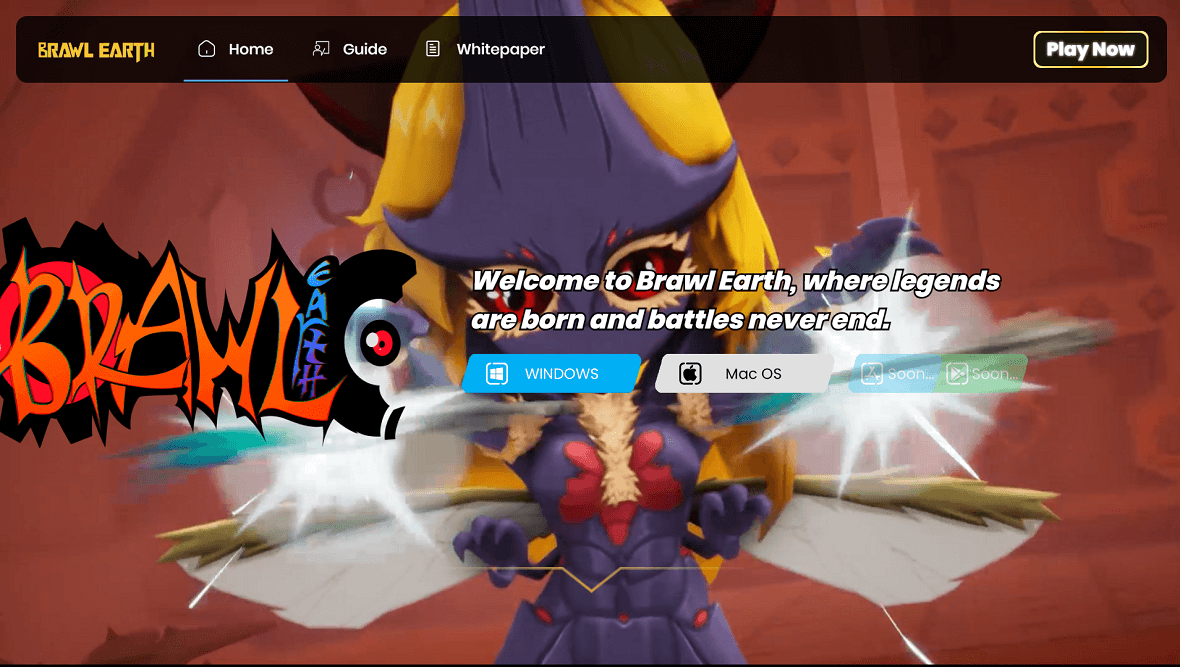
The second way the malware spreads is via phishing. In this case, social media hackers contact users to offer them payment in exchange for testing one of these new (fake) games.
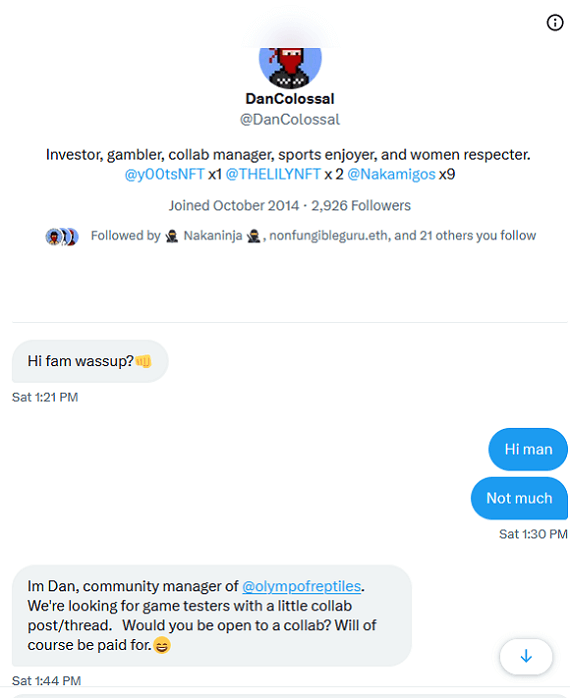
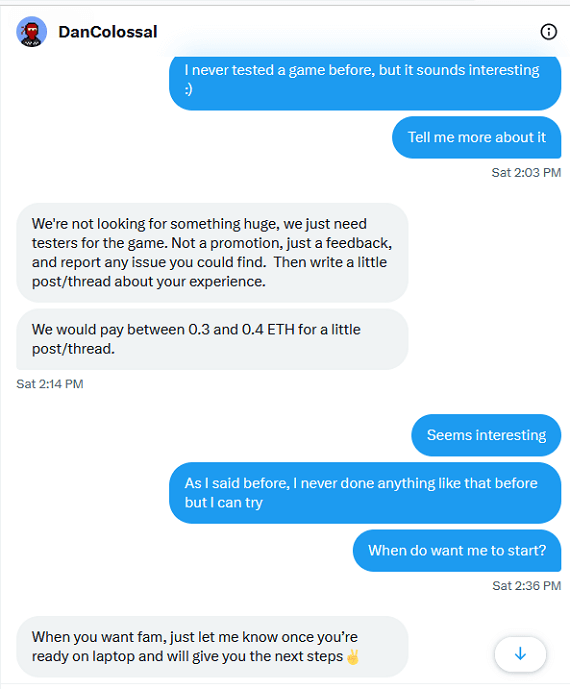
In both cases, here’s how Realst spreads and gets onto Macs:
- Victims are directed to a fake game through ads on websites or through contact via social media.
- Users are then directed to a website to download the game. Each game has its own website and fully functional Twitter and Discord accounts with hundreds of users.
- Users download the game and run the installer on their computers.
But getting users to download the fake blockchain game is only the first part of this well-orchestrated cyberattack.
How Realst steals passwords and empties crypto wallets
Once the user downloads the executable file and runs it to install the fake game, a legitimate-looking graphic user interface appears on their screen to guide them through a step-by-step installation process. The interface looks like that of a typical installer. However, this installation is anything but normal.
Once installed, Realst can:
- Steal information from your browsers and your computer
- Target Firefox, Chrome, Opera, Brave, and Vivaldi (but not Safari)
- Extract passwords, keys, and certificates from your Mac
- Target Telegram
- Take screenshots of your computer
- Give hackers access and exfiltration privileges to your browser data, crypto wallets, and keychain databases
- Target the browser extensions of cryptocurrency wallets through Binance, Metamask, Trust, Martian, Pontem Aptos, Petra Aptos Wallet, TronLink, Nami, Temple, Phatomand others.
What can you do to keep yourself safe from Realst?
Your best defense against Realst is to know how this infostealer works and take steps to prevent yourself from becoming a victim. Take care to observe the following best practices.
Don’t download unverified games
Never click on suspicious ads or navigate through unknown websites. And whatever you do, never download a new online blockchain game that you’ve never heard of, especially one that isn’t available on the Apple App Store.
Beware of strangers contacting you on social media
Additionally, be extremely cautious on social media, particularly when you are contacted by someone you don’t know. Remember that cybercriminals can create websites and messages that look very real but are nothing but complex traps. When in doubt, block and report.
Enable adblockers and pay attention to browser warnings
Good privacy and security practices, such as enabling adblockers and setting your browser to the highest level of security, are recommended. If you get a warning that you are visiting a malicious site, never ignore it.
Finally, having trusted and professional anti-malware running in the background is indispensable. A good security software can identify real-time infostealers like Realst, warn you about them, shut them down, and remove all traces of them from your Mac.






