The GoldFactory gang, a group of cybercriminals known for their banking malware targeting Android devices, has created a trojan targeting iOS users. Once this malware breaches iPhone devices, it can steal biometric data, intercept SMS messages, and allow criminals to empty victims’ bank accounts.
The new iOS malware, dubbed by Group-IB in its February 15 report as “GoldPickaxe.iOS,” is going after iPhone users in the Asia-Pacific (APAC) region, and its reach is expanding. Let’s dive into this malware, what it can do, where it comes from, and how to stay safe.
Deep dive into the new GoldPickaxe malware
GoldPickaxe.iOS follows the international criminal trend of updating existing malware to attack new operating systems, jumping, for example, from Windows OS to macOS or from Android to iOS.
The original GoldDigger malware has been active since at least October 2023 and was coded as an Android trojan. With it, GoldDigger impacted over 50 financial institutions in Vietnam. Now, the group behind the attacks, which is believed to be a well-organized Chinese-language group, has updated its malware to attack iPhone users as well.
Group-IB reports that the new trojan for iOS is constantly being updated to avoid detection and run more efficient attacks.
Here’s what GoldPickaxe.iOS can do
According to Group-IB researchers, the new iPhone trojan is unique in many ways.
GoldPickaxe.iOS can:
- Collect facial recognition data from iPhone users
- Steal identity documents
- Intercept SMS
- Use AI-driven face-swapping services to create biometric deepfakes
- Take control of iPhones to change systems and permissions
- Combine deepfakes with stolen ID documents and intercepted SMS to gain illegal access to iPhone users’ banking accounts
Group-IB shared that this is “a new technique of monetary theft” that they have never encountered before. This claim led many media outlets to report that the malware is the “first iOS trojan.”
Distributing GoldPickaxe.iOS among iPhone users
While the original Android GoldDigger trojan spread across the web using fake sites that impersonated the Google Play Store, the strict controls of Apple prevented the gang from doing the same for iOS.
Initially, the bad actors used Apple’s mobile application testing platform, TestFlight, to distribute GoldPickaxe.iOS. TestFlight is an Apple developer tool that allows app developers to invite up to 10,000 users to test an app and get feedback before releasing the app on the Apple App Store.
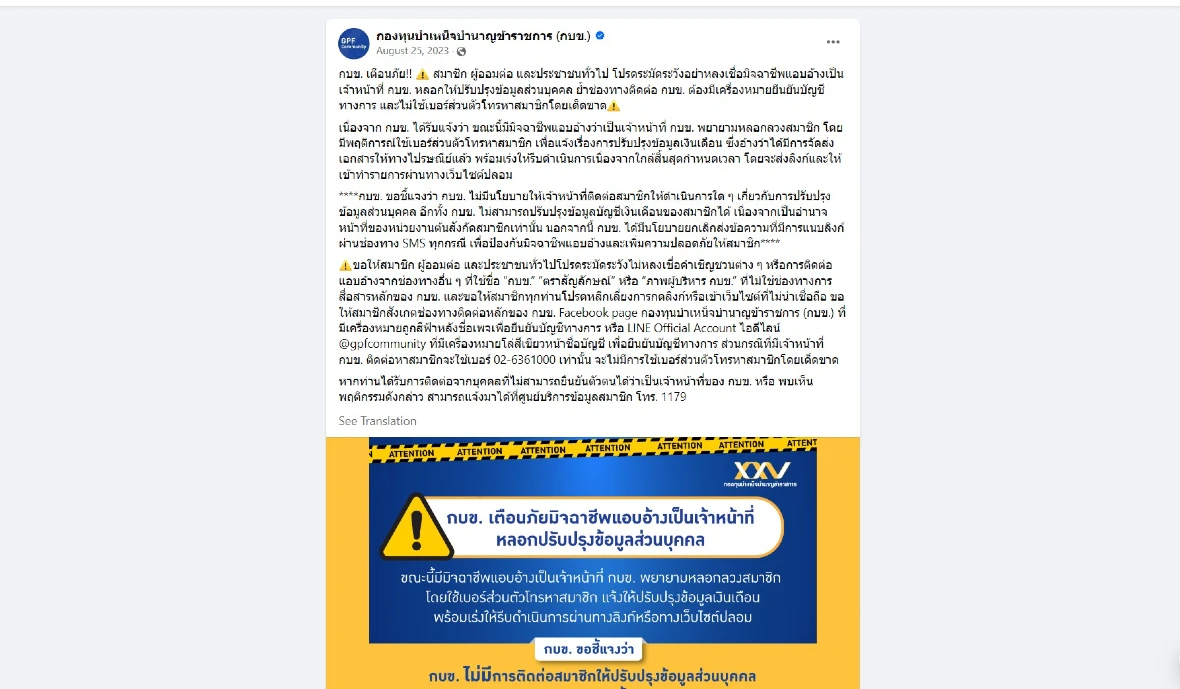
However, Apple rapidly caught on to the GoldPickaxe.iOS malware and shut it down. The gang operating in Asia then decided to change their distribution tactics — opting for smishing and phishing.
A criminal call center and customer support in the heart of Asia
The sophisticated operation uncovered by Group-IB’s investigation proves that this cybercriminal organization is well-funded, organized, and highly active.
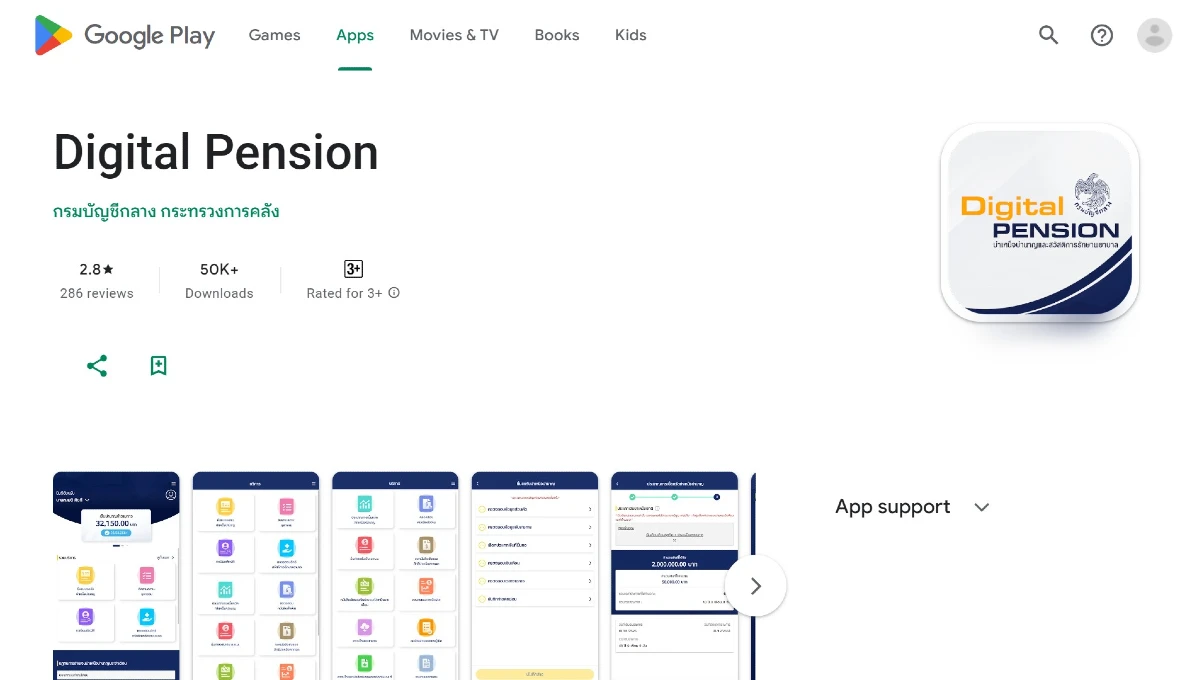
Impersonating government officials and agencies such as Digital Pension for Thailand, other Thai government services, and the Vietnamese government information portal, the GoldFactory gang sends out SMS messages and makes direct calls to potential victims.
Group-IB believes that the criminals might have established a call center to carry out phone calls. The operators of the call center are believed to speak both Thai and Vietnamese.
But the group isn’t just making random calls. They have obtained credible personal information about the victims, proving that they also invest in researching targets before launching attacks.
Once they establish contact, the criminals ask victims to continue the conversation over online messengers, where they redirect them to malicious URLs and guide them through downloading and installing the malware on their iPhones.
A new version of the malware dubbed GoldDiggerPlus even has a fake Contact Customer Service button, which connects victims to live calls with the criminals.
“It is as though the cybercriminals are running a real customer service center,” Group-IB wrote in their report.
Once installed on a device, the iOS trojan acts as a Mobile Device Management (MDM) app, creating new profiles and allowing the criminal gang to gain complete control over a breached iPhone.
Why would cybercriminals want the facial recognition data?
Trojans that are after sensitive data to commit financial fraud or theft usually target credentials — usernames and passwords — and access SMS functions to bypass MFA security guardrails. This is the classic modus operandi of digital financial theft. The question, therefore, arises: Why is this new trojan stealing biometric data and creating deepfakes? The answer: Asian government policy.
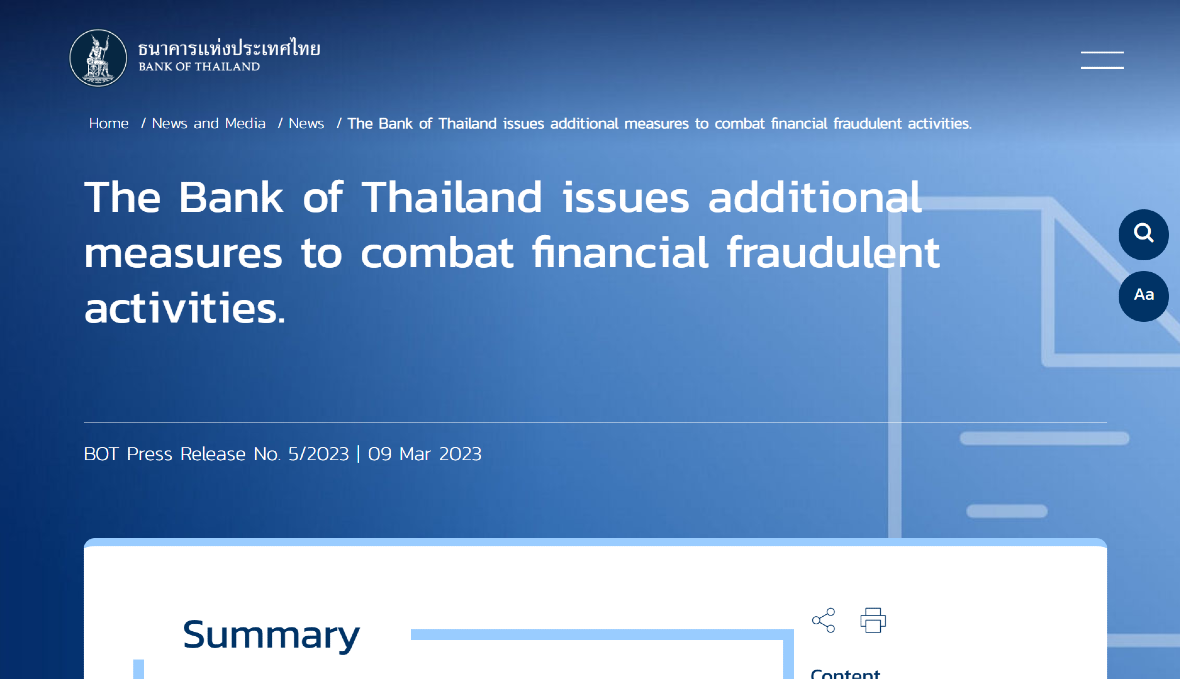
As Group-IB explains, in March 2023, the Bank of Thailand issued instructions for all banks to start using facial biometric verification to confirm users’ identities. The policy change was a response to the rise in one-time-password fraud attacks. In Thailand, every time a person wants to make a transaction of 50,000 baht (approximately $1,430) or more, they must verify their identity with facial recognition. The same security policy is in place for transfers of approximately more than $5,500 per day and raises credit transfer limits on mobile devices to more than $1,382 per transaction.
In Vietnam, where Group-IB believes the gang is also operating, the State Bank of Vietnam (SBV) has also announced a mandatory facial authentication security plan. The plan is expected to kickstart in April 2024.
Facial identification is considered one of the strongest security layers, especially for banks and financial organizations. Internationally, almost every bank encourages its customers to use biometrics.
However, the general global consensus in the banking industry that facial ID provides the highest level of security may need to be reviewed, as malware such as this new iOS trojan (which can also impact Android users) emerge. Additionally, as bad actors leverage the latest in AI-driven deepfakes to launch all types of attacks, trojan biometric stealers seem inevitable.
Will GoldFactory expand internationally?
At the time of this writing, the new iPhone trojan is operating in Thailand and possibly in Vietnam. However, Group-IB is unsure if the malware was developed exclusively by the GoldFactory gang for their own use or if they plan to sell it to other cybercriminal operations in the underground dark web. Both possibilities could trigger a global expansion.
It is also common for cybercriminal enterprises to reverse-engineer a piece of malware once it gains popularity and offers new potential. Black hat hackers often create new versions of malware or integrate the most attractive new features — such as biometric stealers — into their existing portfolio of malware-as-a-service products.
Group-IB says their investigation signals that the Gold Factory gang is “a large group of highly organized criminals” working in areas such as malware development, distribution, and financial theft.
How iPhone users can stay safe against biometric stealers
Whether through fingerprints or facial identification, iPhone users around the world confidently turn to biometrics to secure their phones, apps, data, and accounts. That makes a new malware that can compromise biometric data a serious concern. However, the key to iPhone users staying secure lies in understanding how criminals can execute this attack.
The only reason the GoldFactory gang can steal biometrics is because victims download the malware themselves. Like any other trojan, this malware cannot self-install. It requires that users do it.
Smishing and phishing attacks can be very convincing when the attacker knows who you are, can impersonate officials and government agencies, or offers things like tax discounts. However, they are nothing new. The best line of defense is, therefore, once again, user caution.
If contacted by an unknown source who claims to represent a company, the government, or the organization, iPhone users should hang up and call the legitimate source to verify that the contact is real.
Additionally, monitoring bank statements and accounts is recommended. If users feel that they may have been breached, enabling Lockdown Mode — Apple’s extreme protection for iPhone users — is a good idea. Additionally, they should contact their financial institutions to freeze all of their accounts.
Installing unverified apps on an iPhone or apps that are not available in the Apple App Store is a major risk to security. Signs that your iPhone may have been breached by a trojan include battery drainage, high data usage, slow performance, permission requests and pop-ups, overheating, suspicious behavior, and sudden glitches or freezes.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iOS is a trademark of Apple Inc.