A new piece of Mac malware is spreading online. The malware, discovered by Mosyle, is a browser hijacker that redirects users to phishing sites and other shady domains where users are at risk of having their data and passwords stolen.
We followed up on Mosyle’s investigation and found that about 1,100 ads have been directing users from various countries to the malicious site. All these ads ran in just 2 months. Despite alarms being raised by the cybersecurity community and media, the fake PDF converter site behind it all is still active and online. Let’s dive in.
A browser hijacker, distributed as a free PDF converter trojan, drops big bucks on online advertising
Before we go into what we found while following up on this new malware campaign discovered by Mosyle, let’s look at how it affects Apple users.
This new malware, dubbed JSCoreRunner, is a browser hijacker. Once installed on your Mac, it will change your search engine settings. The malware will set a fraudulent search provider as your default site and direct you to it every time you open the browser or a new tab.
Browser hijackers are more than just annoying. According to Mosyle, this malware will also direct you to phishing sites and promote malicious search results. This can lead to personal data and/or financial theft.
How the new macOS browser hijacker infection chain unfolds
To understand how to stay safe, let’s look at how this malware’s chain of attack develops from an Apple user’s perspective. The following is a step-by-step simulation:
- You need to convert a PDF on your Mac. You go to Google and type in “Convert PDF on Mac for free.”
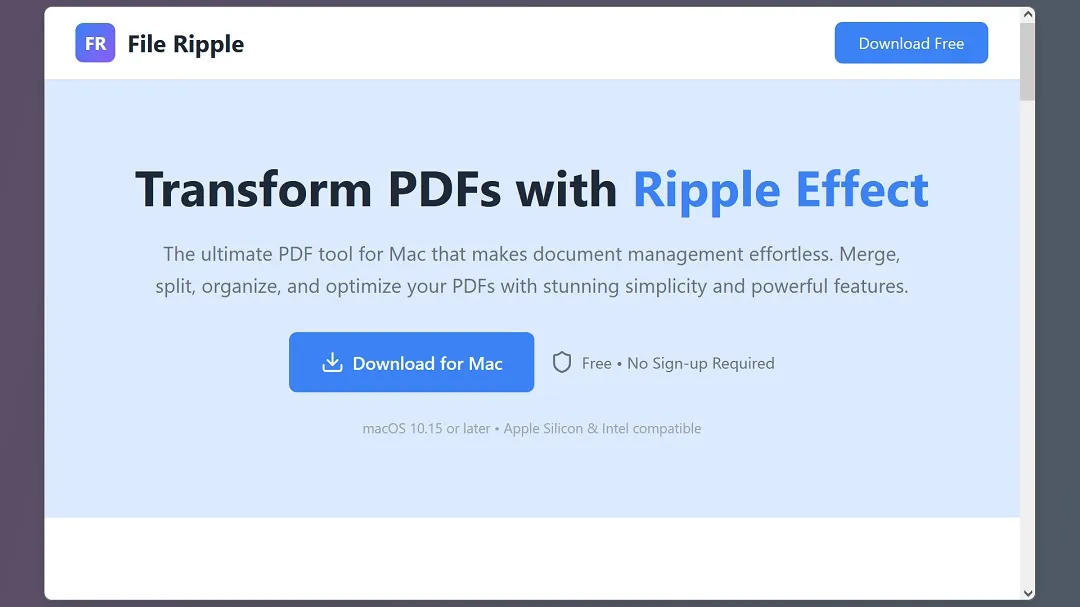
- Google’s search results show you ads, or sponsored top-of-page results. One or more of these ads directs you to the site fileripple[.]com. (The site and the ads are malicious.)
- Once you click on the ad, you are directed to fileripple[.]com/ripplePDF. While the site appears to be a normal, legit PDF converter tool, it is not.
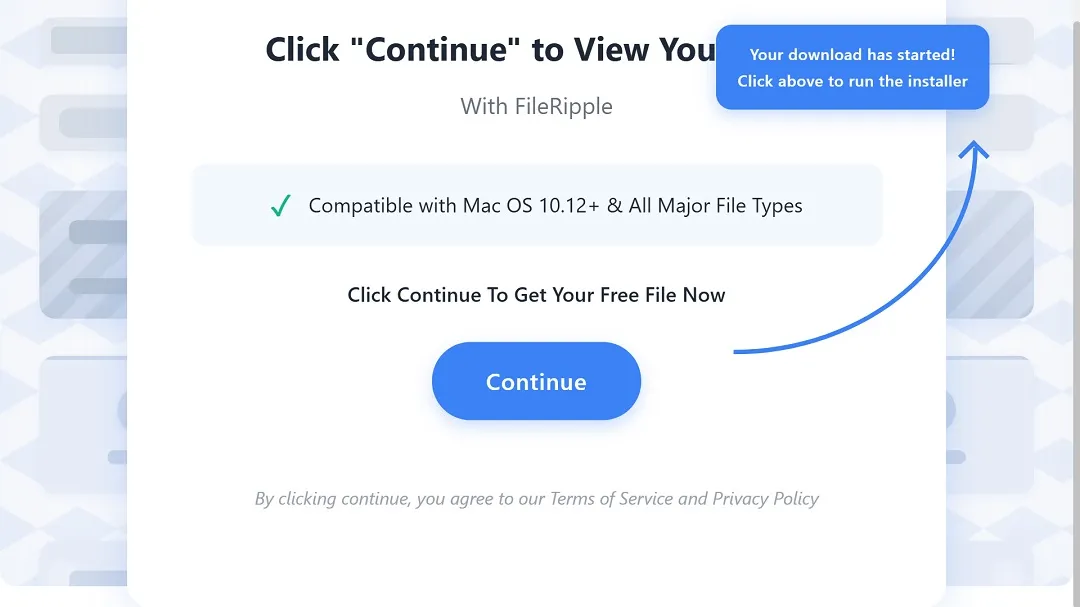
- As shown in the image below, the site has a full window banner and a button that reads Continue. Clicking Continue, Download Free, or Download for Mac will trigger the download of a file named FileRipple.pkg.
- If you run the installation of the file FileRipple.pkg, you will get what also looks like a legit, free PDF software converter. However, this software will trigger the concealed download of another file called Safari14.1.2MojaveAuto.pkg in the background.
- Safari14.1.2MojaveAuto.pkg is a type of browser hijacker malware. It downloads as a second-stage malware, unknown to the user, and bypasses Gatekeeper, Apple’s built-in cybersecurity tool.
- The browser hijacker will then proceed to target your Chrome browser and modify your browser data.
“(The malware) targets and hijacks a user’s Chrome browser by altering its search engine settings to unknowingly default to a fraudulent search provider,” said 9to5mac, sharing the exclusive investigation they got from Mosyle in their report.
“This opens users up to keylogging, redirected searches to phishing sites, and promoted malicious search results, ultimately resulting in any sort of data and/or financial theft,” the Apple-focused media reported.
We took a closer look and found several unusual red flags linked to this campaign
Following up on this report, we conducted some basic investigations and checkups. We were surprised to find some notable and unusual traits and elements in this campaign.
The first thing that caught our attention was that the site fileripple[.]com was still active on the public-facing web. This is uncommon, as malicious and/or fake sites tend to be taken down days after the cybersecurity media sounds the alarm on sites that are scamming users.
Someone paid for about 1,100 malicious ads that ran for 60 days
Going further, we decided to head to Google’s Ad Transparency Center. There, we typed in the domain fileripple[.]com in the search bar and discovered that about 1,100 ads ran from July to August 2025, directing users to this malicious site.
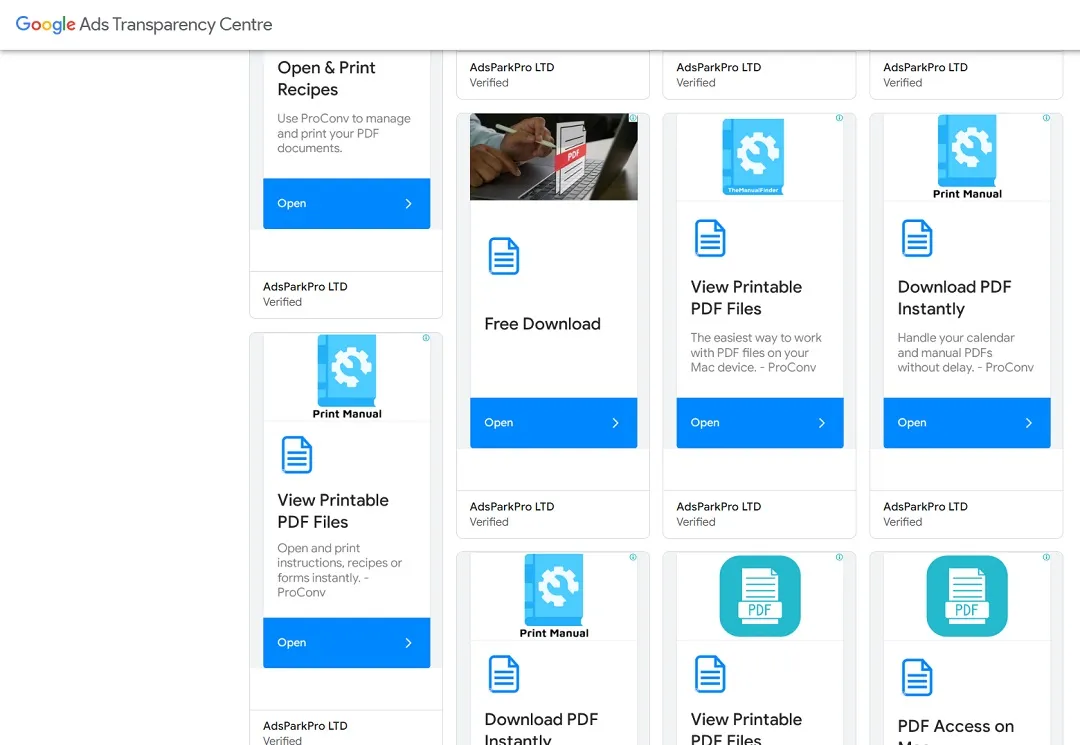
The volume of ads, about 500 ads in July and 600 ads in August, is also unusual. While we have seen cases of malvertising before and ads that abuse the Google Ads platform, the sheer volume of ads we found for such a short period is highly uncommon.
![A screenshot of the advertiser found by a search for the site fileripple[.]com.](https://moonlock.com/2025/09/Ad-distributor.webp)
WHOIS information and IP traces of domains linked to this campaign and for fileripple[.]com turned out to be a dead end. This is what we expected, as scammers know how to cover their tracks well.
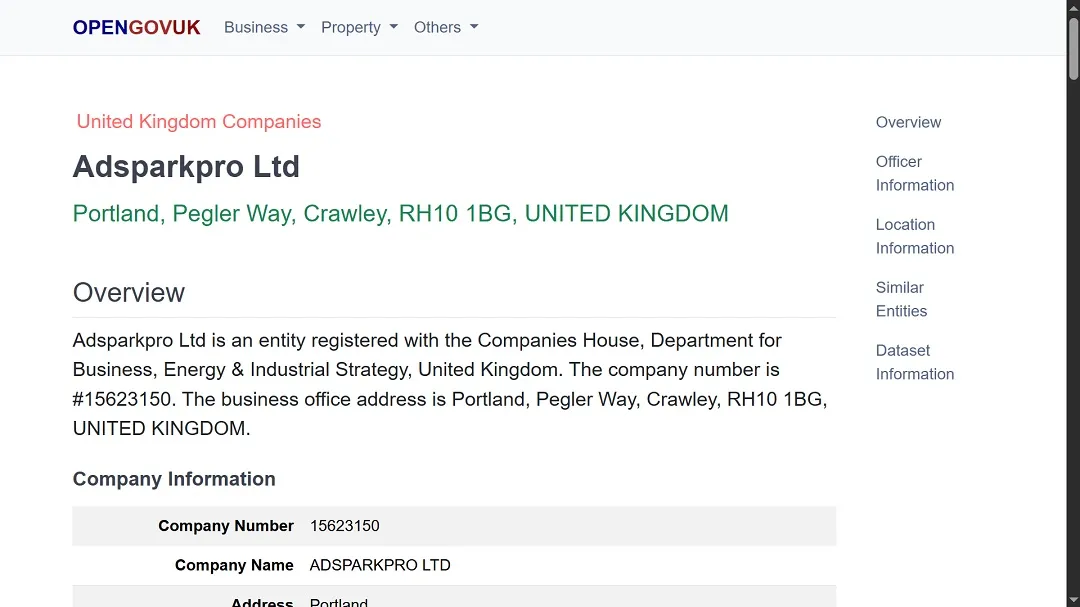
However, after checking the name of the company listed as running these ads on the Google Ads Platform, we noticed that the company was registered in the United Kingdom very recently. The record indicates registration in April 2024.
Are government public records being abused by scammers?
Companies registered in the UK list a lot of information and documents publicly online. Anyone can access this information. This raises the question of transparency versus risk. Can cybercriminals and scammers abuse government public data to, for example, create fake accounts on Google Ads to verify themselves?
We also found 3 websites using the same UK company name, all working in online advertising. One of the sites was flagged by Google and Tor as dangerous, as the image below shows.
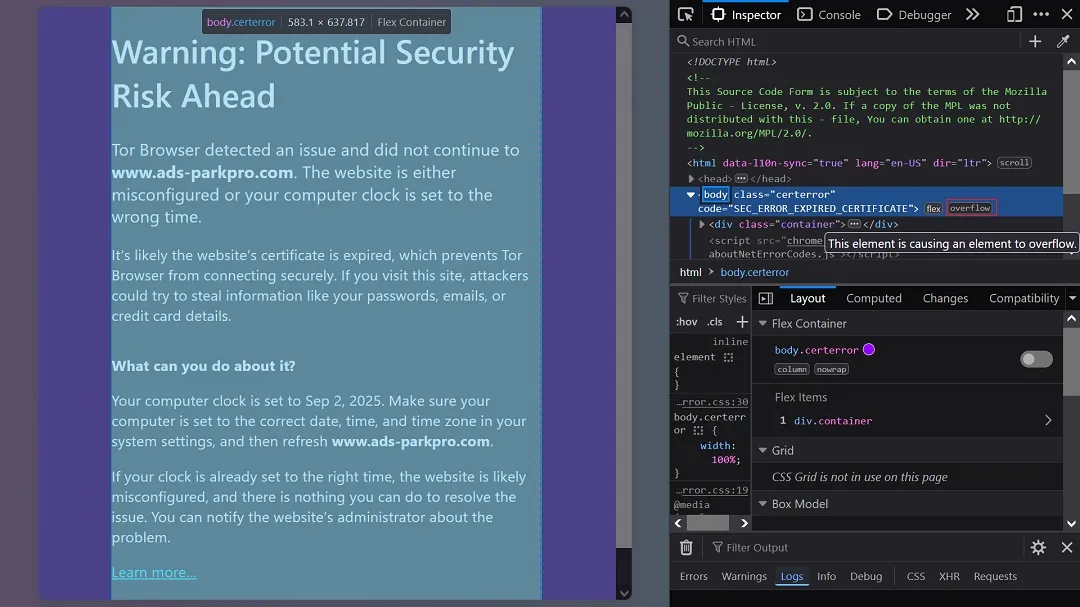
By ignoring the browser flag — which we advise users not to do — we reached the website shown in the image below. In its Contact section, the site displays the same contact data as that of the UK company. The information is also available as a public government record.
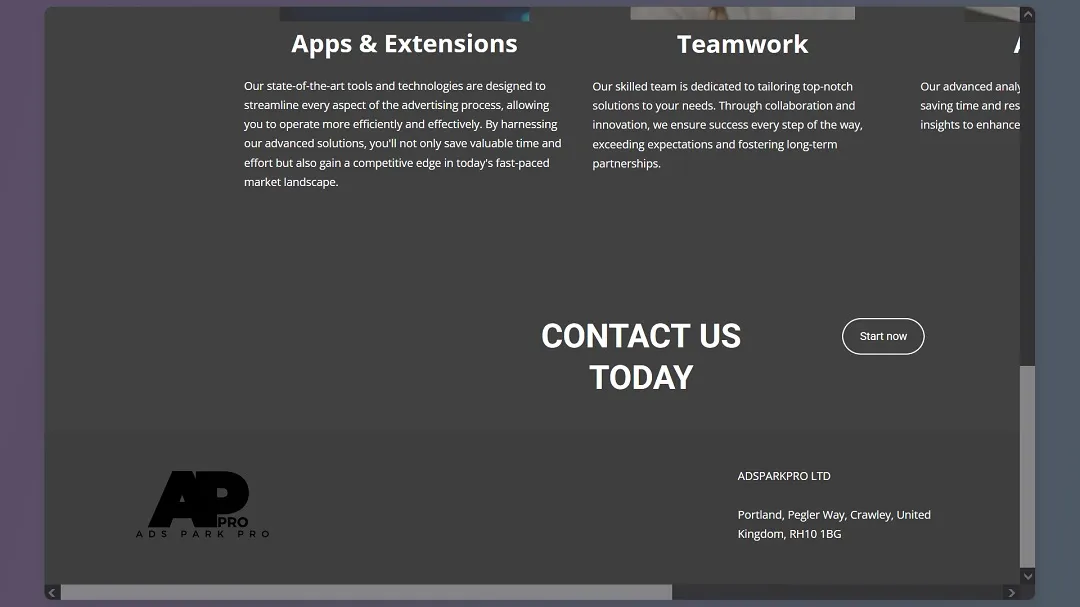
Another site led us to what appeared to be the legitimate site of the company. At this time, however, we cannot verify which of the 3 sites actually belongs to this UK company.
It is worth noting that the UK government’s public data lists a Ukrainian national as the director of the company that appears to be running the ads on Google.
However, this does not imply attribution. Scammers and threat actors usually cover their tracks well, and attribution-misdirection tactics like leaving fake digital trails are common tactics used to throw cybersecurity and law enforcement agents off their tracks.
Spoofing a UK entity not only inspires misplaced trust among Apple users but might make it harder to trace or prosecute, especially if the real operators are in a completely different region.
Other than the use of the name of the company (AdsParkPro) to run the fake ads on the Google Ads platform, we found no connection whatsoever linking the company with the scam or the browser hijacker malware being distributed.
The company also seems to have run no ads on Google until the past 2 months, when it became supercharged and highly active, with 1,100+ ads. These appear to be clear signs of spoofing, impersonation, and account takeover, rather than attribution.
It’s up to local law enforcement to investigate this case and reach a conclusion regarding who is behind this malware distribution campaign.
What and who are the fake PDF scammers after?
If you are an Apple user, you might want to know what these types of free, fake software scammers are after. In this specific campaign, the answer is simple. They want your personal and financial data.
Users in the following countries have been exposed to this campaign:
- United States
- France
- United Kingdom
- Germany
- Italy
- Canada
Please note that users in other countries may have been exposed as well.
As far as we can tell, users from the following countries and regions were not being served this malicious ad:
- Asian countries (including Japan, Laos, and China)
- Russia and Belarus
It is unknown how many users have clicked on this ad and downloaded the malware on their Macs.
This campaign shows how scammers target Apple users by weaponizing ad ecosystems to funnel victims to malicious payloads. By flooding Google Ads with hundreds of instances of near-identical creative, they maximize click-through before the fake sites are taken down or flagged by technology companies.
How to stay safe from Mac browser hijackers
As always, we have some tips for Mac users to stay safe from browser hijackers and other types of malware:
- If you don’t already have an adblocker, now is a good time to get one. The same goes for anti-malware software.
- Do not click on any ad without verifying its authenticity. Remember, scammers and cybercriminals abuse Google Ads and other ad platforms to reach you.
- Do not click on or download suspicious free converters or similar programs. Admittedly, this tip is a tricky one. To find safe options, try using the official Apple App Store if you are looking for a file converter or any other software.
- Black hat hackers have at their disposal many stealers and other types of malware that can break into Chromium-based browsers like Google Chrome, Microsoft Edge, Opera, Brave, and Vivaldi. We recommend non-Chromium-based browsers like Tor, DuckDuckGo, Firefox, and Safari. Because these browsers have a higher degree of privacy and stronger security features, criminals have a harder time hacking into them.
- Save as little information as possible in your browser. This is another tough one because saving data on a browser is very convenient.
- Enable multi-factor authentication (MFA), pins, and biometrics on all your accounts and on your Mac if possible.
Final thoughts
The rate at which the Mac community is being targeted by bad actors has reached unprecedented new levels.
In the past months, we have reported almost every week on a new malware or a new malware distribution campaign targeting Apple users. While the threat campaigns we witness emerging are not technically sophisticated, and any users can detect them if they know what to look for, it seems macOS malware in the wild has become the new normal.
Should Apple users lose sleep over this new macOS malware? Not really. But keep your guard up. All it takes for scammers and phishers to take the big prize is for you to click on the wrong button.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






