If you are one of the millions of people who use Discord, you’ll want to read this report to learn all about a new piece of malware and how cybercriminals are using it to potentially steal your information.
On October 16, Trend Micro revealed the findings of their latest investigation. According to their report, criminals are leveraging Discord’s own network to launch attacks using a new infostealer called Lumma Stealer. The bad actors have also created bots that abuse Discord’s APIs to steal private data.
How Discord attackers abuse CDNs and use malicious bots
Lumma Stealer, written in the C programming language, is not new. It was first detected in August of 2022. In early 2023, it was reported to be targeting YouTube users in spear-phishing email attacks. But now, Lumma Stealer is abusing Discord’s content delivery network (CDN).
The use of CDNs dates all the way back to the earliest days of the internet. These networks bring content and data closer to users. But this new malware uses Discord’s CDN to host Lumma Stealer and spread it.
Imagine the Discord CDN network as a group of small data centers spread around the world. When a Discord user accesses the app, instead of connecting to a large data center operated thousands of miles away, it pings on the CDN.
Websites and mobile applications save critical data on CDNs to better distribute traffic and user requests, avoid delays in data transfers, and increase performance. In this case, attackers have found a way to abuse the Discord CDN network to host the Lumma Stealer malware and launch attacks on users.
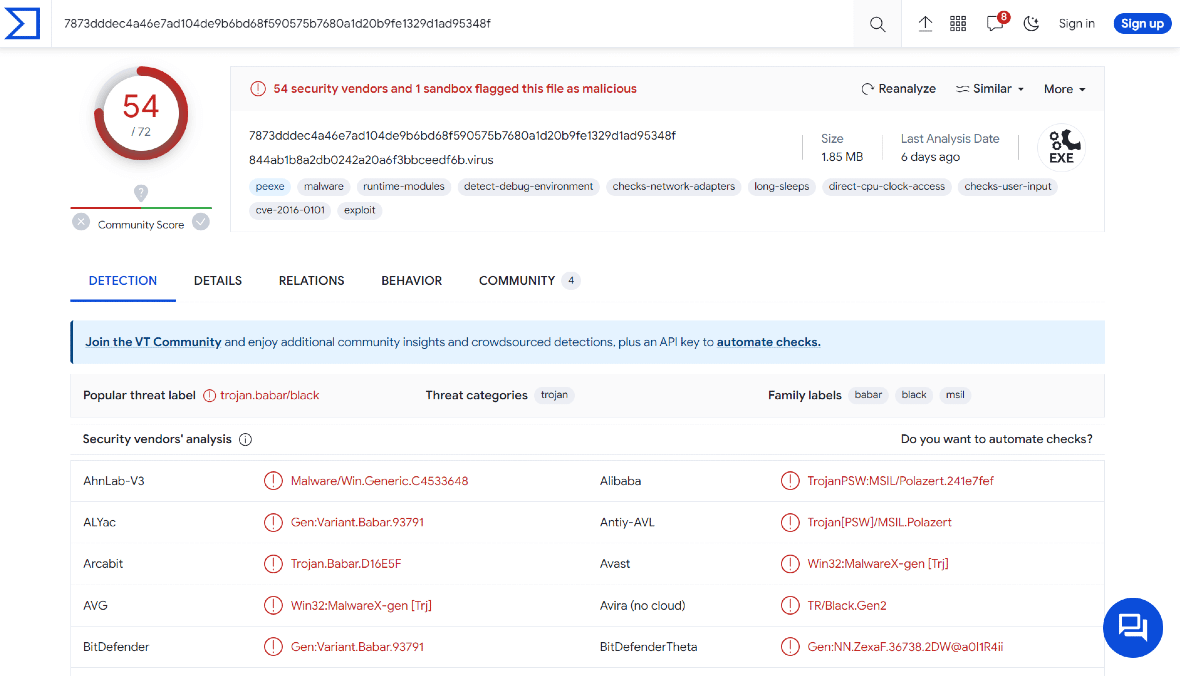
Additionally, criminals are also using Discord’s application programming interfaces (APIs). An API is a type of software that allows two applications to talk with each other. These are critical in cybersecurity, as they are considered gateways into the apps themselves. If an API is compromised, attackers can steal data, hide malicious code in traffic, and execute a wide range of cyberattacks.
Lumma Stealer attackers are using Discord’s own APIs to create bots that “talk” with the malware and control it remotely. Additionally, some of these bots transfer stolen data to private Discord servers or channels.
Be wary of offers for cash or Nitro boosts in exchange for game reviews on Discord
In this new cyberattack on Discord, Lumma Stealer operators are targeting users randomly. The attack begins when they send a direct message to the victim. Attackers are proliferating through the messaging platform using compromised Discord accounts and contacting those accounts’ connections.
Discord is a messaging app ripe with online gamers, content creators, and streamers. According to Trend Micro, the attackers tell victims they are looking for help for a project and will offer them $10 or a Discord Nitro boost in exchange for the work. Nitro boosts — also known as Server Boosting — are very popular among the community, as they allow users to access special features and additional perks that benefit these types of users.
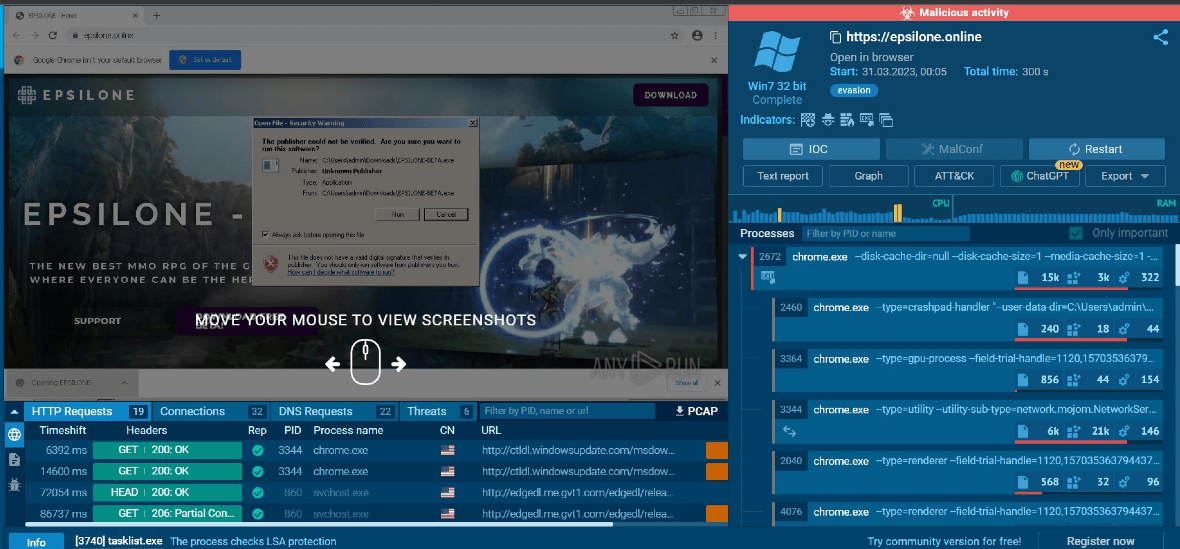
Attackers will tell victims that the $10 or the Nitro boost is an easy win. All they have to do is play a game for a couple of minutes and review it. When a Discord user agrees to the scam, the attacker sends them a file to download. Once the download begins, multiple malicious files are downloaded into the victim’s computer. Attackers are also directing victims to malicious gaming websites.
What we know about Lumma Stealer
Like many other infostealers, Lumma Stealer is being promoted and sold on the dark web and on underground forums. The malware can be purchased under a malware-as-a-service (MaaS) model. The basic plan costs $250 per month.
With this basic plan, cybercriminals can view and upload logs and access log analysis tools. If they go for the professional plan, priced at $500 per month, they will also be able to use traffic analysis tools. Lumma Stealer is offered in two more plans, the Corporate plan for $1,000 and the Ultimate Source plan for $20,000 per month, which includes proactive defense bypass services to avoid detection, in addition to giving users access to the source code of the infostealer, as well as the right to sell it.
Lumma Stealer’s log, traffic, and defense bypass features can help criminals:
- Identify valuable data and systems to target
- Identify vulnerabilities in systems to exploit
- Track the activity of their victims to learn more about their routines and habits
- Cover their tracks and evade detection
- Bypass antivirus and antimalware software, intrusion detection systems (IDS) and intrusion prevention systems (IPS), firewalls, network segmentation, and more
- Help them steal information and data
Final recommendations
Due to the nature of this specific attack, Discord users should be extra cautious when talking to strangers on the platform, clicking on links, or downloading files from unknown sources. Additionally, knowing how infostealers work can help prevent attacks.
To stay safe, users should create strong passwords and enable multi-factor authentication. Always keep your software up to date, and use a firewall and trusted antimalware software.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Discord Inc. Discord is a trademark of Discord Inc.






