The AMOS Mac stealer is back. This time, the malware is impersonating the popular screen recorder Loom, which has over 20 million users and is loved by some Apple users.
In a new investigation, Moonlock Lab researchers found that a sophisticated cybercriminal operation linked to Russia was abusing the Google Ads platform. Their aim was to lure potential victims into downloading a malicious version of Loom from a fake site.
New AMOS stealer variant found in the wild
On August 1, Moonlock Lab revealed that bad actors potentially linked to a threat group called Crazy Evil are distributing a variant of the infamous AMOS Mac stealer. The group is creating and running fake campaigns on Google Ads, impersonating Loom. When victims click on the Google Ad, they are redirected to smokecoffeeshop[.]com. This, in turn, automatically loads another URL address.
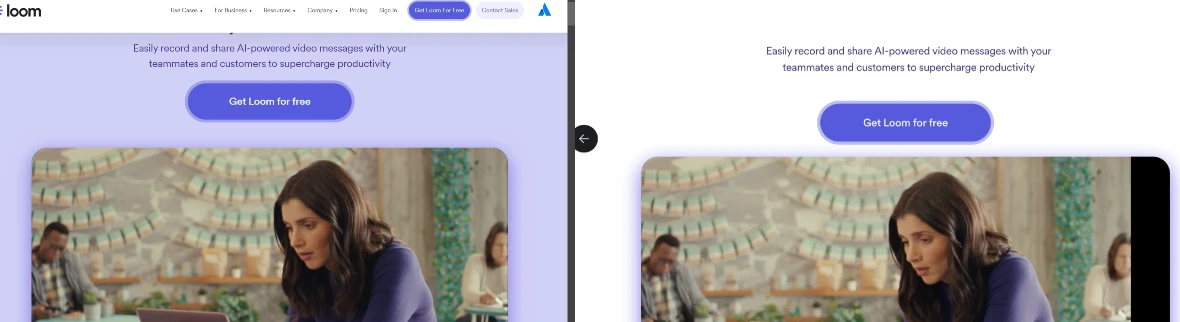
Victims end up on a fake website almost identical in design to the legitimate Loom website (see image below). Any user who clicks on the download button will download a complex version of the AMOS stealer.
The AMOS stealer has been updated and improved over time. The reason why so many different pieces of AMOS malware have been discovered in the past year and a half is that this malware is rented out in the underground criminal market. The AMOS stealer can cost up to $3,000 per month, but for cybercriminal organizations, it’s worth every cent.
The AMOS stealer, also known as Atomic Stealer, can extract specific information and files from breached computers. It also targets browser data, user history, credentials, and passwords. It can also empty crypto wallets and much more.
Cloning apps to bypass Apple’s App Store security
Moonlock Lab found that this new version of AMOS has a novel capability. The malware can replace a specific crypto wallet app with a clone and easily wipe out victims’ e-wallets. This ability has never been reported in a version of AMOS before and represents a significant leap forward.
Moonlock found that this new version of AMOS replaces and clones the app Ledger Live. Ledger Live gives users access to crypto, NFTs, and DeFi. This app is also loved by some Apple users. It has more than 10,000 positive ratings, averaging a score of 4.9 out of 5 stars, on the Apple App Store. Plus, it’s free.

If this new version of AMOS can replace Ledger Live with a fake malicious clone, it could do the same with other apps.
In fact, by digging deeper into malicious functionalities, Moonlock’s investigation also found that these threat actors had created fake versions of other popular applications. The cloned apps include Figma, TunnelBlick (VPN), Callzy, and an intriguing case named BlackDesertPersonalContractforYouTubepartners[.]dmg.
The tactic of cloning an app after a breach could be a new technique that seeks to bypass the strong security controls of Apple’s App Store. These security controls are in place to prevent bad actors from uploading malicious apps to the store. By infiltrating a device and cloning apps, cybercriminals seem to be adapting and moving in a new direction.
Going after gamers and younger targets
The .dmg file mentioned above, BlackDesertPersonalContractforYouTubepartners, implies a reference to Black Desert Online, a popular massively multiplayer online role-playing game (MMORPG).
The gaming community, heavy users of crypto and digital assets, is often targeted by cybercriminals. Attackers commonly post fake recruitment ads or job opportunities on gaming platforms. Using social engineering, they trick gamers with fake rewards.
Who is Crazy Evil?
Moonlock Lab researchers concluded that the group Crazy Evil may be behind the campaign.

“Crazy Evil seems to be a well-organized group that communicates with its partners and recruits via a Telegram bot,” the Moonlock Lab report reads.
Crazy Evil is not a known cybercriminal group. The lack of information about this group, and its active Telegram channel, could imply a couple of things. It’s possible that this is an entirely new group. Alternatively, Crazy Evil might be a rebranded group or an alias of an existing criminal organization. Or the name is just a misinformation tactic.
Moonlock Lab linked Crazy Evil to this new campaign through darknet analysis. They found a recruitment ad that called for individuals to join a team that used the same AMOS stealer posted by Crazy Evil.
The recruiting ad spoke about the features of this new AMOS stealer, highlighting that it could replace “Ledger” on macOS. This means that Crazy Evil is distributing the same AMOS version, which was discovered in the wild, impersonating Loom.
Analyzing the fake Loom threat
Further analysis “of samples with functionality similar to the fake Loom threat” also revealed an IP address — 85[.]28[.]0[.]47.
![A screenshot of VirusTotal IP scan linking Gesnet[.]ru.](https://moonlock.com/2024/08/11_virustotal.webp)
When scanned on VirusTotal, the IP address 85[.]28[.]0[.]47 flagged 93 files marked as malware in the Memory Pattern Parents field. Moonlock Lab reported that the IP had a high malware association linked to a Russian governmental entity.
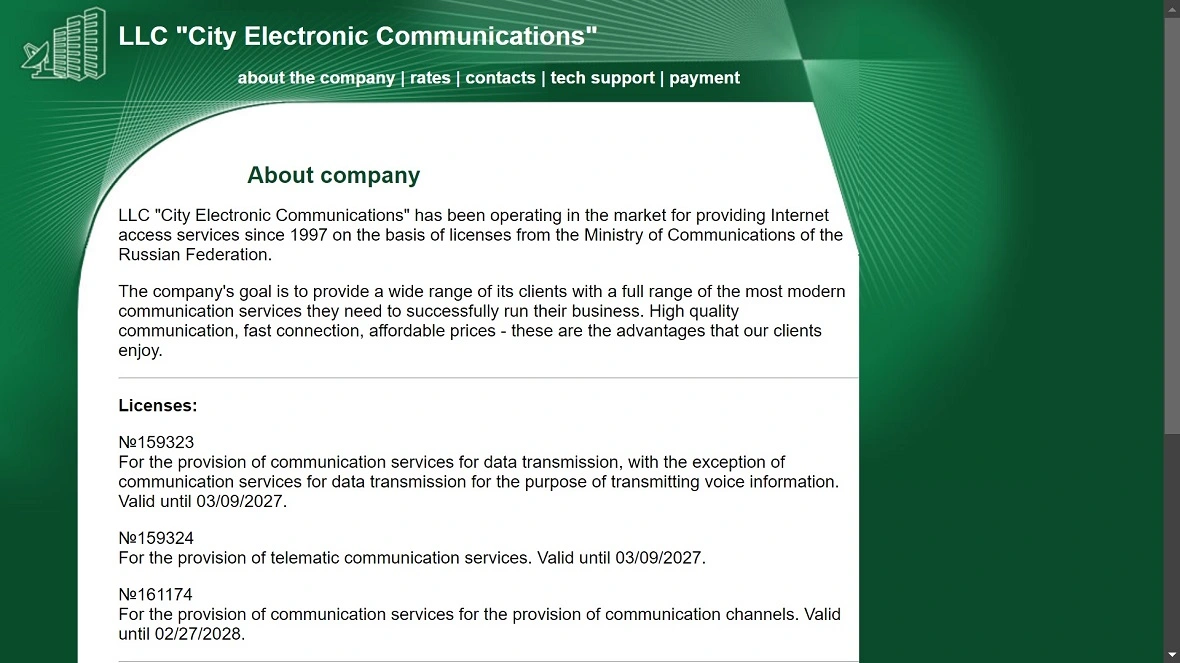
The company Gorodskaya elektronnaya svyaz Ltd (Gesnet[.]ru) is listed as the ISP provider in the VirusTotal scan report. Gesnet[.]ru is a Russian company that appears to be an internet service provider (ISP). Based on the limited public information available, it can be assumed that it operates a significant network with multiple IP addresses and autonomous systems.
![A screenshot of the Gesnet[.]ru site.](https://moonlock.com/2024/08/gg.webp)
While this does not mean Gesnet.ru is behind this campaign — it could be providing a service to bad actors without knowing it — it is interesting to note certain peculiarities about the company, such as:
- ISP: Their primary business seems to be providing internet connectivity.
- Russian-based: The company is registered in Russia and operates within the country.
- Network size: They have a substantial network infrastructure, as evidenced by the number of IP addresses and autonomous systems associated with them.
- Limited public information: Despite the size of their network, there is a scarcity of publicly available details about the company’s ownership structure, financial information, or specific services offered beyond basic internet connectivity.
The ISP market in Russia is not “officially” government-controlled. The unofficial version, of course, is a different story.
Additionally, strict laws make the ISP business in Russia very difficult to understand and completely deprived of transparency for foreigners.
The bottom line: How to stay safe
For Apple users, it is important to remember that your Mac is vulnerable to the AMOS stealer, and this new version is much more dangerous than the previous ones.
The malware is being spread through popular apps and may present itself to you as an app, software, or platform that has not been identified in another AMOS report. Therefore, be particularly cautious about what you download. Double-check URLs, and do not click on Google Ads. Only download software and apps from the official Apple App Store.
Additionally, if you are into gaming, take additional steps to protect yourself. For one, have your guard up at all times. Gaming communities are fun, but that doesn’t mean you should trust strangers. If anyone messages you offering something in exchange for a reward, like trying out a new game, report, block, and delete the message.
It is highly likely that this is not the last time we will hear from the AMOS stealer. However, this report will hopefully help prevent it from breaching your Mac the next time it emerges from the shadows of the digital criminal underground.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. or Google LLC. Mac and macOS are trademarks of Apple Inc. Google Ads is a trademark of Google LLC.