Infostealers are on the rise and are fast becoming one of the most popular types of malware in the cybercriminal´s toolkit for 2023. Infostealers can breach your Mac, iPhone, or iPad without you ever knowing it and can run in the background, sending your information to attackers.
Apple deals with infostealers and other threats using several technologies. This includes encryption, user access authentication, and the built-in malware detectors and blockers Gatekeeper and XProtect. However, according to new reports, a new infostealer is capable of bypassing Apple’s security.
On September 11, SentinelOne reported that some variants belonging to the family of the MetaStealer malware were not detected by XProtect.
How MetaStealer is different from other attacks
While this year has seen a significant rise in infostealers targeting macOS, including MacStealer, Pureland, Atomic Stealer, and RealStealer, they usually do not target Mac business users. Attackers using MetaStealer, however, seem to be targeting small- and medium-sized businesses using macOS to run their operations.
Here’s how the attacks work:
- Criminals posing as potential clients contact business owners.
- Attackers convince the victims to download a file to their Mac computer using social engineering techniques.
- Once the fake file is downloaded to the Mac computer, the infostealer is installed and begins to work in the background.
How does MetaStealer target business owners?
For Mac business owners, getting malware from a client request is perhaps the last thing they expect. Unfortunately, this is exactly what is happening.
SentinelOne’s investigation revealed that attackers are sending password-protected .dmg files — a type of file used to compress several files, even installation files, on Mac computers.
MetaStealer malware may be hidden in files with names such as:
- Advertising terms of reference (MacOS presentation).dmg
- CONCEPT A3 full menu with dishes and translations to English.dmg
- AnimatedPoster.dmg
- Brief_Presentation-Task_Overview-(SOW)-PlayersClub.dmg
- Contract for payment & confidentiality agreement Lucasprod.dmg
MetaStealer has also been found hidden in Adobe files.
How to protect yourself from MetaStealer
While XProtect cannot detect all versions of MetaStealer, it can detect some of them. Therefore, it is important to make sure your Mac has the latest XProtect update.
XProtect uses YARA signatures, a tool used to conduct signature-based detection of malware, which Apple updates regularly. And because Apple is constantly monitoring for new malware infections and strains, new update signatures are expected.
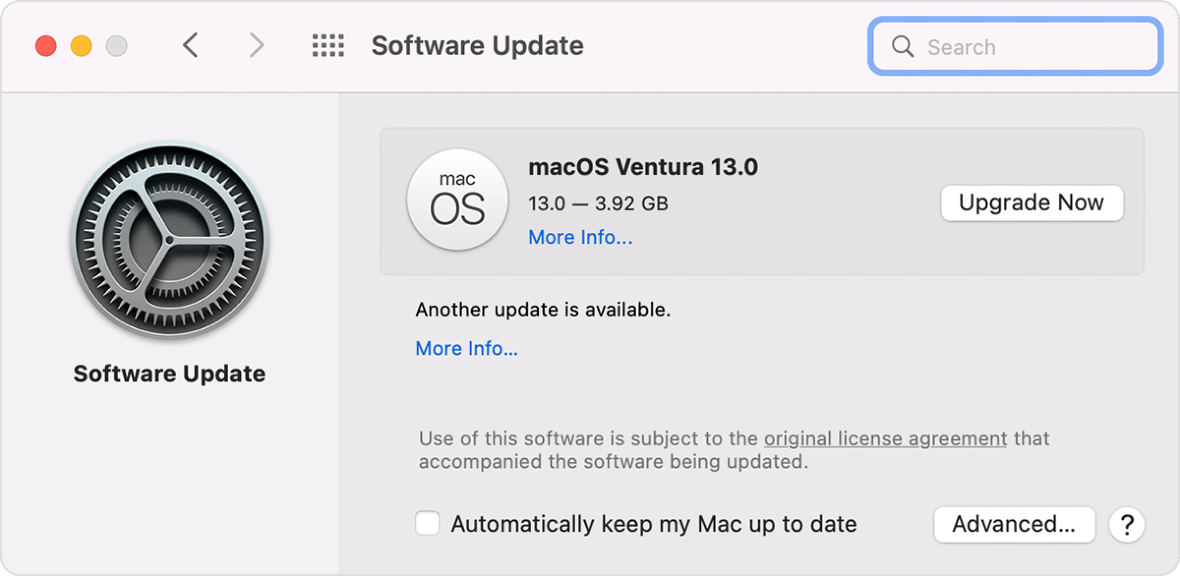
XProtect updates in macOS are automatic, and automatic updates are turned on by default. Still, it’s a good idea to double-check that these updates are enabled on your system.
To ensure that automatic security updates are enabled on your Mac:
- Navigate to the Apple menu.
- Select System Preferences, then Software Update.
- Click on Advanced at the bottom right.
- Make sure the box for “Install system data files and security updates” is checked.
Security experts also recommend having professional and trusted anti-malware detection software installed and running on your Mac. Anti-malware software should prevent MetaStealer from being installed and flag a file or an attachment if it is suspicious.
The best defense against malware is to be knowledgeable and vigilant when it comes to emerging cybersecurity threats. And naturally, Mac business users should be extremely cautious when downloading attachments sent over email, messages, or other platforms.