In the old days, you would open a webpage, and a fake virus scanner would pop up claiming you had been infected. This was way back in the late 90s. Strangely enough, this type of scareware tactic is still around and targeting Mac users.
While scareware cyberattacks have evolved and become more sophisticated, the concept remains the same: use fear to trick a user into taking an action they would not usually take.
LayerX Labs has been tracking one of these campaigns. So, let’s get straight into it.
LayerX uncovers a highly sophisticated scareware browser attack
Recently, LayerX Labs reported that a new cyber threat campaign had shifted from targeting Windows users to targeting Mac users. The campaign is a web browser fake notification attack that attempts to trick users into giving away their credentials with the excuse that their Macs have been locked due to a security threat.
Cybercriminals shifted from targeting Windows to macOS rapidly, a sign that their capabilities are advanced. The shift toward Macs happened when Microsoft, Chrome, and Firefox rolled out security patches to shut down the attackers.
“Within 2 weeks of Microsoft rolling out the new anti-phishing defenses, LayerX began observing attacks against Mac users, who — apparently — were not covered by these new defenses,” LayerX said.
The bad actors behind this campaign responded to the updates by pivoting to Safari and Macs. This threat has been active for at least a couple of months.
LayerX warned that malicious webpages and the attackers’ infrastructure are still online and operating.
This is what a modern macOS scareware browser attack looks like
So, how does this cyberattack look from the user’s point of view? As seen in the image below, the attack is self-explanatory. The user visits a malicious site, and the fake system notifications pop up on the user’s Mac with a fake “Virus Alert.”
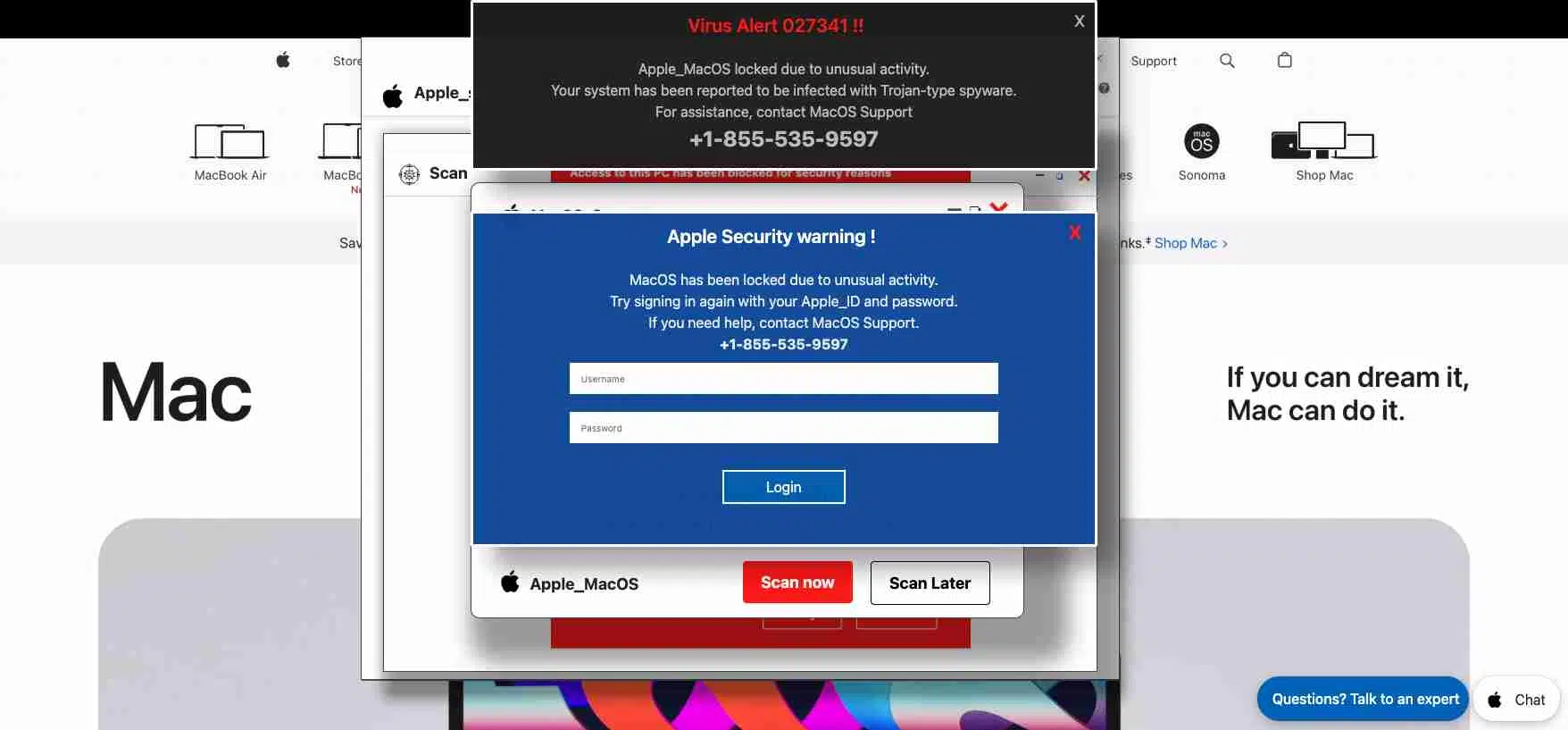
Interestingly, this threat locks the Mac environment and then asks the user to enter their username and password, impersonating Apple. Locking the screen and making a macOS freeze is a unique innovation that adds a level of pressure to victims.
To lure victims, the threat actors abuse the legitimate Windows[.]net infrastructure. Their intention is to create the illusion of legitimacy when users visit these malicious web pages.
“Code adjustments specifically target macOS and Safari users by leveraging HTTP OS and user agent parameters,” LayerX said.
LayerX’s investigation found that victims were redirected to the phishing pages via compromised domain “parking” pages. The malicious pages do rapid redirects through multiple sites to inadvertently lead victims to the attack page.
Apple security guardrails and browser technologies are not optimized to deal with this type of threat. LayerX reports that attacks are bypassing Mac security and even targeted individuals who use Secure Web Gateways (SWG).
Key takeaways that spell danger for macOS users
According to LayerX, there are several key takeaways from this attack:
- Mac and Safari users are now prime targets.
- This level of sophistication of threat is high compared to similar campaigns targeting macOS users.
- Cybercriminals display high adaptability and the speed to pivot, modifying their attack techniques dramatically when security patches are released.
- A resurgent wave of attacks using this infrastructure is expected.
“Based on the longevity, complexity, and sophistication displayed by the actors behind this attack campaign thus far, we suspect that this is just a first response by them, as they adapt their attacks to new defenses,” LayerX said.
Browser attacks have surged by a staggering 140%
Unfortunately, this attack is not an isolated incident. It is part of a trend that has gone from niche to mainstream to massive.
The recently released Menlo Security report, “Browser Security Report: AI-Powered Attacks Surge,” found a 140% increase in browser-based phishing attacks in 2024. Most of these (130%) are zero-day attacks that leverage vulnerabilities in operating systems and other software. While these can be patched by vendors like Apple and Microsoft, it’s an eternal battle between security teams and cybercriminals that never ends.
Menlo Security says that cybercriminals are impersonating major brands like Facebook, Microsoft, and Netflix.
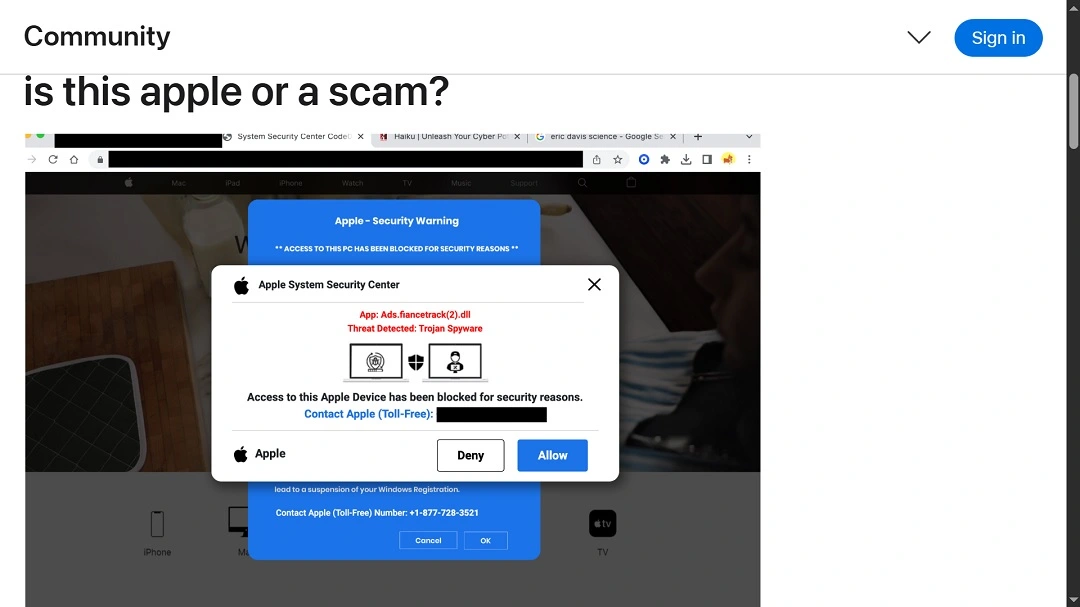
Fake sites built to lure victims have also been found to offer malicious AI resume generation services or PDF documents where malware or malicious scripts are embedded. We recently reported on fake document converter sites and how these criminals attracted the attention of the FBI.
Menlo Security detected more than 752,500 browser-based phishing attacks and 170,000 zero-day phishing attacks. In 1 in 5 of these attacks, some form of evasive technique is displayed that can bypass most network and endpoint security technologies.
So, what can users do to stay safe?
If firewalls, your macOS, and traditional browser security tech cannot flag or shut down these cyberattacks, what should you do?
First of all, a trusted, industry-leading anti-malware solution can help you stay safe. These types of software are developed to go the extra mile, so even if browsers are not flagging malicious sites, anti-malware tech can add a new layer of security and get the job done.
Second, you are the final line of defense in your cybersecurity. This does not mean that these types of threats should scare you or drive you into a panic attack when they happen. Most of these threats go nowhere if you restart your Mac or ignore the request for sensitive information. Entering your username and password is the last thing you want to do.
Finally, staying up to date with cybercriminal trends gives you a vital advantage. If you know what you are in for, the chances are you can avoid falling into these scareware tactics.
It is also important to keep your system up to date, as attackers can only leverage zero-day vulnerabilities for a limited time. This means that Apple will patch up these weaknesses through software updates. So, make sure your apps, OS, and system have the latest releases running.
Final thoughts
Browser threats are on the rise. Cybercriminals are going after your browser data, e-wallet credentials, and personal information. They are also abusing browsers with fake notifications and malicious scripts to put on a scareware show and convince you to give away info or download malware. This is not new.
What is new are the specific techniques they are using. This includes the use of GenAI and advanced scripts. To keep yourself safe, follow the advice in this report and stay one step ahead by learning how criminals work to steal your data.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






