United States Postal Service (USPS) scams, which have been around for decades, are experiencing a comeback. The classic “you’ve got a package to be delivered” scam is being updated with new techniques to increase attack efficiency rates.
In a new report, ZLabs uncovered a large-scale USPS impersonation scam that stands out from the rest. Let’s dive into the scam, how it manages to bypass security mechanisms, and how you can stay safe.
New USPS scam uses a never-seen-before technique
Zimperium’s ZLabs team of researchers reported that in a USPS scam, a never-seen-before technique is being used to conceal malicious content in PDF files. The malicious code in these files is heavily obfuscated. It is unrecognizable by most security vendors and is coded to steal credentials and compromise sensitive data.
Interestingly, this campaign doesn’t just target American victims. Fake phishing pages in this campaign appear in more than 50 languages.
ZLabs found 20 malicious PDF files using this technique and a shocking 630 fake USPS web pages used for phishing. The scale of this cybercriminal infrastructure signals a large-scale operation, likely centralized and run by a single threat group.
PDFs: A valuable resource for black hatters
PDFs are fantastic assets for black hatters. These files are heavily used by everyone and have an incorrect reputation for being safe.
For this reason — and because malicious links, scripts, or payloads can be integrated into PDFs — cybercriminals use them as efficient trojans to kickstart scams and phishing attacks. Interestingly, email providers like Apple Mail, Gmail, Outlook, and others employ automated malware scans for PDF attachments. Consequently, criminals choose to lean heavily on targeting mobile victims, as these environments often do not offer the protection desktop or laptop computers do.
In the last decade, internet usage shifted toward mobile devices, and so did attackers. USPS scams previously reached victims through emails. Now, it targets mobile phones, which generate by far the most online activity in the world. And we can only expect mobile threats to increase.
iPhone users are also at risk, as they account for a significant portion of the global mobile device traffic — nearly one-third, according to Cloudflare.
“Without robust mobile threat defense mechanisms, particularly on-device scanning, enterprises face the risk of data breaches, credential theft, and compromised workflows via seemingly harmless PDF files,” ZLabs researchers said.
How does the new USPS scam and cyberattack work?
This new USPS scam is distributed via smishing techniques. This means potential victims receive an SMS message that appears to come from USPS.
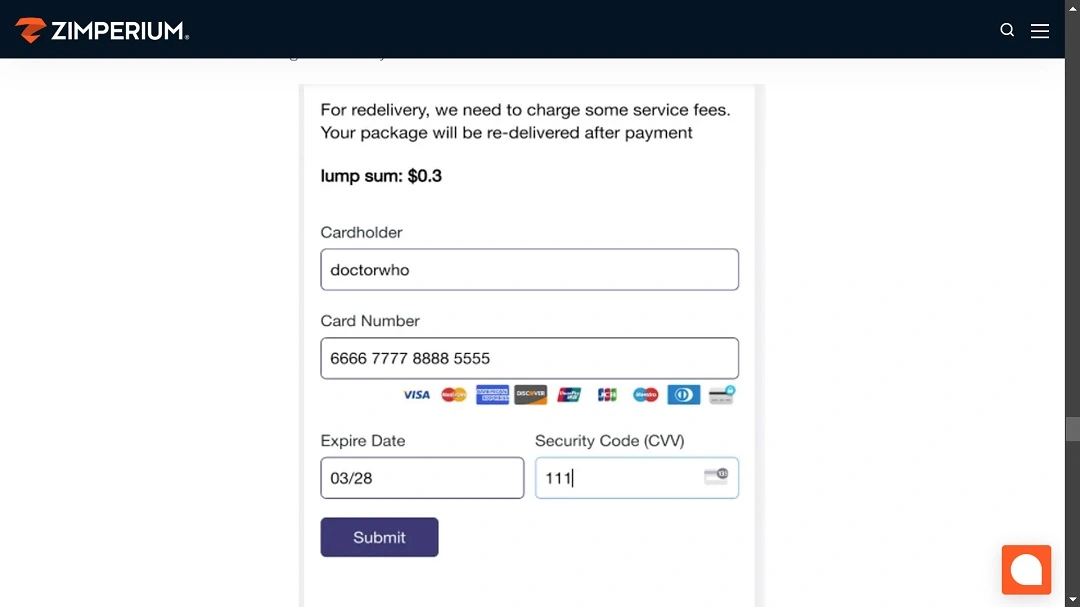
The message includes a PDF attachment that has hidden clickable elements. The links in the PDF are concealed so automatic anti-smishing technologies do not flag the file as malicious.
Malicious links in the PDFs will redirect victims to fake USPS sites that look like the real thing. The victim is then guided through a multi-step web funnel that is designed to steal credentials via personal data and credit or debit card forms to pay fake USPS minor costs (as seen in the image above).
How black hatters hide URLs in PDFs by avoiding the /URI tag
Links in PDF files are typically represented using the /URI tag. This standard tag is coded with a Go-To-URL action.
However, in this campaign, the malicious links do not have the standard /URI tag. By leaving out the standard tag, black hatters manage to bypass detection by standard endpoint security solutions.
“This obfuscation technique is further enhanced by placing object 16 (an XObject) in the middle of the written URL, creating the appearance of a clickable button,” ZLabs said.
Researchers also discovered that the fake phishing page, in addition to tricking users into giving away their name, address, phone, and bank information, is connected to a C2 attacker-controlled server.
The fake page will package, encrypt, and transmit the stolen victim data to this C2 server.
USPS on how to distinguish scams and keep safe
The official USPS site warns users that they do not charge a fee for rescheduling deliveries.
The USPS adds that they do not send customers unsolicited SMS text messages or emails. Even when USPS does engage with customers (responding to customer requests for services with a tracking number), they never include links in these messages.
The bottom line is that any SMS, email, or other type of message that claims to be from the USPS, has a link, and wants to charge you a fee for package delivery management is simply a scam.
Checking IoC, fake sites, and malicious PDF hashes
Moonlock examined indicators of compromise (IoC) linked to this new large-scale campaign. We did not check all of the endless websites associated with this campaign. However, we can say that the URLs we did check (more than a dozen) are all currently inactive.
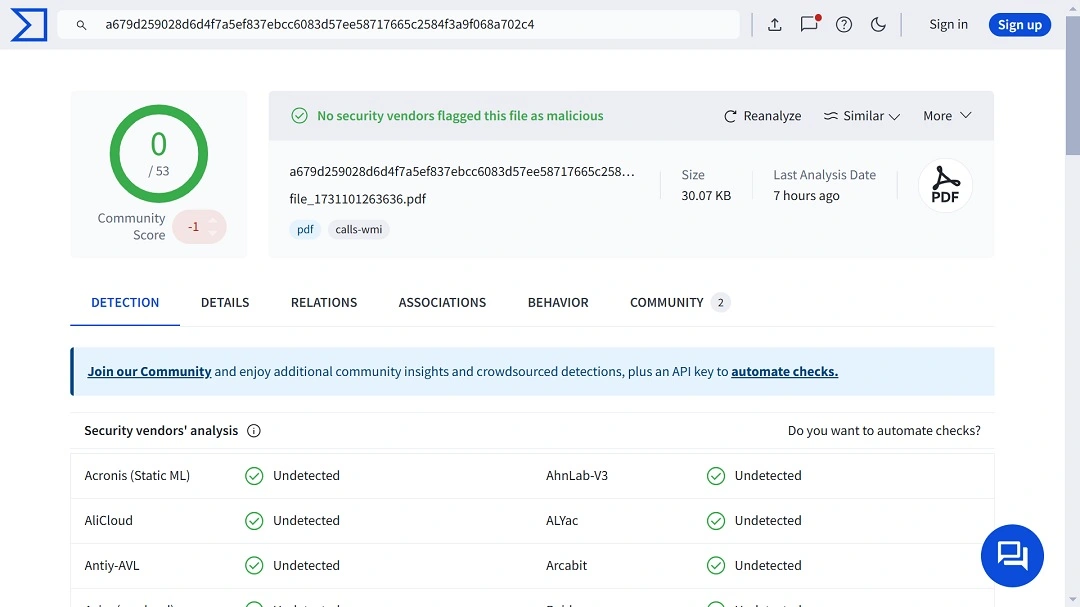
Moving on to PDF file hashes, we checked those on VirusTotal and found that most of these files fly under the radar and are completely undetected by most security vendors.
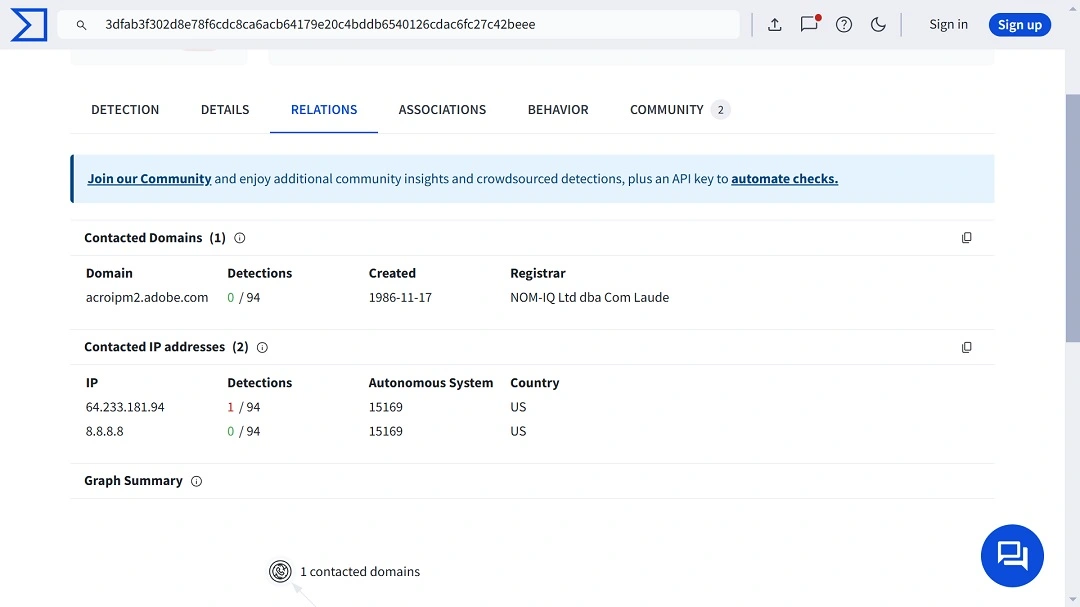
But not all hashes came back green. One PDF IoC hash we examined (3dfab3f302d8e78f6cdc8ca6acb64179e20c4bddb6540126cdac6fc27c42beee) was flagged by 7 out of 63 security vendors.
Links to other known malware
Interestingly, according to VirusTotal, this malicious PDF file contacted the IP address 64.233.181.94. This IP address is identified by Malpedia and other cybersecurity sites as an IP used as a C2 attacker-controlled server by the Rhadamanthys info-stealer threat.
The Rhadamanthys stealer has been used in spam phishing email campaigns and distributed via fake Google Ads that impersonated legitimate websites, popular among remote workforces like AnyDesk, Zoom, Notepad++, and others.
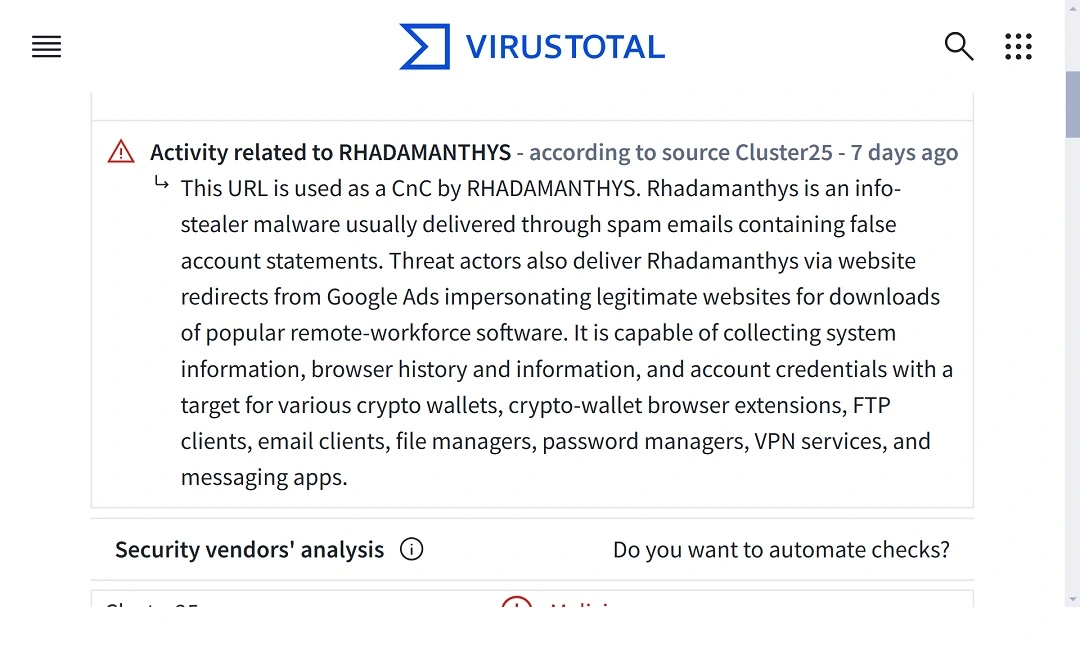
The Rhadamanthys stealer can collect system information, browser data, and account credentials while targeting various crypto wallets and crypto wallet browser extensions. It can also target FTP clients, email clients, file managers, password managers, VPN services, and messaging apps.
Rhadamanthys is linked to the Russian threat group Sandworm, which, along with ATP28, has targeted the Ukrainian region.
Sandworm is also known as Voodoo Bear or APT44. Cybersecurity researchers believe that this group is responsible for Black Energy, a piece of malware associated with electricity and power generation for espionage, denial of service, and data destruction purposes.
It is unclear why this would be one of the IPs that this PDF contacted.
Security experts, developers, and cybersecurity enthusiasts can find the full Zimperium IoC list, which includes over 650 entries on GitHub.
Final thoughts
While USPS scams are often downplayed and considered low risk because they are supposedly easy to spot, new campaigns reveal that USPS scammers have new tricks up their sleeves.
In this specific case, the red flag is not only the massive malicious infrastructure (over 600 domains and 50-plus languages). It’s also the way URLs are concealed in malicious PDF files.
Fortunately, there is a simple solution to stay safe. All users have to do is remember not to engage with USPS SMS, never click on a link, and never open a USPS PDF attachment or other file.