Businesses and individuals alike face many cybersecurity threats these days. Whether it’s hackers trying to steal sensitive customer information or distributed denial of service (DDoS) attacks, system IT admins are required to stay on their toes at all times. But arguably the most insidious threat faced individual users and company networks is ransomware.
Ransomware is a form of malware that enters a computer network, encrypts files, and can even lock down the entire system. In theory, the only way for a system to be recovered and get files decrypted is to pay the attacker a ransom: money in exchange for a decryption key. In other words, ransomware is just good old-fashioned blackmail.
Is it possible to remove ransomware?
Although an attack can be disastrous, ransomware can be removed — if it’s caught early enough. This is just one of many good reasons why you should have third-party antivirus software on your MacBook, such as Moonlock.
The damage isn’t done the moment a piece of ransomware jumps onto a network. It takes time for files to become fully encrypted. So, if you have a solid anti-malware software, the ransomware can be detected and removed before encryption takes place.
There are cases in which you may lose some files, but if the ransomware is caught early enough, you can save the rest. This may not be ideal, but it’s better than paying an attacker for a decryption key that may or may not exist. And if you have Time Machine backups of your device on an external drive, then you can quickly replace the encrypted files and move on.

Is it possible to decrypt files encrypted by ransomware?
Whether or not you can decrypt the files yourself depends on many factors, such as identifying the ransomware type, the encryption algorithm used, and whether decryption is even possible in the first place.
In general, decrypting files that have been encrypted by ransomware is an extremely difficult process. In fact, many ransomware variants don’t even have decryption options available, and even paying the ransom won’t get you access to your files. This is why it’s critical to always have an external backup.
We would argue that your time would be better spent wiping and resetting your device and uploading backups of the files that were lost. The built-in macOS Time Machine backup tool is the natural choice for this.
How to detect a ransomware attack
If ransomware has already encrypted your files, it’s too late. Your best chance is to catch an attack early. So, how do you know when a ransomware attack has begun, and how can you stop ransomware in its tracks?
Your computer is slowing down
Once the ransomware sets up shop on your MacBook, it will start to encrypt your files. Depending on the number of files you have, this will likely take a while.
In the meantime, the encryption process is going to consume a lot of CPU and memory, which means the machine is going to slow down.
Your MacBook is overheating
Since the encryption process requires a great deal of resources from the CPU, your MacBook may start to heat up.
Turning your computer off will only solve the overheating problem temporarily. This will not remove the ransomware or stop it from carrying out the file encryptions the next time your MacBook starts up.
Files are becoming inaccessible
When a file is encrypted, it is made purposefully unreadable. Without the proper password (encryption key), you won’t be able to access the file.
If you notice this happening to your files and you haven’t encrypted them yourself, you have a problem.
You get a ransom payment demand
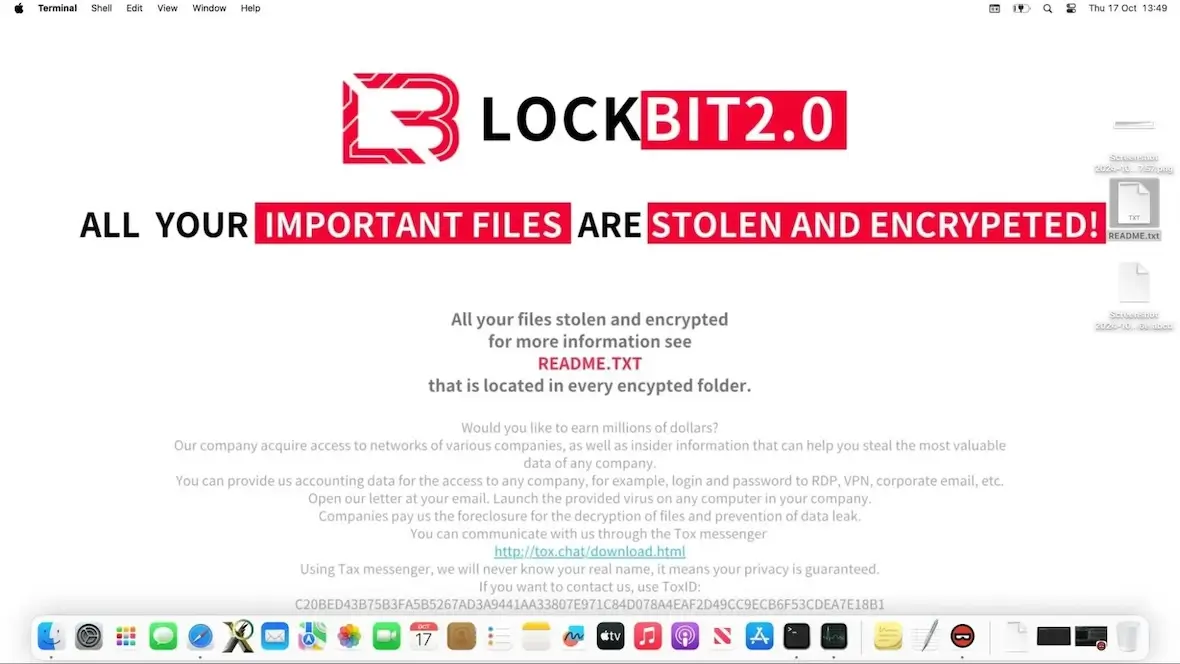
If you get a demand on your screen like the one pictured above, there’s no doubt anymore. You have become a victim of ransomware.
Keep in mind that while a ransomware attacker may claim that they will give you the encryption key to your files after the ransom has been paid, they are under no obligation to do so. There are no assurances that you will be able to regain access to your files, even if you do pay the attacker.
How to remove ransomware from a Mac
So, you’ve just discovered that you have become the victim of ransomware. What now? How do you remove it? Can you remove it? And what could the damage be?
Remove ransomware using Moonlock
The first course of action would be to use Moonlock to attempt to remove the ransomware.
Before you do so, however, there are some things we should clarify:
- You have the highest chance of success for removing ransomware just after it has entered the computer. The longer you wait, the harder it is to get rid of it.
- If the encryption process has already begun, Moonlock can remove the ransomware, but any files that have been encrypted will remain encrypted. You should also perform a deep scan afterward to ensure that no other ransomware variants are present.

To get rid of ransomware on your MacBook:
- Start your free trial of Moonlock.
- Open the Moonlock app, then navigate to the Malware Scanner tab on the left sidebar (the sunglasses icon).
- From the drop-down menu, choose whether you’d like to conduct a Quick, Balanced, or Deep scan. This depends on how much time you’re willing to give the scan, but we recommend selecting the Deep scan option.
- Click Scan, and Moonlock will methodically search through your Mac, depending on the degree of depth you’ve chosen, looking for malware, spyware, or any suspicious-looking files.
- When it finds the threat, Moonlock will immediately isolate it from the rest of your system and files in Quarantine. There, you’ll be able to safely inspect the infected files and opt to safely remove them from your device.
If you’re worried that you’re dealing with a particularly stealthy or new type of ransomware, you might only get results if you opt for a Deep Scan. When you’re done removing malware from your Mac, don’t hesitate to take advantage of the other features built into Moonlock, like Security Advisor, Network Inspector, and System Protection.
Again, keep in mind that Moonlock can only remove ransomware. This will prevent any further damage from being done, but it will not decrypt any files that have already been encrypted.
Get rid of ransomware by doing a factory reset
If a large number of files have already been encrypted or your entire system has been locked down, your best course of action is to completely wipe the MacBook and reset it to factory settings. From there, you can use Time Machine to restore your Mac from a backup.
When it comes to keeping system backups, you don’t have to back up operating system files — those can be easily re-installed. But documents, images, audio files, video files, and so forth should be backed up regularly, ideally on a daily basis. Fortunately, Time Machine can automate the process for you.
Once you’ve reset your Mac, restore the machine from your most recent backup. In the interest of peace of mind, run an antivirus scan with Moonlock to remove any ransomware that may be on the backup.
If no backup is available, your best bet is to boot your machine in macOS Recovery Mode and reset the machine to factory settings. The ransomware will be gone, but you will unfortunately lose all your other files as well. And while it’s rare for ransomware to lock an entire Mac in a way that prevents access to backups, if this happens to you, the solution is a full system reset or factory reset.
What won’t help with ransomware removal

There’s lots of advice out there about what to do if you become the victim of a ransomware attack. Here’s what not to do.
Paying the ransom
Once the ransomware has fully embedded itself into your device and your files are encrypted, the attacker will ask for a ransom to be paid, normally in the form of cryptocurrency.
Your first instinct may be to pay the ransom. After all, it’s the path of least resistance, isn’t it? Pay the money, distasteful though it may be, get the encryption key, decrypt the files, and get on with your day.
Here’s the thing, though. Even if you pay the ransom, there’s no guarantee that you’ll receive a decryption key. If the hacker has their money, why should they care about returning access to your files? You may never receive the key, or you may get one that doesn’t work. Ransomware attackers are not known for their 24/7 customer support.
Threatening the hacker
It doesn’t help the situation to get angry and threaten the hacker with legal consequences. Going full Liam Neeson with a vow like “I will find you” won’t intimidate anyone. You’ll never be able to track them, and they know that.
The only thing this may accomplish is to antagonize the hacker, resulting in an even slimmer chance that you’ll ever receive the encryption key. We get it — being blackmailed is an awful experience, and it’s natural to be angry. But reacting emotionally won’t change anything.
Rebooting your device
Once ransomware is on your computer, it will remain there. Rebooting your machine won’t help. It will only pause the process. Encryption will resume when the computer reboots.
Disconnecting from the network
Once ransomware has established itself, it doesn’t need a continual Wi-Fi or ethernet connection to do its work. Once it lands on your computer, the damage begins, and denying it an internet connection won’t matter.
Trying to decrypt the files yourself
As we said previously, there are many variables involved in trying to decrypt files. You first need to know what the encryption standard is. Only then can you attempt to untangle the entire mess. It’s a process that verges on impossible.
The best use of your time would be to wipe and reset your computer and restore your files from a backup. The longer you wait, the harder this will be.
How to know if ransomware was successfully eliminated

If you catch ransomware early enough and Moonlock manages to get it off your machine, you may still have some encrypted files sitting there, since Moonlock can’t decrypt them for you. If this is the case, you may need to wipe and reset your device.
If you ultimately decide to pay and are lucky enough to get a decryption key that actually works, you should still probably wipe and reset your device. Some, if not all, of the files may be affected. For ultimate peace of mind, a complete wipe can ease your fears and remove that nagging voice in your head asking, “Is the ransomware really gone?”
What to do after a ransomware attack
After using Moonlock to remove ransomware or paying the attacker (a course of action we do not recommend), what else do you need to do?
Figure out how you got the ransomware in the first place
You don’t want history repeating itself. Find out how the ransomware got onto your network in the first place, and take steps to ensure that it doesn’t happen again.
Check other devices on the network
Many devices may be connected to any given network, and malware can jump from one to another. Check anything else that is connected to see if the ransomware ended up there.
For all you know, it may be gone from one device but is now lurking elsewhere, ready to pounce.
Make sure you have backups in place
If you were unfortunate enough not to have backups in place before, start now. Configure Time Machine and make sure your files are updated daily.
You can also buy a removable hard drive and manually transfer only certain files onto it. Cloud storage, such as Google Drive or ProtonDrive, is also a possibility.
How to protect your Mac from ransomware threats
Ransomware is an ever-present danger, so you have to take steps to minimize your risk.
Never install apps or software from unknown developers
Ransomware is often bundled with legitimate-sounding software to lower your guard. You can mitigate this risk by only downloading from the Apple App Store or from highly trusted sources such as Moonlock.
Never click on links from unknown individuals
Another way ransomware gets onto your computer is when users click on phishing links that lead to malware-infected websites/servers.
Never click a link sent to you by an unknown person, whether it’s by email, through SMS, in a document, or in a chat message. And even if the person claims to be someone you know, double-check to make sure it really is them.
Install Moonlock and schedule regular scans
Prevention is the best strategy when it comes to personal cybersecurity. However, you still shouldn’t neglect having a second line of defense to rely on if a virus does infect your device.
By installing Moonlock, you can use the Scan Planner feature to schedule malware scans to automatically run in the background on a daily or weekly basis. That way, you can rest assured knowing that if anything were to go wrong, you’ll be immediately notified.
As we said, getting ransomware and being threatened by a cyber attacker is a traumatic and frustrating experience. But the way out is to remain calm. We recommend that you never pay the ransom. Instead, follow the steps outlined in this guide to purge the ransomware and reset your MacBook, and you’ll come out on the other end as the winner.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. MacBook and macOS are trademarks of Apple Inc.