As Bitcoin breaks the 100K mark, reaching a historic all-time high, cybercriminals are following the money and doubling down on crypto attacks.
A new ESET report found that the surge in the price of Bitcoin has already led to a 127% increase in password thefts targeting Mac users.
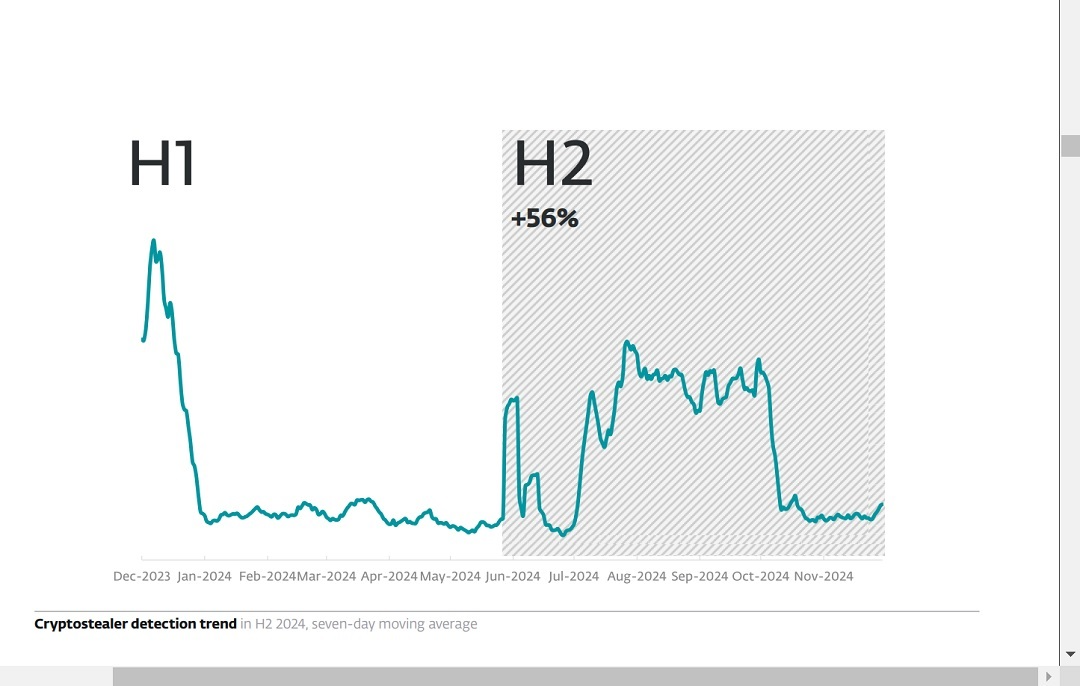
ESET identifies a correlation between infostealers and the price of Bitcoin
The recently released ESET H2 2024 report found evidence that crypto-stealing malware is increasing as the price of Bitcoin soars. According to ESET telemetry data, crypto stealers’ numbers have risen across the board.
These infostealers are targeting Windows and Android but especially Mac users.
“The increase was the most dramatic on macOS, where password stealers targeting cryptocurrency wallets more than doubled in detections compared to H1,” the ESET report reads.
ESET registered a 127% increase in Password Stealing Ware (PSW) targeting cryptocurrency wallets. As ESET recognizes, there is no specific malware used for PSW. Cybercriminals are turning to different existing malware like infostealers, which can be used to illegally gain access to e-wallet credentials and passwords.
If you are a Bitcoin or crypto user or holder, you should be aware that you are part of a population group that is being targeted more than other groups.
Why are crypto thieves targeting Mac users more than others?
According to ESET, while crypto stealers attempting to breach macOS environments spiked by 127%, Windows crypto stealers only grew by 56%, and Android financial threats, including crypto-stealing malware, only grew by 20%.
Why are Mac users being targeted the most in this new criminal Bitcoin gold rush? ESET says infostealers, specifically the Atomic Stealer, aka AMOS, are the culprits.
AMOS stealer is behind the spike in crypto hacks targeting Apple users
Moonlock’s long history with AMOS attack campaigns stretches back to its origin. Moonlock has reported on how AMOS attackers impersonate brands like Slack, build fake sites and promote them through Google Ads, and deploy all kinds of phishing tactics to trick users into downloading AMOS.
The popularity of AMOS on the dark web is directly tied to its efficiency. Once AMOS breaches a Mac, it will extract sensitive information, such as passwords, credit card details, cryptocurrency wallets, and other private data.
AMOS is rented out on cybercriminals’ sites under malware-as-a-service (MaaS) models. AMOS copycat malware, various versions, and different customizations of the infostealer now exist.
How to keep your Bitcoin and crypto secure
While AMOS is undoubtedly a powerful and effective piece of malware, it does have an Achilles heel. An infostealer like AMOS cannot self-install on your Mac. If AMOS is on a Mac, it is because the user downloaded it — unknowingly, of course.
Therefore, as a first step to securing your cryptocurrencies, do not engage with strangers who ask you to click on a link or download software or an app. Always double-check URLs, download files from original stores and channels, and understand that these types of cyber heists can happen to anyone, including you. So, stay on alert.
Hot wallet and cold wallet: Adding layers of security to your crypto
We recommend that e-wallet users take direct action to secure their crypto wallet accounts.
First, make sure your passwords are strong, as that is your first layer of defense.
Second, add another layer of security by enabling MFA. If possible, use biometrics. Face ID or Touch ID are among the most secure in the world.
Finally, enable security notifications if your wallet offers them. Security notifications will alert you via push, email, or other channels if someone is trying to access your account. This should give you enough time to react.
Where you store your crypto is also important. Make sure your e-wallet provider is respected, well-established in the industry, and has a clean cybersecurity record.
All of the advice above is fit for hot crypto wallet users. For those who want even more security, we recommend that you get a cold wallet.
Cold wallets and hot wallets have several cybersecurity differences, but the most important is that a cold wallet is not connected to the internet like a hot wallet is. This means that cold wallets are offline and offer air-tight security.
A cold wallet is usually a physical device like a Ledger Nano S or Trezor that stores your cryptocurrency private keys offline, making them inaccessible to hackers. When choosing a cold wallet, make sure you understand how it works and check the provider’s reputation.
Final thoughts
The price of crypto is on the rise, and users are buying the asset in great numbers. We should assume that some of these buyers are new to the blockchain, crypto, and Web3 world. Therefore, many may not be familiar with what it takes to secure an e-wallet or the state of the global crypto threat landscape in general.
As happens with any digital attack surface that expands, crypto stealers see the rise of Bitcoin as an opportunity for crime. If the price of Bitcoin continues to shoot up, which it will most likely continue to do, and other crypto coins follow, we should expect an increase in crypto heists and crypto malware.






