Jamf Threat Labs has reported that they’ve discovered a new malware campaign using pirated applications as the attack vector. Cracked versions of applications, popular among Mac users, are being hosted by a Chinese website that is known to host pirated software. Researchers say that the malicious campaign and its associated malware share similarities with the Zuru malware, which is also linked to China.
The pirated versions of these Mac apps may contain malware
Users should always exercise extreme caution when downloading software, whether from the web or from app stores. That said, some apps demand special attention.
The pirated apps in this new malware campaign have been tracked, and researchers say they are hosted by the Chinese website macyy[.]cn.
Specifically, Jamf Threat Labs identified pirated versions of several well-known apps that contained malware, including pirated versions of:
- Navicat Premium: a database development tool available for Mac users
- UltraEdit: a powerful text and hex (code) editor available for macOS users
- FinalShell: an all-in-one server and network management software
- SecureCRT: an SSH and Telnet client and terminal emulator
- Microsoft Remote Desktop Beta: available for macOS and used to connect to Azure Virtual Desktop, Windows 365, remote PCs, and admin-provided virtual apps and desktops

Getting your Mac infected with malware won’t immediately brick it. In fact, you might not realize you have malware until weeks or months later. For malware such as spyware or ransomware, the damage is too severe to reverse by then.
To keep yourself safe from malware, try Moonlock for free and enable real-time protection to keep an eye on all new files and activity on your Mac. That way, if anything is amiss with the new app you’ve just installed, Moonlock will immediately notify you and neutralize the threat.
What do all these apps have in common?
The one thing all these apps have in common is that they are popular among Mac users who work in high-value areas for cybercriminals. These areas include development, administration, coding, managing, cloud, and edge computing. These roles are prime targets for cyberattackers, as they often include privileged access for these users.
Moonlock could only access the Chinese website macyy.cn by disabling our VPN or setting it to Asia. When attempting to access the site via a server in the United States or Europe, Google Chrome flags the site and prevents it from being loaded.
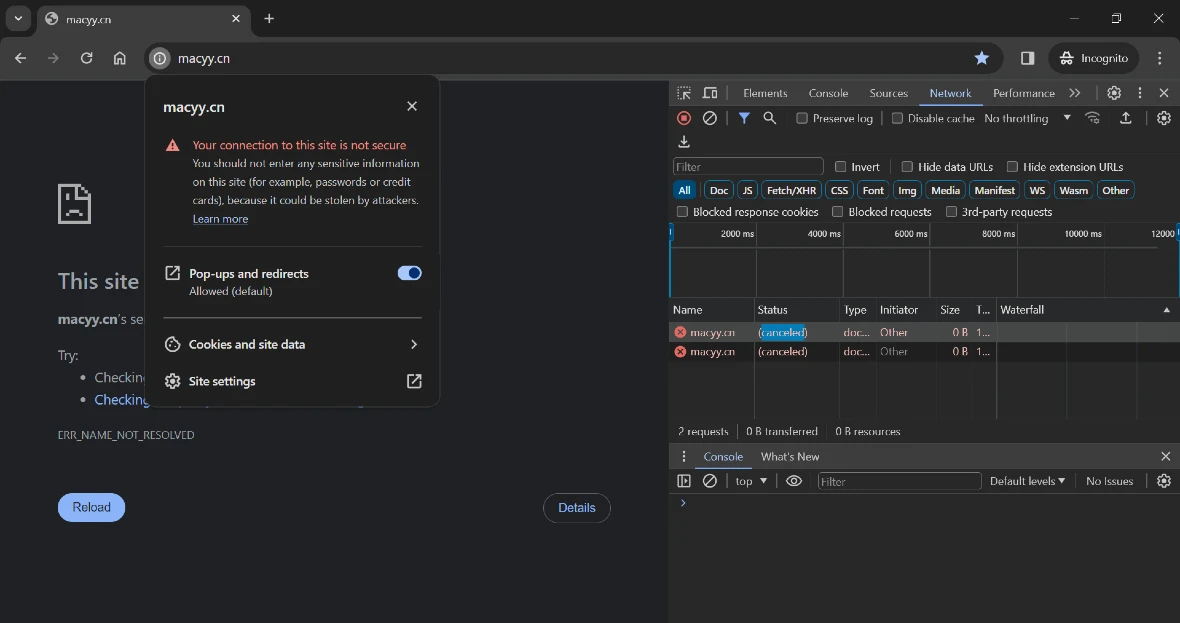
After accessing the site via a VPN set to Asia, Moonlock confirmed that most of the pirated applications that Jamf lists as malicious are still being offered by the site.
Jamf researchers have not concluded that the website macyy[.]cn is, in fact, the author behind the new pirated macOS apps containing malware. However, the malicious apps are hosted there.
It’s common practice for cybercriminals to move to new websites to host malicious applications after being discovered. Therefore, we can assume that these malicious pirated apps will pop up on other similar sites. Users should exercise caution when visiting any website that promotes popular pirated apps, cracked software, or codes to break into them.
Jamf Threat Labs believes that it is a possibility that this new campaign and malware is “a successor to the ZuRu malware (2021), given its targeted applications, modified load commands, and attacker infrastructure.”
Similarly, in addition to the pirated apps listed by the Jamf Threat Labs research report, there could be more malicious apps on this site. Our exploration revealed that the site hosts numerous pirated apps.

Macyy issues dangerous security advice to users
Surprisingly, the Chinese website also offers a blog section where they discuss issues such as “How to bypass Adobe installer security.” This advice effectively suggests that users ignore warnings of damaged or dangerous installation files.
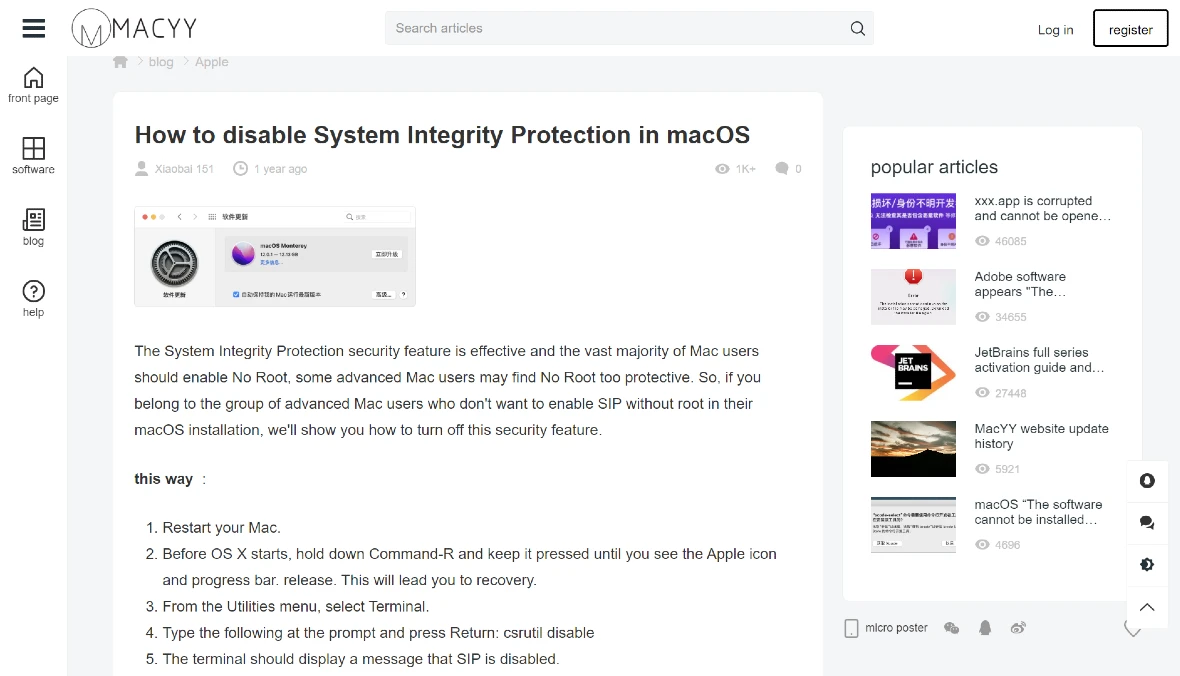
The site even has a blog post with a detailed step-by-step on “How to disable System Integrity Protection in macOS.” Turning off System Integrity Protection on a Mac is extremely dangerous. It exposes the system and makes it vulnerable to viruses, malware, ransomware, and cyberattacks.
Moonlock also conducted a simple Google Chrome search for the website macyy[.]cn. The results included the site promoting cracked versions of other popular Mac apps, including:
- Smooze Pro 2.0
- Downie 4.6.25
- PlayCover for Mac 3.0.0
- Movist Pro for Mac
- Adobe products
- OmniPlayer Pro
Cracks and codes to break into some of these app versions are often offered online by suspicious sites.
The 3 types of malware hidden inside the pirated apps
Researchers who studied the pirated apps concluded that all of the apps studied “resulted in the execution of malicious activity.” The main goal of this campaign is, therefore, not to sell pirated software but to breach devices and spread malware.
The malware that these bad actors are integrating into the illegally modified and pirated applications include a malicious library, a capable backdoor, and a persistent downloader.
A malicious library is loaded by the pirated application and is executed each time the victim opens the application.
The malicious library (malicious dylib) then downloads backdoor malware, which conceals itself in the temporary directory. And while this is deleted when the system shuts down, it regenerates and runs again the next time the application is opened by the victim.
Finally, the persistent downloader uses an evasion technique common across macOS malware. It disguises itself as a legitimate Apple property list — a programming framework.
The combination of these three malware is very dangerous. It enables criminals to gain unauthorized entrance to systems and steal sensitive information. The data at risk can include login credentials, financial data, personal documents, and even browsing history. Using this malware, attackers can also take remote control of a computer, install additional malware, spy on digital activities, and use breached computers to launch more attacks.
Pirated apps are an effective tool for cybercriminals
Pirated applications have existed since the dawn of software. These illegal versions of legitimate programs have always been linked to viruses and malware. And while some users find pirated applications attractive because they’re free or low-cost, the risks associated with them far outweigh the temporary benefits.
The business of pirated applications has also changed in recent years. In the past, pirated apps were simply trying to take a piece of the market from legitimate apps. But today, pirated apps have become an effective tool for cybercriminals. Attackers use them as trojans to breach systems and computers.
Tips to protect yourself against pirated applications
There are several good pieces of advice to consider when it comes to app safety. First, avoid downloading unofficial versions of software or apps. Investing in legitimate software may have a higher upfront cost, but in the long run, it’s still the cheaper option when you consider the consequences. Illegal software can end in complete disaster, including data theft, identity theft, malware, spyware, adware, ransomware, and much more.
Always stick to trusted sources when downloading apps. If you’re unsure, double-check the website’s legitimacy and consult customer reviews.
But even legitimate websites could harbor malicious files if they themselves have been targeted by a cyberattack, for example, as a result of a malvertising attack. To make sure you’re not missing anything, schedule regular scans with Moonlock’s Scan Planner to find malware before it gets the chance to do any damage.
Always follow the warnings that your web browser gives you, especially when it flags a site as malicious and urges you not to visit it.
Finally, invest in professional antimalware software. An extra layer of security can help detect and neutralize potential threats from pirated applications. By prioritizing security and privacy, users can stay away from pirated applications and follow the safe and ethical path that comes with using legitimate software.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






