A new large-scale cybercriminal operation has been identified operating in the wild.
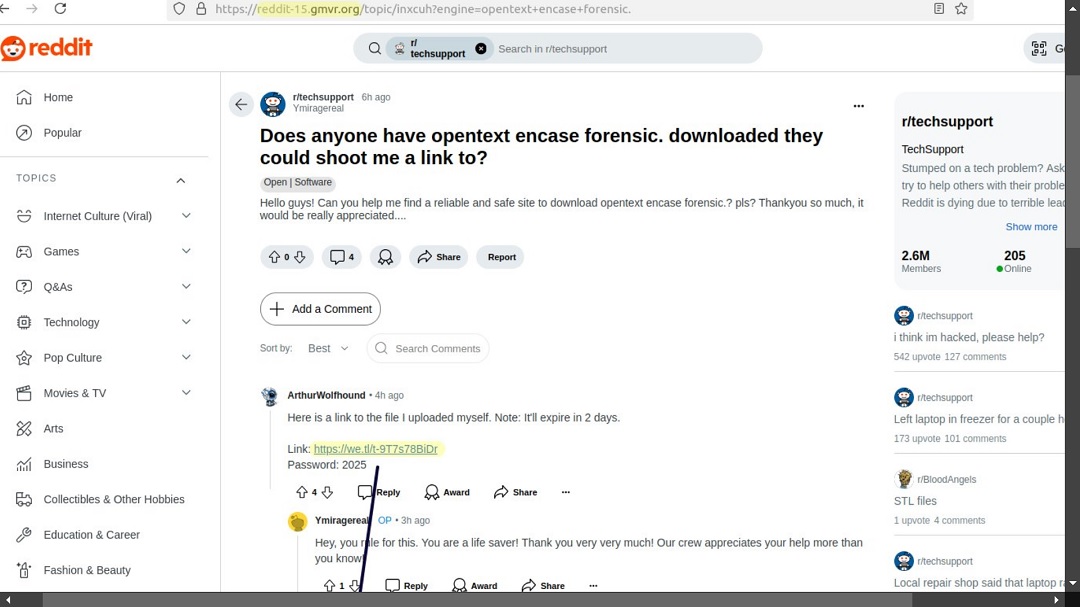
This new threat campaign ran over 1,000 fake sites, impersonating WeTransfer and Reddit. The goal of the campaign is to trick users into downloading the Lumma stealer. But it is also part of a growing trend that is becoming the norm. Let’s dive into it.
1,000 fake Reddit and WeTransfer sites coded to load Lumma
Recently, the X (formerly Twitter) user @crep1x, a Cybercrime Analyst from Sequoia tracking adversaries’ activities and infrastructure, pulled back the curtain on a massive new cybercriminal operation.
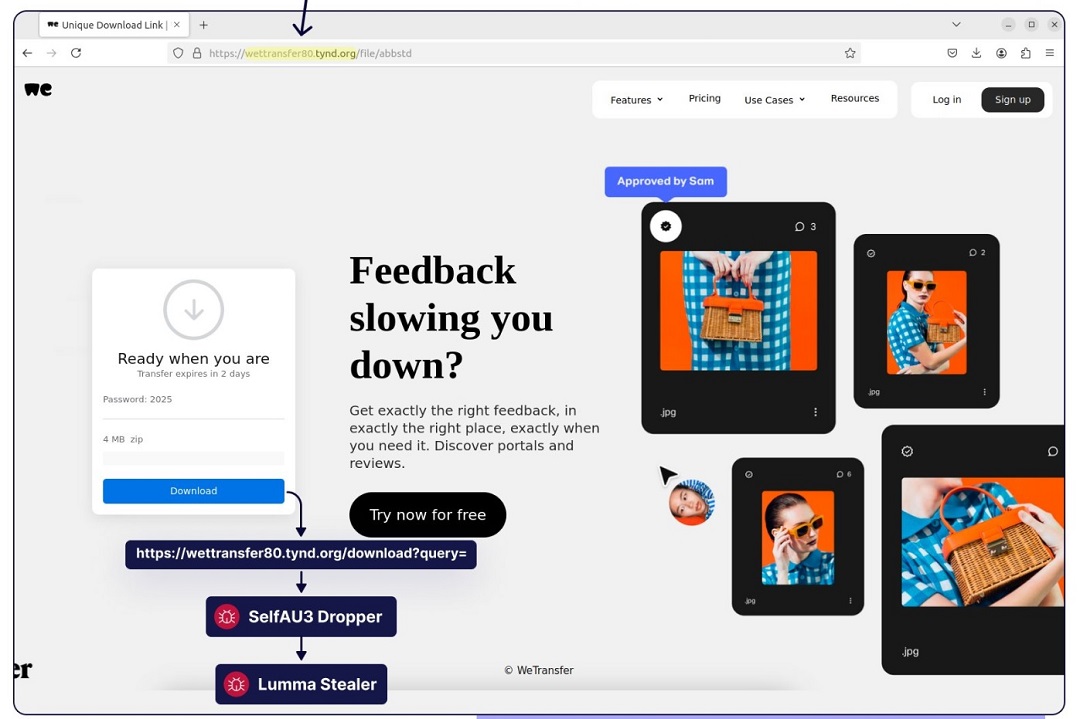
@crep1x shared a list of Indicators of Compromise (IoC) with about 1,000 malicious domains hosting webpages, a shocking amount of domains. Threat actors used these pages to trick users into downloading password-protected files that concealed malware, specifically Lumma Stealer.
“These archives contain an AutoIT dropper, we internally named #SelfAU3 Dropper at @sekoia_io,” @crep1x said.
More on Lumma Stealer and how criminals combine it with AMOS
Lumma Stealer is offered on the dark web under the malware-as-a-service (MaaS) business model. This means that those developing the stealer are continually enhancing the malware with updates and new features while making it available to any operator (criminals or black hatters who rent out or buy the source code of the malware).
Since August 2022, when it was first spotted, Lumma has been linked to Russian-speaking hacker forums. Although Lumma can extract sensitive data from web browsers and files, it is not heavily used as nation-state spyware. The malware is designed for criminals seeking to earn illegal financial gains.
Lumma goes after web browser data. It targets cryptocurrency wallets and two-factor authentication (2FA) browser extensions.
The stealer is promoted on Telegram, with several Telegram bots selling their services, reporting bugs, or offering support and other resources.
Additionally, threat actors are often combining Lumma Stealer campaigns with the AMOS stealer. This double stealer approach can breach victims’ machines no matter what operating system they are running, Windows or Mac.
Efstratios Lontzetidis, a Cyber Threat Intelligence Researcher based in Athens, Greece, explained that the Lumma malware is offered under three plans: Experienced ($250/month), Professional ($500/month), and Corporate ($1,000/month).
The particular threat campaign that impersonates WeTransfer and Reddit seems to have been done under a Corporate Lumma plan. This can be inferred due to the vast infrastructure discovered — 1,000 websites.
While Lumma’s development and distribution are linked to Russian black hatters, operators can be based anywhere in the world. So, the presence of Lumma does not imply attribution.
It is worth noting that Lumma developers ban operators from targeting Russian-speaking organizations and companies.
Can Lumma breach macOS or Safari?
At the present time, Lumma Stealer malware primarily targets Windows systems through deceptive tactics. The stealer leverages commands that often involve the Windows Run dialog and PowerShell scripts. These are specific to the Windows operating system.
Lumma can also breach browsers like Chrome, Firefox, and others. However, given that Safari is predominantly used on macOS and iOS platforms, which do not support these Windows-specific features, it is unlikely that Lumma can compromise the Safari web browser. At least, that’s the case for now. This can change very rapidly.
As mentioned, large-scale financially driven phishing criminal operations like these have begun to distribute Windows stealers and macOS stealers alike. Their fake webpages can gather operating system information and redirect users to the malware that fits their OS.
More importantly, malware developers are also constantly improving their malware, and stealers that can breach Windows and Macs are the holy grail.
Future outlook for large-scale cybercriminal campaigns
Based on our observations and investigations from last year and this year, we expect more large-scale cyber criminal operations like these to emerge. Malware automation, MaaS services offered on the dark web, GenAI, ready-to-use phishing kits, and fake webpage generators are widely available for anyone online.
We have reported on threat campaigns in which cybercriminals continually increase their digital attack surface to cast a wider net. This often means generating a significant number of domains for each campaign and taking to different media for automated distribution and promotion. From Google Ads abuse to social media and platforms like Reddit, GitHub, and others, everything follows this trend.
This cyberattack is by no means unique but part of a wider trend where vast, malicious infrastructures and C2 servers are rapidly set up.
Cybercriminals running these campaigns have also become very good at hiding their tracks. Once a report exposes their scams and illegal operations, the entire infrastructure disappears, often leaving cybersecurity researchers empty-handed, with little information about the operation and even less information for attribution.
Creating vast infrastructures also makes the work of security researchers very hard. Tracking and tracing a couple of domains can be done, but analyzing 1,000 is a nightmare.
The bottom line
To stay safe from these threats, use strong passwords, enable MFA, and only engage with websites that are verified and official. Never download files, and understand that more threat campaigns like these, and maybe even bigger ones, are expected.
The reason why these large-scale phishing campaigns prevail is simple. For criminals, it is a low-risk, high-reward opportunity. All they have to do is lease out a stealer and hire the services that come with it. Until this business model is disrupted, it will only continue to grow.