Locky, the ransomware malware introduced in 2016, has infected millions of users worldwide, affecting Mac and Windows operating systems alike. While the original Locky is not active, some variants are still out there and are of great concern to security experts.
What is the Locky virus?
The Locky virus is ransomware malware that, once it breaches a computer, encrypts files and holds them hostage, demanding pay as ransom to decrypt them.
The malware depends on social engineering techniques. Hackers trick a victim into downloading or clicking on a link. Attackers have used email phishing for most of Locky’s infections. Locky has a very advanced and sophisticated code, considering it was released in 2016. It is also known for rapidly spreading to other devices.
How does Locky work?
The most common way Locky spreads is through email. Victims receive an email that contains an attached Microsoft Word document that hides the malware. Users who open the Word document will see an illegible string of gibberish text and are prompted to “enable macro” to view the document. If users hit this, they unpack Locky’s payload.
Once this happens, the virus deploys and loads into the system’s memory. Then it starts encrypting documents and renames them as hash.locky files. It also installs .bmp and .txt files. Locky can spread through network files that the user has access to.
Once Locky encrypts files, users see a ransom note as a desktop wallpaper or a text file, as shown in the image below.
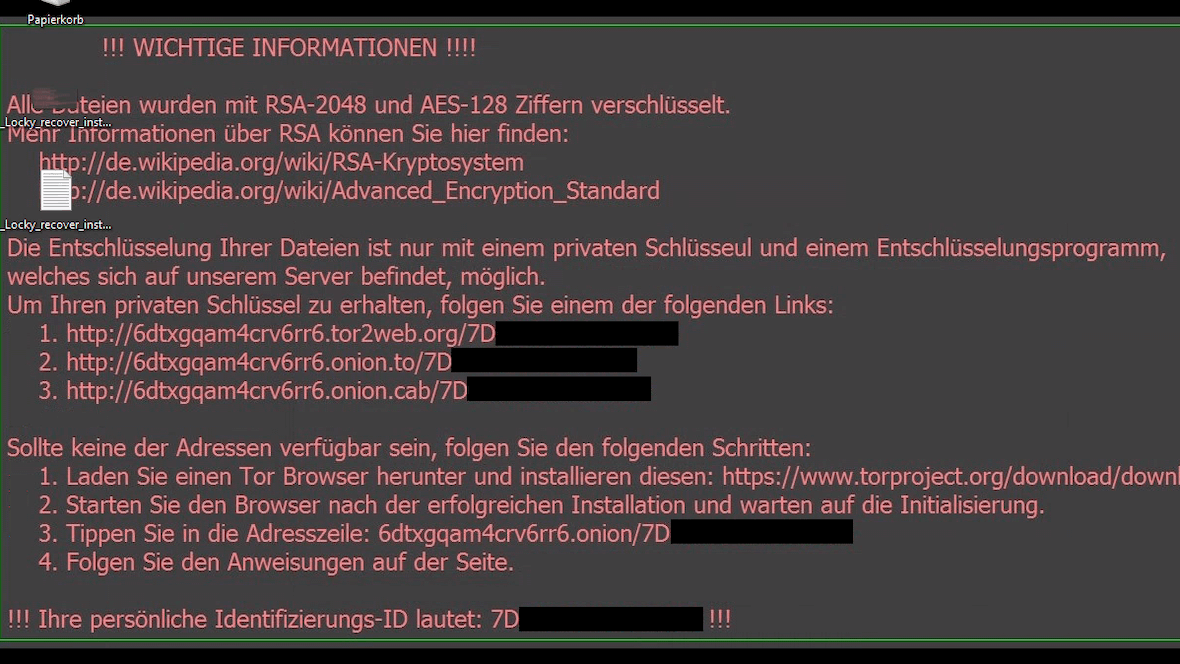
Attackers will provide links for victims to get the decryption program and keys. If users cannot access the provided links, they are asked to install the Tor browser. And once users open the Tor browser, they are directed through a step-by-step guide to transferring a ransom in Bitcoin (BTC) in exchange for the decryption key. Locky demands, on average, 0.5 to 1.0 Bitcoin (BTC), with 1 Bitcoin set at about $23,200 as of August 2022.
When files are encrypted, file names are converted to a unique 16-letter and number combination. The first waves of attacks only used the .locky file extension, but later, other file extensions were added, such as:
- .asasin
- .diablo6
- .locky
- .loptr
- .odin
- .osiris
- .shit
- .thor
- .ykcol
- .zepto
Who is vulnerable to Locky, and who is most affected?
Locky targets Windows and Mac users alike. It is known for its massive bulk email campaign attacks. Locky email campaigns are sent through botnets, a network of computers operating together. Botnets are used to deliver malware, spam, and a host of scams.
In 2017, a Locky malware variant sent out 23 million messages in just 24 hours. In 2016, it also sent millions over the year as it gained notoriety. Google Trend data shows global user interest in Locky, revealing spikes of infections between long dormant periods since it began.
Experts believe Locky is capable of executing 100,000 infections in just one day. Locky has extensively targeted personal users. However, the most notable cases involve attacks on businesses and public services.
For example, in 2016, the Hollywood Presbyterian Medical Center paid a $17,000 ransom in the form of bitcoins for the decryption key for patient data due to a Locky infection. And in 2016, the Dartford Science & Technology College was infected with the virus when a student opened an infected email that spread through the school’s files.
Who is behind the Locky ransomware?
The leading actor behind Locky distribution is the Necurs botnet. As reported by Wired, after long years of investigation and cooperation, Microsoft dismantled Necrus in 2020. Russian cybercriminal groups are believed to have operated the Necurs botnet.
While the Necurs botnet is now down, Locky versions are still distributed through other means. It is said to have controlled 6 to 9 million computers simultaneously. It also has a reputation for delivering the worst Trojans. Worst of all, it has had the power to reinvent itself over the years.

How to protect your data from Locky
The ultimate prevention is backup. Protecting your data and system from Locky is like protecting it from any other ransomware attack. Ransomware malware is one of the most challenging attacks to deal with once your computer is infected. Prevention is your best bet.
When it comes to ransomware, many believe that if they pay, they will get their files back. But malware and attackers can damage, destroy, lock, steal, sell, and leak your data. However, there are ways to protect your data today.
1. Watch out for suspicious messages
Locky’s primary form of infection is through malware hidden in attachments sent over email. You will not be infected if you do not download the attachment. Other variants work similarly, trying to trick you into taking action. Whether downloading an attachment or clicking on a link, you should always be cautious when dealing with suspicious messages from unknown sources.
2. Disable macros in Microsoft Office
To be effective, Locky needs to trick you not once but twice. First, you must download the .doc Microsoft Word file. Then you have to click on “enable macros” to view the attachment.
To avoid clicking on “enable macros,” you can disable macros by default in your Microsoft Office programs. You should only enable macros when you know a file is from a trusted source.
To disable macros:
- Open Microsoft Word.
- Go to File > Options > Trust Center.
- Go to Trust Center Settings > Macro Settings.
- Select your desired macro settings.
3. Back up your files and system
The ultimate prevention is backup. Whether it’s your business data and systems or your personal devices, keep your backups in offline storage devices like USD or removable hard drives if possible. This means keeping them off your network.
You should also make sure that your computer has the backup and restore option active and set to do regular backups. While backups come in handy for recovering your files without paying a ransom, they will not protect you against data leaks or if the attacker decides to sell your data to the highest bidder on the dark web. It is, however, imperative that you have updated backups.
4. Don’t neglect updates and anti-malware
Like all malware, Locky will take advantage of security vulnerabilities and the lack of trusted and efficient anti-malware software. Experts strengthen operating systems (OS) and software through updates that also fix security loopholes. If you get a notification for an update, do not leave it for later. You should always turn on automatic software settings.
Finally, anti-malware tools can instantly detect corrupted or malicious files even before you try to open them. Having trusted and efficient malware can be the difference between losing your files and data and dealing with a ransom, or working normally.
Is Locky still a threat today?
Today, in 2024, Locky has significantly decreased in terms of threat level compared to 2016 and 2017, when it was a very serious problem. But, even though the original Locky virus has more or less departed from the malware stage, people should still be vigilant for Locky clones. Some of these may be even more sophisticated and dangerous than their predecessor.
That’s the problem with malware — it never completely dies. It just gets cloned into something new.
Common methods used to spread Locky ransomware
There are 2 main methods that were used to spread the Locky ransomware attack.
Locky primarily attacks through email. It is sent as an email attachment in the form of a Microsoft Word document and a macro. When the victim downloads the Word document — perhaps disguised as an invoice — and runs the macro to read the file, Locky is released.
This method is much more efficient if the victim is using an older version of Microsoft Word that may not have up-to-date security patches.
A malware-infected website
The other common delivery method for Locky is a malware-infected website. Victims may be social-engineered into clicking the link, for example, by a phishing email or a smishing SMS.
How can you detect a Locky ransomware infection?
How do you know when you’ve become a victim of a Locky attack? Here are the signs to watch out for.
Your system slows down
Like many types of malware, Locky will slow your system down to a crawl. This is because Locky will be consuming a large chunk of your CPU and memory, as it encrypts all of your files in preparation for asking for the ransom.
Your antivirus scanner will alert you
When the ransomware hits your network, your antivirus will send you a warning to notify you that it’s there.
Your firewall will try to block it
The ransomware needs to establish a connection with its home base, which means going through your firewall. Your firewall will try to block it from establishing an outside connection.
Your file names will have weird extensions
If Locky has encrypted your files, they will then all have weird file extensions, such as locky, .odin, .osiris, .thor, .ykcol, or zepto (among others). You won’t be able to change those file formats back or open them, as the files will be locked.
You will receive a ransom demand
If it isn’t already obvious, you’ll get final confirmation when a ransom note arrives telling you to pay an amount in cryptocurrency in return for the decryption key. You then have a choice to either pay the ransom or wipe and reformat your system. However, unless you have a backup of your files, you will lose them all if you wipe and reset your network.
How to get rid of Locky
There are two ways to remove Locky from your computer. The first, manual removal, may be too complicated for the average user. It requires technical knowledge to remove the Locky app or program, cookies, temporary files, web browser extensions, and registry keys. If you don’t complete the manual removal correctly, you risk damaging data, files, and even the OS. Restoring your computer to a previous date can also be done manually but only works to remove early versions of the malware.
The other method to remove the malware requires using antimalware tools. For Mac users, Moonlock is an effective, user-friendly option — and it’s notarized by Apple, meaning it’s software you can trust.
Remove Locky with Moonlock
To remove Locky with Moonlock:
- Get your free trial of Moonlock and launch it.
- Select Malware Scanner from the sidebar.
- Select Deep mode and hit the Scan button.
- Moonlock will detect Locky automatically, as well as other suspicious malware.
- Open Quarantine and click Remove to completely get rid of Locky.
Anti-malware software can remove Locky but will not decrypt your files. As mentioned before, this is why it is necessary to do regular backups.
Once you remove the malware, you can restore files if you have saved them in external storage devices or hard drive backups. In Windows, you also can try to restore files with the backup and restore feature.
Use Time Machine to remove Locky
Mac users can take advantage of Time Machine to restore files and systems. Time Machine does schedule backups at different intervals to allow you to return the state of your computer to a certain point in time.
If your Mac is not starting up properly, you can run Time Machine in Recovery Mode.
To run Time Machine restore on a Mac Intel:
- Shut down your Mac.
- Press the Power button and hold down Command-R.
- Release Command-R when you see the Apple logo or a spinning globe.
- Type your admin username and your password.
- Choose “Restore from Time Machine backup” from macOS Utilities.
- Follow the instructions on the screen.
To run Time Machine on an Apple silicon Mac:
- Shut Down your Mac.
- Press the power button and hold it down as your Mac boots.
- Release the power button once you see the startup options.
- Select “Options.”
- Type your admin username and password.
- Choose “Restore from Time Machine backup” from macOS Utilities.
Security experts explain that while Locky is not the first ransomware, it remains one of the most dangerous. Locky also revealed to the world just how much damage ransomware can create. Today, many ransomware attacks work with the same principles while technically operating very differently — the infamous 2017 Bad Rabbit attack being just one example.
Prevention and remediation tools are the go-to solutions when it comes to avoiding the costs that come with a ransomware attack.






