There is a common saying in the crypto world: “Nothing is more secure than a cold wallet.” Unfortunately, this saying is no longer true. As bitcoin and other cryptocurrencies reach historic all-time high prices, crypto cyber incidents and crypto heists have become the new norm.
In this active threat landscape, Moonlock Lab has uncovered 4 active campaigns using a new feature that can steal users’ cold wallet seed phrases. More concerningly, the feature is being integrated into macOS stealers like AMOS, which are heavily distributed. Let’s dig in.
A novel malware feature can phish seed phrases from Live Ledger cold wallet users
Recently, Moonlock Lab released a report on 4 active campaigns leveraging a feature to steal cold wallet seed phrases. The technique is new but has been active since at least August 2024.
Analysis of the observed malware samples reveals that this campaign, which seems to be driven by malware-as-a-service distributors, specifically targets users running macOS — and only those who have cold wallets and the Ledger Live app.
Cold wallets and how hackers can trick victims into giving away seed phrases
A “cold” wallet, once considered the safest way to store crypto, is usually a hardware-level blockchain wallet. Unlike online “hot” wallets, cold wallets are not online.
When users set up a cold wallet, they choose a series of words known as seed phrases. Think of these seed phrases as the combination to your offline crypto vault.
In theory, anyone who has your seed phrases can take full control of your wallet. Seed phrases are never stored online. Users usually write them on a piece of paper in the real world and store it for safekeeping. A number of other methods to store seed phrases exist.
So, how can hackers remotely steal words written on a piece of paper? By tricking the users into believing that their app has encountered a problem and needs those seed phrases to recover the wallet and its funds.
To do this, cybercriminals have reverse-engineered one of the most popular cold wallet apps, Ledger Live, and written some rather sophisticated code that allows them to delete Ledger Live from a victim’s device and replace it with a fake version of the app that is designed to steal the seeds. They do all this after running malicious scripts and installing macOS stealers.
Experienced crypto users, as well as newcomers to the crypto economy, use cold wallets. They are the preferred storage method chosen by crypto whales and the crypto wealthy.
The crypto sector, traditionally dominated by North Korean hackers, is increasingly being targeted by new criminal gangs
Those in the blockchain cybersecurity sector know that the global blockchain threat landscape has been dominated by nation-state threat actors from North Korea.
North Korean hackers have been linked to most of the millionaire crypto hacks targeting crypto platforms and blockchain developers. However, due to crypto’s surge in price, new financially motivated cyber threat actors and violent criminal gangs are emerging to target crypto holders. And some incidents are proving to be deadly serious.
In the past few months, criminal gangs have been committing violent crimes. They are shaking down crypto wealth from New York to Paris, where police recently detained 20 suspects of violent crimes.
Through the use of violence, extortion, kidnapping, and even torture, these highly resourced criminal gangs, operating with intimidating precision, have been after the seed phrases of their victims by using real-world violence.
The same trend spills over on the dark web. Moonlock Lab reported that dark web chatter from hackers talking about how to steal seed phrases has been rising.
As mentioned, Ledger Live is one of the most popular and well-known cold wallet providers. They have about 1.5 million users.
I have a cold wallet. Should I worry?
If you are an Apple user, have a cold wallet, use the Ledger Live app, and connect to it using your Mac, take note.
Should you worry? Yes. But not in a way that makes you lose sleep. You can take some steps to mitigate this type of cyberattack.
If you are a major holder of Bitcoin or other crypto assets and do not use Ledger Live but use cold wallets, you should still take precautions. The best defense is to stay up to date with crypto security news and to learn the tricks hackers use.
How the Ledger Live cold wallet cyberattack works
Moonlock Lab identified 4 active campaigns using the new Ledger Live impersonation technique. The feature in 1 campaign is still in development. The other 3, however, are reported to be out in the wild, hot, and active. All 4 campaigns go after seed phrases from Ledger Live users.
“The initial vector of this attack is social engineering,” explained Moonlock Lab. “A victim first downloads a malicious app (cracked Photoshop, CoinMarketBots, phishing through ads, etc), so we can’t blame LedgerLive, since the infection chain starts with the user clicking a malicious link or downloading a malicious app.”
Here is how this new cyberattack technique works:
- Ledger Live app cold wallet users are targeted by cybercriminals. This is most likely done via spear phishing — a variant of phishing where the criminal first investigates the potential victims, learning who they are, what industry they work in, their interests, etc.
- The malware is sent to the potential victim, typically via email, SMS, social media channels, or other phishing channels.
- The malware drops malicious scripts on Macs, bypasses their security, and installs a stealer. At this stage, the attackers go after browser data, passwords, hot wallet credentials, files, etc.
- Next, the attackers install a fake Ledger Live app and delete the real Ledger Live app.
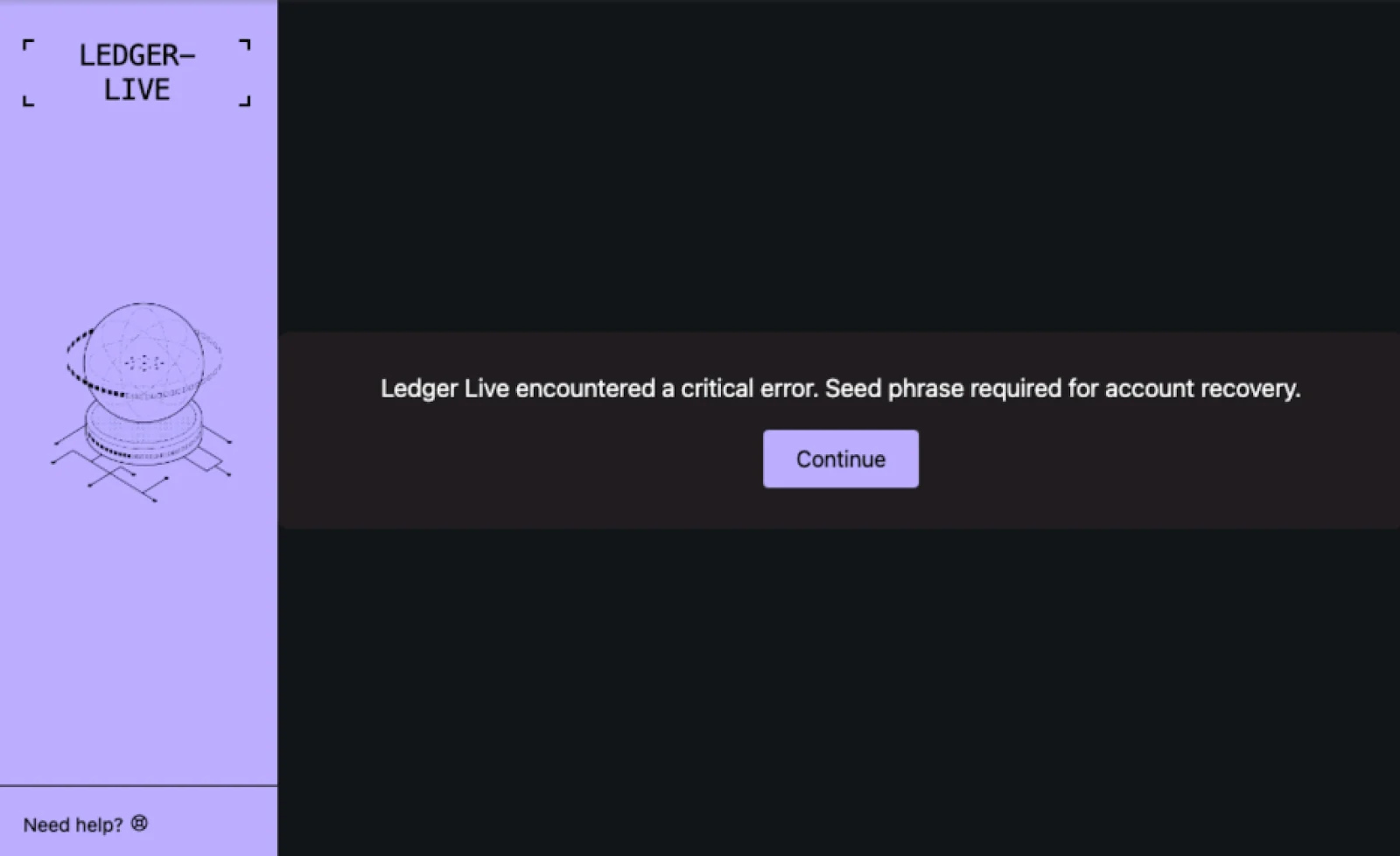
- The fake Ledger Live app triggers a screen warning. This notification attempts to trick the user by displaying a message that reads, “Ledger Live encountered a critical error. Seed phrases required for account recovery.”
- The victim then enters the seed phrases, probably in a rush and worried about losing their cold wallet funds. And, just like that, the malware sends the seed phrases to an attacker-controlled C2 server. Using the seed phrases, the attacker gains full control of the victim’s wallet.
All roads lead back to… Rodrigo4?
Moonlock Lab reported that a single threat actor was the catalyst for this new technique that targets cold wallets. The actor goes by the username @Rodrigo4 on XXS Forums — a known hacker forum.
Rodrigo4 is not a new face in town. He was involved in the development of the Atomic Stealer (AMOS), Poseidon, and the Odyssey Stealer.
“The turning point came with a threat actor known as Rodrigo, who introduced a game-changing feature in his Odyssey stealer,” Moonlock Lab said.
Using this feature, the stealer developed by Rodrigo4 (Odyssey) has been bypassing Ledger Live’s defenses with a sophisticated phishing scheme since March 19, 2025.
Rodrigo4 eventually said he wanted out of the black hat hacker game and was going to transition to legal activities. The veracity of this statement is unknown.
Palo Alto Unit 42 claims that Rodrigo4 sold the Poseidon Stealer MaaS to an unknown source in August 2024. The malware has apparently remained active since then.
Moonlock Lab experts told us that Rodrigo4 wanted to sell his business in 2024 and stop doing “bad things.” However, he seemed to be unsuccessful in his attempt to break out clean from the cybercriminal underworld.
“He came back this year after a few months,” Moonlock Lab said.
Active Mac stealers leveraging cold wallet phishing tech
What Moonlock Lab did find out is that, inspired by the work of Rodrigo4, several threat actors picked up the work and developed their own versions of this cold wallet phishing grabber malware to integrate as a novel feature into their stealers.
In the underground cybercriminal world, imitation is the sincerest form of flattery, and new features like these spread like wildfire in the malware-as-a-service black market.
“Rodrigo’s impact has set a dangerous precedent for others to follow,” Moonlock Lab reported.
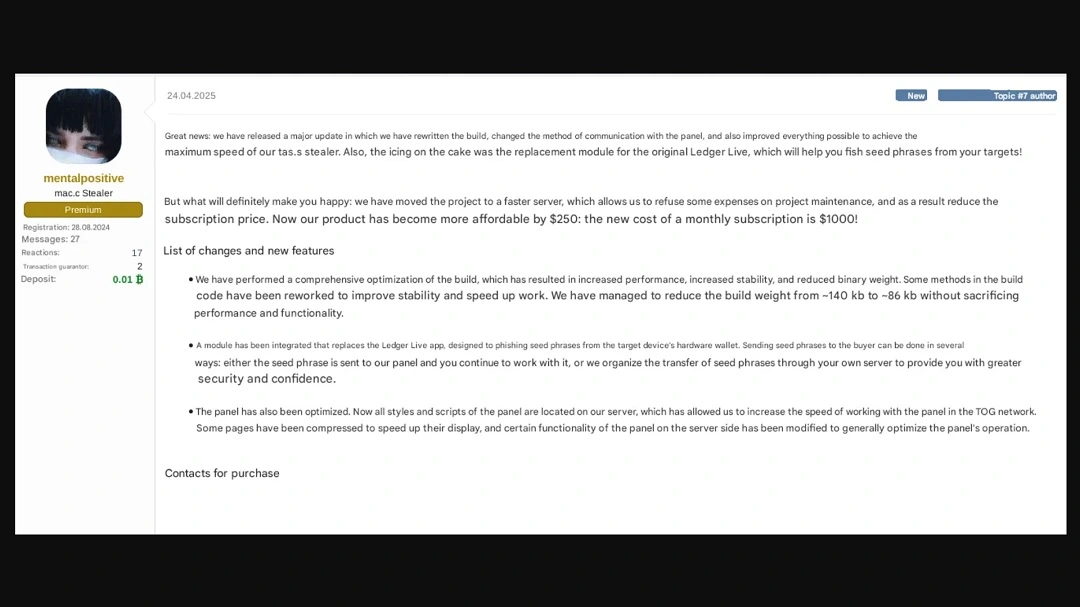
One of the threat actors that leveraged this feature goes by the username @Mentalpositive. He recently posted an ad on a dark web forum claiming that his updated malware now includes an “anti-Ledger” feature. Moonlock Lab analyzed samples of the malware @Mentalpositve was selling and found that the feature is still not operational nor fully developed.
Jamf Threat Labs also picked up on this new cold wallet malware. They reported that another threat actor, active for at least the past 3 months, had integrated the tech to target Ledger Live users.
Anyone with a crypto wallet is a potential target
More dangerously, Rodrigo4’s work caught the attention of the gang (or gangs) that distribute the AMOS stealer. Moonlock Lab found that the stealer now features an “almost identical phishing page with slight frontend tweaks to target Ledger Live users.”
These stealers can steal not only cold wallet seed phrases using phishing but can also extract victims’ sensitive data, including browser credentials (Chrome, Firefox, and Safari), Apple Notes, Keychain databases, and files like PDFs, in addition to wallet configs from Desktop, Documents, and Downloads. It also targets Binance and TonKeeper configs.
“It targets everyone who has crypto wallets, and not only LedgerLive, but many others we mentioned in our previous articles, like Electrum, Exodus, Atomic, Coinomi, etc.,” Moonlock Lab said. “We’re seeing detections among our users, but since their data is anonymous and we can’t trace their losses, we can’t say if they are wealthy crypto holders or average folks.”
It targets everyone who has crypto wallets, and not only LedgerLive, but many others we mentioned in our previous articles, like Electrum, Exodus, Atomic, Coinomi, etc.
Moonlock Lab
It is evident that in the fragmented yet connected cybercriminal world, black hat hackers are picking up tricks from one another, competing with new features, and ultimately pushing the innovative edge of their macOS-targeting information-stealing malware.
Mitigation: How to protect your cold wallet from seed-phishing
While the popularity of decentralized technologies like blockchain and crypto is fundamentally beneficial for global users — improving the speed of transactions, dropping rates, and bridging financial inclusion gaps — the meteoric rise in the price of digital coins has lured a nasty bunch of criminals and cybercriminals to the game. In response, users should take some preventive actions.
Moonlock Lab recommends that users do the following:
- Be on the lookout for fake error messages that ask for your 24-word recovery phrase (a classic phishing move).
- Never give out your seed phrase. It doesn’t matter how real the site or person seems — just don’t do it.
- Only get Ledger Live from the official website. Don’t follow any sketchy links.
- Keep yourself in the loop. Follow legitimate security teams like Moonlock for heads-up warnings on new threats.
Heed this final word of caution from Moonlock Lab experts, who say that users should be suspicious of any message requesting their 24-word recovery phrase.
“Legitimate services never ask users to enter seed phrases through pop-up alerts or websites,” said Moonlock. Any unexpected security alerts should be verified through official Ledger support channels before taking action.
Final thoughts
Financially motivated cybercrime is on the rise, and crypto users are prime targets.
While the first versions of this cold wallet feature and malware seem to have been coded to target specific crypto holders, dark web activity shows that the tech has been integrated into AMOS and other malware. This makes the development extremely dangerous for cold wallet users.
Fortunately, knowing how this cyberattack works is a good enough defense. Remember, if your Ledger Live app asks you for your seed phrases, you are probably being targeted. We expect Ledger Live to come up with a security patch to protect users from this new criminal scheme.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






