A dangerous new piece of malware targeting macOS devices has been discovered, posing a significant threat to Apple users. Cybercriminals are increasingly focusing their attention on Apple’s operating system, and this latest development underscores the importance of robust security measures for Mac users.
macOS-targeting Banshee Stealer breaks onto the dark web market
On August 15, Moonlock Lab sounded the alarm on a new macOS info stealer malware dubbed Banshee. Bad actors behind this new malware were found promoting it on dark web forums and on Telegram. Moonlock Lab highlighted some of Banshee’s most noteworthy features.
Banshee Stealer can breach macOS x86_64 and arm64. It can also collect notes from the Notes app, data from Keychain (all registered user passwords), and full system information, as well as macOS password data.
This malware is not one of the stealthiest ones out there. However, it is considered dangerous due to its potential to cause damage.
Deconstruction of Banshee and how it compares to the Atomic Stealer (AMOS)
Elastic Security Labs deconstructed the Banshee info stealer in detail and linked the malware to Russian threat actors.
“This malware presents a severe risk to macOS users, targeting vital system information, browser data, and cryptocurrency wallets,” Elastic Security Labs said.
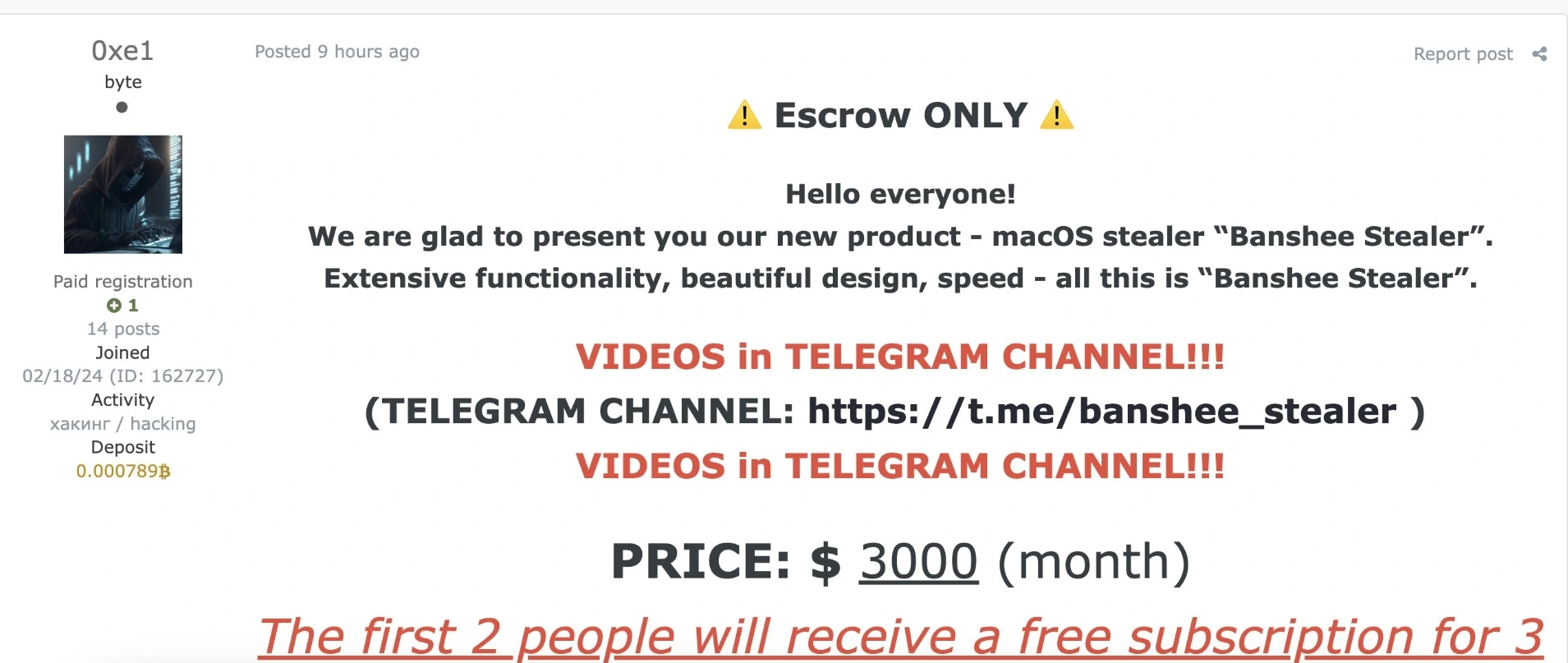
The price of Banshee on the underground market
This new info stealer shares several characteristics and functions in common with the AMOS stealer. For example, just like AMOS, Banshee Stealer has a steep monthly subscription price of $3,000 — exactly the same price.
Analysis from Elastic Security Labs also signals that the distribution of Banshee is gaining momentum.
While no definitive vector of attack has been linked to Banshee, these types of malware can be distributed via malicious email (phishing), fake ads, fake websites, software product impersonation, and zero-day vulnerabilities.
Programming languages and functions
Regarding the programming language, Banshee uses C++ symbols, which is interesting when compared to other info stealers.
According to Moonlock Lab, many stealers for macOS are developed using Python, Go, or Swift programming languages. AMOS, for example, was developed using Swift, and the executable can run on different CPUs, including Intel and Apple Silicon.
Analysis of the C++-generated global variable initialization functions, done by researchers from Elastic Security Labs, found very similar functions in Banshee — comparable to AMOS.
These functions include:
- Controller.cpp: Oversees the malware’s main functions, including evading detection, gathering information, and sending stolen data
- Browsers.cpp: Collects data from web browsers installed on the victim’s computer
- System.cpp: Gathers information about the victim’s computer system and attempts to steal passwords
- Tools.cpp: Contains reusable functions for encrypting data, creating folders, and compressing files
- Wallets.cpp: Targets and steals information from cryptocurrency wallets
Why aren’t Banshee’s stealth and evasion capabilities very good?
For some reason, Banshee’s detection evasion techniques are not advanced. These features may be updated in the near future, as it is a common tactic in the malware-as-a-service illegal industry to release more powerful versions and new features for their malware.
To detect debugging, Banshee uses the sysctl API. This means it relies on a system-level function to check for active debugging sessions.
While this method can provide basic protection against simple debugging tools, it’s not considered an advanced technique. More sophisticated malware often employs multiple layers of anti-debugging measures, including dynamic code generation, virtual machine detection, and code obfuscation to hinder analysis.
Another common feature in malware is virtual machine detection. Virtual machines are used by cybersecurity researchers to deconstruct malware in isolated and secure environments. Advanced malware can detect when a virtual machine attempts to access it and prevent it from running, making the work of analysts more challenging. Elastic Security Labs spoke about their findings regarding this issue.
“For virtualization detection, it runs the command system_profiler SPHardwareDataType | grep ‘Model Identifier’ to determine whether the string Virtual appears in the hardware model identifier, which suggests a virtual machine.”
“These methods are relatively simple and can be easily circumvented by advanced sandboxes and malware analysts.”
What Banshee can do and where it comes from
Another interesting note that once again implies that this malware is of Russian origin is that Banshee is coded not to run on a computer if it detects that its primary language is Russian.
Naturally, this is a common feature that is seen in all types of malware coming from Russia, from info stealers to ransomware. Moonlock found that the IP for extraction is also hosted in Moscow, Russia.
Like AMOS, Banshee also targets browser data from a wide range of different browsers, including:
- Safari (cookies)
- Chrome(cookies, passwords, auto-fills, wallets, and cards)
- Firefox (auto-fills and cookies)
- Brave (cookies, passwords, auto-fills, wallets, and cards)
- Edge (cookies, passwords, auto-fills, wallets, and cards)
- Vivaldi (cookies, passwords, auto-fills, wallets, and cards)
- Yandex (cookies, auto-fills, wallets, and cards)
- Opera (cookies, auto-fills, wallets, and cards)
- OperaGX (cookies, auto-fills, wallets, and cards)
Additionally, it can breach and control e-wallets and add-ons from Binance, Electrum, Exodus, Atomic, Coinomi, and over 100 plugins, including the most popular ones.
These capabilities all align with the AMOS stealer and the different versions of it that circulate in the wild.
Extraction and C2 bad actor-controlled server analysis
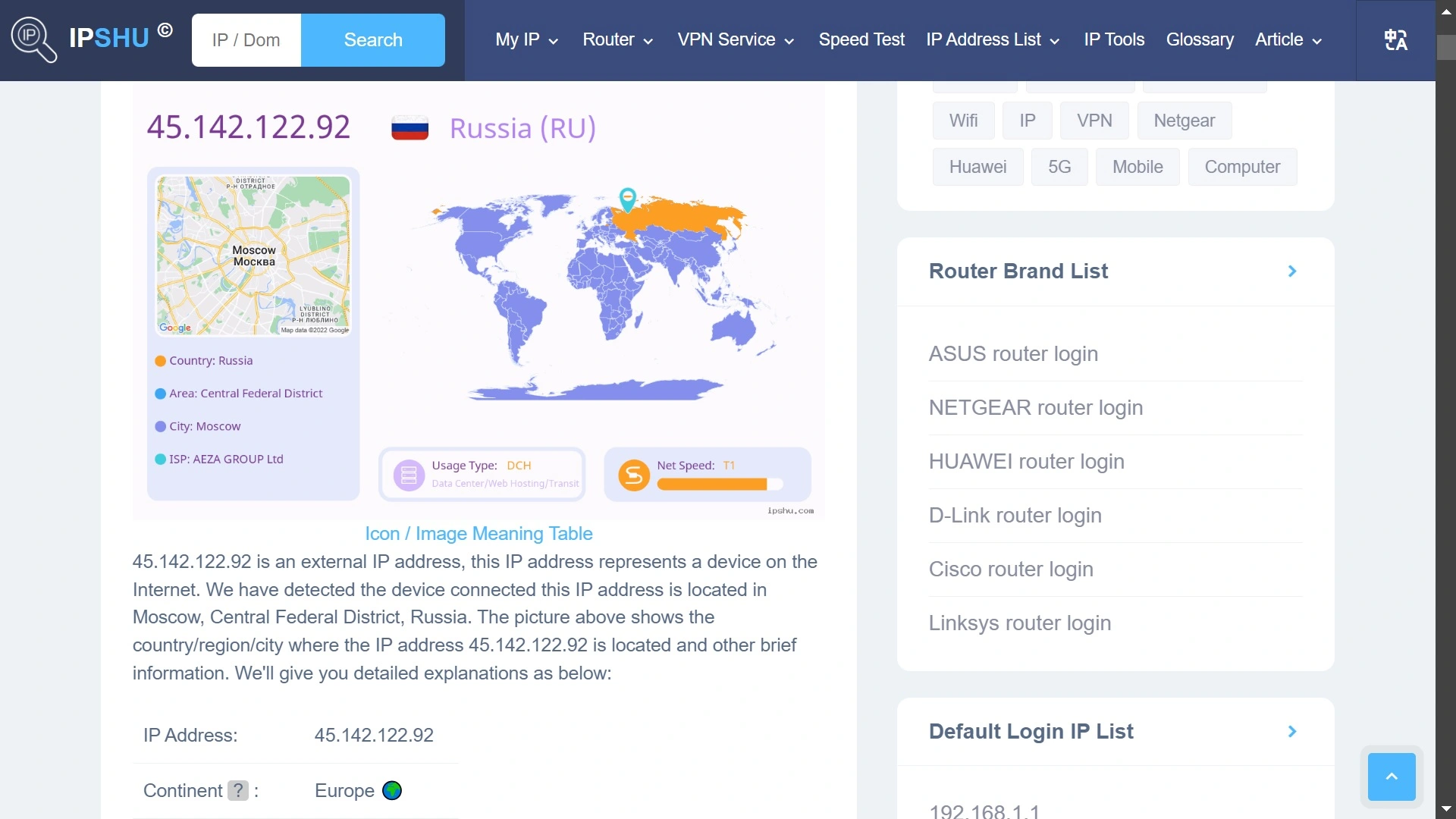
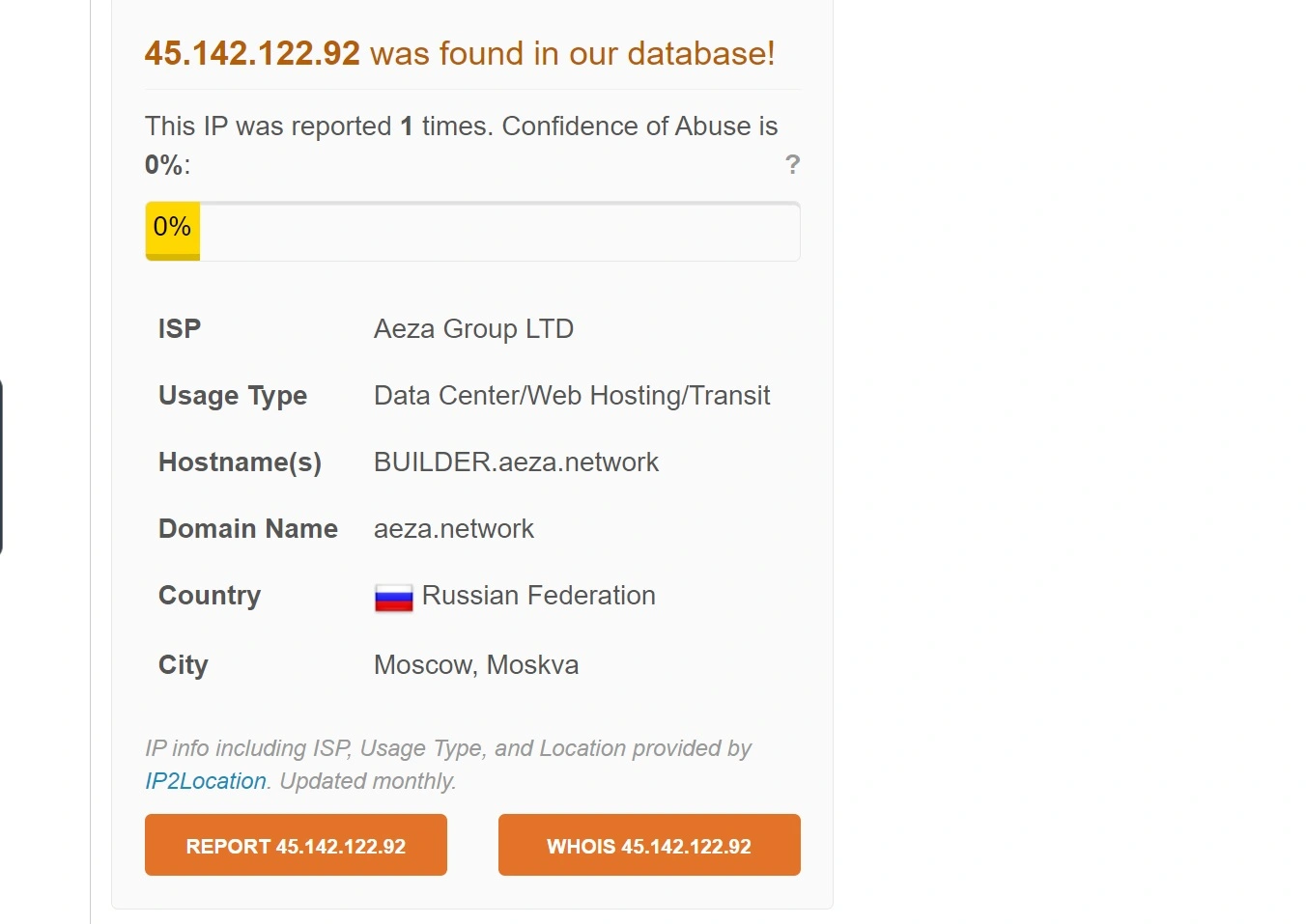
Once Banshee gathers the data it wants to steal, it compresses it into a ZIP file and stores it in the temporary folder. The ZIP file is then encrypted and sent through a post request to the URL http://45.142.122[.]92/send/.
Moonlock accessed the 45.142.122[.]92 C2 server — allegedly controlled by bad actors — which is used to send the data exfiltrated from macOS victims. Moonlock found that the IP Reference Location is set to Tverskoy District, Moscow, Russia.
The postal code listed for the IP is also Moscow, Russia (103132), and the Neighborhood is listed as the Moscow Kremlin, Moscow, Russia.
The IP address 45.142.122[.]92 belongs to the subnet 45.142.122[.]0/24. This subnet includes hosts that begin with address 45.142.122.0 and end with address 45.142.122.255, allowing for a space of 256 possible hosts.
139 reported IPs from this subnet have historically generated a total of 14,598 abuse reports, some very recent. Moonlock found several folders and files in the IP, including code repositories.
The IP directory could be a malware development environment where code bases are hosted for collaboration or testing purposes. It can also be a staging server, where malware is deployed before being distributed to victims.
It is also probable that the server itself is compromised and being misused. Finally, the files in the directory may be a distraction for researchers. Or, even worse, they could contain hidden malicious code.
From stealer to stealer until the end of time?
The rise of macOS info stealer malware is nothing new. Moonlock has been warning about the increasing frequency and capabilities of Mac-targeted info stealers for more than a year now.
Mac info stealers have become popular due to their effectiveness. Cybercriminals have reverse-engineered infamous versions of these types of malware and have rapidly assimilated the necessary know-how needed to build new macOS info stealers and variants.
“As macOS increasingly becomes a prime target for cybercriminals, BANSHEE Stealer underscores the rising observance of macOS-specific malware,” Elastic Security Labs said.
Until Apple finds a holistic security software update solution that can effectively patch up all the macOS vulnerabilities that info stealers exploit, users and cybersecurity researchers are left with no option but to continually monitor the emergence of new macOS-targeted info stealers and raise awareness for each one.






