A North Korean group of hackers linked to the country’s military cyber warfare units has updated the OtterCookie malware. This modular stealer, now in its fourth version, can breach Windows, macOS, and Linux environments. Let’s dive straight in.
NTT Japan unveils North Korean OtterCookie malware update
On May 7, NTT Japan, a global technology company, reported that the North Korean hacker unit behind the Contagious Interviews campaign — which lured victims on LinkedIn and similar job sites — is picking up speed. They have released a new version of the OtterCookie malware.
NTT said that the group behind this malware is WaterPlum, a rebranding of the Famous Chollima group. It targets financial institutions, cryptocurrency operators, and FinTech companies worldwide. Their new OtterCookie modular backdoor/stealer is now in its fourth version.
NTT reported on this malware in December 2024, and it has come a long way in a short period of time.
Understanding the context: Barrage of North Korean missiles fired into the Sea of Japan
Tensions between Japan and North Korea are at a record high. Media reported on May 8 that a “flurry of short-range ballistic missiles” had been fired into the Sea of Japan.” The exercise was reported to be possibly linked to North Korean weapons tests for exports to Russia for use against Ukraine. This served as a warning sign to the United States and its allies, who were conducting a naval exercise in the region.
Japan’s Defense Minister Gen Nakatani said Tokyo “sternly protested and strongly condemned” the missile launches. Nakatani added that no missiles had reached Japan’s exclusive economic zone, and no damages were reported.
While the “missile test” is not directly connected to OtterCookie, increased geopolitical and military tensions are often followed by a spike in cyber warfare activity.
A rundown of cyber warfare linked to North Korea
Cyber warfare is key for North Korea. To bypass international sanctions and fund its defense and nuclear program, North Korea deploys thousands of military-trained hackers operating under the Lazarus group umbrella.
From crypto heists to money laundering, Lazarus brings in billions of dollars into the country, according to a United Nations report.
In the past year, 2 of the biggest threat campaigns that North Korean hackers have been running include posing as IT workers to infiltrate and funnel wages back home, and infecting victims by luring them with tech work.
Both these campaigns have been active for years, with WaterPlum or Famous Chollima leading the Contagious Interview campaign.
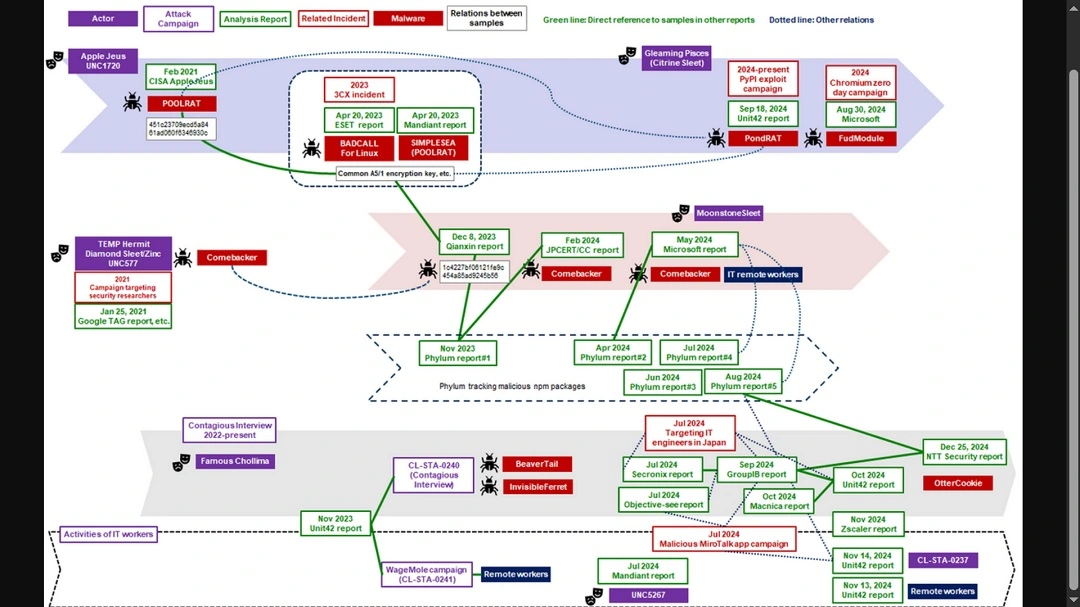
Famous Chollima has done more than change its name. It switched from distributing the malware known as Bevertrail and InvisibleFerret to OtterCookie.
How is OtterCookie distributed? The Contagious Interview method
Famous Cholima, now WaterPlum, runs a classic but effective technique to find new victims and infect them with OtterCookie malware.
The group of hackers uses sites like LinkedIn or Telegram to recruit skilled developers. Instead of posting ads on these platforms, the group collects key data on its targets. They learn their strengths, skills, and personal interests, and they tailor-built job offers to lure them in. This means that the group does its research before even contacting victims, increasing the chances of success.
Their main target interests include blockchain or crypto developers, software developers, and IT professionals with high-paying roles. Once they cold-contact a victim, they might, for example, arrange for a “coding test.” In reality, this is just an excuse to trick the developer into downloading the malware.
The fourth version of OtterCookie has been spotted in the wild since April 2025. Besides its 2 main modules, the stealer malware has added new features.
OtterCookie: Version 4 and its 4 modules
Let’s look at the 4 modules that are fully functional in the new OtterCookie to understand what it can do and how it can evolve.
Main core module: Coded to interact with other modules, extract system information, and execute remote commands; you can think of this main module as the engine.
Version 4 of OtterCookie’s main module is now coded to steal contents from clipboards, access macOS files, detect virtual machines (which cybersecurity researchers use to study malware in isolated environments), and collect document files, image files, and files related to cryptocurrency. The main core module of OtterCookie is also responsible for orchestrating extraction functions with the Upload module.
Upload module: Coded to establish a 2-way communication channel between the infected device and the attacker-controlled C2 server. This module can be used to remotely control victim devices, send commands to the core module, and extract the stolen victim information.
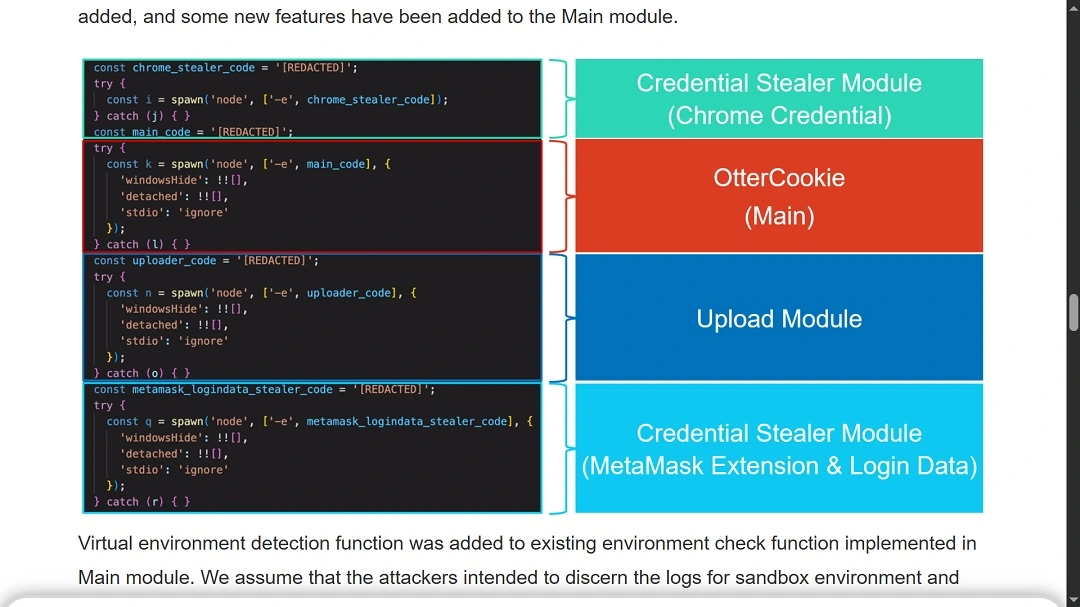
Google Stealer module: OtterCookie’s v4 Google stealer module steals usernames and passwords from Google Chrome.
Credential Stealer module: This module is also coded as a stealer and looks for files and data related to MetaMask, Google Chrome, Brave browser credentials, and macOS credentials.
Using these modules, OtterCookie can take full control of a Mac (or Windows or Linux) system. It can then steal sensitive information, financial details, and blockchain-crypto data and funds, conduct cyber espionage, and much more.
OtterCookie’s flexible motivation and the Lazarus group’s agenda
Given the modular nature of OtterCookie, the motivation behind this campaign is flexible. This means that WaterPlum (aka, Famous Chollima), the Lazarus subgroup running Contagious Interview, might choose to empty the crypto wallet of one victim while running cyber espionage on another.
In the end, the Lazarus group is aligned with the North Korean government’s goals and objectives. They employ cyber warfare techniques to fund sanctioned defense and nuclear programs. They also conduct espionage operations aligning with their international political agenda, regional Asian strategy, and, more locally, targeting the South Korean government.
There are 2 reasons why no one should underestimate this threat. First, Contagious Interview — as well as other infiltrations by North Korean mole workers — are growing more prevalent every day, with hundreds of known companies already breached or affected.
Second, Lazarus subgroups like Famous Chollima have been running these types of campaigns for more than 2 decades. They know what they are doing and can trick even the most tech-savvy and cybersecurity-aware individuals. Furthermore, there is little that these attackers cannot hack.
The skills that the Lazarus group demonstrates, for example, in moving stolen cryptocurrencies, funneling, layering, and consolidating funds through a multitude of e-wallets and brokers in modular malware like OtterCookie, make this nation-state threat as dangerous as they come.
How to avoid Contagious Interview and similar threats
To avoid these types of sophisticated nation-state threats, always verify job opportunities from trusted sources, and never download files or take technical tests from unknown recruiters without vetting.
If a coding test or file seems suspicious, analyze it in a sandbox or consult a cybersecurity expert before opening it.
To stay safe from OtterCookie, Apple users should:
- Avoid downloading files from unverified recruiters or unknown sources.
- Keep macOS updated with the latest security patches.
- Use an up-to-date antivirus tool that monitors for malware behavior.
- Disable automatic script execution from downloaded files.
- Regularly monitor the clipboard and system activity for unusual behavior.
- Only allow apps from identified developers.
- Use a password manager instead of browser-based credential storage.
- Keep backups of important files and store them offline.
- Use a safe browser and be cautious of what data it stores.
Final thoughts
OtterCookie is a reminder that North Korean cyber operations are not just about espionage. They’re a sophisticated, well-funded extension of the country’s military strategy.
As these campaigns evolve, developers and IT professionals must remain vigilant, especially when approached for lucrative roles online. In today’s cyber battlefield, the most dangerous weapon might just be a fake job offer.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






