The Realst Mac-targeting infostealer is back. This time, the Rust-written crypto-data stealer has been deployed in what looks like a laser-focused spear phishing campaign in which a threat actor is going after Web3 developers.
Spear phishing Web3 developers with fake jobs
On December 6, Cado Security Labs announced they had discovered a new phishing infostealer scam distributing the rust-based Realst stealer.
The scam is optimized to target Windows and macOS devices alike, including all the different versions that exist in these operating systems.
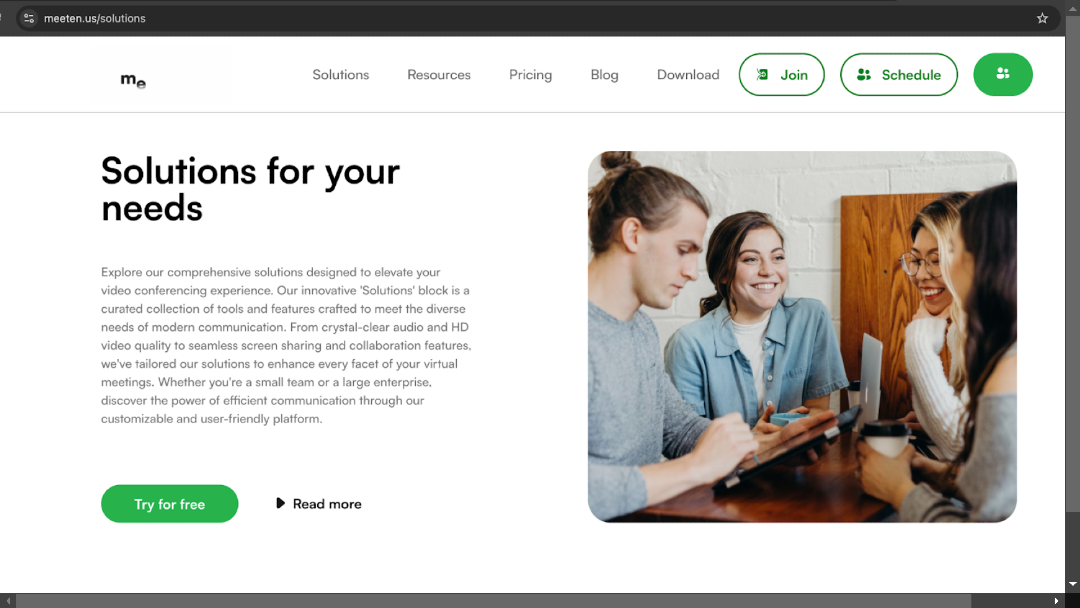
How the Web3 job offer scam works
In this campaign, cybercriminals are using fake job offers as bait. Targeting job seekers is not a new trend, with actors recently taking to LinkedIn to run these scams.
The threat actors behind this new cyberattack are likely doing their homework and investigating potential victims before contacting them. Cado Security reports that blockchain community developers and workers are contacted via personalized messages on social media apps like Telegram and have even received phone calls from the threat actors.
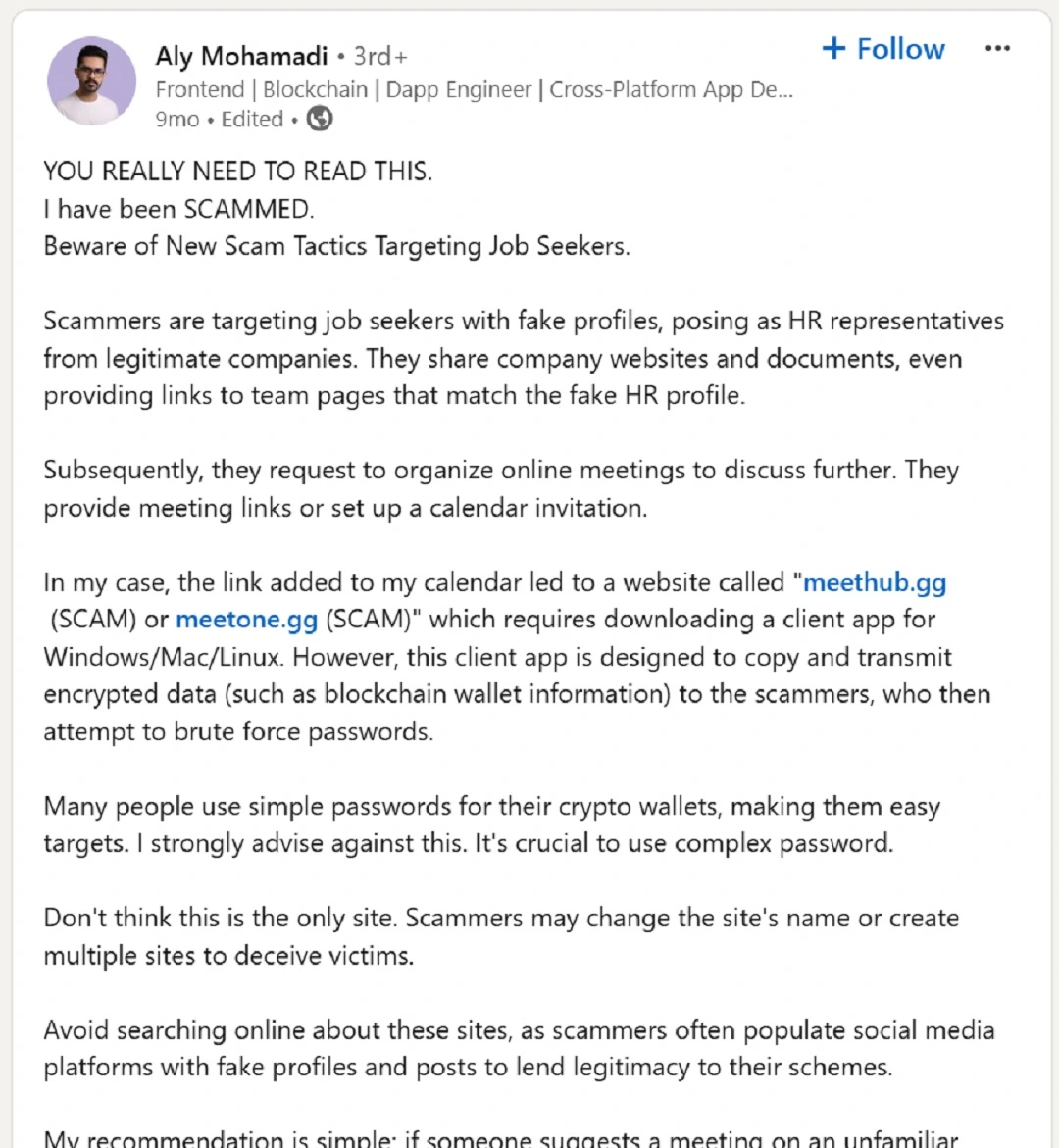
Once the victim is hooked on a fake job offer, threat actors will redirect them to an online site that appears to be a legitimate service. Scammers will then tell victims that they need to set up a virtual meeting to discuss details and move forward. This is when victims are directed to a fake video meeting site and asked to download the app to conduct the meeting.
When users click on the download button, they download the Realst stealer, which rapidly goes through malicious commands to exfiltrate as much data as possible and empty crypto wallets.
Interestingly, Cado Security also found that the website itself contains Javascript coded to steal cryptocurrency if the victim stores it in a web browser. This happens even before the victim downloads or installs any malware.
Threat actors are burning through websites and domains fast
For some reason — probably for the sake of evasion and exposure — the threat actors behind this campaign have already burned through a lot of different websites and domains.
“It (the threat actor) has gone by Clusee[.]com, Cuesee, Meeten[.]gg, Meeten[.]us, Meetone[.]gg and is currently going by the name Meetio,” Cado Security warned in its report.
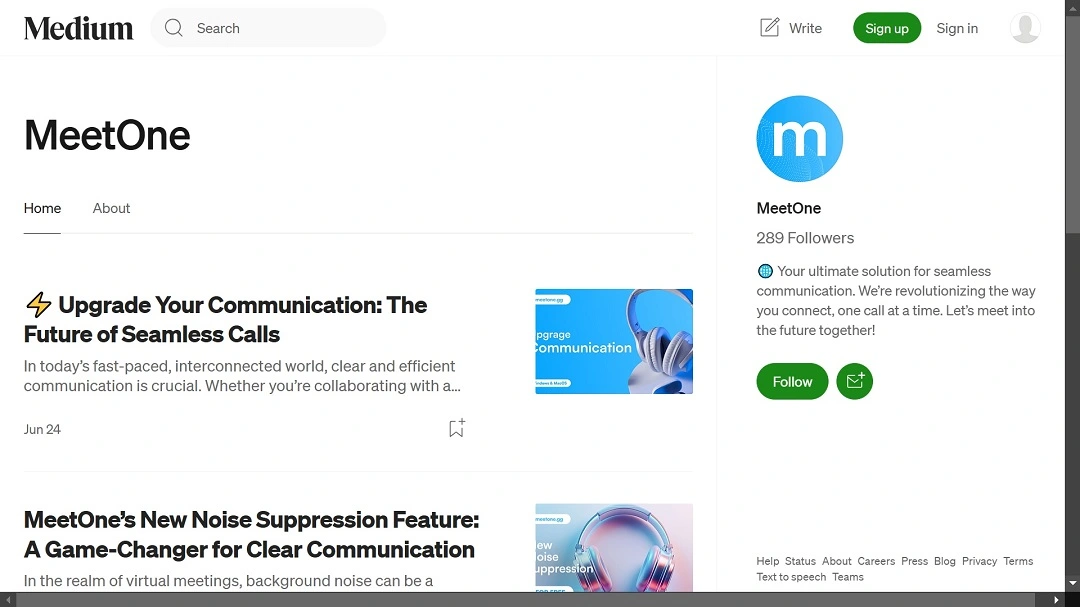
Cado Security reported that to speed up and perfect the process, the threat actor is using AI-generated web content.
Usually, large-scale threat groups will create dozens of domains and leave them active to bait in as many victims as possible. Given that this threat actor is creating one domain at a time while putting the old ones to bed, we can expect this actor to resurface in the near future, possibly impersonating a brand in a different industry.
We have already found evidence that this threat group switches targets. For example, we found that one of the domains linked to this threat actor, Clusee[.]com, leans heavily on the financial sector and not on the blockchain or Web3 industry, as the images below show.
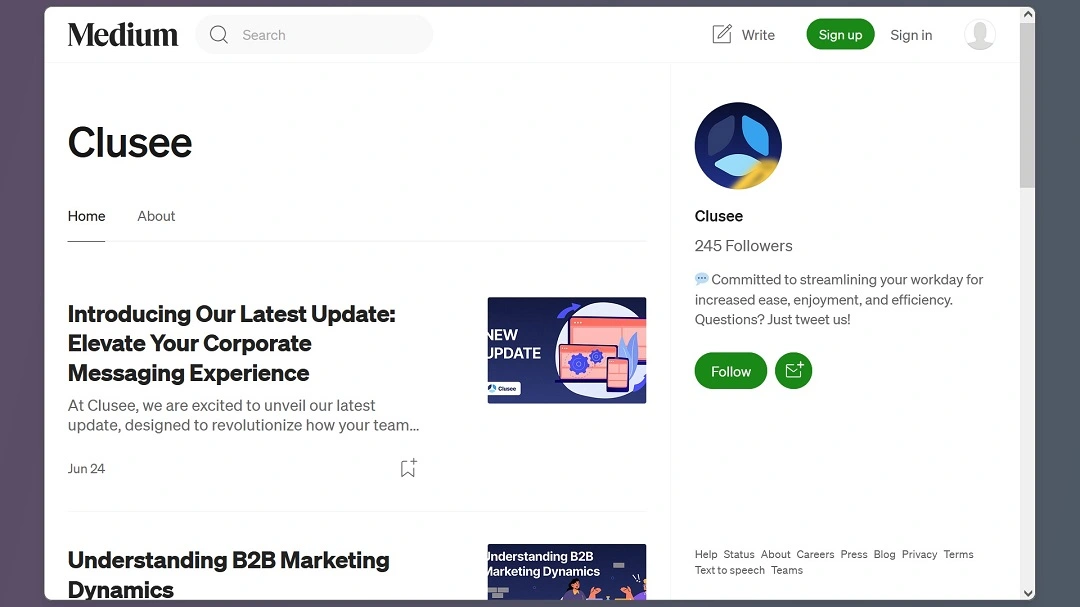
“In order to gain credibility, the threat actors set up full company websites, with AI-generated blog and product content and social media accounts including Twitter and Medium,” Cado Security said in its report.
The swift processing of the Rust-based Realst stealer
Once the Realst stealer breaches a Mac, it immediately begins causing damage. The Realst stealer will go after the following resources:
- Credentials from password stores: Keychain
- Credentials from password stores: Credentials from web browsers
- Web session cookies
- Browser information discovery
- System information discovery
- System network configuration discovery
- System owner/user discovery
- Data from the local system
- Local data staging
- Application layer protocol: Web protocols
Once those commands are executed, the malware begins an exfiltration process of compromised data and sends it over a C2 channel controlled by the attackers.
The speed at which an infostealer like Realst can steal all of this information depends on a number of factors, such as processing speed, evasion capabilities, internet connection, and more. However, on average, an infostealer like Realst will finish exfiltrating all stolen data on the same day it breached a device. This leaves victims with little time to react or even identify anything suspicious.
Cado Security adds that Realst stealer will also steal the following, if available:
- Telegram credentials
- Banking card details
- Keychain credentials
- Browser cookies and autofill credentials from Google Chrome, Opera, Brave, Microsoft Edge, Arc, CocCoc, and Vivaldi
- Ledger wallets
- Trezor wallets
How criminals are bypassing operating systems to run malware
The reason why threat actors behind this campaign can breach all OS variants is because their web infrastructure is coded as a malicious Electron application.
Electron, previously known as Atom Shell, is a free and open-source framework developed and maintained by OpenJS Foundation.
Electron applications are popular among developers due to their cross-platform potential. This means that Electron apps can run most Windows, MacOS, and Linux versions.
How does Electron do this? Electron apps use web browser technologies and programming languages such as JavaScript, HTML, and CSS, which can leverage the vast ecosystem of web development tools and libraries. These technologies are widely supported and optimized for different platforms.
Unfortunately, cybercriminals have caught on to the potential of Electron as well. Cado Security warns that while malicious Electron apps are a relatively new threat, “There has been an increase of threat actors creating malware” with this framework.
Realst Stealer attribution: The missing key
While the Rust-based Realst stealer is not as popular as other macOS-targeting malware like AMOS, it is not new to the scene. In August 2023, Moonlock reported that threat actors were using the malware to target the blockchain and gaming community.
In that cyberattack, threat actors used social engineering, fake blockchain game sites, and phishing to lure victims into downloading the Realst infostealer. Threat actors then also contacted victims to offer them jobs or rewards.
The techniques and tactics for that campaign are almost identical to those of the campaign recently identified by Cado Security. This would imply that the malware is being leveraged by the same threat group for different attacks or being licensed to other cybercriminal gangs on the dark web under malware-as-a-service models.
Despite several scams and cyber incidents, it is unknown who developed Realst, who is using it in live cyberattacks, and whether one or several groups are reselling the stealer on the dark web.
Until attribution is established, putting a final stop to these types of attacks is nearly impossible, as they can regenerate after exposure without hiding in a carefully crafted net of anonymity.
Final thoughts on how to stay safe
There are a couple of simple tips and best practices that developers linked to the gaming, finance, blockchain, and Web3 industries must consider.
First, never store your crypto or finance credentials on your browser. This might save you sign-in time, but it also puts you at significant risk of losing your hard-earned cash.
Second, enable multi-factor authentication (MFA) on all your accounts, with biometrics if possible. MFA is not an impenetrable technology, but it does add a valuable additional security layer to your accounts.
It is also best to enable security notifications. These notifications will SMS or email you when someone is trying to access your account, giving you enough time to take action, change your passwords, and lock the attacker out before they are inside.
Finally, be extremely suspicious of any contact that emerges out of the blue offering you a job. If you believe that the job you are being offered is legitimate, when the employer asks you for a video meeting, use trusted applications only like Google Meet, Apple’s FaceTime, or Zoom. Always make sure you are downloading these apps from trusted and verified URLs.






