As 2024 edges to a close, a new study has found that “scam-yourself” attacks have increased 614% in the past quarter. Not only are these sophisticated automated social engineering attack vectors on the rise, but the study warns that more than 50% of all cyberattacks are now scams.
Scam-yourself attacks rose by 612% in the past quarter
In their recently released Q3-2024 threat report, Gen Digital said they blocked 445 million URLs, 194 million malicious files, and 2.58 billion cyberattacks in the third quarter of 2024. Analyzing attacks against desktop, mobile, and different operating systems, including macOS and iOS, the company found that most attacks are scam-yourself incidents.
“One of the most alarming trends is the rise of ‘Scam-Yourself Attacks’ — an advanced social engineering tactic that tricks users into compromising their own systems,” Gen Digital said.
One of the most alarming trends is the rise of “Scam-Yourself Attacks” — an advanced social engineering tactic that tricks users into compromising their own systems.
Gen Digital
In mobile environments, “scam yourself” cyberattacks amounted to 64.2% of all attacks, followed by malvertising with 25.2%. Similarly, desktop devices saw 50% of scams and 29.9% of malvertising attacks.
“With a staggering 614% increase of these scam-yourself attacks quarter-over-quarter; social engineering, psychological manipulation tactics, continues to be one of the most dangerous tools in the cybercriminal arsenal,” the company said.
The attack starts with an automated scam but ends with an infostealer
While scam-yourself attacks are the predominant vector of attack, infostealers are the trending malware, with a rise in activity of 39% in the past quarter.
Lumma Stealer and AMOS stealers are often used in combination to target both Windows and macOS devices. Under the umbrella of the criminal malware-as-a-service black market industry, these stealers are easy to use, even for less tech-savvy hackers, making the tech dangerously accessible.
Scam-yourself attacks prove social engineering has dramatically changed
Gen Digital dubbed the term scam-yourself to more accurately represent how social engineering has evolved and modernized. While social engineering is usually linked to phishing and other types of SMS, email, website, and social media messaging tactics, cybersecurity researchers are now recognizing that social engineering techniques have come a long way and have evolved.
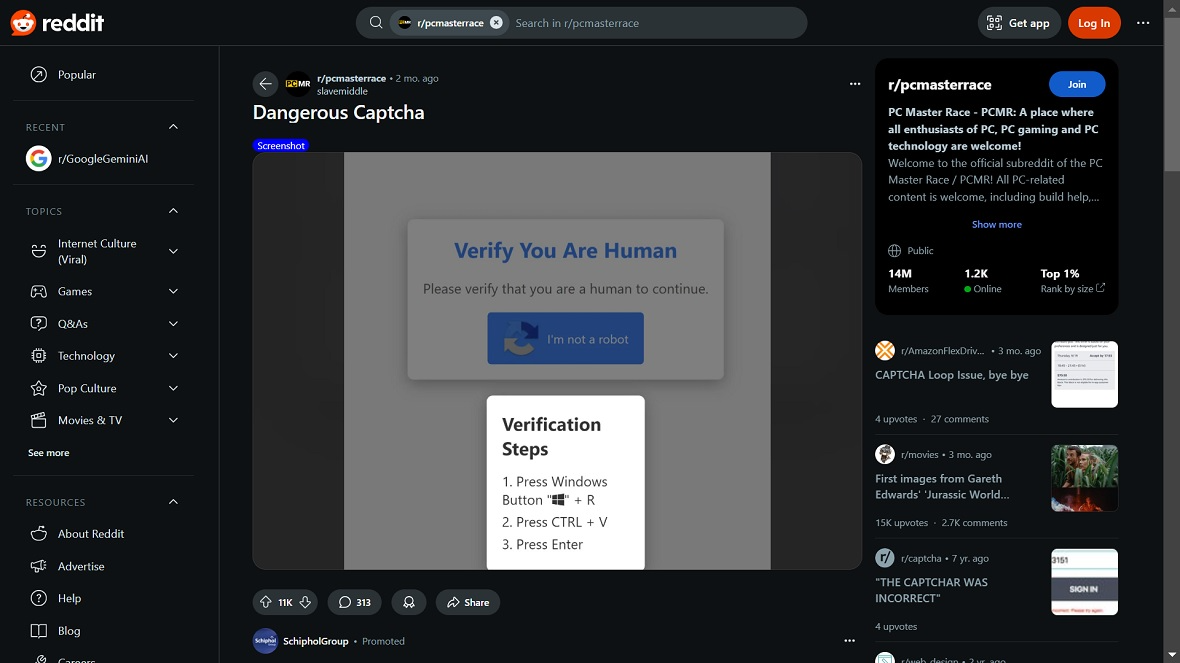
Normal social engineering scams require victims at some point to interact with a threat actor who is there to convince them and guide them through the attack. Scam-yourself attacks, on the other hand, are automated.
Instead of threat actors engaging one-on-one with victims, criminals develop malicious infrastructure that tricks users. Examples of these types of attacks include FakeCaptchas, fake browser updates, fake operating system notifications, and others.
Naturally, scam-yourself cyberattacks are much less expensive to deploy in scale and can reach millions of victims without criminal groups having to recruit scammers or run large illegal scam and fraud call centers.
“The term (scam-yourself) encompasses a variety of threats, from Fake Tutorials to ClickFix scams, FakeCaptcha tricks, and Fake Updates. Together, they form a broader web of deception that’s catching millions of users off guard,” Gen Digital said.
Let’s break down some of these cyberattack trends.
Software downloads with ReadMe.txt files
A common and relatively simplistic technique that cybercriminals are using is the ReadMe attack. Targeting all kinds of users, from gamers to crypto communities to those looking for cracked software, cybercriminals are distributing malware that comes with a simple ReadMe.txt file.
Users who download malware that follows this trend will open the ReadMe file for instructions. The instructions will look quite legitimate but will include fatal commands such as, “Disable your antivirus for this software to work properly.”
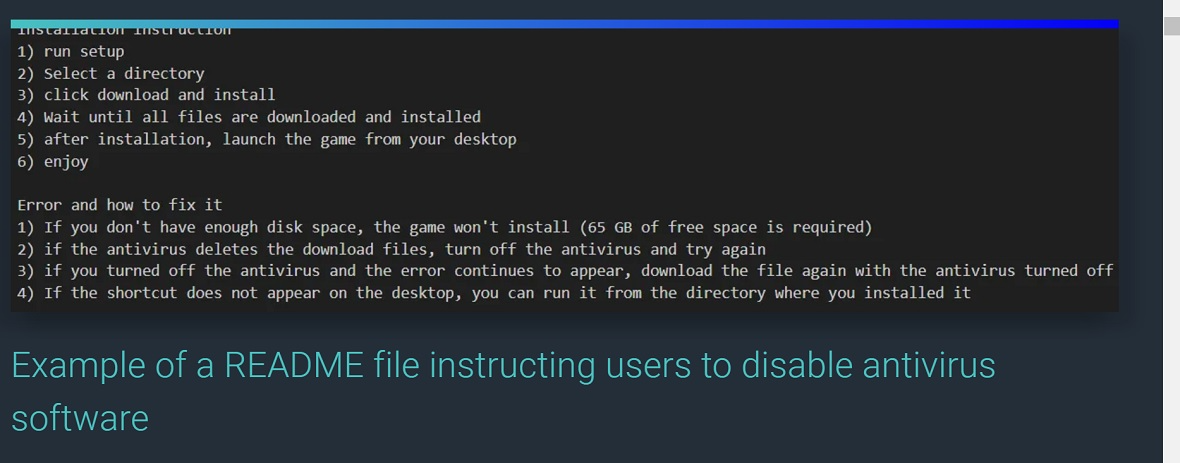
This technique tricks users into bypassing security features that are there to protect them. More advanced threats, such as fake system notifications or browser updates, use the same principle but require more technical development.
Software tutorials on YouTube that distribute malware
Who hasn’t turned to YouTube in search of good advice on how to install or download tricky software at one point or another? Unfortunately, cyberattackers are now using malicious YouTube tutorials to prey on users.
In this technique, criminals walk users through how to install software. The catch? They list download links in the Comments section or in the video description areas that lead to malware.
“What started as a guide to help you ends with your device compromised,” Gen Digital said in the report. “The worst part? You’re the one who clicked, copied, and executed the threat.”
ClickFix, the magical black hat button coded to hack your Mac or iPhone
Another trending scam-yourself tactic is the ClickFix attack, which Moonlock has been following and reporting on for some time now. ClickFix attacks are very diverse. They might attempt to trick users on a specific app like Google Meet or even try to impersonate their own operating systems.
A classic ClickFix message will start out by saying, for example, that an update is needed. Or it may display an error code and then offer options to the victim with buttons that usually read “Click to Fix.”
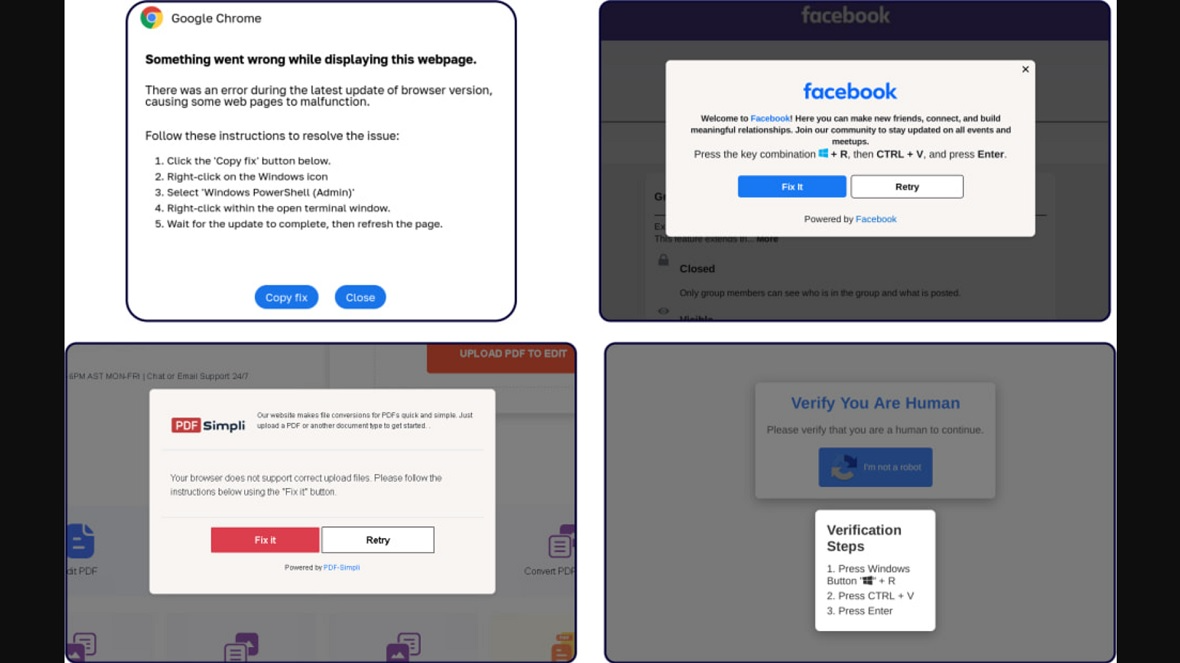
Instead of fixing anything, these buttons are coded to break things. They are automated to copy a script to your clipboard, paste it into the command prompt, and hit Enter, installing malware.
FakeCaptcha and fake updates trends
FakeCaptcha and fake update attacks employ the same basic principles we discussed above.
Black hat hackers have figured out how to code FakeCaptcha pages that blend perfectly into the “normal web browsing” activity. When you complete one of these malicious captchas, what you’re really doing is downloading malware — once again.
Fake update strategies do the same but impersonate a fake browser message that tricks users into believing that their browser is asking for an update.
Final thoughts and strategies for mitigation
While the phrase “scam-yourself attack” isn’t really an established term within the cybersecurity industry, it accurately describes modern social engineering.
These new trends, exploding in popularity among criminals, are coded, deployed, and left to operate by themselves.
The endgame of scam-yourself attackers is to load malware onto your Mac, iPad, or iPhone to later steal your personal data and empty your wallets.
Because these scams are so well designed, it is incredibly hard to spot them. Basically, the same rules prevail. Do not click on anything you have never seen before, double-check updates and permission requests, and stay away from Captcha pages that do not look official or prompt you with suspicious buttons.
A strong password and multi-factor authentication, especially with biometrics, can go a long way, too.






