Fake browser updates are nothing new. Since the early days of the internet, there have been incidences of users landing on sites and receiving warnings that they need to update their browsers. Malware or a virus would then drop on the user’s computer once they clicked on the update to download it. The problem is that this old trick has now been reinvented.
Criminals are hacking an ever-growing list of websites, inserting fake browser update code and using the blockchain to evade shutdown. They are also targeting new users. As Malwarebytes reported on November 21, the criminals behind the infamous Atomic Stealer are now targeting Mac users via a fake browser update chain tracked as ClearFake.
If you get a Safari or Chrome update message, think twice
ClearFake is a fake browser update malware that, at first glance, may seem like nothing special. In fact, we recently reported on a similar fake update. But today, a closer look at the malware reveals it has been evolving rapidly and is reaching dangerous levels.
Malwarebytes assures that it is the first time they see a social engineering campaign, which was previously reserved for Windows operating systems. It has now expanded to target macOS users while simultaneously spreading rapidly globally.
ClearFake was first discovered by Randy McEoin in August 2023. In just a couple of months, this malware acquired Mac distribution capabilities. It was also upgraded numerous times and began using the blockchain to store its malicious files. On November 17, security researcher Ankit Anubhav was the first to discover that ClearFake had gained a foothold in the Mac world.
According to Malwarebytes, these new traits make ClearFake “one of the most prevalent and dangerous social engineering schemes.”
“With a growing list of compromised sites at their disposal, the ClearFake threat actors are able to reach out to a wider audience, stealing credentials and files of interest that can be monetized immediately or repurposed for additional attacks,” Malwarebytes reports.
Why is ClearFake so different?
ClearFake is effective for several reasons. Most Mac and iPhone users believe that very few pieces of malware can breach their devices. Attackers leverage the trust that users place in Apple security and use it to their advantage.
Having found a way to distribute malware to Mac users, ClearFake attackers are hijacking and hacking a long list of websites to reach large audiences.
These criminals are also using blockchain smart contracts to hide malicious code. Atomic Stealer previously used Cloudflare to host malware. However, Cloudflare blocked its hacked sites. In response, they switched to hiding code in blockchain smart contracts.
The malicious code in the smart contracts is linked to hacked websites and used to run a complex and coordinated malware attack and delivery. All a victim needs to do is click on the fake “Update your browser” button to have the malware installed on their computer. ClearFake attacks also send data to the Atomic Stealer command and control server.
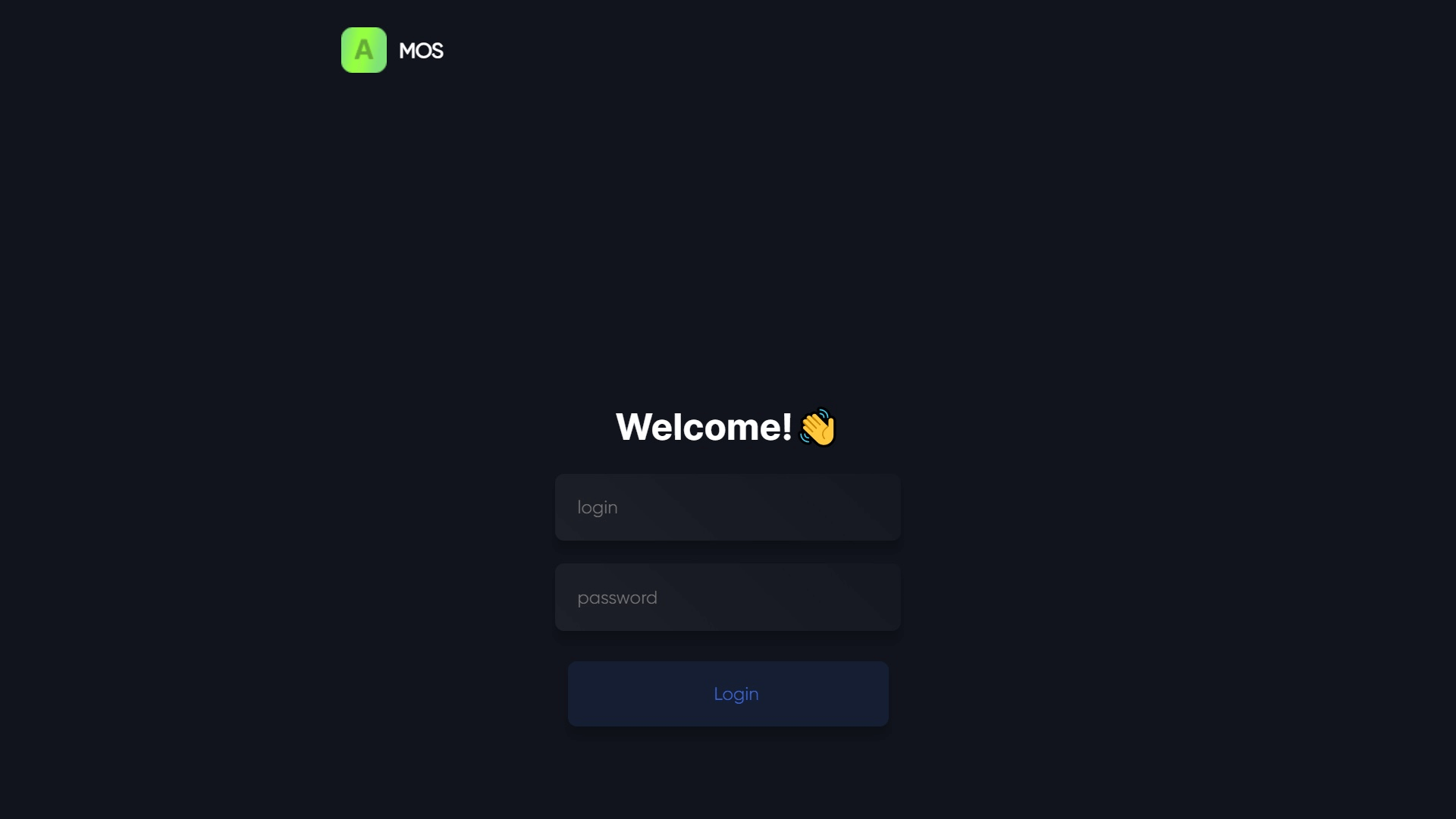
From a Mac user’s perspective
If you are a Mac user and experience this attack, it will unfold as follows:
- You will be online and unknowingly reach a ClearFake hacked website.
- Once the hacked website loads, you will get a legitimate-looking message that claims to be from Safari, Chrome, or another browser asking you to update the browser.
- If you click Download or Update, you will be prompted to follow what seem to be official Safari or Chrome instructions to download and install the malware.
- If you follow those instructions, the Atomic Stealer malware payload will be automatically installed on your device.
Atomic Stealers can steal credentials, breach accounts, steal browser data, steal data from crypto or e-wallets, steal credit and debit card numbers, modify files, take over users’ computers, and much more.
Is malware hiding on the blockchain?
Atomic Stealer made headlines due to its ability to trick victims by using fake Google ads, banners, phishing websites, and malicious apps. Now, through ClearFake, this malware can pose as a Safari or Chrome update message for Mac users. But that isn’t the only dangerous evolution that ClearFake attackers created. Hackers are also using the blockchain to store, hide, and execute malicious code.
ClearFake attackers are using Binance’s Smart Chain contracts. Nati Tal and Oleg Zaytsev of Guardio Labs called this blockchain-malware technique “EtherHiding.” They report that it is a “novel twist on serving malicious code.”
Storing malware on the blockchain solves a longstanding problem for cybercriminals — the constant takedown and shutdown of platforms where attackers store malware. To get around this, criminals have hidden malware in the strangest of places. These include the dark web, hacked WordPress sites, the CDN of Discord, Telegram channels, and platforms such as Cloudflare.
Cybercriminals are using next-level tactics
A persistent problem facing cybercriminals is that as soon as attacks become successful and draw attention, the sites where they store the malware are blocked or taken down. In response, they have begun hiding malware or malicious code chains on blockchain smart contracts. Guardio Labs calls this “the next level of Bullet-Proof Hosting.”
This method is anonymous, has no limitations, is decentralized, and is easy to access for criminals. The code of smart contracts is also virtually impossible to see by non-authorized users or third parties.
ClearFake attackers hack WordPress sites and embed code that directs traffic to Binance-controlled servers. The process creates a new Binance contract. This is controlled by the attacker, which establishes the functions and structure of the Binance smart contract. The contract runs, returning a specified malicious payload that is later decoded and evaluated as JavaScript code.
Malware on the blockchain stored using this technique cannot be blocked, taken down, or changed. In fact, the actual code used to compile the contract is virtually impossible to see.
How to protect yourself against fake browser updates
ClearFake has managed to put Safari users at risk. Still, there are several things users can do to protect themselves.
It’s important to understand that Safari is built into macOS, iOS, and iPadOS. Therefore, when your operating system is updated, Safari is updated too. Furthermore, Apple’s operating systems update automatically.
You can still update your Safari to the latest version by going to the Apple menu in the corner of your screen and selecting System Settings. Click General in the sidebar, then click Software Update on the right. This update is done through Apple’s Software Update and includes not just Safari updates but all OS updates. In short, there is no scenario in which you will be asked by Safari or by Apple to update your Safari while browsing the web.
Additionally, the best defense against fake browser updates is not to fall for known tricks. If a website is asking you to update Safari or even Chrome, it is likely a cyberattack unfolding. You can avoid potential damage by simply not clicking anything and closing the page.
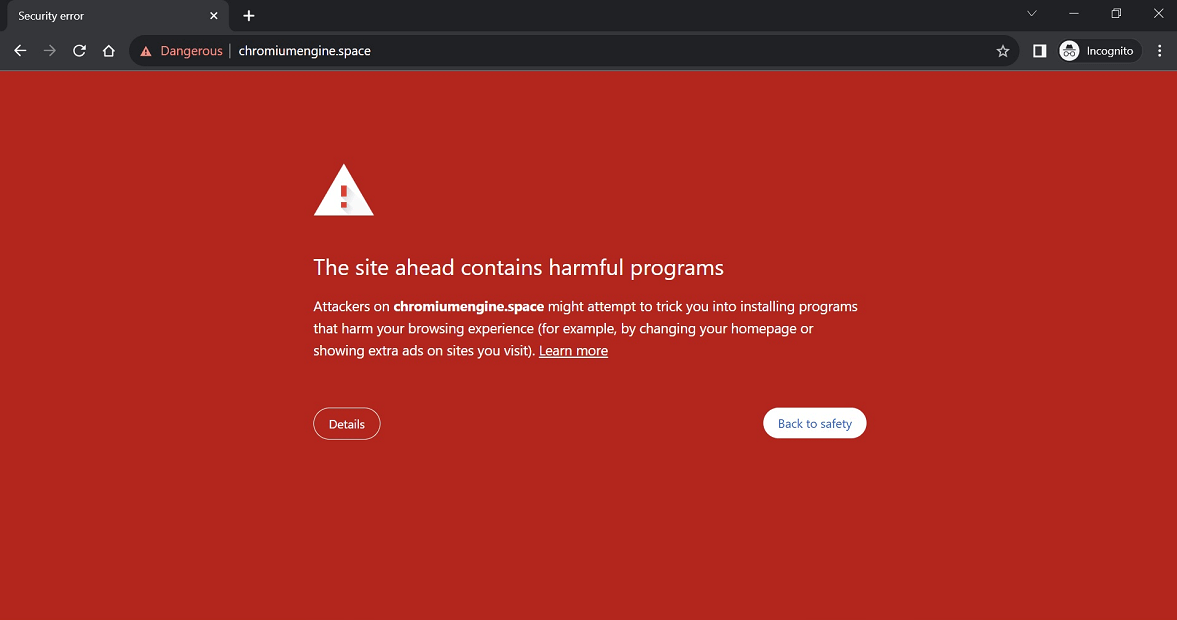
It is important to pay attention to any warnings your browser may display. If Safari or Chrome tells you a site is suspicious or unsafe, do not ignore the red flag and close the site. To create additional security layers and increase your safety, set your browser settings to the most secure configurations.
Always keep your operating system, apps, and software up to date. Additionally, do not save passwords or other sensitive data on your browser. A trusted anti-malware can also help you by identifying, shutting down, and removing malware in real-time.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Safari, macOS, and iOS are trademarks of Apple Inc.






