Think about the last time you opened a website and found yourself already logged in. Or maybe you recently revisited a site and discovered that your preferences were still there, days or even weeks later. This happens thanks to browser cookies. But even a helpful feature like cookies can be exploited by bad actors. This is the case with cookie theft.
Cookies are simple identification tokens that let a website recognize you when you visit it for the second time. They help you skip having to repeatedly log in and keep a record of your last visit. But what happens if someone manages to steal your cookies? Here’s everything you need to know.
What is cookie theft and cookie hijacking?
Cookie theft, also known as cookie hijacking, is a type of cyberattack that targets the cookies stored in your web browser. The attacker can then use those cookies to trick websites into thinking they’re you, thus bypassing the necessary authentication steps and gaining access to your account.
Cookie theft is also referred to as “session hijacking” because the attacker uses the information in the cookies to access a website in the particular state in which you last left it. That way, instead of accessing the site as a new user, the attacker can retrace your steps, making the site think it’s you in the middle of a normal browsing session.
Can cookies be exploited, and are they a security risk?
Cookies themselves aren’t dangerous. In most cases, accepting a trusted website’s cookies will make your online browsing experience more convenient. However, that’s not to say they can’t be exploited by malicious individuals.
Privacy concerns regarding cookies are nothing new, as every time you accept cookies, you’re leaving a small trail of information behind. While cookies are normally harmless, the data they contain may be sensitive. If, for example, an attacker were to gain access to the cookies used for a particularly sensitive website like your bank or social media account, they could steal your financial information or lock you out of your account.
There are many types of cookies, ranging in purpose from marketing and analytics to site performance. But the cookies responsible for user authentication are often the ones being targeted by cybercriminals. In 2018, almost 50 million Facebook users risked losing access to their accounts. This came after the company was affected by a breach targeting user access tokens.
How cookies are stolen
Companies aren’t the only targets of cookie theft. Even individual users can have their cookies stolen and their online sessions hijacked.
There are many ways that attackers can gain access to your cookies, including:
- Phishing attacks: Site cookies are typically stored in your browser, whether on your iPhone or your Mac. Attackers can organize session phishing schemes that grant them access, so they can read and compromise the cookies stored in your browser.
- Man-in-the-middle (MITM) attacks: Attackers can take advantage of unsecured Wi-Fi networks to intercept your internet connection, allowing them to see and read everything you’re doing online. This includes storing copies of the cookies you accept from websites.
- Cross-site scripting (XSS): Instead of targeting you directly, attackers can target a vulnerable website by injecting malicious code into it to steal the cookies of everyone who visits the site or logs into their accounts.
- Malware: In the event that your device is infected with malware or trojans, usually spread through infected download links and email attachments, the attackers can gain access to different parts of your device. This includes your browser, where your authentication cookies are stored.
Stay one step ahead of malware
Cookies being stolen is quite a common occurrence, and unfortunately, it usually happens long before you notice anything’s wrong.
The easiest and simplest way to stay protected is with a dedicated security app designed specifically for macOS. Moonlock will rid your Mac of any existing malware threats and keep you protected from new attempts at gaining entry to your device.
This is what Moonlock was built for! It utilizes a robust Malware Scanner to search every part of your system and its files, including hidden and dormant files, along with old downloads and email attachments. Its Real-Time Protection also works 24/7 to prevent malware from entering your system by quarantining threats the minute they are detected. To get the peace of mind you are looking for, try Moonlock for free today.
Signs of cookie theft and session hijacking on your accounts
Cookie theft isn’t a particularly quiet type of cyberattack. If you know what to watch out for, you can easily recognize the signs of a cookie stealer and act before it’s too late.
Unexpected account activity
You should be able to account for all account activity. Whether it’s a new post you didn’t make, a direct message you didn’t send, a small, unauthorized financial transaction, or a login attempt from a device or location you don’t recognize, these are signs that someone has accessed or is trying to access your account, and you shouldn’t ignore them.

Other account activity can be more subtle, like changes to your account settings. Are you receiving fewer notifications, or has 2-factor authentication been disabled without your knowledge? It’s important not to ignore any suspicious activity and to further investigate the cause.
Notifications of login attempts
Cookies aren’t a clear-cut way into your account, but they can be of great value to cybercriminals. As attackers attempt to secure access to your account, you’ll likely receive push notifications, in-app notifications, emails, or text messages informing you of the failed login attempts, the associated IP address(s), and the device(s) used.
This is a clear indicator that while your account remains secure for the moment, someone is targeting you. You’ll need to reset your browser, delete all cookies, and change the password on the targeted website.
Unexpected password reset notifications
Like attempted login notifications, password reset notifications are a sign that your account is still safe but you’re being targeted.
Password reset notifications imply that, through a data leak, a phishing scheme, or cookie theft, someone was able to obtain the username, email, or phone number you use to log in to a website. Now, they are trying to access that account through password recovery.

What to do if you think an infostealer is stealing your cookies
If you’ve noticed one or more of the 3 signs of session hijacking, don’t panic. While it might be distressing to learn that you’re being targeted by an infostealer, you can still take the necessary steps to mitigate the damage.
Run a malware scan
Don’t try to guess when or how your device has been hacked or infiltrated. Run a malware scan using cybersecurity software you trust to detect the vulnerabilities and any current issues on your Mac.
We strongly recommend using macOS-specific cybersecurity tools when scanning for malware on your device. Moonlock can identify and neutralize malware that doesn’t want to be found, including threats that target your browser cookies and authentication tokens.

Here’s how to get rid of an infostealer:
- Sign up for a free trial of Moonlock and download the app.
- Open Malware Scanner.
- Run a Deep Scan. This is the most invasive type of scan and will find every suspicious file on your system.
- Anything that is found will be moved to Quarantine.
- Results will be ready to review once the scan is complete.
Moonlock will analyze your system files, browser data, and downloads to uncover any cookie-stealing malware. Protect your Mac with confidence and run a free malware scan with Moonlock.

Mass logout and reset your passwords
By the time you notice and address a cookie hijacking issue, a malicious actor might’ve already gained access to one or more of your accounts, so you’ll need to act fast.
First, access the settings of your compromised accounts and force a logout on all devices, starting with higher-risk accounts like your bank.
You’ll then need to set new passwords for your accounts, as the attacker might already know them. If possible, enable 2-factor authentication on your accounts and make sure you’re receiving notifications for login attempts, both successful and failed.
Clear your browser cookies
If you suspect a malicious party has hijacked your session, your best course of action is to clear all cookies on your browser on your iPhone and on your Mac. This renders all the cookies the attacker might’ve collected from your older sessions useless, ensuring that those cookies can no longer be used to impersonate you online.
On your Mac, open Safari and click on the Safari menu. Select Settings from the drop-down menu.
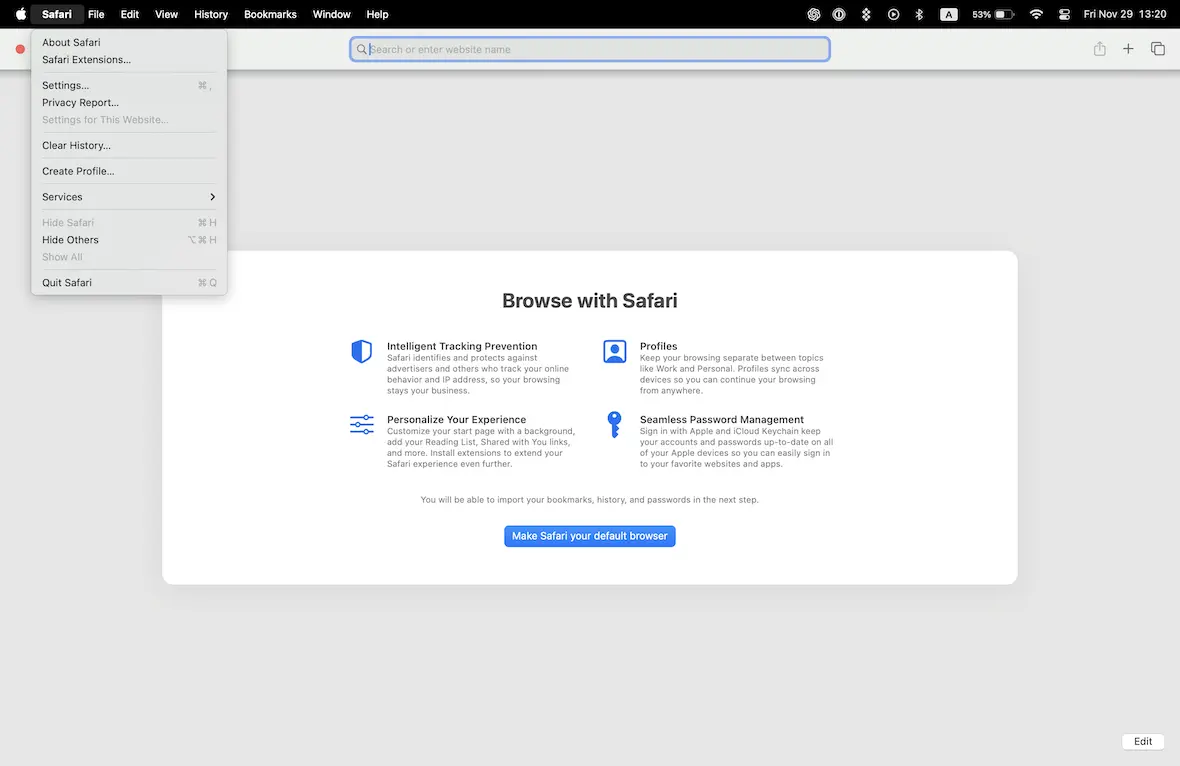
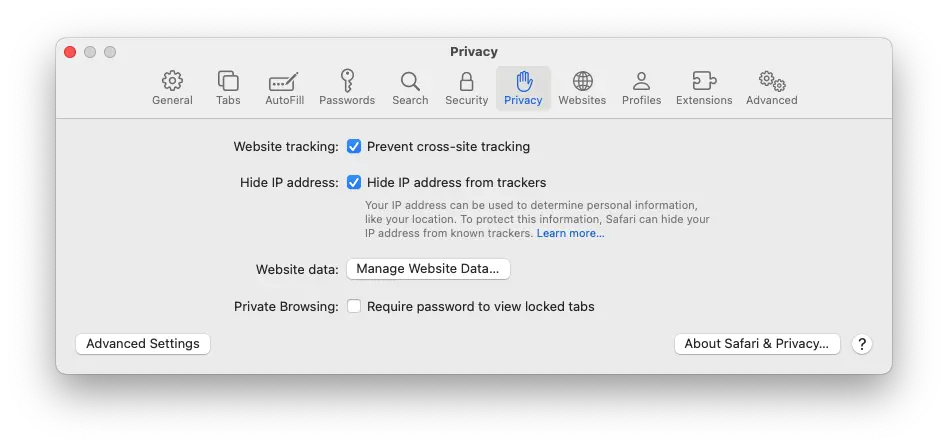
This will open a new window. Navigate to the Privacy tab. Then click Manage Website Data.
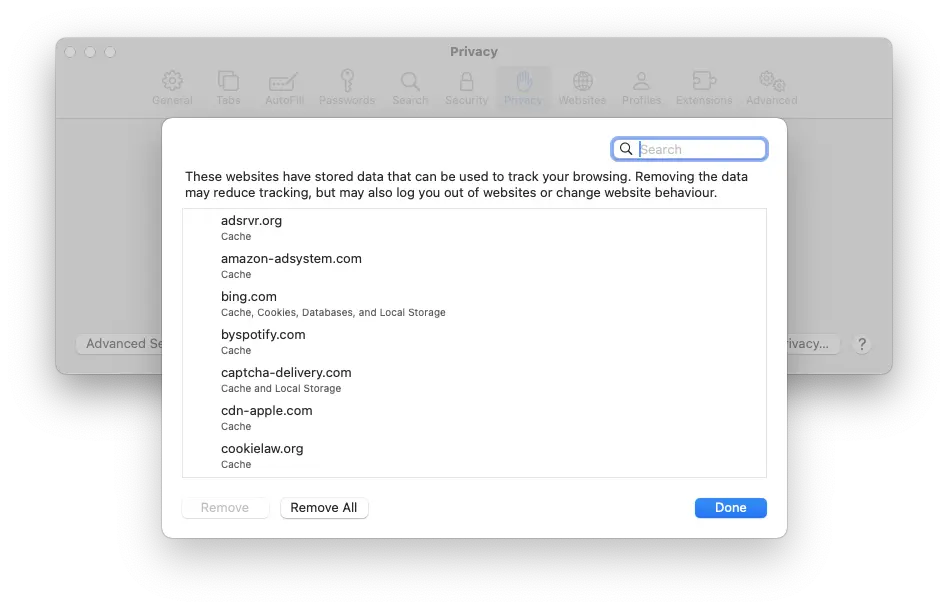
A smaller window will open. This contains a list of all the cookies currently stored in your browser. Click Remove All.
A small pop-up window will ask you to confirm your choice. Click Remove Now.
This course of action doesn’t just apply to Safari. You should clear the cookies on whatever browser you prefer to use on your Mac.
Note that after clearing browser cookies, you’ll need to manually log back in to all your accounts. Also, note that any site preferences you might have had, like chosen themes or fonts, will be reset to the original site configurations.
How can you prevent cookie and session hijacking?
It’s important to know how to act in the case of a session hijacking incident, but you’re better off preventing this type of exploit altogether. Luckily, there are a few easy things you can do to keep yourself safe, including:
- Avoid unsecure public Wi-Fi: Hackers can employ MITM attacks over unsecured networks to intercept and monitor your network traffic. If you must use public Wi-Fi, pair it with a VPN you trust.
- Use HTTPS everywhere: Make sure all sites you visit or log in to use HTTPS, shown by a padlock in your browser.
- Use Moonlock’s Security Advisor: This tool analyzes your system’s security and detects any weak spots that could be taken advantage of. It then provides recommendations to boost your security in plain language — you will not need any security certifications to follow the instructions! By doing this, you’ll strengthen your protection against cookie theft and session hijacking while improving your overall Mac security posture.
- Regularly clear browser cookies and cache: Getting rid of cookies reduces your trail. This can help safeguard your data if a website you regularly visit is compromised or if your device gets infected with malware down the line.
- Log out of sensitive accounts: Don’t just close the browser when you’re done with your bank; log out entirely to end the session.
When it comes to browser cookies and cookie theft, the most important thing is to stay vigilant regarding your online activity. Familiarize yourself with your device and the websites you regularly use. That way, you can more easily tell when something’s wrong.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac, MacBook, and Safari are trademarks of Apple Inc.






