A threat actor is using X (formerly Twitter) to distribute links to a fake AI video generator website that hosts malware. The malware in this campaign are infostealers, and they can breach Windows and macOS computers alike.
Cybersecurity researcher identifies AMOS stealer distribution campaign leveraging X
On November 15, cybersecurity researcher @g0njx warned via Twitter that a threat actor was impersonating the EditProAI site. This was the first discovery of this threat campaign in the wild.
The impersonation of popular AI image and video generators is not a new development. Since the beginning of the AI hype, cybercriminals have been using AI as bait because the tech attracts a lot of potential targets.
This campaign, however, is not only leveraging the AI revolution. The post on X seizes on interest in the recent United States presidential election by featuring a fake AI video that went viral on social media, in which President Donald Trump and President Joe Biden “spend time together as friends.”
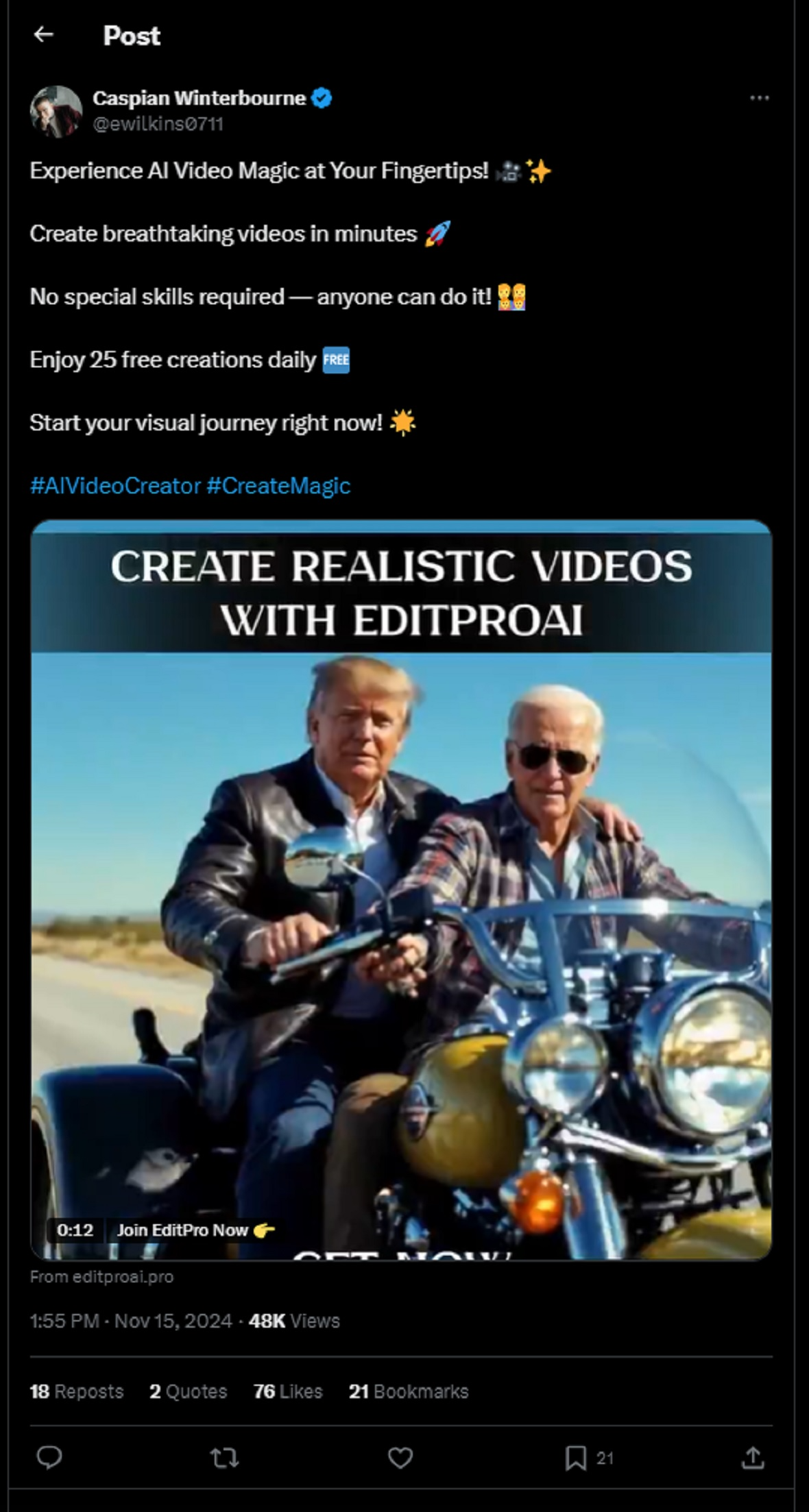
The post distributing the fake EditProAI video generator has 48K views and was reposted 18 times. It is unclear but likely that the distributor of the malware created similar posts on other sites, forums, and social media platforms. However, these have not been discovered.
The malware being distributed can empty your wallet and steal your data
The infostealers used by this threat actor are Lumma Stealer for Windows victims and the infamous AMOS for macOS. Once AMOS breaches a Mac, it can steal cryptocurrency wallets and cookies, credentials, passwords, credit cards, and browsing history from Google Chrome, Microsoft Edge, Mozilla Firefox, and other Chromium browsers.
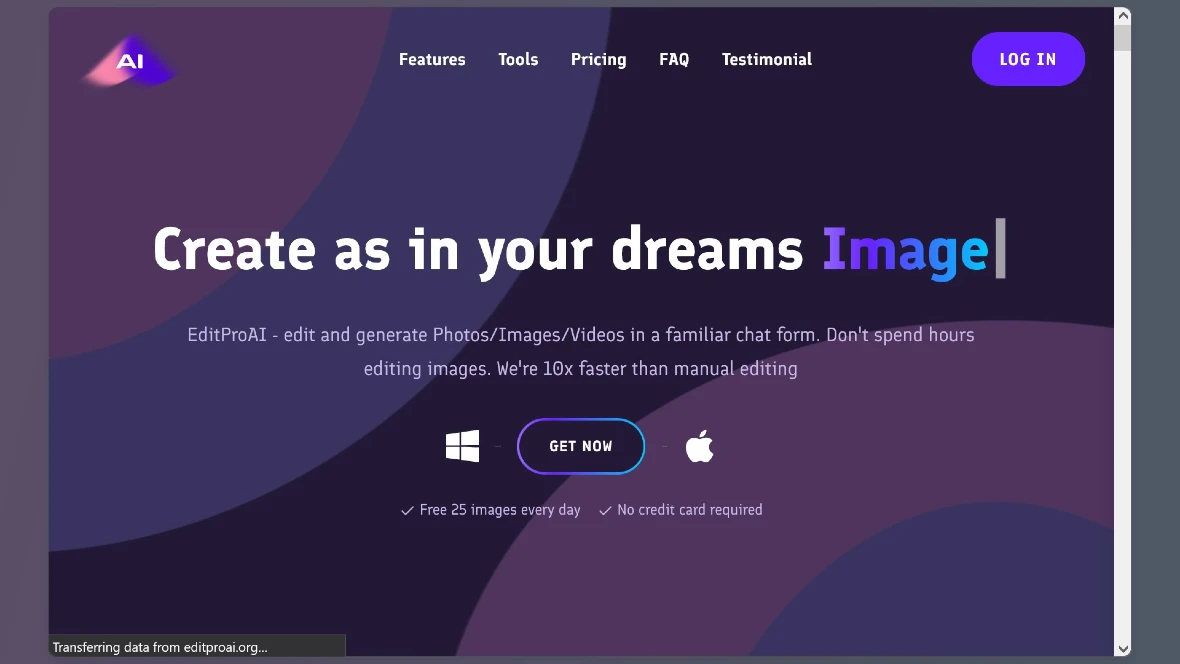
The X post directs Apple users to the editproai[.]org site. Once again, we can see how cybercriminals have mastered web design and can easily get away with operating malicious sites that appear legit. This site looks almost exactly like the real thing.
Users who click the “Get Now” button on the malicious site will download the infostealer. We have seen this type of campaign time and time again, yet it is easy to see how people would click on these types of links.
Here are the sites Mac users should stay away from and browser companies should block
Domains linked to this campaign are:
- editproai[.]pro (Windows)
- editproai[.]org (MacOS)
- Admin panel -> proai[.]club/panelgood/
A not uncommon but easy-to-access C2 server
The panel discovered by g0njxa at “proai[.]club/panelgood/” is used as the gateway into the C2 attacker-controlled servers where the infostealer exfiltrates the stolen data from breached devices.
This panel is not uncommon for infostealers, especially AMOS. However, in the past few months, most C2 analyzed in cyberattacks are hosted only on IP addresses.
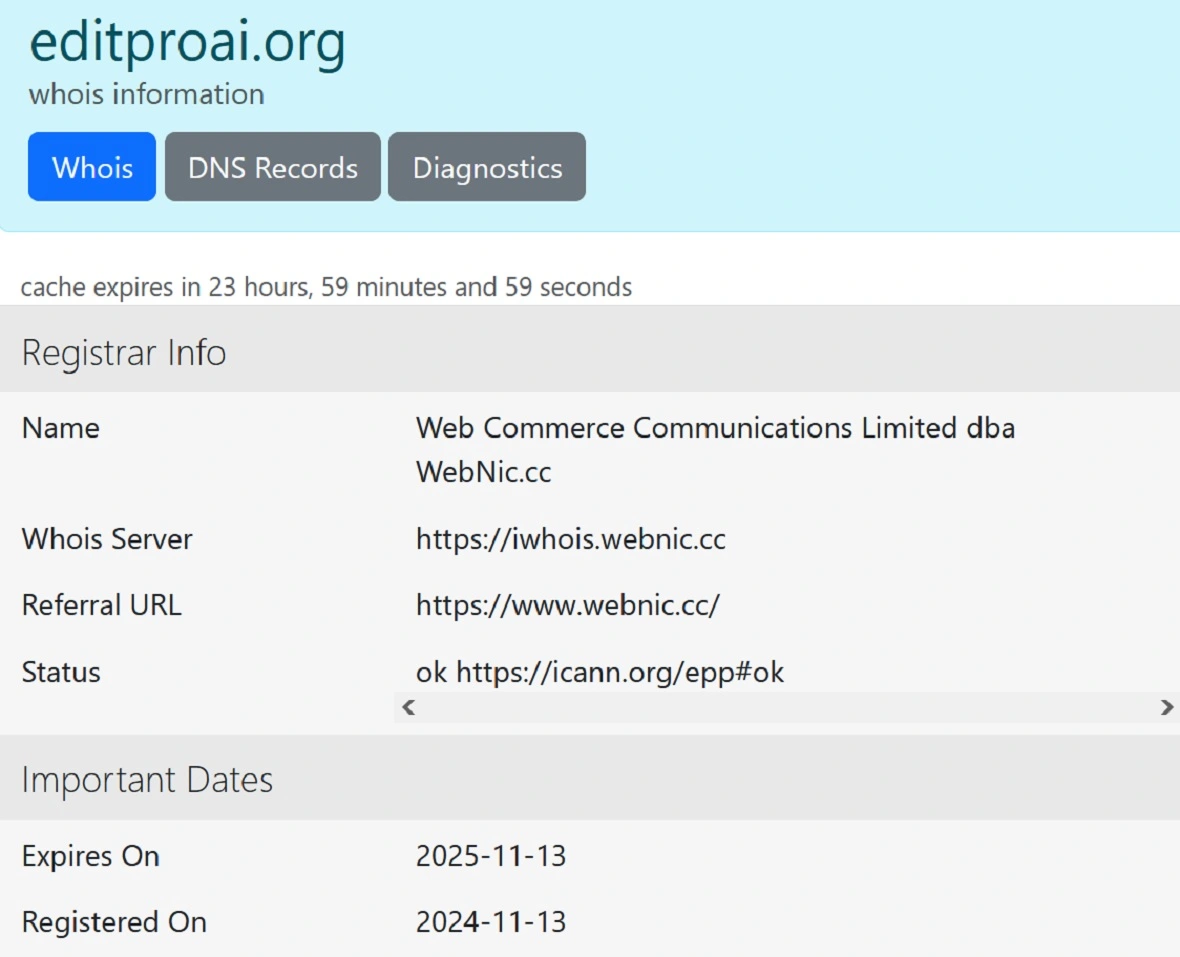
WHOIS information checked by Moonlock found that the IP associated with this campaign is linked to the Australian territory of Cocos (Keeling) Islands (.cc).
Moonlock has previously linked .cc servers to a pig butchering scam campaign that hit Asia, Europe, and probably America. Pig butchering scams have been linked to transnational cybercriminal Asian organizations, or “Asian organized crime groups,” as the United Nations describes them.
How small-scale threat actors manage to create sophisticated campaigns
Compared to large-scale malware distribution campaigns on social media that Moonlock has covered, this new infostealer campaign has been linked to only a small number of websites, domains, and IPs.
This could be a sign that the threat actor is a small-scale operation developed by a small team. This could even be a one-man operation, as the infostealers used in this cyberattack can be bought by anyone on the dark web.
Not only can threat actors buy or lease macOS infostealers on the dark web, but under the malware-as-a-service model, those who buy these criminal tools are often offered support, resources, and step-by-step guides on a wide range of things. For example, dark web malware distributors can guide threat actors on how to set up C2 servers, trick browser security so the site is not flagged, and much more.
Small-scale malware distribution campaigns can also go undetected longer than larger ones. While one small campaign does not cause enough damage to raise red flags, a combination of several small campaigns can have the same effects as large-scale operations.
Then again, this infrastructure could belong to a more inexperienced threat actor in the process of building and scaling.
Final thoughts on deepfake impersonation
Impersonation campaigns online have become so highly effective at subtly blending in with real content that they have high success rates. Nothing about the chain of this attack would raise a red flag except for the URL of the malicious site itself — if a user were to look at it closely.
The cybersecurity mantra “never click on links or download anything” is the only backstop users have today as social media companies prove that they cannot handle malicious actors and web search engine companies fail to flag malicious sites. Infostealers like AMOS may have a high price tag on the dark web, but virtually anyone can get their hands on it if they want. And that is a big problem.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






