A new campaign exclusively targeting macOS developers was spotted in the wild. The threat leverages a popular attack chain that includes malvertising, abuse of the Google Ads platform, fake phishing sites, and download of the AMOS Stealer.
The threat campaign apparently was active for just a couple of days. It began on January 17, was flagged by a developer on X (formerly Twitter) on January 18, and was resolved by January 20.
While the attackers’ infrastructure was short-lived, the reach of this malware distribution campaign may have been significant due to the popularity of Homebrew among Mac developers.
Before we dive into the details, if you recently installed HomeBrew on your Mac, we suggest you check the /temp/update folder, where the malware payload downloads. If you find anything in that folder that should not be there, run a trusted anti-malware tool. Also, be ready to back up your system and data and do a factory-reset to remediate the issue as a last resort.
MacOS developers targeted in new AMOS Homebrew threat campaign
On January 17, the Canadian-based developer Ryan Chenkie warned in an X post that Google was “serving” malicious ads that impersonated Homebrew. If you aren’t familiar with HomeBrew, it is a popular package manager for macOS.
macOS developers use Homebrew to install, update, and manage a wide range of software tools and applications directly from their terminals. Homebrew provides access to an abundant library of open-source software, including programming languages (Python, Ruby, Node.js), databases (PostgreSQL, MySQL), build tools, and more.
Developers have become a prime target among cybercriminals, as they are believed to host blockchain and cryptocurrency assets and sensitive data that attackers can leverage.
The motive behind this campaign is likely financial. The malware being used is the AMOS stealer, available for black hatters on the dark web and coded to extract data from browsers and empty crypto accounts.
None of the techniques used in this cyber threat campaign are new, original, or unique. We have reported extensively on how cybercriminals abuse Google Ads, the efficiency of the malware-as-a-service stealer AMOS, and how black hatters develop fake phishing sites to trick users into downloading malware or running malicious commands or scripts.
How does the Homebrew AMOS attack chain work?
Let’s take a look at the step-by-step technical rundown for this “hit and run” guerrilla tactic cyberattack. This is how the black hatters behind this campaign developed the attack chain.
Step 1: Potential victims search on Google for Homebrew and get back a sponsored top-result Google Ad that looks identical to the legitimate site. Having an ad blocker and enabling it will prevent users from seeing this ad, so we recommend that you get one. Also, try to avoid clicking on Google Ad links.
Step 2: Users are redirected to a fake Homebrew site. The URL address is almost identical to “Brew.sh,” but if you look closely, you will see that it has an extra “e” and reads “Brewe.sh.” This small difference makes URL visual verification challenging for victims.
Step 3: On the fake Homebrew page, victims are prompted to run the command to install Homebrew. This is normal, as Homebrew is not a downloadable file but runs directly through Mac’s terminal.
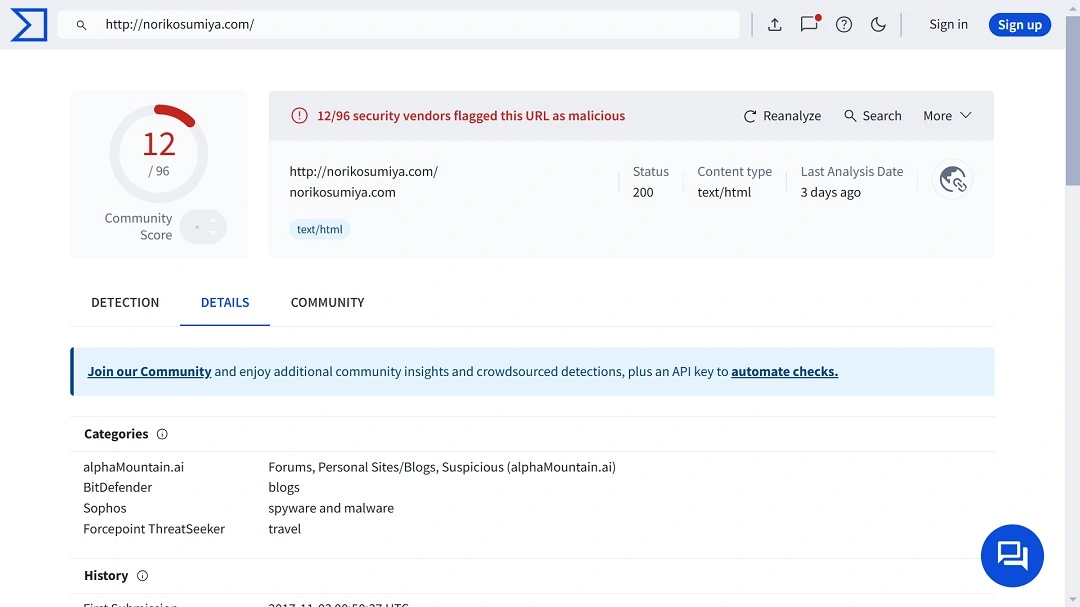
However, this is another subtle, nefarious change. The original Homebrew page directs to a GitHub repository (https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh), while the malicious command redirects users to a strange site (hxxps://norikosumiya[.]com/brew/update).
We admit the difference between a GitHub link and a norikosumiya[.]com link is rather significant. Still, it’s easy to see how anyone can fall for this impersonation hack during a normal, busy work day.
Step 4: Those victims that run the command to hxxps://norikosumiya[.]com/brew/update trigger a download of the AMOS stealer, breaching their device.
Note that hxxps://norikosumiya[.]com/brew/update is now defunct, but this does not mean you should let your guard down.
macOS developers take to social media to express frustration against Google Ads’ lack of security
The original X post that flagged this new AMOS threat, published by Ryan Chenkie, got 1.2 million views, 2.9 thousand reposts, and over 270 comments.
This level of engagement is not common on cybersecurity social media posts that sound the alarm on new threats. This proves that the reach that the bad actors may have had is significant. It also signals the popularity of Homebrew among the macOS community.
On X, countless macOS developers expressed their frustration over the lack of Google Ads’ security policies, which once again failed to protect users.
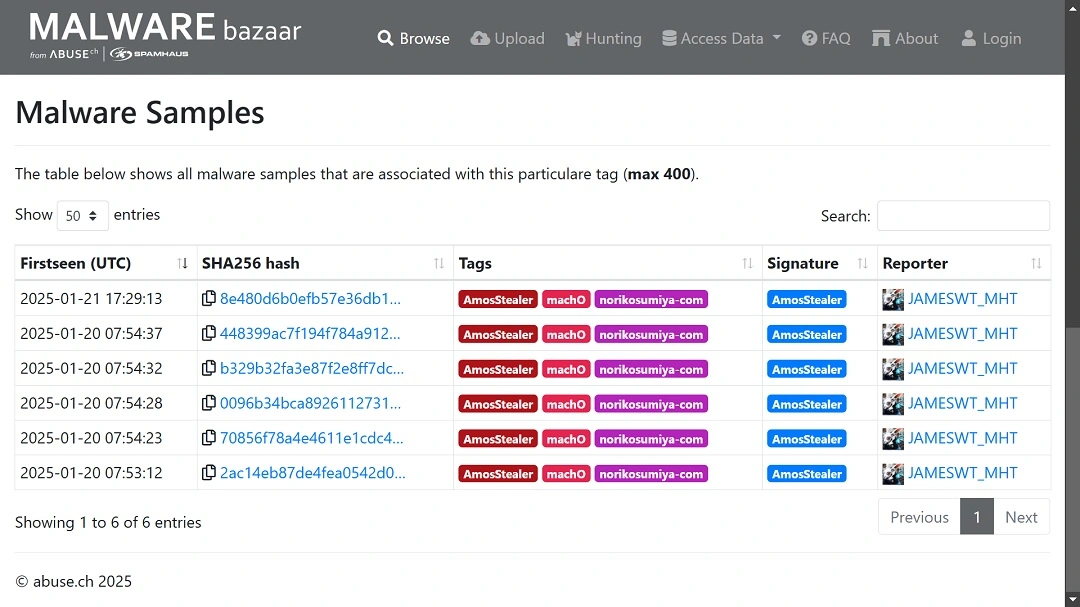
On January 20, 3 days after the initial report, the independent malware hunter JamesWT linked this campaign to AMOS. Also on X, he shared scans of samples from Malware Bazaar.
That same day, HomeBrew project leader Mike McQuaid published a post saying that the issue seemed to have been solved.
Echoing the thoughts of the macOS developer community, McQuaid said, “There’s little we can do about this really, it keeps happening again and again and @Google seems to like taking money from scammers.”
Why we will see more of these threat campaigns in the future
This AMOS malvertising distribution tactic is an attack-rinse-and-repeat style technique. Countless campaigns leveraging precisely the same methods have already been spotted in the wild.
These types of threats are on the rise because the AMOS stealer’s developers and distributors offer the malware to anyone on the dark web. The widespread accessibility of this malware — and the challenge of attribution that cybersecurity researchers face — have driven AMOS cyberattacks for the past year.
Malvertising: Google individual and business account takeovers
The abuse of ad platforms such as Google Ads is also fueling these cyberattacks. Criminals will create new Google Ads accounts or take over business and individual accounts that run ads on Google. Account takeovers are also on the rise.
On January 15, Malwarebytes reported that they had found the “most egregious malvertising operation” they had ever tracked.
In this campaign, Malwarebytes found that to hack into Google Ads accounts, criminals use malicious Google Ads, a rather ironic fact. According to Malwarebytes, this campaign is affecting thousands of customers worldwide.
Again, figuring out who is behind these small AMOS distribution campaigns is extremely challenging, as they continually pop up in an endless game of whack-a-mole.
Final thoughts
This is not the first (and will not be the last) threat campaign that uses malvertising, abuses Google Ads, and distributes the AMOS stealer.
Targeting macOS developers is a criminal trend that is picking up momentum. For developers and users, we recommend avoiding clicking Google Ads, double-checking URLs, and keeping an eye on breaking cybersecurity news to stay one step ahead of cybercriminals.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. or Google LLC. Mac and macOS are trademarks of Apple Inc. Google Search and Google Ads are trademarks of Google LLC.






