Malware is an ever-increasing threat to users on Mac and Windows ecosystems alike. Understanding the many varieties of cyberattacks can seem daunting, but when it comes to macro viruses and macro malware, you can think of them as malicious code that abuses legitimate tools in popular software suites.
While macro attacks have been fading out — with JavaScript attacks taking over in their place — macro cybersecurity remains as important as it has ever been. Let’s dive into macro viruses, what they do, and how to get rid of them.
What is a macro virus?
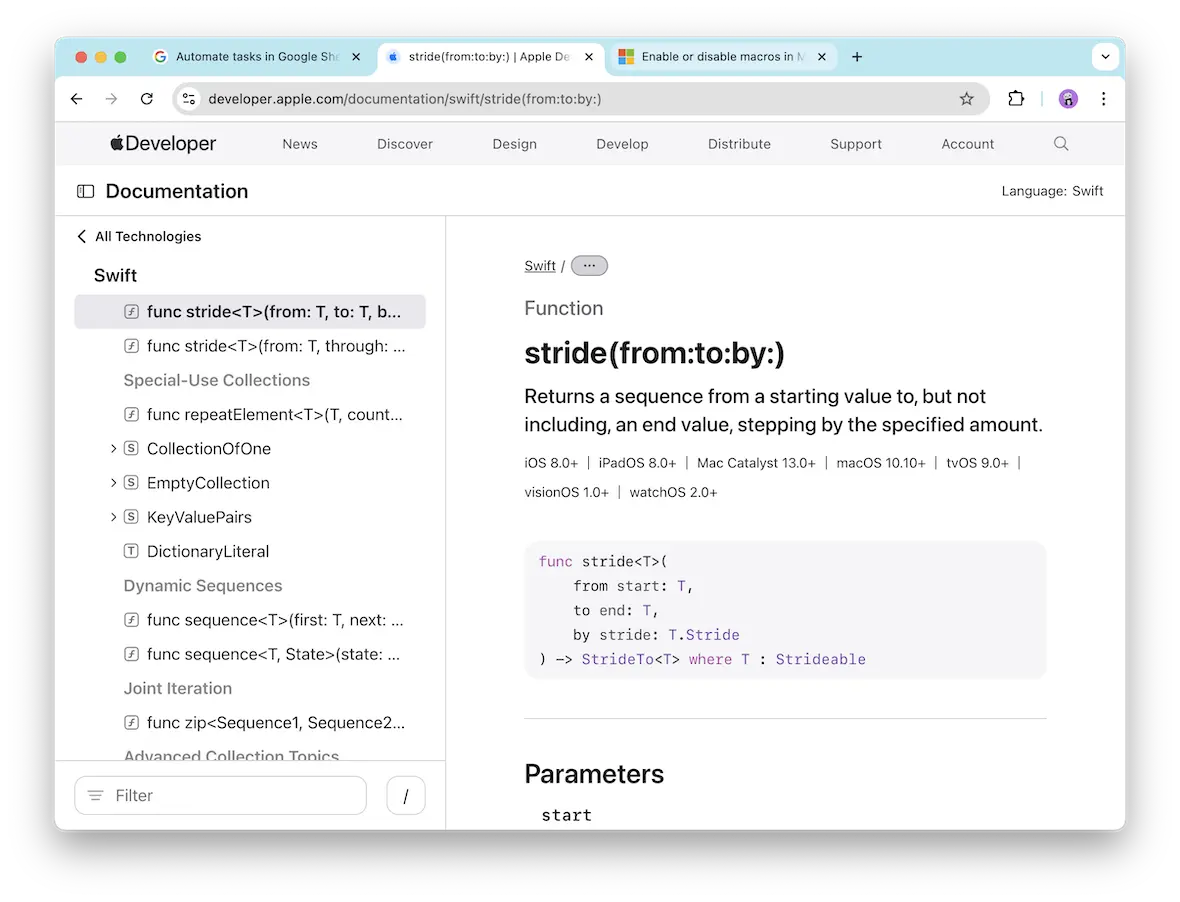
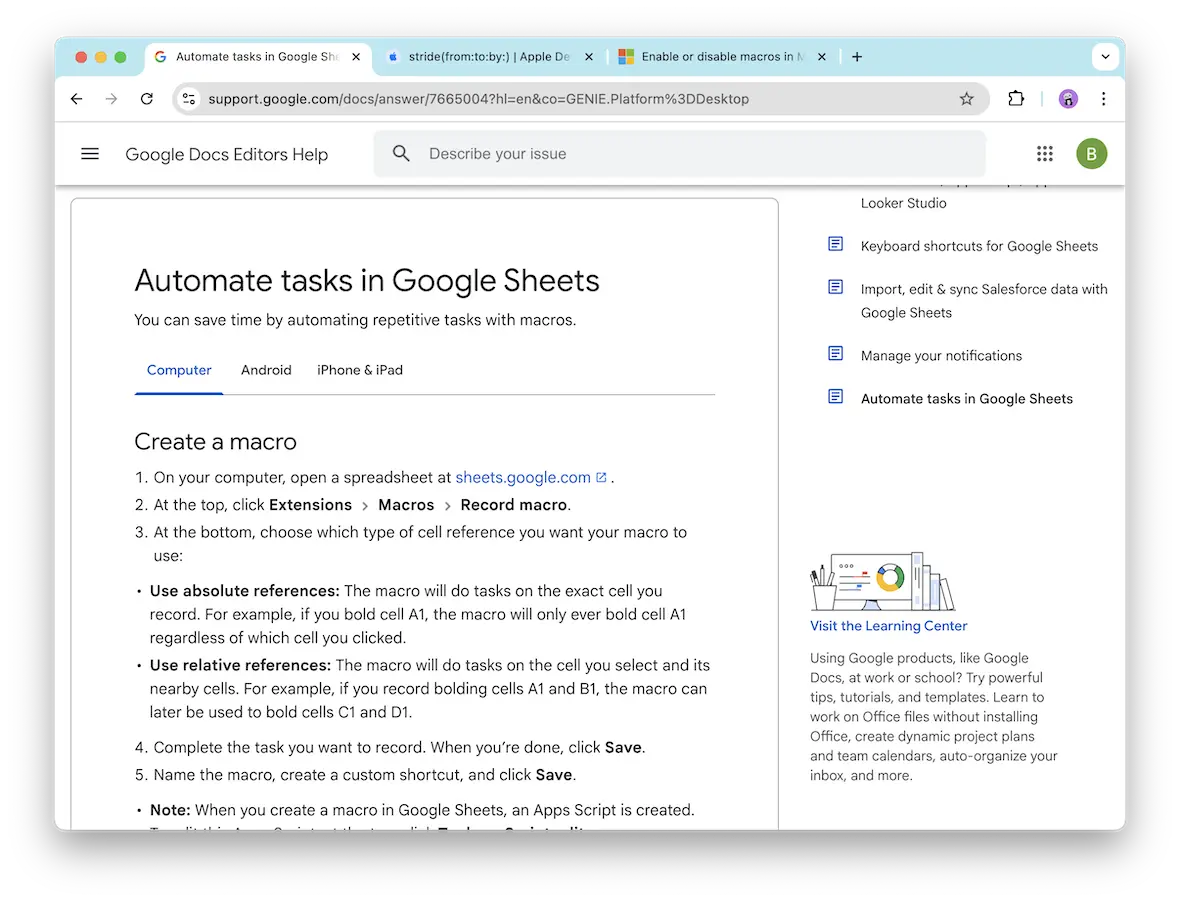
Technically, the definition of a macro virus is that of malicious code written in a programming language known as a macro. Popular software like Google Docs and Google Sheets, parts of Google Workspace, allow users to create and run macro programming languages. Microsoft Office, Excel, and PowerPoint do the same. This is why this type of malware is sometimes called an “Excel virus” or a “Word virus.”
A user may create a macro, for example, to automate repetitive tasks, such as extracting emails from inboxes on Google Workspace or Microsoft apps. Basically, a macro virus leverages this legitimate feature to create malicious scripts that abuse the platform for nefarious purposes.
In a way, a macro virus can also be considered a trojan. You can learn more about trojans in our trojan horse malware guide.
What macro viruses do and why they’re dangerous
The problem with malicious macro scripts is that because the scripts are allowed by the software, cybercriminals and bad actors can deploy them without raising much of an alarm. And contrary to popular belief, Macs can get macro viruses, just like Windows computers.
Macro malware can also come embedded into a .doc file, a .docx file, or an .xls file. Macro malware is not to be confused with malicious JavaScript malware, despite both being capable of integration with Google Workspace and Microsoft Office software.
Let’s look at some other risks of macro malware and their details:
- Ease of deployment: Macro malware leverages built-in software features to run without triggering immediate suspicion.
- Widespread distribution: A macro virus spreads rapidly through common sharing methods, making infected files appear trustworthy and abusing popular and trusted software.
- Data exfiltration: Malicious macros can steal sensitive information like credentials or financial data. Companies like Google and Microsoft have security guardrails in place, such as time restrictions or volume extraction restrictions, to prevent abuse of macros.
- Persistence and evasion: Macro viruses hide within legitimate files and use obfuscation to avoid detection by antivirus software.
- Automatic execution: Macros may run with minimal user interaction, triggering malicious actions as soon as a file is opened.
- Exploitation of trusted applications: These attacks take advantage of users’ trust in popular software, making it more difficult for the user to detect harmful intent.
- Complex attack scenarios: Cybercriminals combine macros with other types of malware to create multi-stage attacks with severe repercussions.
How do malicious macros spread across devices and networks?
Malicious macros can spread rapidly through different devices and laterally through networks with ease. Let’s look at how cybercriminals do this:
- Email spam with malicious attachments: Cybercriminals send mass emails with infected Google or Office documents attached, hoping users will open them so the macro will run.
- Online sites with malicious downloads: Attackers host compromised files on fake or hacked websites to lure in and infect unsuspecting visitors. When the download is opened, the macro runs.
- Automated embedded malicious macro: Malicious code is pre-embedded in files to automatically execute distribution actions, such as extracting your contacts and sending a fake email with a malicious attachment.
- Fake notifications: Users are tricked into enabling macros via deceptive messages or prompts within a document, which activates the malicious code.
- Compromised collaboration tools: Shared documents in platforms like Google Workspace or Microsoft Office 365 can contain embedded macros that spread malware laterally, infecting multiple devices and network endpoints.
How to recognize macro malware before it spreads
Macros are sneaky and hide in the back end of known, trusted, and popular software. However, there are several macro signs that will help you spot the malicious ones. Let’s look at 3 clear macro symptoms.
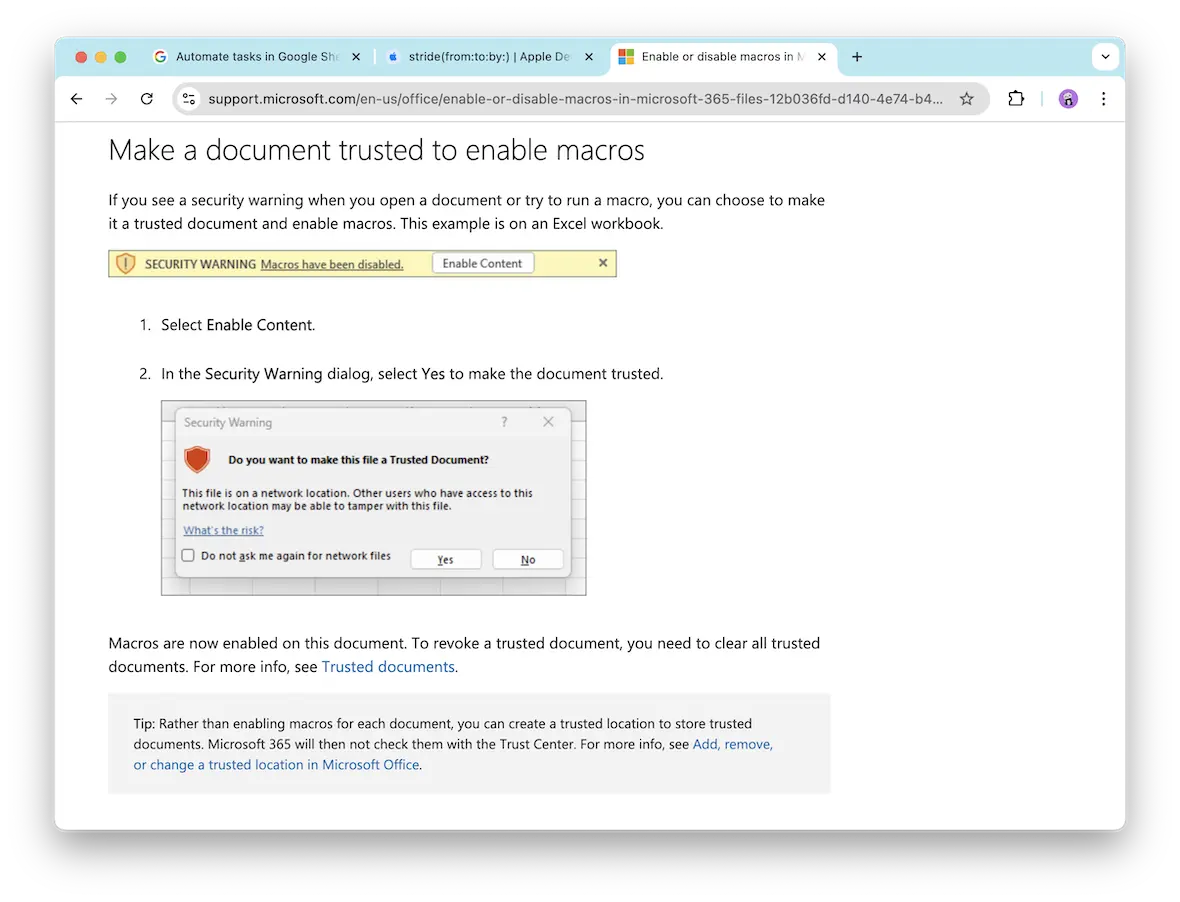
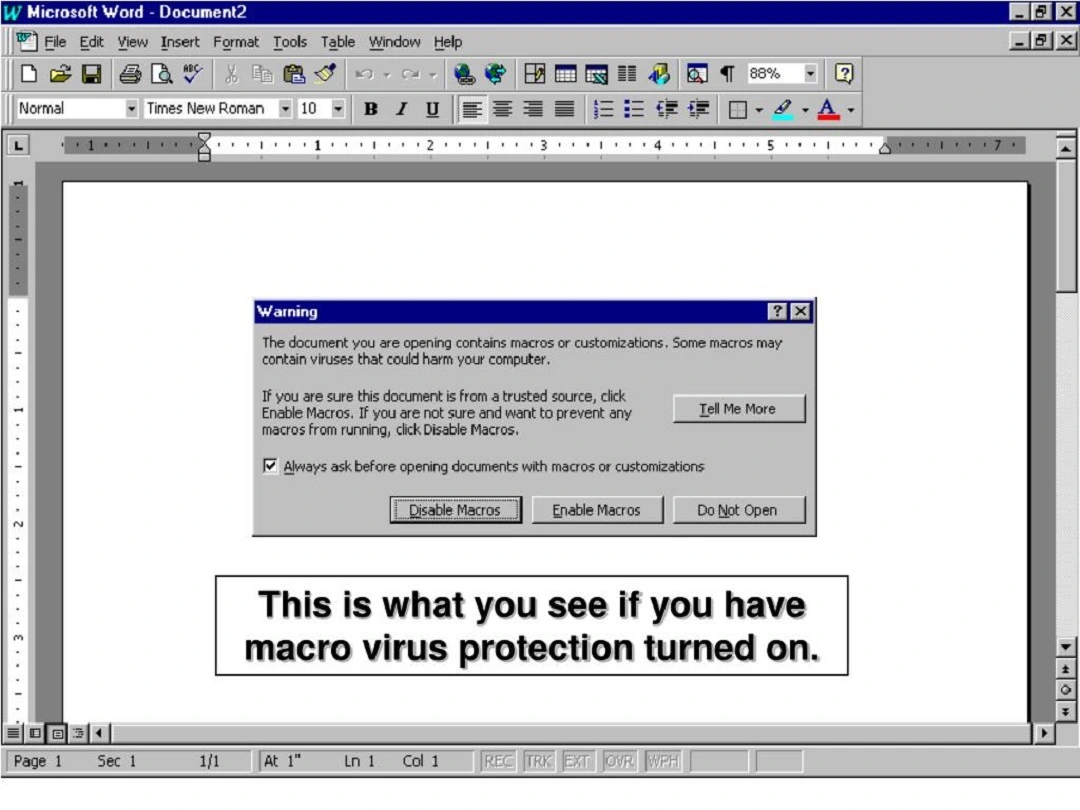
Sign 1: Warning notifications
Companies are getting better at making sure that cybercriminals do not abuse legitimate tools. Therefore, there is a high chance that an attachment that contains a malicious macro will be flagged by the software provider.
If you get a warning message or a strange notification when opening a type of file that you usually have no problem with, take the warning seriously.
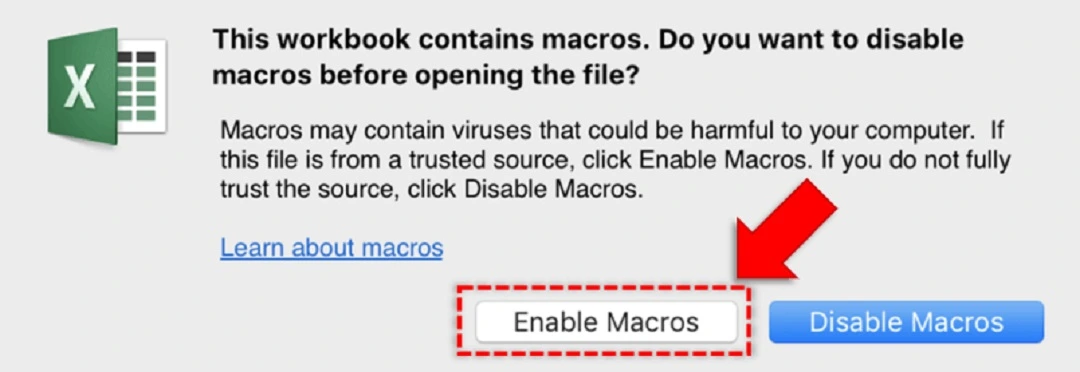
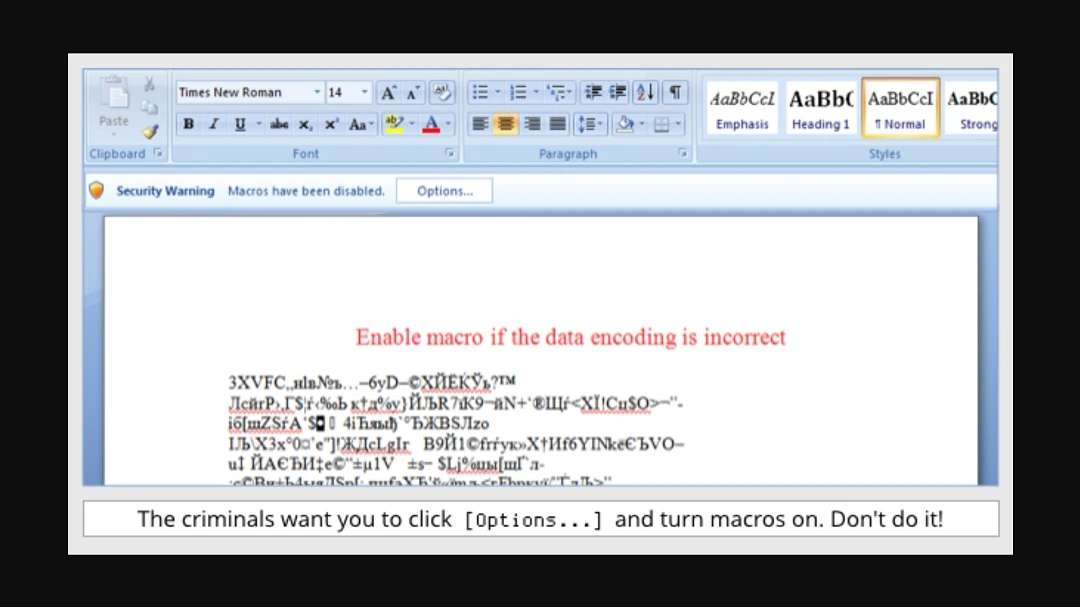
Sign 2: Unexpected macro prompts
This one is easy. If a piece of software is asking you over and over again to enable macros, you are probably looking at a macro virus in action.
Sign 3: Irregular file behavior
Be alert for changes in file behavior, such as unexpected edits or system slowdowns when interacting with what appears to be a normal document, as these can be signs of malicious macros at work.
Why are macro viruses hard to detect?
As mentioned above, macros are hard to detect because they are not alien to the software in which they run. Abusing legitimate features of known software makes it very challenging for security tools to detect this type of cyberattack.
Additionally, a macro virus, once deployed, can make changes in your configuration, evade scans, and hide deep within your system. Even if you remove the malware that the macro downloads, bits and pieces of code and files might remain on your computer.
How to remove a macro virus from your device
In order to get rid of a macro virus, you need to delete all the infected files — starting with the original infected files and any replicas the virus might’ve made of itself. However, spotting the files isn’t always easy, especially if you’re in the habit of saving Excel and Word files under random names and saving them all over your device.
Manually removing any type of malware is a difficult process, but here’s what you can do.
Start up your Mac in Safe Mode
When you reboot your Mac in Safe Mode, only the essential system files and drivers are allowed to run. That way, if your Mac has been infected with a macro virus or any other malware, it won’t run. This will give you the best chance at finding and getting rid of any stray macro virus files.
To go into Safe Mode, start by completely shutting down your device. Press and hold the power button for a few seconds. This will turn your Mac back on and display “Loading startup options” on the screen. Choose a boot volume, then press and hold the “Shift” key. Finally, select “Continue in safe mode.”
Your Mac will then automatically start in Safe Mode. You’ll still need to input your password to log in, but you’ll notice “Safe Boot” in the menu bar.
Delete all temporary files and cache
While temporary files are generally harmless, macro viruses can sometimes be hidden in this category of files in order to evade detection. You won’t lose any of your personal files when deleting temporary files and cache files, so don’t hold back from selecting and deleting everything.
It’s recommended that you regularly clear out both temporary and cache files, as they can pile up and clog your system. You can either do it manually by following the path ~/Library/Caches and deleting everything there.
Delete suspicious files
Macro-enabled files often have file formats like .docm, .xlsm, and .pptm. Go through your files, and if you find any that you didn’t create yourself or did not intentionally download, they’re likely the host of the macro virus. To prevent the viruses from running, don’t open the files. Immediately delete potential macro malware from your Mac.
While simple in theory, this process can take a lot of time and require you to be comfortable using the Terminal of Finder to locate different file formats. Even then, it’s not guaranteed that you can find and delete all traces of the macro virus.
Real-world macro virus examples
Let’s briefly dive into some real-world cyberattacks that used macros and take a look at their consequences to understand what’s at stake.
Concept Virus (1995): One of the earliest macro viruses, it quickly spread through Microsoft Word documents, infecting thousands of computers and forcing companies to re-evaluate security practices for document-based macros.
Melissa Virus (1999): One of the first widespread macro viruses that infected Microsoft Word documents and spread via mass email, causing network congestion and significant business disruption. This macro virus is estimated to have infected around 100,000 computers worldwide and caused tens of millions of dollars’ worth of damage in lost productivity and remediation efforts.
Locky Ransomware (2016): This ransomware was delivered by email with an attached Microsoft Word document that contains malicious macros. This attack used malicious macros to execute payloads that encrypted user files, forcing victims to pay ransom for data recovery. Locky is estimated to have affected hundreds of thousands of users globally, with victims facing encrypted files and significant ransom demands, resulting in substantial financial and operational consequences.
Ways to keep your system safe from viruses and other malware
Here are a few things you can do to limit the risk of various malware types:
- Make sure your OS and apps are updated: A lot of users postpone updates to avoid downtime. However, updates to your OS, apps, or software include the latest security patches and should not be ignored. Keep your environment up to date to make sure you have the latest protections.
- Set up antivirus protection: You can rely on Moonlock to run regular scans of your Mac and enable real-time monitoring to catch threats and malware as quickly as possible. Moonlock has a free 7-day trial, allowing you to try it out before purchasing.
- Avoid cracked software: Software can be expensive, and for some, it may be tempting to use cracked software. However, if you are not running a legitimate version of the software, it will not be updated, nor will it receive support. Macro attacks in these types of environments can bypass your system fast.
- Don’t click on random links: Malicious links can reroute you toward malicious websites where you risk your personal information getting stolen and your Mac being infected with all sorts of malware.
- Configure your Mac’s built-in security features: Follow Moonlock’s Security Advisor and System Protection recommendations on the best ways to configure your Apple security settings to optimize for security and privacy.
- Email attachments: Always verify the source of email attachments and downloads, and avoid opening files from unknown or untrusted senders. When in doubt, reach out to the sender to confirm the file’s legitimacy before enabling macros.
- For tech-savvy users: Configure your applications to disable macros by default or only allow macros from trusted sources. This can significantly reduce the risk of inadvertently executing harmful code.
Macro malware may not be as prevalent as it once was, but it remains a serious threat. There are still many cybercriminals who use macros as an entry gate and a loader to take over your computer, steal your contacts and network info, and spread.
By keeping your software up to date and watching out for malicious attachments and suspicious behavior, you can shut down a macro attack before it is too late. A trusted antivirus also adds an important layer of defense to your digital environment. Follow the advice in this guide, and you can live free of macro-attack concerns.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac is a trademark of Apple Inc. Microsoft Word and Microsoft Office are trademarks of Microsoft Corporation. Google Sheets, Google Docs, and Google Workplace are trademarks of Google LLC.