Malware is the buzzword of the day. We hear it in reference to many different types of online attacks, and almost everyone has at least some idea of what it is — and has possibly seen it in action. One of the cleverest types of malware is the trojan horse.
Keep reading this guide to learn all about the history and evolution of trojan horse malware, including examples, types of trojans, and how to detect and remove them.
What is trojan horse malware?
“Trojan horse malware” is a blanket term for many different types of malicious software. A piece of malware qualifies as a trojan horse when the program pretends to be something it isn’t. In reality, the software is an attack in disguise.
Historical context and the evolution of trojan malware
The term “Trojan horse” stems from Ancient Greek history. According to legend, during the Trojan War, the Greek strategist Odysseus devised a plan to get his people into the city of Troy undetected. The Greeks wheeled a giant horse to the city’s gates and left. Trojan soldiers, believing it was a sign of defeat and surrender, brought the horse into the city. In reality, Odysseus and his men were hiding inside. This clever tactic allowed the Greeks to launch a sneak attack by night, seize control of the city, and win the war.
The term “trojan horse” has since been adopted in the cybersecurity community to describe any program that uses deceit or social engineering to trick the user into installing it onto their device, essentially letting it in the door.
Is a trojan a virus?
No. Trojans are not viruses, nor are they worms. Rather, the term refers to a category of attacks that can do many different things. In short, a piece of malware is classified as a trojan due to how it functions.

Examples of trojan attacks
For as long as computers have existed, hackers have been devising ways to attack networks and devices. The idea is not novel, but the execution and style can be. Some examples of trojan attacks include the following.
ANIMAL
In 1975, cybercriminals launched one of the first trojan attacks using a simple game called ANIMAL. As the user played, the program quietly copied itself to other parts of the network. This early version didn’t do much damage; it was more of a prank than anything else.
AIDS trojan
In 1989, subscribers to PC Business World magazine and a World Health Organization AIDS list received floppy disks containing the AIDS trojan, the first recorded ransomware. It locked the user’s files after 90 days and demanded $189 for the key.
Whack-a-Mole
By 1990, hackers had grown bold and used another simple game, Whack-a-Mole, to entice users to download what was really a copy of NetBus, a remote controller for Windows. It provided remote access, meaning the criminal could do just about anything to the user’s computer.
What do trojans actually do once inside your system?
A trojan horse in computers is the beginning of a real problem. Trojan malware deceives users by impersonating legitimate software, popular apps, and even macOS and Apple security notifications. For example, due to the popularity of AI, threat actors are impersonating public AI platforms to trick victims into downloading trojans.
Trojans are sneaky, too. They can hide deep in your system and even survive data wipes. They are coded to do one thing: trick users into running them so they can modify system settings and establish a connection to load the second-stage attack malware.
Technically, depending on how a trojan is coded, it can remain dormant for years before it is activated remotely or through a set timer. In the wild, however, when a trojan gets inside a victim’s digital environment, it usually gets to work right away. How long a trojan cyberattack takes depends on the level of sophistication of the hackers who coded the malware and the actions that the trojan is designed to take. For example, a spyware trojan could be in a system for months before the attacker commands it to execute.
Threat actors who deploy trojans will use them as a doorway into systems. Through this backdoor entrance, they can take full control of any device and load all kinds of malware, leading to significant damage.
Common delivery methods of trojan malware
Trojan malware may be delivered through various methods. Some examples are:
- Phishing emails
- SMS text messages with links
- Games laced with malware
- Social media posts
- Fake ads
- Malicious websites
- Free files/downloads
- Apps
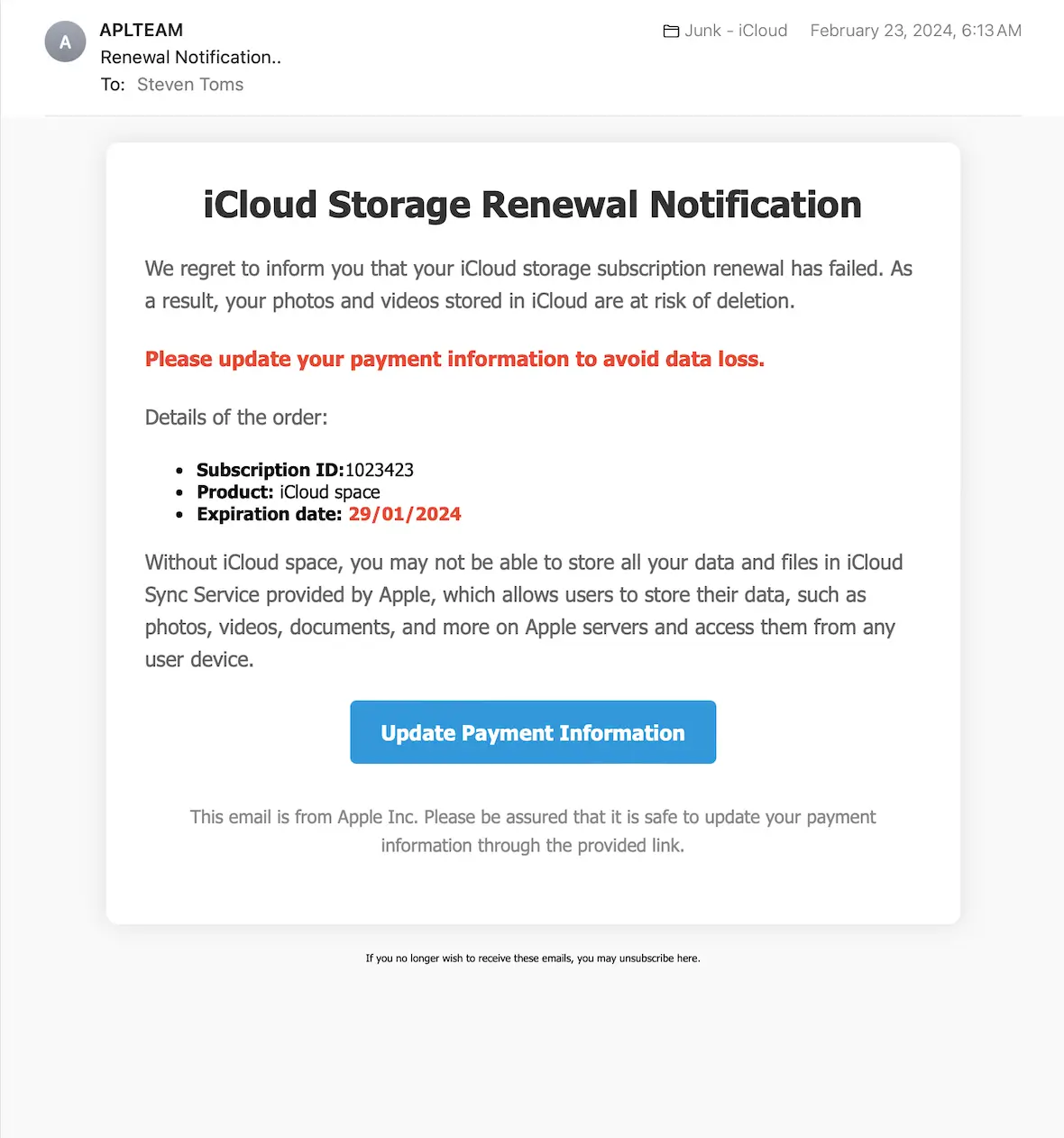
What kind of damage can trojan malware cause?
As mentioned, trojan malware is often used as a first-stage attack resource. It breaches a computer and establishes communication with the attackers’ infrastructure. Once a trojan is in, it might automatically download malware from the web or connect to a C2 server run by cybercriminals. Using this line of communication, bad actors can send commands to the trojan and get information back.
Trojans can load or be coded to act as all types of malware, including spyware, infostealers, ransomware, keyloggers, cryptojackers, and others. This is why cybersecurity professionals often refer to trojans as the most dangerous malware in the wild.
When referring to the damage trojans can cause, we can recall the original Trojan horse used in the Trojan war. The wooden horse itself represented no real danger. It’s what was inside the horse that caused devastating damage.
Let’s look a little closer at some types of trojans and the potential damages for each:
- Spyware trojan: Surreptitiously monitors user activities and captures sensitive information, compromising privacy and security
- Ransomware trojan: Encrypts or locks critical files and data, holding them hostage until a ransom is paid, which can cripple operations
- Wiper trojan: Irreversibly deletes or corrupts important data, causing permanent loss and disruption of services
- Crypto-mining trojan: Exploits system resources to mine cryptocurrency without permission, leading to degraded performance and increased energy costs
- Botnet trojan: Covertly recruits infected systems into a network of controlled devices, which can be used for coordinated attacks or the spread of further malware
- Spammer trojan: Floods systems with unsolicited, often malicious communications, overwhelming networks, and potentially spreading additional threats
- Stealer trojan: Infiltrates and extracts confidential credentials and sensitive data, opening the door to identity theft and unauthorized access
- Financial trojan: Manipulates or intercepts financial transactions and details, resulting in direct monetary losses and financial instability
- RAT trojans: Gains unauthorized remote control over an infected device and uses it for a wide range of criminal activities, from spamming to DDoS attacks and more (learn how to spot and remove remote access trojans to better understand and manage this threat)
Trojans generally rely on hiding in places they won’t be seen or disguising themselves as something else. That is why you need a tool that will uncover what’s hiding beneath the surface. Moonlock was built specifically for Mac and is equipped to detect, quarantine, and remove trojans before they can cause any harm.
Moonlock utilizes real-time protection to make sure that malicious files don’t have a chance to cause any damage and runs deep scans to make sure all of the unwanted files are identified and removed, even if they are dormant. Moonlock also has a free trial, so you can see it in action without paying a dime.
Who do trojan attacks usually target, and why?
Unlike other malware, trojans do not discriminate. They target all types of individuals, organizations, and governments. Because trojans are an effective point of entry (vector of attack), they are leveraged as an essential hacker tool by all types of cybercriminal gangs.
There are also Mac trojans, Windows trojans, and trojans used to breach other operating systems, including mobile. We will discuss how you can detect a trojan in the following sections.
What follows is a comprehensive list of population groups, individuals, and organizations that are frequently targeted with trojan malware:
- Average tech users and high-value targets alike: Trojans cast a wide net and attract as many victims as possible, often impersonating popular software downloads online to target average tech users. However, this malware is also used to target executives, software engineers, and even military and intelligence agencies.
- Nonprofits, human rights workers, and journalists: Several well-known scandals started out with trojan malware, including the Pegasus spyware campaign that involved spyware installed on the devices of nonprofit workers, human rights activists, and journalists.
- Government and defense individuals and organizations: Breaching government and defense systems requires more hacking skills than breaching normal systems. To get the job done, cybercriminals may send a trojan to do the work. These trojans are more sophisticated than others, but in essence, they work in the same way.
- Small- and medium-sized companies: Trojans are used against small and medium companies for several reasons, including a lack of security tools, gaps in cybersecurity awareness, data or financial theft, ransomware installation, and supply chain manipulation.
- Large companies and international corporations: Cybercriminals deploy trojans against these giants because their complex IT infrastructures often harbor hidden vulnerabilities that can be stealthily exploited.
- Financial sector: Attackers use trojans in this arena to covertly access sensitive systems and bypass layered defenses, setting the stage for unauthorized transactions and data exfiltration.
- Technology sector and IT: Cybercriminals favor trojans when going after big tech because they can infiltrate trusted IT environments and establish persistent backdoors, enabling ongoing espionage or broader cyber disruption efforts.
Types of trojan horse malware
Below are some of the different kinds of trojan horse malware.
Downloader trojan
This type of trojan, once installed, downloads additional types of malware to the infected device to do even more damage.
Backdoor trojans
A backdoor trojan provides an unlocked door in the system so a hacker can gain remote access anytime. A backdoor is very dangerous, allowing the attacker to do anything they want to your computer.
Spyware
Spyware is another damaging type of trojan attack that spies on your activities. It can collect keystrokes, passwords, and login credentials, which are then used to steal your identity or money.
DDoS Attack
A distributed denial-of-service (DDoS) attack is designed to overwhelm the device or network with an overload of activity. Once disabled, the network or device becomes more vulnerable and easier to take over.
Rootkit
A rootkit trojan is a master of disguise. A rootkit’s primary function is to provide access to normally off-limits areas of software, and hiding a rootkit in a trojan helps ensure that no one discovers the malware on the machine.
Banking trojans
Banking trojans target users’ bank credentials and logins. The attackers aim to use your collected information to gain access to your financial accounts and drain them.
RATs
Like backdoor trojans, remote access trojans (RATs) provide remote access to a machine or network.
Infostealers
As the name suggests, this type of malware steals information and files, usually for financial gain or fraud.
Other common trojan variants
Along with the malware listed above, you may come across other variants of trojans such as spy trojans, SMS trojans, ransom trojans, IM trojans, exploit trojans, mailfinder trojans, and SUNBURST trojans that do many nefarious things.
How to spot trojan infections and remove them
There are several clear telltale signs that your Mac has been breached by a trojan. For example, if you notice changes in your configurations, files, folders, startup process, or settings, these might be symptoms of a trojan taking over your device.
Other signs are more serious and could include failure to access your data or accounts, changes in passwords, unexpected system errors and constant pop-ups, or a disabled firewall. If you see any of these, take immediate action. These symptoms only emerge during the final stages of a cyberattack, right before the real damage begins. Read more on how to detect malware on your Mac.
Removing a trojan is a bit tricky. However, you can mitigate the damage by cutting off the Wi-Fi or your internet connection. Trojans set up communication channels with the attackers who will command cyberattacks, so shutting down your connection leaves the attackers offline.
Next, make sure no automated process is left running on your computer. To do this, open the Activity Monitor. Is there anything running that you do not recognize, and is it using a significant percentage of your CPU and memory? If so, force it to stop. Then, remove the app by navigating to the Applications folder. You should also scan all installed applications and delete those that should not be there.

To completely remove malware from your Mac, you need to use a trusted anti-malware tool like Moonlock. Moonlock was designed to detect and neutralize threats like trojans or viruses, even if it has infiltrated deeply into your files or emails.
To remove a trojan and other malware using Moonlock:
- Open Moonlock and select the Malware Scanner.
- Choose Deep Scan, which will scan your entire device and system, including common hiding locations.
- Hit Scan. Moonlock will then begin to scan for all types of malicious files.
- If a threat is found, Moonlock will instantly move it to Quarantine, keeping it from spying, stealing, or spreading.
- Review the results of the scan, and remove everything that it found by clicking Remove.
You can try Moonlock for free for a week and see how it actually works on your own Mac.

Removing a trojan on iPhone
If you believe you have a trojan on your iPhone, follow the steps below to remove it.
- Restart your iPhone.
- Update your iOS if not updated already.
- Clear Safari’s browsing history and browsing data.
- Look for any suspicious apps that you did not install and remove them.
- Perform a factory reset on your iPhone and restore it from a safe backup.
Best practices for avoiding trojan horse infections
It’s said that an ounce of prevention is worth a pound of cure, and cybersecurity is no exception. Some best practices for preventing trojan infections include the following.
Get a trusted and professional anti-malware tool
Due to the complexity of the threat landscape, the wide-ranging variants of trojan malware, and the broad spectrum of victims they target, the best defense against trojans is a trusted and professional anti-malware solution.
Moonlock combines real-time protection, on-demand scans, and quarantining into the same easy-to-use platform. It blocks malware before it has the chance to run, isolates suspicious files like viruses, cryptocurrency miners, keyloggers, worms, and trojans automatically, and gives you clear, supportive guidance on what to do next. Instead of worrying about what infections could have gotten past your security system, feel safe with Moonlock and its more than 17 years of Mac security expertise.
Never click links in texts or emails
Phishing and smishing are some of the ways hackers get you to download unsafe software. Never click links in emails or SMS messages sent from someone you don’t know.
Keep systems updated
Always update your hardware and software with the latest security patches.
Turn off macros
Turn off macros in Excel and Word. This may not seem like an obvious tip, but criminals can use macros to download malicious software to your machine.
Avoid downloading anything from unsafe sources
Never download email attachments from unknown senders, and never download free software from unsafe sources. If you find something online that seems too good to be true, it’s probably laced with malware.
Turn on 2FA or MFA
Turn on 2-factor authentication or multi-factor authentication on all your accounts for an added layer of security.
Keep good backups
Always back up your data so you have a safe copy to restore your device if you get infected.
Trojan horses continue to be an effective tool used by cybercriminals. Thankfully, Moonlock keeps a close eye on emerging threats to inform and warn consumers so they can protect themselves.
Trojan horse attacks are clever and difficult to detect. The best way to stay safe from these particular threats is to follow the cybersecurity best practices listed in this article and always err on the side of safety.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and iPhone are trademarks of Apple Inc.






