With an increasing number of bad actors seeking to infect personal computers with malware, just going online can seem like a rather risky proposition these days. Malware is an ever-present threat, and one particularly nefarious type of malware is the remote access trojan (RAT).
As the name implies, a remote access trojan is a type of malware that gives the hacker remote access to your computer. In this guide, we’ll delve deeper into what a remote access trojan is, how it works, and how to remove one from your Mac or MacBook.
What is a remote access trojan, and how does it work?
Once embedded on your MacBook, a remote access trojan (also known as a RAT) will set up a secret backdoor, which a hacker can use to send commands to your device and receive data back.
The commands used by a RAT could include logging your keystrokes, transferring your files, or activating your webcam, among many others.
Why do hackers use RATs?
RATs are very popular among hackers due to their versatility and ability to give a cyberattacker complete control over your MacBook. Some of the benefits for attackers include:
- RATs can be very difficult to locate. They prioritize hiding in the depths of your machine.
- A RAT can give a hacker remote access to your computer, potentially from the other side of the world.
- RATs aren’t nearly as common on macOS as data stealers or adware, and when they do appear, they usually come from more advanced threat actors, like DPRK-linked groups. They’re not simple to deploy, but if a hacker manages to get a RAT onto your device, it instantly makes their job much easier – giving them long-term access and plenty of room to move around inside your system.
- RATs can be used to set up botnets, which are large groups of compromised computers that can be used to launch distributed denial of service (DDoS) attacks against websites.
Some may think they are not interesting targets for RAT developers. That’s not always true, as some popular malware has been seen bundling RATs.
Mykhailo Pazyniuk, Malware Analyst at Moonlock
Why are remote access trojan attacks considered dangerous?
Remote access trojan attacks are especially dangerous for the following reasons:
- It is often difficult to detect a RAT by using antivirus software.
- Once inside the computer, a RAT will quickly alter the system settings and begin setting up more malware.
- If RAT malware gets inside a network, it may try to spread to other machines, depending on the attacker’s goals. When lateral movement is part of the plan, a RAT can be used to explore the network and access other connected devices.
- A RAT can manipulate elements of the computer, including the keyboard strokes and the webcam. This can lead to valuable and perhaps compromising data being stolen or the owner being forced to pay a ransom.
Сommon signs of a RAT trojan infection
The telltale signs of a RAT infection are no different than those associated with other forms of malware. Here are the RAT symptoms you need to look out for:
- Your system starts to slow down: Malware requires a lot of CPU power to operate in the background and is competing with your normally running apps. If your Mac or MacBook suddenly slows down, check the Activity Monitor to see which apps are hogging all the juice.
- You suddenly have unknown apps on your machine: Like any malware, a RAT needs to set up its own program to run malicious scripts, communicate with home base to receive commands, and transfer your data out. This means you’ll likely have unauthorized apps appearing on your Mac.
- Your internet usage increases: This doesn’t happen in every case, but it can if the RAT is actively sending data – for example, streaming video from your webcam or turning your device into part of a botnet. In those situations, you may see unusual spikes in network activity at odd hours.
- Pop-ups and redirects: As part of its data-gathering operation, a RAT may use adware to place pop-up windows on your screen and redirect you to malicious websites.
- Your webcam is activated: Some types of RATs are potentially capable of accessing a webcam if they gain the necessary permissions, but this is uncommon on macOS. Still, if you see the webcam blinking on and off, you have a problem.
- Your typing speed gets sluggish: When the RAT is logging your keystrokes, it can lead to your typing speed slowing down and your accuracy becoming rather dodgy.
How can you detect a remote access trojan?
If you’re experiencing the telltale signs outlined in the previous section, how can you detect the RAT and know for sure?
Check for suspicious processes with Activity Monitor
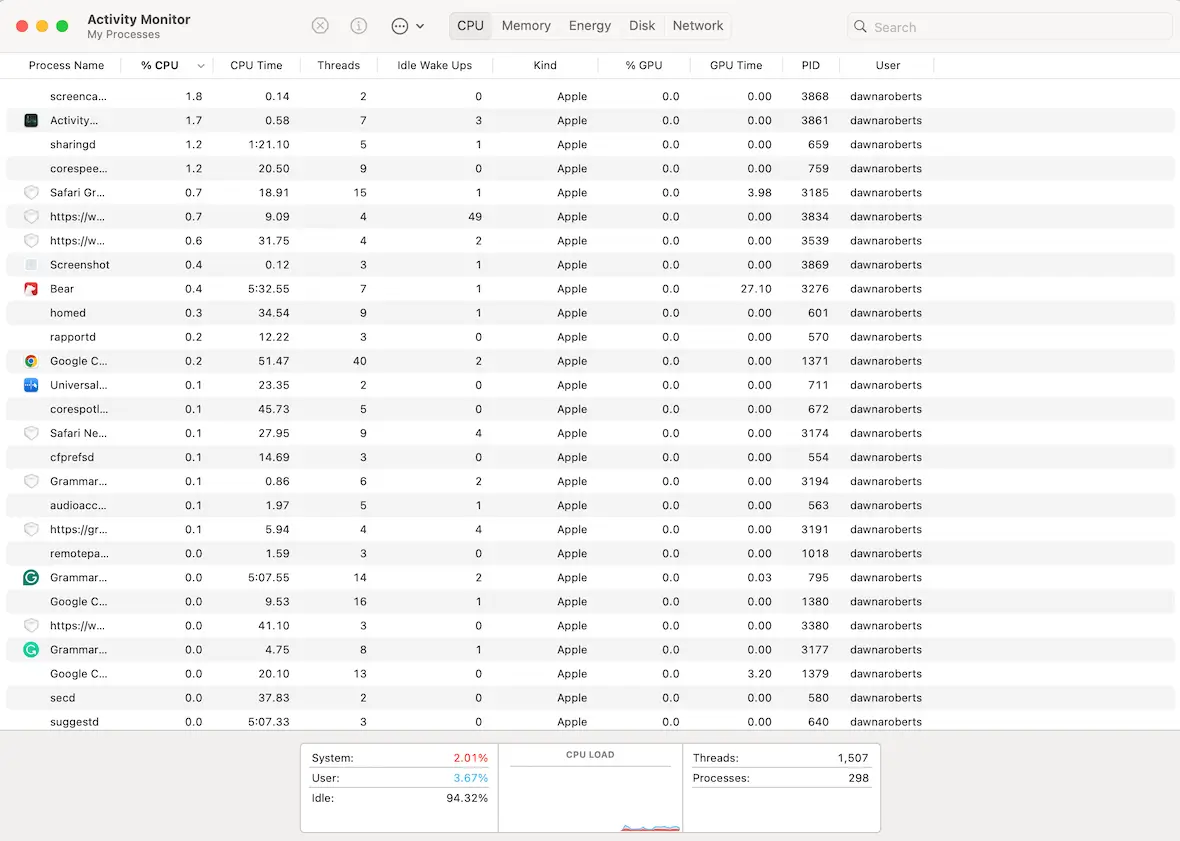
As mentioned earlier, a RAT will install its own program that runs in the background. To check for this, open Activity Monitor, select the CPU section, and order the running apps list by the most CPU usage.
Do you recognize the processes hogging the highest CPU percentage? If you don’t, Google their names. Then, force-quit them and see if they reappear. If they restart by themselves, you may have a problem.
Review installed applications in Finder
When a RAT installs its own program, there’s a good chance it will appear in the Applications folder in Finder. This is why it’s always good practice to check the Applications folder on a regular basis.
Go to Finder > Applications and see if there’s anything there that you don’t recognize. Run a web search for the name in case you did install it but forgot about it.
Run a scan with Moonlock
You can’t go around manually checking every file for malware like a remote access trojan. Instead, run a scan using the Moonlock anti-malware app. A system-wide scan will find all threats hidden on your Mac, whether they’re RATs, adware, or spyware, and fully remove them.
If you’re interested in trying it out, sign up for a free trial of Moonlock and run your first anti-malware scan to get rid of RATs.
The best strategy to prevent RAT infections is to carefully check all apps you install and avoid giving them excessive permissions.
Mykhailo Pazyniuk, Malware Analyst at Moonlock
How to effectively remove a remote access trojan
So you’ve established that you have a remote access trojan. Now it’s time to go on the offensive and remove it. So, what do you do?
Disconnect from the internet
The first step is to disconnect from the internet. An internet connection is what the RAT needs to be able to work properly. So, by disconnecting from Wi-Fi, you’re depriving it of the fuel it needs to run.
Do a deep scan with Moonlock
With everything ready, now’s the time to run a deep scan with Moonlock. Here’s how:

- Open Moonlock and click on the Malware Scanner on the left sidebar (it’s the cool sunglasses icon.)
- From the drop-down menu, select Deep for a more thorough scan of your device.
- Click Scan.

As soon as Moonlock finds the RAT (or any other malware), it’ll isolate it in Quarantine, stopping it from continuing to access your files. Once the scan is complete, you’ll get a comprehensive list of all the threats Moonlock found on your device. From there, you can then easily select everything for safe and complete removal.
This entire process takes only a few minutes and very little work on your end. Get the Moonlock app, and you are ready to conduct your first Deep Scan today and clean your device of all malware.
Consider wiping and resetting your MacBook
Moonlock is highly thorough and will likely remove every trace of remote access trojan malware. But for extra peace of mind, you may also want to consider wiping and resetting your MacBook.
This is obviously a lot of work, as you’ll need to set up your MacBook from scratch. But to be 100% sure that the RAT is gone, it may be a good idea.
Change your passwords and enable 2FA
Assume everything is compromised. That means you should change all your passwords and enable 2-factor authentication on all of your accounts.
Also check the files on your laptop. Pay close attention to anything that contains sensitive information.
How do hackers deliver remote access trojans?
The best way to avoid getting a RAT is to understand how a hacker can deliver one to your device in the first place.
Malware-infected links
The easiest low-effort method is to send out links far and wide and then wait for someone to click on them. These links will either take the user to an infected website domain or to software that will start installing on your device.
Bundled inside legitimate software
Another method of installing software is to bundle it with legitimate software. When you install the real software, the RAT will get installed in the background.
Sending you an infected file via email
Infected email attachments are another low-effort way to spread RAT infections. Most major email platforms are now very good at detecting infected files, but they’re not infallible. Some may still slip through.
Exploiting security vulnerabilities
Operating systems like macOS are excellent at staying on top of security vulnerabilities and pushing out patches. But what if the vulnerability isn’t known yet?
The period between the vulnerability first appearing and Apple discovering it and pushing out a patch could be a big enough window for a RAT to take advantage of it.
Scanning for network misconfigurations
Another method a RAT can gain access to your computer is through your Wi-Fi network. If your network has no password and is publicly accessible, it’s child’s play for a hacker to gain access and introduce a trojan virus.
Infected USB drives
Have you ever seen a USB drive lying around and been curious about what’s on it? Well, curb that curiosity because the drive could have been left there intentionally by a cybercriminal hoping you will plug it into your MacBook and release the RAT.
How to protect your Mac from remote access malware
MacBooks are no different than any other type of personal computer when it comes to RATs and other malware. So it’s necessary to be vigilant about protecting your Mac from a RAT threat.
Be wary of links and email attachments
Obviously, we can’t tell you to never click on a link or email attachment. That would be impractical. But if someone you don’t know sends you a link or an attachment, don’t click it or open it. Even if you know them, do you trust them?
Sometimes, it’s safer to be paranoid.
Set up and run Moonlock
The remote access trojan solution that will protect you the most is running a strong anti-malware tool. Install Moonlock on your Mac and schedule frequent Deep Scans using the built-in Scan Planner.
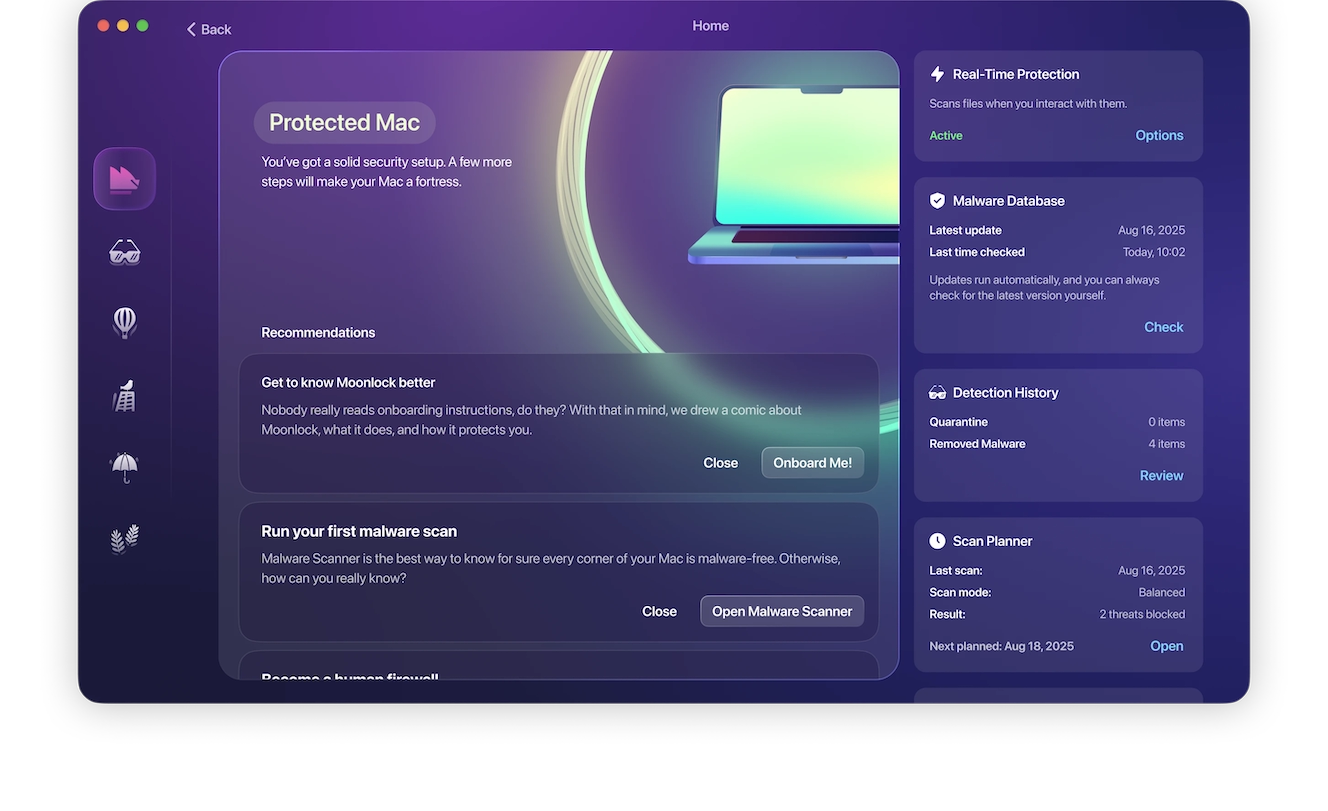
Moonlock will scan your files around the clock, immediately altering the moment it detects any new threats—including remote access trojans. This gives you the chance to react promptly, dealing with the threat before it gets the chance to take control over your device and data.
Avoid installing software outside of the App Store
Since RATs can be installed by being bundled software with other apps, it’s a good idea to mostly confine yourself to apps and software available inside the Apple Store.
Apple thoroughly scans and vets all apps in their store, so the chance of a RAT lurking there is slim to none. There may be times when you need to buy something from a developer outside of the App Store. Just be careful before buying and downloading. Stick to trusted names.
Install all system and app updates right away
If there is a known security vulnerability on your Mac, Apple will quickly push out a patch to fix the hole. So, when you see that there is an update waiting, you must install it as soon as possible.
It’s easy to ignore updates and say that you’ll get to them later. In the meantime, a RAT may gain access to your machine. So don’t do it later — do it now.
Make sure your network is configured correctly
To prevent a RAT from entering your network, ensure that the network is configured properly.
Since there are so many routers with different settings, it’s difficult to provide specific instructions in this regard. However, at the very least, ensure that you have encryption protocols enabled and have a very strong password set up to stop unauthorized intruders from coming in. This is also a good reason for you to avoid using public Wi-Fi.
A remote access trojan can cause a considerable amount of trouble, inconvenience, and chaos if it gets onto a targeted computer. But, as with all types of malware, the key is to educate yourself on its existence and then study the various ways to avoid it or defeat it.
Once you know what to avoid and what proactive steps to take to kill the RAT, you’ll be able to be on the offensive side and well on your way to protecting your valuable data.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and MacBook are trademarks of Apple Inc.