The classic definition of an email virus is a malicious email that includes code or a link designed to infect your device. It can then send copies of itself to everyone on your contact list. However, as threats evolve, their definitions tend to broaden.
Today, email malware is considered to be any email that is sent with a malicious purpose, whether it’s a phishing email or a virus email. This also includes any emails that contain malicious links, files (like malware PDFs), or hidden malware code.
What is an email virus? Types of email malware and examples
As mentioned, due to the many online threats that exist today, email malware comes in different shapes and forms. Let’s look at the most popular types of email malware.
Phishing
Emails designed to deceive users into revealing sensitive information, such as login credentials or financial data, are considered phishing emails.
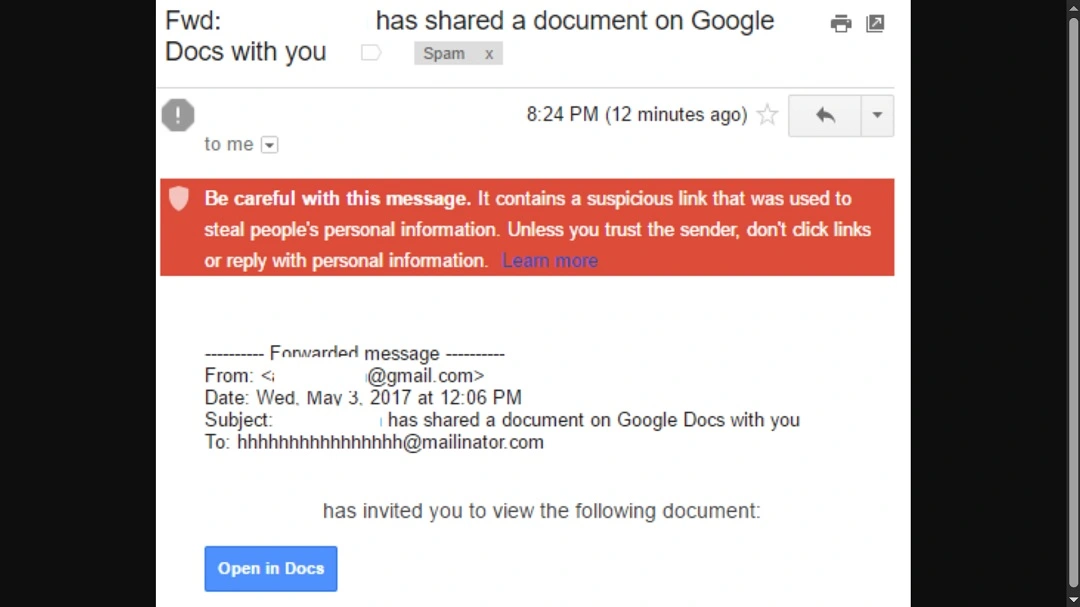
In the 2017 Google Docs phishing attack, cybercriminals sent emails that appeared to be invitations to a Google Docs document. Users who clicked the link were directed to a fake Google login page, where their credentials were stolen.
Ransomware
Emails containing attachments or links to malicious software that can encrypt files on a victim’s computer are known as ransomware. The attackers subsequently demand payment for the files’ release.
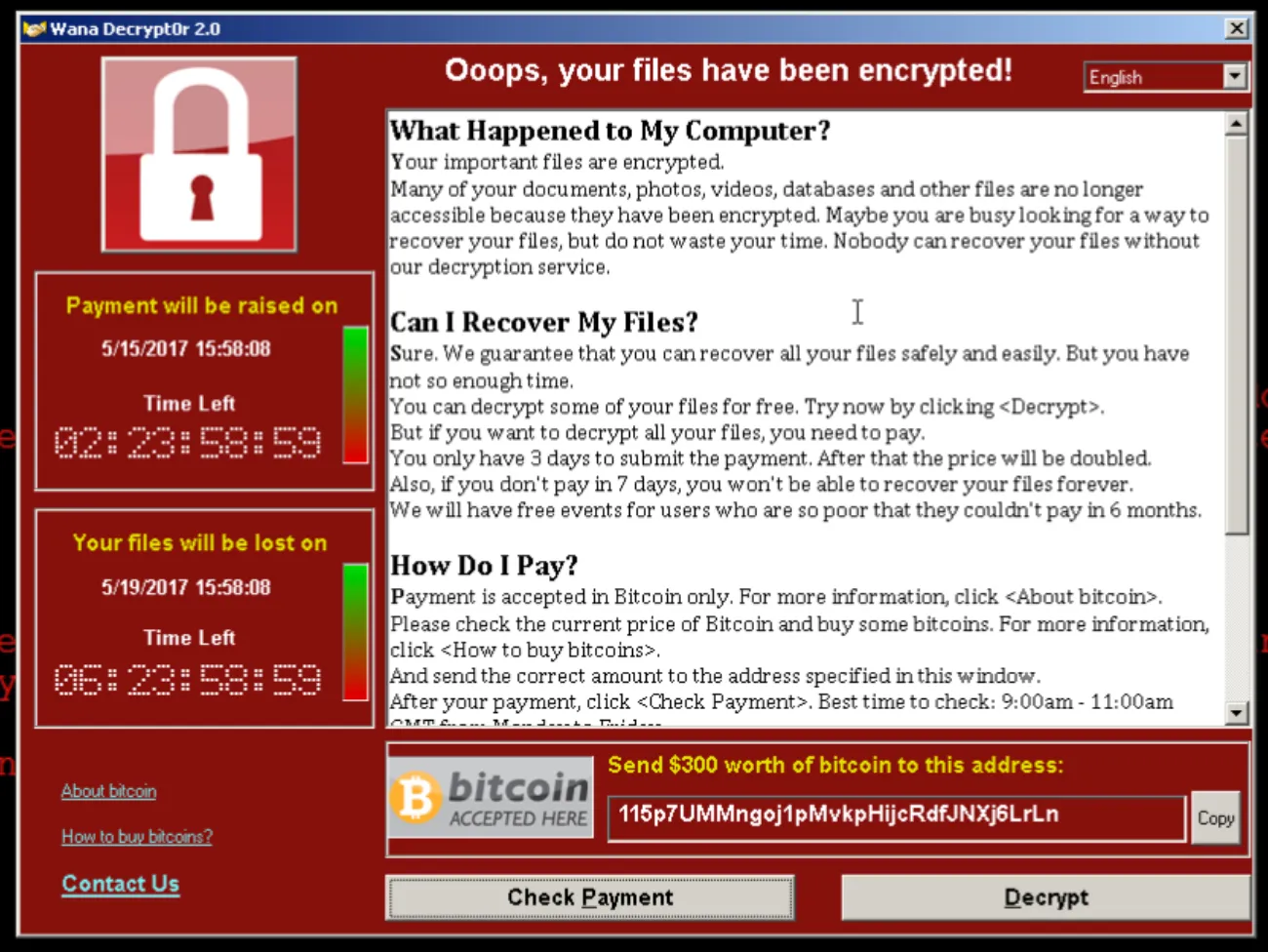
In the WannaCry Ransomware Attack (2017), emails containing infected attachments were used to spread WannaCry, which locked users’ files and demanded a ransom payment in Bitcoin for decryption.
Trojans
Emails offering fake legitimate software or apps, often impersonating well-known brands, may trick users into downloading trojan malware. These can steal information, install ransomware, or spread other malicious software.
The 2018 Emotet Trojan Campaign was spread through phishing emails disguised as invoices or shipping notifications, tricking users into downloading malicious attachments that installed the trojan and other malware like ransomware.
Viruses
Emails containing malicious programs that spread through attachments or links, often infecting the system once opened, are considered viruses.
In the case of the ILOVEYOU virus in 2000, a malicious email attachment was disguised as a love letter. Once opened, it spread rapidly through email systems and infected millions of computers worldwide, causing widespread damage.
Email malware with hidden code (invisible text or JavaScript)
Malicious code hidden within the body of the email, such as invisible text or embedded JavaScript, can execute harmful actions when the email is viewed or clicked.
The 2020 zero font campaign used emails that contained hidden JavaScript in invisible text, which executed malicious code when the email was opened. The code was designed to steal personal information or deploy malware onto the victim’s system.
Spear phishing
As a more highly targeted form of phishing, spear phishing uses personalized information to deceive specific individuals or organizations.
The 2016 Democratic National Committee (DNC) spear phishing attack saw hackers send emails to DNC staff members impersonating Google, warning of a security breach and asking them to change their password. The link led to a fake Google login page, allowing attackers to steal sensitive information.
It is important to understand how phishing and email threats evolve. For example, a recent cybercriminal campaign managed to trick users into believing that their Mac was blocked. This type of phishing attack can happen while users are simply navigating the internet, so always stay updated on these sorts of things.
Can you get malware from opening an email?
Cybercriminals can hide malicious auto-executable code in images, pixels, and text. They can also conceal scripts that download malware in an email. So, technically, yes. You can get infected by a virus or malware simply by opening an email. Having said this, these types of zero-click attacks are extremely sophisticated, need to bypass email security protocols, and are very rare.
The majority of malware and viruses that spread through emails require the user to download a file and open it, click on a link, or follow specific instructions that the attacker gives.
The threat landscape is constantly changing. Be on the lookout for quishing, which involves malicious QRs that can be sent via email. When you scan them, they direct you to pages that steal your data or trigger the download of malware.
Could malware in an email be dangerous?
Yes. Malware in an email can be extremely dangerous and damaging.
The most common vectors of attack today are email and messaging. Emails can contain stealers, spyware, and other malware that can take over your computer.
The malware that is spread via email can steal your personal data, breach your browser, and steal your passwords and history. They also have the potential to encrypt your device, spy on you and your family, and do much more.
How to scan your email for a virus
There are automated ways to scan your inbox for malware or suspicious contacts. Most of these, however, are paid services built into anti-malware solutions.
A quick note: If you plan to use anti-malware software, make sure it is respected in the industry and has great reviews. Refrain from free online scanning or new and unverified companies offering these services.
There are also ways to manually check if there is malware on your email account, but these methods are very time-consuming. Nevertheless, several tips can help you build healthy habits that, with time and consistency, will secure your inbox.
Use anti-malware software
When it comes to malware disguised as email attachments, anti-malware software is your first and best line of defense. Moonlock can automatically scan Apple Mail attachments, ensuring that all files are free of malware threats.
Check links carefully
Before clicking on any link in an email, even if it looks legitimate, hover over it to see the actual URL. Many malicious emails use links that look similar to trusted websites, but they lead to phishing sites or malware download pages.
Enable email security features
Many email providers (such as Gmail, Outlook, and Yahoo) have built-in security features that can help detect phishing and malicious attachments. Make sure these features are enabled. Spam filters and email malware protection can help reduce phishing attempts.
Avoid opening unknown attachments
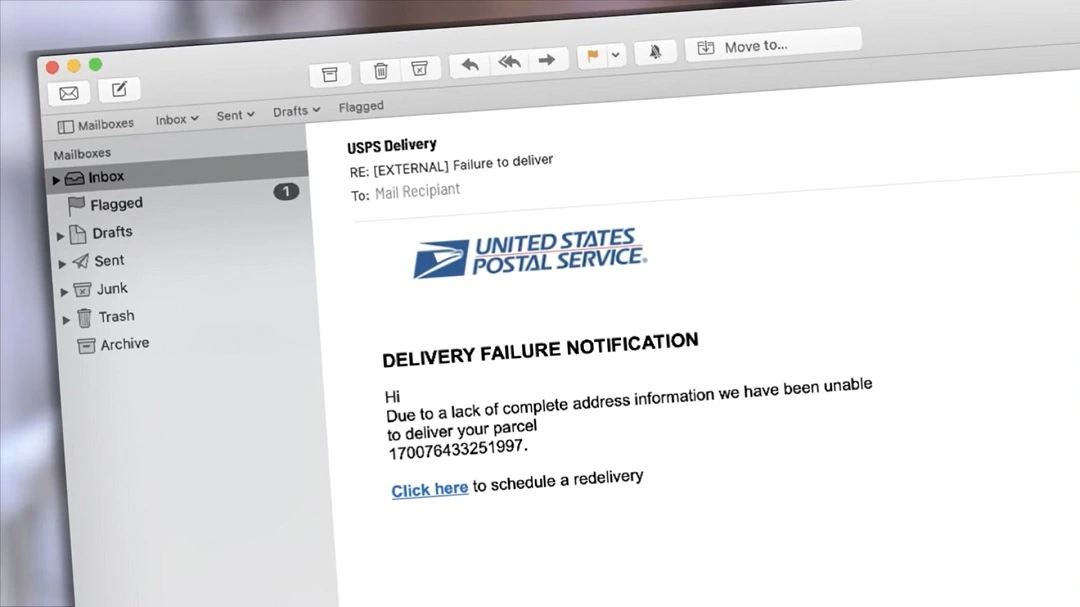
Never open attachments from unfamiliar senders or emails that look suspicious, even if they claim to come from a trusted source. Malicious attachments may be disguised as innocent-looking documents (PDFs, Word files, images, etc.) but could contain hidden malware or viruses.
Verify suspicious emails
If you receive an unexpected email asking for personal information, financial details, or login credentials, proceed with caution. Verify the sender before taking action. Contact the person or organization directly using their official contact information (not the one provided in the email).
What are some ways to recognize if an email has a virus?
In most cases, the trained eye can immediately sense if there’s something “off” about an email. And the truth is, the signs are not that difficult to notice.
Be on the lookout for anything that breaks the routine and does not behave like your inbox behaves on a daily.
Here are a few quick tips:
- Watch out for fake security alerts: If you see a pop-up or message claiming to be an Apple Security Alert, be cautious. Apple does not send security warnings through web pop-ups or random messages. These alerts are often scams.
- Double-check the sender’s email address: Is something wrong with the source of the email? Check the email address for any slight discrepancies or oddities.
- Think twice about attachments: These days, a file attached to an email can carry major risks. Even if the person sending you the file is someone you know, they might have been hacked. Check all attachments for malware. (Yes, that means scan them.)
- Don’t click links without checking them: How do you know if a link will really lead you where it claims? Hover over links to see if the URL is that of a legitimate website. Avoid clicking on suspicious links.
- Beware of urgency: Is the sender contacting you regarding an “emergency”? Be wary of emails that pressure you to act quickly or threaten negative consequences. These techniques are designed to trick users into taking rash action.
- Pay attention to normal inbox routines: If something in your inbox feels off and breaks the “normal” routine you experience with your email account on an average day, identify it, report it, and delete it.
- Carefully examine requests for personal information: Legitimate companies won’t ask for sensitive info like passwords or credit card numbers via email.
- Look out for odd branding: Inconsistencies in logos, fonts, or design may indicate that an email is fraudulent.
How to get rid of an email virus
While you might be able to keep an eye on suspicious email attachments, zero-click attacks are much harder to mitigate, especially when they hit via email.
As an average user, you probably won’t ever come across this type of malware, as it’s difficult to fabricate and tends to exclusively target politicians, military organizations, or enterprise leaders. You’re more likely to encounter threats through malicious links, mail attachments, or threats that automatically open fake pages on your browser or download additional files.
Even after receiving your email, the attachment is still stored on the Apple Mail servers and not your device. This means your device will only get infected if you download and run the suspicious file.
Remove malware from emails using Moonlock

For Apple Mail, Moonlock can scan and flag malware before you even tell it to. But don’t worry if you use another email client. You can still use Moonlock’s Malware Scanner to detect and remove all threats that might have come with a recent download or email attachment.
Here’s how to find and remove malware that has been downloaded from email:
- Sign up for a 7-day trial of Moonlock.
- Open Moonlock, then click on Malware Scanner from the left sidebar.
- If this is your first scan, you’ll need to configure your scan preferences. For that, click on the drop-down menu, then select Configure.
- In the new window, under “Scan type,” you can choose between Quick, Balanced, and Deep scan, with each scan type’s Speed, Depth, and Purpose listed below them. We recommend selecting a Deep scan and including all optional file formats: archives, disk images (DMG), and packages (PKG).
- Once you’re happy with your selection, exit the window. Click Scan.
Moonlock will proceed to sift through all the files on your Mac, looking for anything that might constitute a threat, whether it was a malicious email attachment, spyware, or adware. If it finds anything, it’ll capture and isolate it in Quarantine, away from the rest of your system, before fully and safely removing it.

What else should you do if you suspect that an email contains a virus?
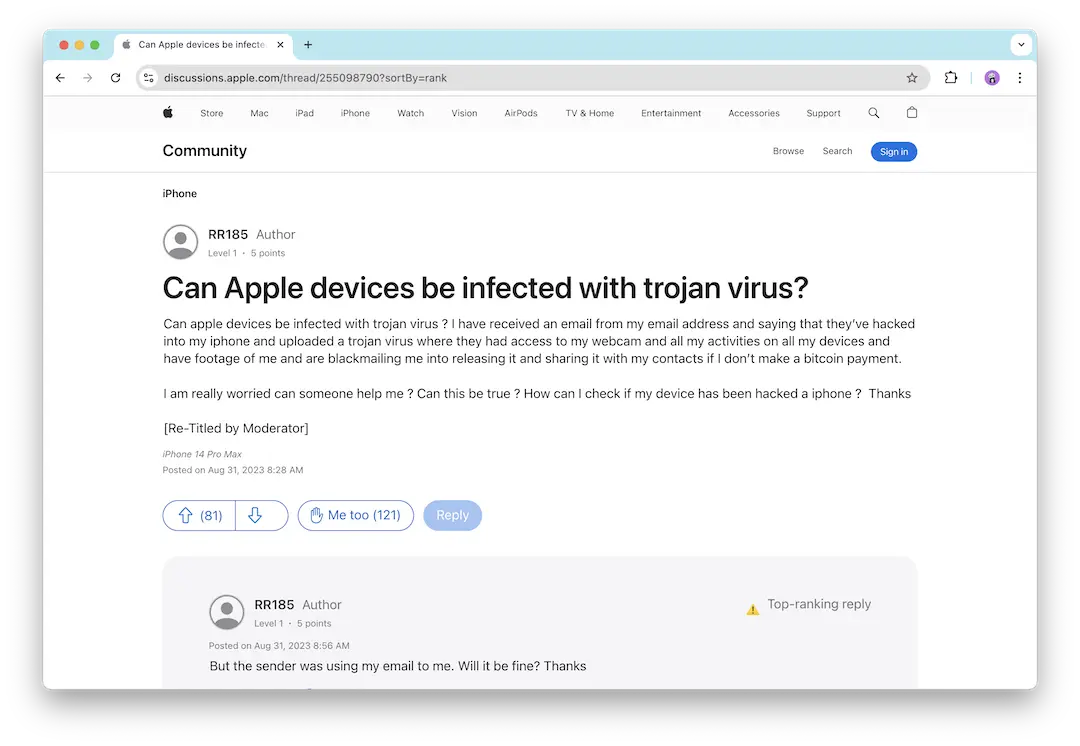
While we have covered most of the ground on what to do about email viruses and malware on your Mac. However, many users spend more time accessing email via their mobile phones. You might be wondering, can email malware infect an iPhone?
The short answer is yes. Cybercriminals are well aware that people often use their mobile devices to open emails. Consequently, malware can infect your iPhone just as easily as your Mac, so be certain to follow the tips listed above when accessing email on your phone.
Other common questions about email malware:
- Do email providers have anti-phishing? Yes. Gmail, Apple Mail, and others have built-in protections to catch phishing emails.
- Should I get an anti-phishing tool? If you’re serious about staying safe, an additional anti-phishing tool can help block threats that manage to sneak through.
- Are strong passwords and 2FA enough? Sadly, no. Hackers can still find clever ways around them. However, strong passwords and 2FA can add a layer of security.
- Are phishing scams getting smarter? Absolutely. Phishers use AI and tricks to make emails look legit, scale attacks, and conceal malware.
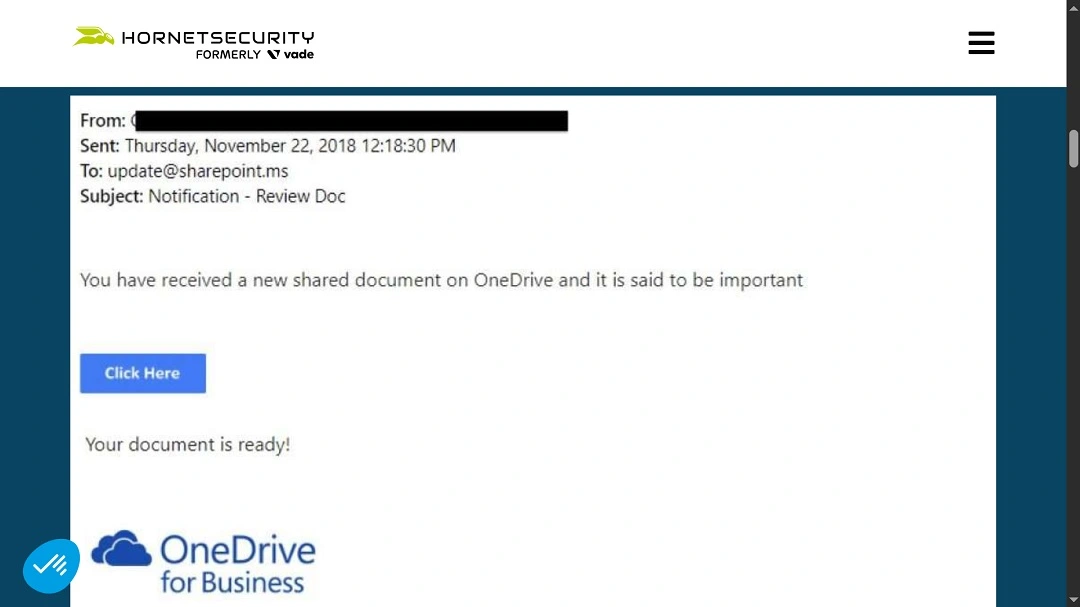
How to protect yourself from malware in email attachments
For those who have an email sitting in their inbox with an attachment and want to know if it contains malware, here are some simple tips to help you:
- Unknown senders can carry email viruses: This is true even without attachments. In general, if you didn’t expect it, just skip it. Random attachments are like uninvited guests — some just won’t leave.
- Enable Moonlock’s real-time protection: Moonlock can monitor all activity on your Mac, scanning new files and downloads for threats.
- An odd file type is a red flag: If the file extension is .exe, .zip, or .bat, it could indicate a not-so-fun surprise. Proceed with caution.
- Take advantage of built-in security tools: Let your email provider scan email for virus threats automatically. Turn on those built-in security features and let your email provider flag suspicious attachments.
- Hire a digital bouncer: Shop for a good anti-malware tool and let it scan attachments before you dive in to help keep your inbox safe.
- Contact the sender directly: If in doubt, text or call the sender. Trust your gut — it’s better to ask than to regret it later.
Finally, if you are getting too much spam, there might be something off with your configurations or settings. Read our guide on how to stop getting spam emails to rapidly fix the eternal spam issue.
Final thoughts
Staying safe from email threats is all about being cautious and aware and using the right tools. Whether it’s phishing, malware, or sneaky links, following simple steps like verifying the sender, checking links and attachments, and keeping your security software up to date will keep you one step ahead.
By staying vigilant and making smart choices, you’ll avoid falling for common email traps and keep your digital life safe.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and iPhone are trademarks of Apple Inc.






