We’ve all done it. We’ve typed the name of a website into the browser address bar and wondered why the page is not working. Then we discover that we’ve accidentally typed gooogle.com. Unfortunately, seemingly harmless mistakes like that can be exploited by something called typosquatting.
Also known as URL hijacking, typosquatting is a serious cyber threat. Below, we break down what typosquatting is, how it works, and how to avoid it.
What is typosquatting?
A proper typosquatting definition is a malicious scam in which cybercriminals and hackers take advantage of common URL typos to spread malware. They do this by buying domain names that have those misspellings, hoping that someone’s typing error will land them on their fake page instead.
If, as in the example we mentioned in the introduction, you attempt to go to Google but instead go to gooogle.com or goog1e.com, those domains could, in theory, be under the control of a hacker. Consequently, you will end up on their page instead. This is often a fake version of the page placed there to trick people into entering personal information or downloading malware.
How typosquatting works
Hackers and criminals try to brainstorm all the different ways that a domain name could potentially be misspelled. These spelling errors can include:
- Extra letters like yaahoo.com
- Adding or removing characters such as hyphens
- Registering other domain types, such as .net, .org, and so on
- Subtle changes like replacing letters with other characters, such as goog1e.com (the “l” being replaced by a “1”)

What are hackers’ motivations for typosquatting?
As always, a hacker’s primary motivation is money. They want to profit from your simple errors. They do this by:
- Sending you phishing emails directing you to their version of the website
- Placing malware such as trojans and spyware on their site to infect your MacBook
- Landing on the fake site will expose you to adware, which allows the attackers to gain ad revenue
- Intentionally damaging the reputations of well-known, high-profile brands, with extortion being the end goal
- Tricking business competitors into revealing sensitive information
The risks that typosquatting exposes you to
Needless to say, becoming a victim of typosquatting in cybersecurity can lead to serious consequences. Here are some things you can expect to likely happen to you:
- Identity theft: Having personal details stolen, such as your name, address, social security number, and bank account details, will expose you to having your identity stolen.
- Malware installed: If you believe you have visited a malicious site and there is malware on your Mac as a result, you can use Moonlock to neutralize it. Moonlock is designed specifically for macOS and can run a full Deep Scan to uncover any threats on your device. Its real-time protection and background monitoring will then keep you protected moving forward.
- Financial damage: If bank account details, credit card numbers, and sensitive business information are taken, you will suffer a degree of financial loss. For businesses, it could lead to bankruptcy.
- Brand damage: As stated in the section above, if a customer or client is redirected to a fake website, they may blame the real site they meant to go to. This could damage the company’s brand and lead to financial losses.

Notable legal cases
The following are some real-world typosquatting examples that help to illustrate the threat:
- Wells Fargo vs. weiisfarg0.com: How anyone could think a site with a URL is real is anyone’s guess, but this is what happened in 2021, when Wells Fargo took action against the typosquatting website weiisfarg0.com. Wells Fargo ultimately won the case and was given control of the fake site.
- Facebook vs. Facebobk.com: In 2013, it was discovered that cybercriminals had registered over 100 different variations of the Facebook domain, including Facebobk.com. Facebook won the case and was given control of all the domains.
- Google vs. 3 domains: Obviously, Google is a top target for typosquatting hackers. Among the many instances of typosquatting against them, a 2005 case saw them sue the owners of goog.kle.com, ghoogle.com, and gooigle.com, which were being used to spread malware. Unsurprisingly, Google won the case.
Prepending vs. typosquatting
There are 2 ways that criminals can redirect users to fake domains. We’ve covered typosquatting, so how does “prepending” work?
Prepending is when an attacker tries to mislead you by putting information at the beginning of a bad URL. They can also manipulate an email subject line, for example, to trick people into accepting the email at face value.
Here’s how it works:
- If the fake site is, for example, fakesite.ru, then they may try to muddy the waters by making a long URL to obscure the fake domain. So fakesite.ru could have a subdomain added that makes the URL search.google.com.fakesite.ru. The victim will see the subdomain and mistakenly assume it is legitimate.
- How many times have you received a spam email with “Re:” or “Fwd” in the subject line? This is meant to mimic legitimate emails that are part of email threads or emails that have been forwarded.
So, to sum up the difference, typosquatting is exploiting domain typos, while prepending is manipulating how people view things, such as emails and web links.
How to identify typosquatting domains
There are a few ways you can spot a typosquatting domain. Check out the following clues to identify typosquatting attacks.
Incorrectly spelled web links

The most obvious sign, as we’ve outlined above, is a web link that is spelled wrong. If you see a link spelled as microsofft.com or amaazon.com, don’t go there.
The wrong domain type
Big-name websites almost always use “.com.” If you see a domain called google.net or amazon.org, you could be viewing an example of typosquatting.
No secure HTTPS
These days, legitimate sites always start their web address with HTTPS (secure certificate). If a URL is only HTTP, don’t click the link. This isn’t always foolproof, however. Though many criminals don’t bother with obtaining secure certificates, they can use HTTPS for their fraudulent websites, too.
Shockingly bad website quality

It’s a safe bet that Google won’t have a blurry logo, grammar mistakes, or ads on their front page. Outdated content is another red flag. The New York Times probably isn’t going to post the results of the 2024 US elections on their front page in 2025.
What tools and techniques help detect typosquatting?
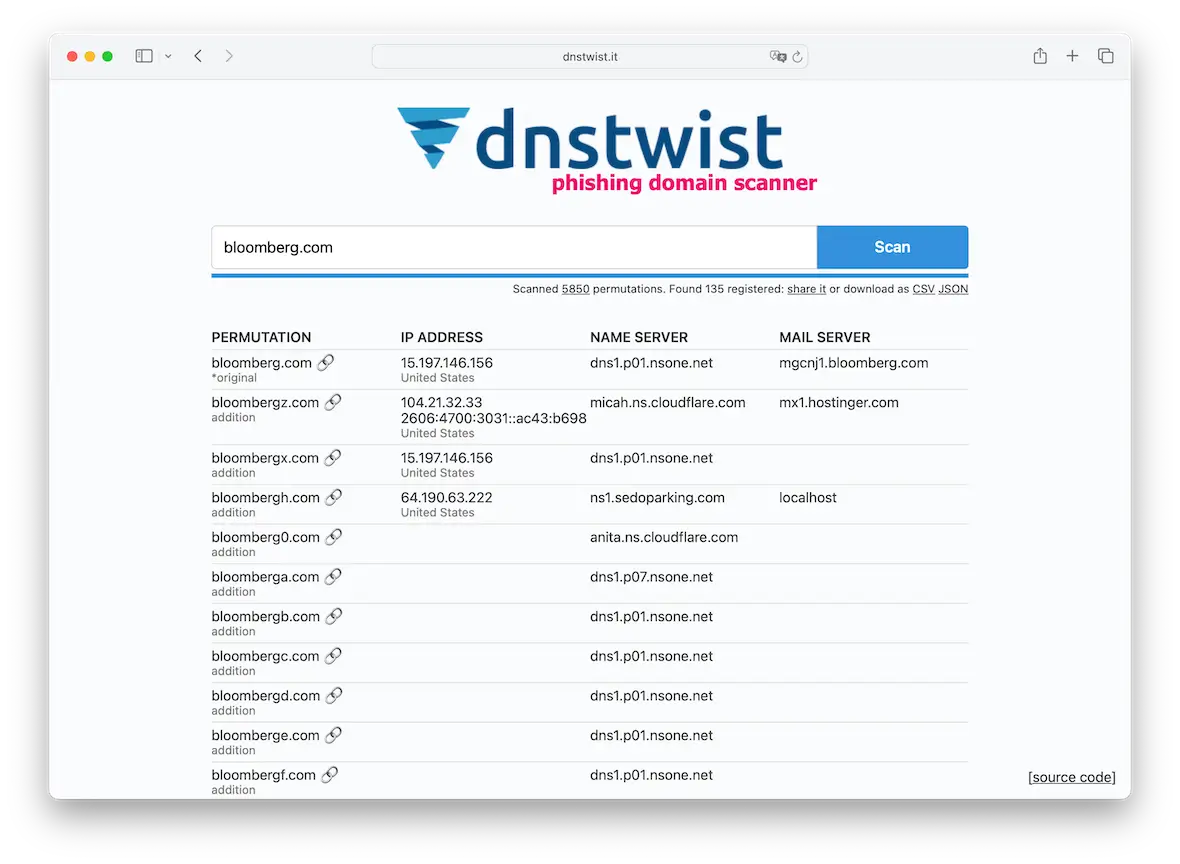
If you’re unsure if a domain is fake, plug the address into dnstwist. It will tell you the name of the real site, as well as known fake versions.
Other services that do the same thing include Typosquatting-Finder and Have I Been Squatted? However, all of these tools require that you be vigilant and check the domain before you visit it.
What to do when you encounter typosquatting
If you encounter a typosquatting attack, here’s how to proceed:

- Do not click on any links or interact with the fake website in any way. Leave the site immediately.
- If you worry that your Mac has been infected with malware after visiting a suspicious site, it’s worth it to run a deep malware scan with Moonlock. It will isolate hidden threats like trojans, spyware, and adware and move them to quarantine, where you can review and delete them. This will prevent the malicious files from doing any more damage to your Mac. Moonlock has a free 7-day trial, so go ahead and give it a try.
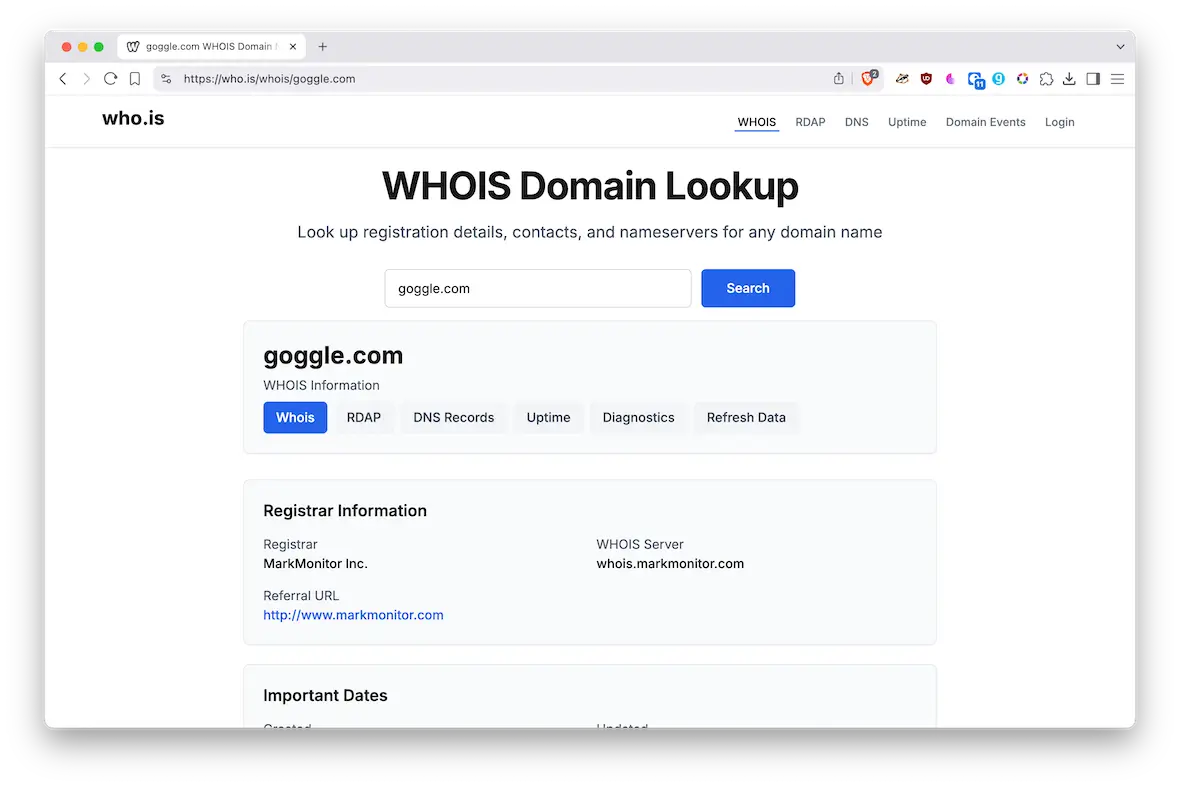
- Run a WHOIS lookup and find the company that is hosting the fake site. Report the site to the hosting provider and demand that the site be taken down.
- If the site is infringing on your trademarks and copyrights, consult a lawyer to get your legal options.
- Consider going to the police if you think the fake website has committed fraud against you or your customers. Law enforcement may be limited in how they can respond, depending on your resources. A good start would be to get the name and address of the site owner from WHOIS.
- Warn your family, friends, and business clients that the site exists and tell them not to interact with it.
What legal options do you have against typosquatting?
In cases of typosquatting, there are 2 laws you can take advantage of. That said, we highly recommend that you employ the services of a legal professional:
- Uniform Domain-Name Dispute-Resolution Policy (UDRP)
- Anti-Cybersquatting Consumer Protection Act (ACPA)
These laws allow you to challenge any domain registrations that infringe on your trademarks and copyrights.
Steps you can take to avoid typosquatting scams

Although it’s difficult to avoid making the occasional typo, there are ways you can minimize the risk of malware. Here are a few:
- Always check the link you’ve typed before you go to it. It only takes a few moments to scan it.
- If the URL for a site like Google, Microsoft, or Amazon has a .org or .net ending, leave immediately.
- Never ignore browser warnings that tell you that the site is dangerous.
- Never override a browser when it blocks you from going to non-HTTPS websites. It’s not trying to annoy you. It’s trying to protect you.
- If you believe you have been infected with malware from a malicious site, or you just want peace of mind, you can use Moonlock to detect and neutralize threats before they even become an issue. All suspect files are quarantined immediately with real-time protection, and Moonlock’s Deep Scan will remove all existing threats from your system.
- A VPN can’t prevent typosquatting directly, but it will encrypt your internet traffic and hide your IP address, protecting your online activity and identity. Moonlock VPN adds that extra layer of security when you’re on public or untrusted networks, such as airports, cafés, or hotels.
- Never override macOS security settings. If typosquatting malware manages to slip onto your machine, those security settings can make all the difference.
It seems like there is nowhere that malware doesn’t extend to online. Now, attackers are even jumping all over your typos.
As malware threats evolve, so too must detection methods. Fortunately, Moonlock will be there to help you defeat cybercriminals and stay safe online.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and MacBook are trademarks of Apple Inc.