When going online, you want to be reassured that your Mac security is strong enough to stand against all types of threats. Malware is a growing problem, and although you hopefully have strong security software for Mac, a firewall, and a password-secured network, you still need to be satisfied your Mac can withstand a full-frontal assault if malware breaches the outer defenses.
Are Macs considered secure?
While Macs are considered to be a fairly secure devices that make it difficult for malware to propagate and wreak havoc, they aren’t completely secure. In fact, a completely secure device is impossible.
No device is infallible. However, MacBooks are built in a way that utilizes several key security features, which give them a fighting chance against malware.
Your MacBook is split up into multiple partitions, and each partition is sandboxed against the others. This means that even if malware enters one section of the Mac, the chances of it spreading to other areas of the Mac are low, thanks to the restrictions of sandboxing.
This is not to say that a Mac is perfect. Far from it. And while Apple’s security protocols are strong, malware is evolving all the time, and cybercriminals have learned how to breach sandboxed partitions. Consequently, adding a form of backup support in the form of third-party security software may be a good idea.
Is macOS more secure than Windows?
As we said, Macs are not perfect in terms of security, but compared to a Windows PC, they are much more secure.
First, as we’ve outlined, the Mac is designed in a way that separates each app and operating system file from the others. Macs also have powerful built-in tools that do a good job of repelling any attempts by malware to scale the walls.
Third, Macs get regular operating system updates, and, compared to how Windows brings out its updates, Mac updates tend to be smoother and faster. This helps motivate users to install them more quickly.
However, we can’t emphasize enough that despite these advantages, a Mac is still vulnerable to cyberattacks. Macs do get malware and viruses. And as the popularity of the Mac grows, so does the target on its back. In fact, it’s now more profitable than ever for criminals to target Mac users.
Malware and virus threats against Apple machines are increasing and evolving daily. Apple does a first-class job of trying to keep up, but sometimes it’s not enough. This is why you should complement your Mac cybersecurity with third-party solutions to complement what Apple already provides.
Do Apple M chips improve the hardware security of MacBooks?
Apple has upgraded their MacBooks with M chips, which improve the device in many ways, especially performance. But what about security? Do M chips improve a MacBook’s security?
The answer is yes, they do (with one exception, which we’ll come to in a moment).
First, there is something called Secure Enclave, which handles the Touch ID and encryption key storage. This isolates these features from the rest of the operating system, making them safer from malware.
Next is Unified Memory Architecture, which protects the system memory from unauthorized access.
Last of all, M-series Macs have Advanced Threat Detection, which uses machine learning to proactively identify and neutralize security threats.
The GoFetch vulnerability
We mentioned above that there was an exception to the enhanced security from M-series chips. This is called GoFetch.
Without getting too much into the technical weeds, GoFetch refers to a family of malware through which attackers have managed to extract secret keys from Macs, even those using M chips. The vulnerability is supposed to be “unpatchable,” and any improvements to plug the vulnerability will supposedly seriously impact M-series chip performance, especially the M1 and M2 generations.
The GoFetch issue proves that Macs are not as perfect as Apple has made them out to be in the past.
How to keep your Mac safe
We recommend always having third-party antivirus protection software on your Mac. Hardcore Apple fanboys may debate this statement, but, as we’ve just outlined with the GoFetch attack, certain well-known Mac vulnerabilities are unpatched. We recommend using the Moonlock anti-malware app.
Moonlock is a next-level Mac security software specialized tool focused on a specific task. It doesn’t weigh itself down with add-ons like password managers, as you might find on typical antivirus platforms. This makes it lightweight on system resources.
Let’s go into how Moonlock will help you keep your Mac safe from external threats.
Run a protection scan to find malware with Moonlock
Start by opening Moonlock. Then click on the Malware Scanner tab on the left-hand menu. Once there, you’ll be able to choose between a Quick, Balanced, and Deep scan from the drop menu. And finally, click Scan.

Moonlock will run a system-wide scan, checking for all kinds of malware on your device, such as ransomware, adware, spyware, or remote access trojans (RATs). If it finds any, it’ll immediately isolate and neutralize them. The process is simple and takes only a couple of clicks on your end. You can sign up for a free trial of Moonlock and run your first protection scan today.
Set up real-time protection
While Moonlock’s Malware Scanner is perfect for catching any threats already lurking around your Mac, real-time threat monitoring continuously searches for malware 24/7. It keeps track of every file you interact with, including ones you download to your device. That way, it’s able to react instantly if it notices anything out of order, even during your Moonlock free trial.
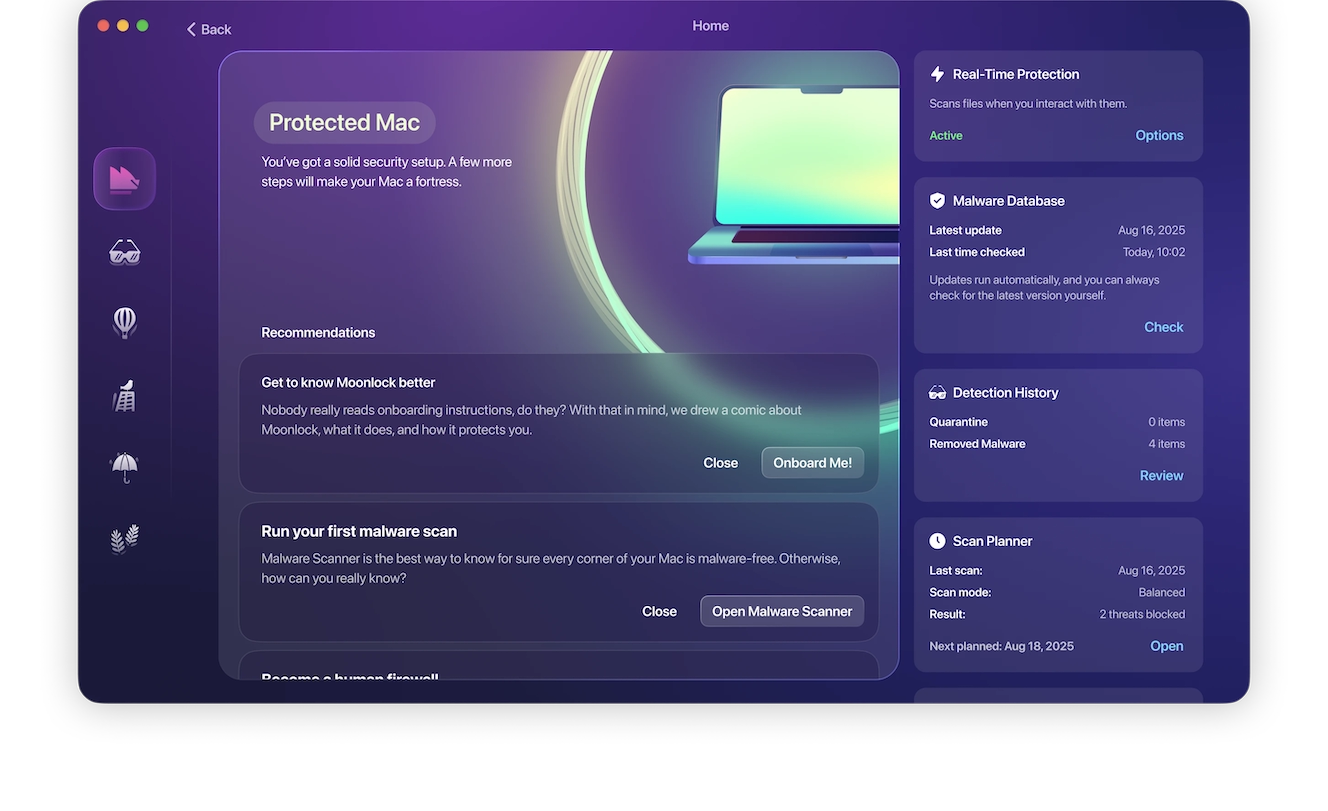
To enable Real-Time Protection in Moonlock, open the app and make sure you’re on the Home tab, which you can select from the left-hand sidebar. Then click Explore. There, you’ll see all the features and settings available to you in Moonlock.
From the sidebar on the right, find Real-Time Protection, then click Options. Under Malware Scanner, there’s an option for “Continuous monitoring.” Tick the box called “Turn on real-time protection.”
Update your installed apps with one click and remove app leftovers
Another essential policy for improving Mac security is to keep your apps updated at all times. If an app develops a vulnerability, the developer will develop a patch and push it out to users. These can be updated automatically if they have been downloaded from the Apple App Store.
If, however, you install a trusted third-party app (desktop WhatsApp, Slack, etc.) that didn’t come from the Apple App Store, it may not be automatically updated.
The CleanMyMac smart cleaner takes the task of manually checking for updates off your hands and tells you when something needs to be updated. It’ll even do the update for you if you let it.
In the same vein, CleanMyMac will also remove “app leftovers” from apps you’ve uninstalled.
Check login items and background processes
Malware may set up its own program that constantly runs in the background of your machine, using up system resources. It will also set itself up to automatically start when you log in to your MacBook.
Checking background processes and login items is, therefore, an important aspect of Mac security. Doing so will tell you, at a glance, which processes are starting up and then running, hidden in the background, so you can stop them.
The built-in Mac security features you should be using
Macs already have several built-in security features that are likely protecting you without you even realizing it. Some require that the user enable them manually, but others are enabled by default.
We covered some of Mac’s security features in our article about whether MacBooks need antivirus or not, but here’s another quick rundown.
XProtect
XProtect is the Mac’s built-in antivirus scanner. It compares possible threats against a database maintained by Apple. It’s an excellent defensive tool, but its drawback is that it only deals with threats actively coming onto the device. It doesn’t give you proactive advice, such as warning you of dangerous links and suspicious downloads.
XProtect is enabled by default and can’t be switched off. Therefore, this starts running in the background as soon as you start the Mac, and no input is required from you.
Gatekeeper
To protect your Mac from malicious apps, you should try to download as many of your apps as possible from the Apple App Store. Everything available on the App Store has been heavily vetted and monitored by Apple, so the chances of malware coming from the App Store are remote.
Many first-class third-party developers, like Moonlock, operate independently from the App Store. Unfortunately, there are also a lot of dishonest developers who stuff their Mac apps with malware.
Gatekeeper is a background feature on your Mac that scans all incoming apps being installed and checks to see if they’re approved by Apple. If not, the installation will be blocked. You can override the block in the macOS security settings, but doing so may make you reconsider whether you really do want that app after all.
Firewall
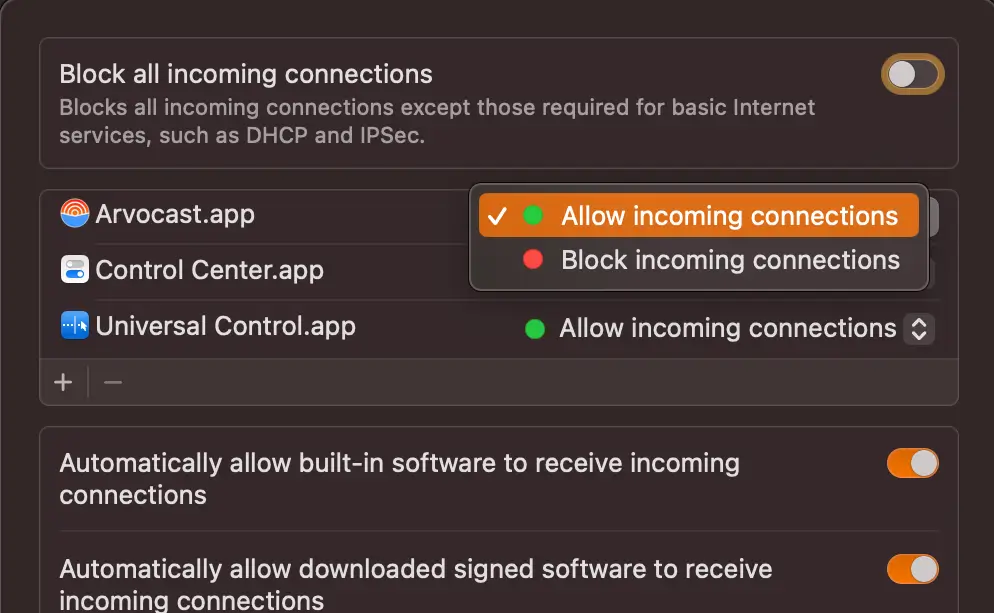
The built-in Mac firewall is the first line of defense after your Wi-Fi network. If malware manages to penetrate your network, then the Mac Firewall is the first obstacle that malware has to overcome.
The Mac Firewall is a feature that must be enabled by the user — it isn’t on by default. But once you enable it, that should be it. Although you can tweak settings for individual apps, this usually isn’t required.
Just go to System Settings > Network > Firewall, and toggle it on.
FileVault
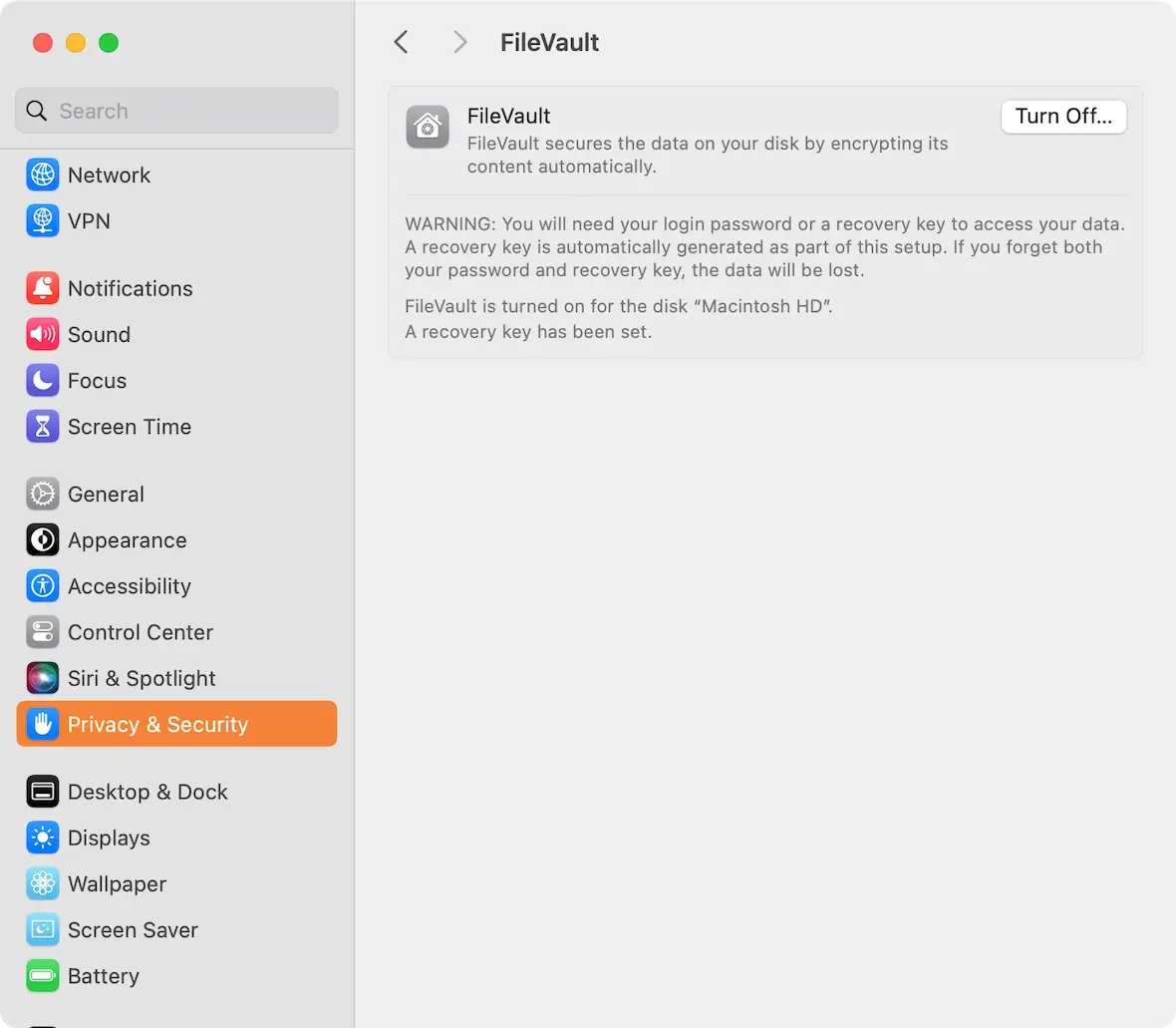
FileVault is another feature that must be manually enabled by the user, but, like the Mac Firewall, it’s a “switch it on and forget about it” deal. FileVault encrypts your entire hard drive, including all the files. Then, when the MacBook is turned off, your files are inaccessible.
To enable FileVault, go to System Settings > Privacy & Security > FileVault, and click the Turn On button. How long it takes to get started depends on how many files you have to get encrypted. If your MacBook is new, FileVault won’t take much time at all.
Lockdown Mode
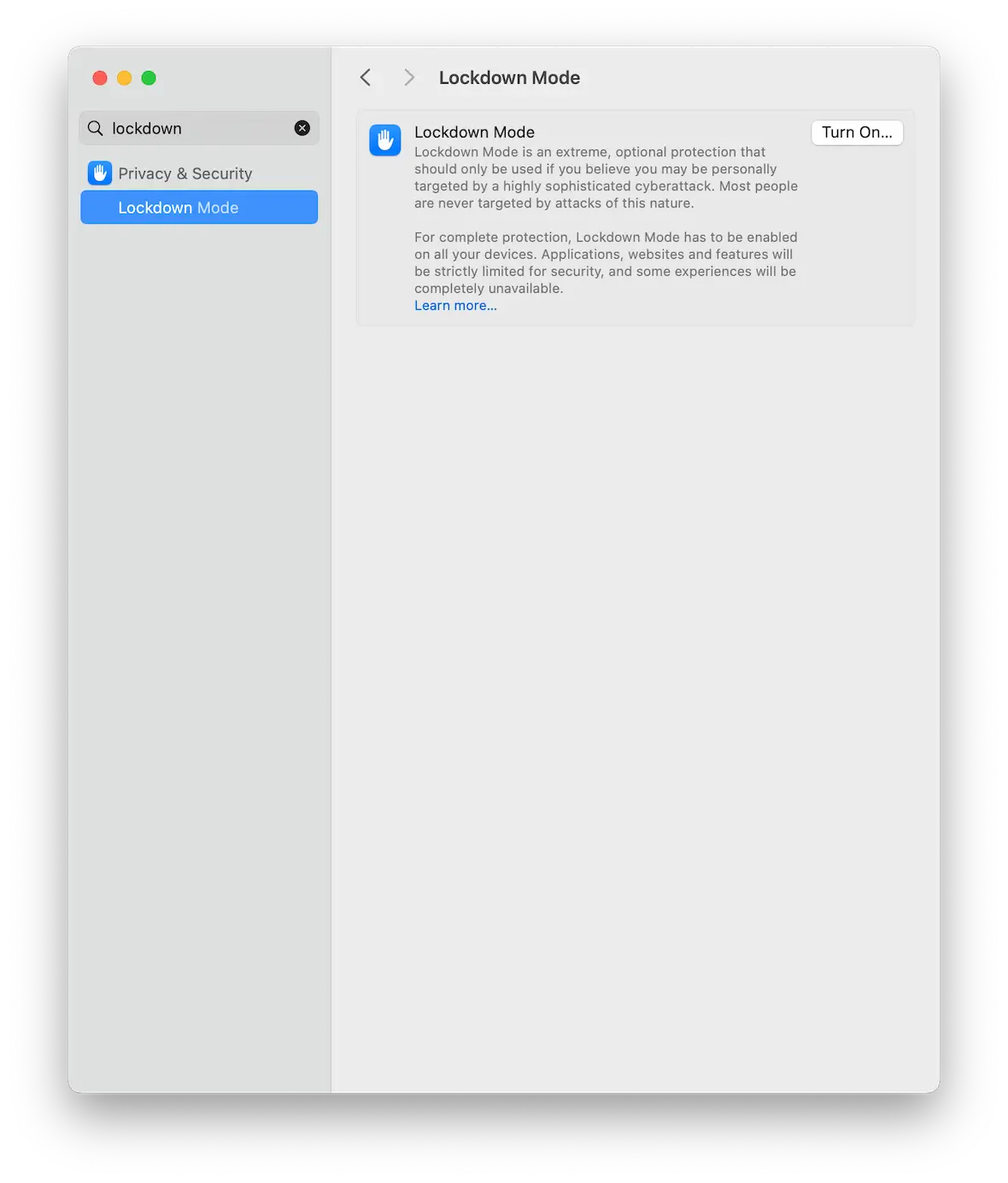
Lockdown Mode is the nuclear option when it comes to cybersecurity, and it should only really be used if you feel that you find yourself in a critical security position.
Lockdown Mode affects some key features of your MacBook. It limits FaceTime, disables file sharing, and blocks all external devices from connecting to your MacBook.
How else can you protect your Mac from threats and cyberattacks?
There are many other ways you can protect your Mac from external threats.
Cover your webcam and silence your microphone
One of the ways hackers get information from their victims is by watching them through their webcams and listening via their microphones. You can neutralize that threat by covering your webcam when you’re not using it.
To mute your microphone, use a trick done by Mark Zuckerberg. Take an old pair of wired earbuds and cut the wire just above the USB plug. Put that USB plug into the MacBook’s socket. This, apparently, stops anybody from being able to listen in.
Limit app permissions
When an app is installed on your MacBook, it may request access to your microphone, your webcam, your location, and other things. Quite often, these permissions are not required, but the app asks for them anyway.
On a regular basis, you should go to System Settings > Privacy & Security. Choose a category like Microphone and see which apps currently have access to it. Disable any that don’t need it.
Install a VPN
We’re big fans of VPNs, and for good reason. VPNs heighten your security by a wide margin, rerouting your internet connection to a secure, encrypted tunnel, thus preventing man-in-the-middle (MITM) attacks.
In Moonlock, we take VPNs to the next level by incorporating a Kill Switch feature that automatically cuts your internet connection if your VPN drops. That way, you don’t have to worry about accidentally revealing your IP address to any person or website online. We also have a strict no-logs policy, because we believe your IP address is yours and yours alone.
Moonlock VPN works by creating an encrypted tunnel that takes you anywhere you want to go online while keeping you protected and anonymous. This is particularly useful if you often rely on public Wi-Fi for internet access, where hackers could set up all sorts of tricks to intercept your traffic.
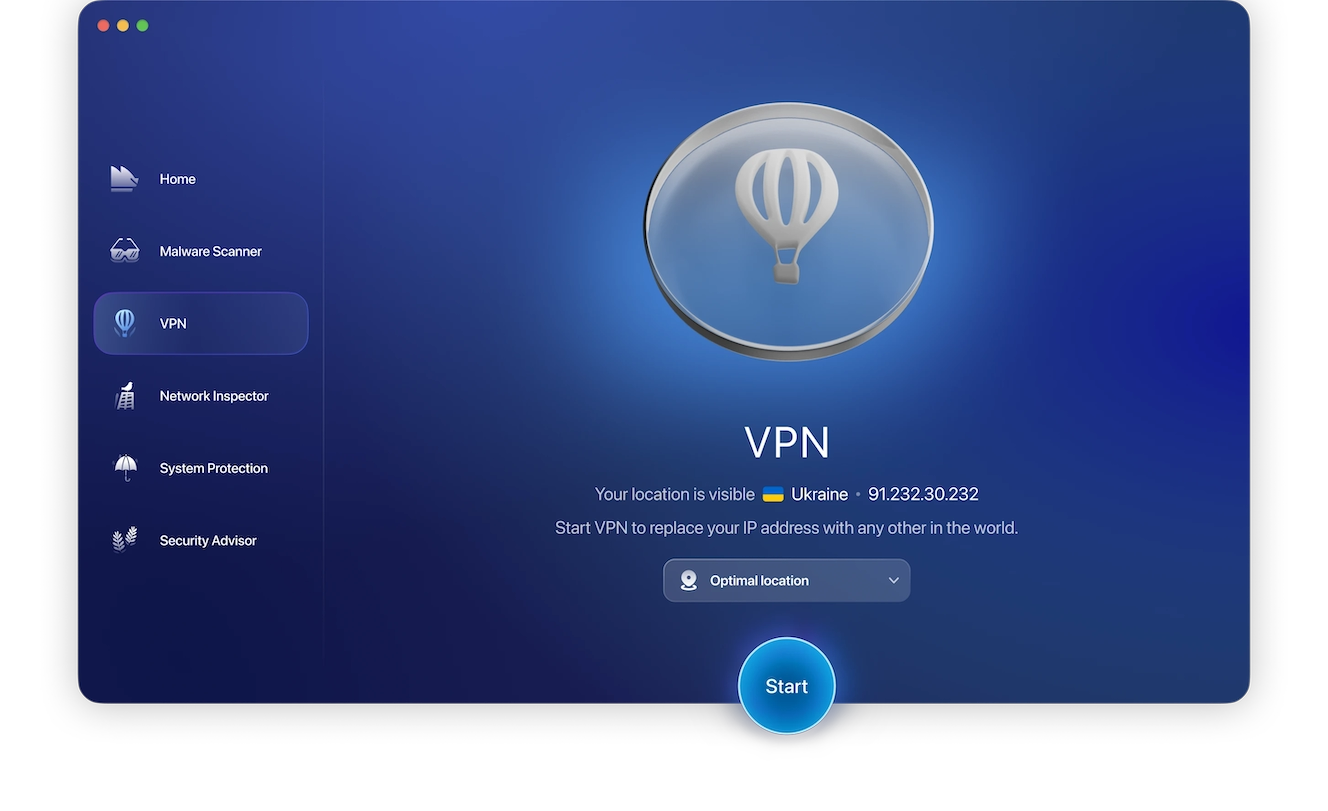
Best of all, Moonlock VPN is right there in the app — no need to install any additional software or browser extensions. Get started with Moonlock, navigate to the VPN tab from the left sidebar in Moonlock, choose your preferred location from the drop-down menu, and click Start.
Limit AirDrop to Contacts Only
AirDrop is a remarkable innovation for sharing between Apple devices, but one potential security vulnerability is having it set to accept files from everyone in the immediate area.
Go to AirDrop on your Mac, and make sure the setting is set to Contacts Only. Even better, disable AirDrop entirely and only enable it when you need to use it.
How to physically secure your Mac
How can you protect your data if you lose your MacBook or if it’s stolen?
Set a strong screen password
This should be a given, but neglect to protect your MacBook with a strong password.
Go to System Settings > Users & Groups. Select the user. On the next screen, you’ll see an option to set a password for that user’s login.
Enable screen lock after X minutes of inactivity
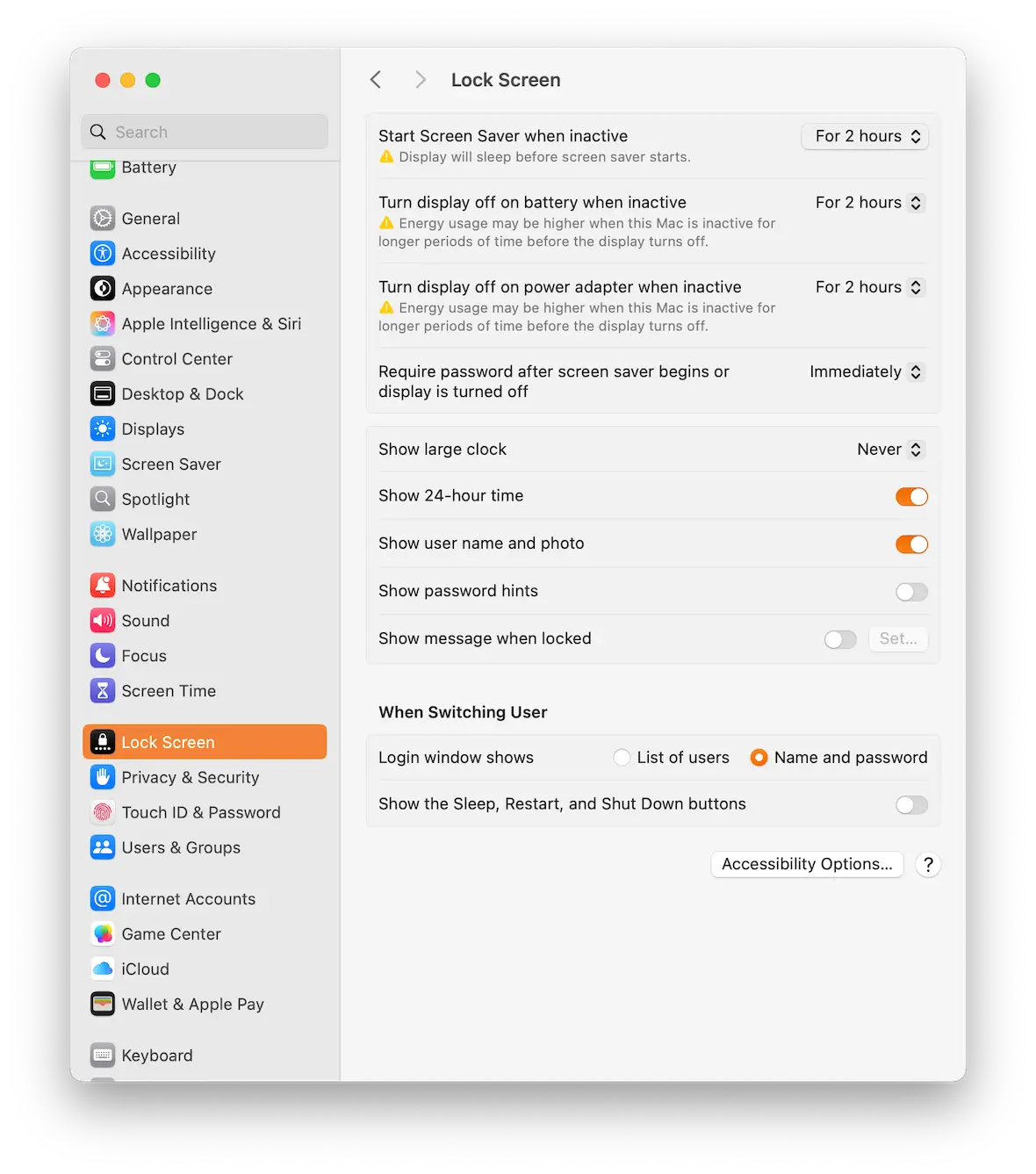
Next is to tell the MacBook to lock the screen once you’ve been inactive for a set period of time.
Go to System Settings > Lock Screen. You’ll find various options for when the screen lock should kick in.
Activate Find My Mac
If you lose your MacBook or have it stolen, Find My Mac can be the difference between finding it and permanently losing it.
To enable Find My Mac, go to Apple Account > iCloud. Under iCloud, click See All and select Find My Mac. Turn on both Find My Mac and Find My Network.
What are the common threats that target Macs?
We’ll finish by summarizing some of the common threats that target Macs. Here’s what they are and what to look for:
- Phishing attacks: A phishing attempt occurs when you are sent an infected link that leads to a malware download.
- Adware: This is a form of malware that inundates a user with ads, such as pop-ups, potentially leading to insecure online destinations.
- Ransomware: This type of malware targets businesses and personal users alike by infecting their computers via their networks. The files are then encrypted, and a ransom is demanded in exchange for the decryption key.
- Remote access trojans: As the name implies, a RAT is a type of malware that gains access to your MacBook remotely, giving the hacker access and control to certain aspects of your device.
Threats against Macs are increasing at an alarming rate. Fortunately, by following a strict guide of security protocols and rules and installing Moonlock, you can defend your MacBook and protect your data from anything that attempts to throw itself at you.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac, MacBook, and macOS are trademarks of Apple Inc.