How savvy is the average person in their understanding of cybersecurity? That is exactly what we have been trying to find out.
To celebrate and raise awareness during Cybersecurity Awareness Month 2024, Moonlock launched a quiz for people to test their knowledge and understand how well they are protected.
What we found after running a cybersecurity quiz
Moonlock’s Cybersecurity Quiz, which remains live, has already shed some light on users’ security and privacy awareness. In this report, we share the first findings, as the 350 responses we’ve gathered reveal patterns and trends.
1. Quite a few people still think iOS is malware-free
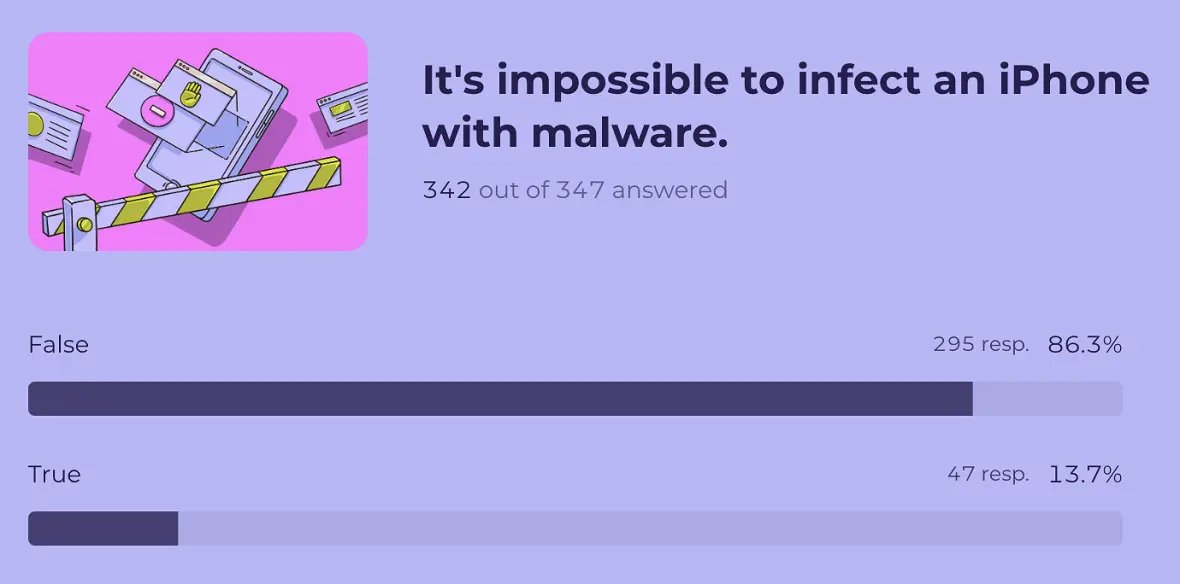
Apple’s security and privacy-centric design has been so efficient that Apple devices often exceed the security standards of the industry. This security reputation has created a myth that neither Mac computers nor iPhones can be infected with malware.
However, in the past years, Apple devices have become more popular among enterprises. In response, cybercriminals have evolved, and macOS and iOS have been successfully targeted with malware like the AMOS stealer and spyware like Pegasus on phones.
As global threats against Apple users escalate, we wanted to know if people are over the “Apple security myth” and just how aware they are about iPhones being targeted.
To our welcomed surprise, we found that about 87% of those surveyed said the statement “It’s impossible to infect an iPhone with malware” is false. However, that means 13.7% still believe that the myth is true.
If you want to hear more about iPhones and malware, check out our article Can an iPhone get a virus or malware, and what are the signs?
2. Almost all users know Apple does not send security notifications
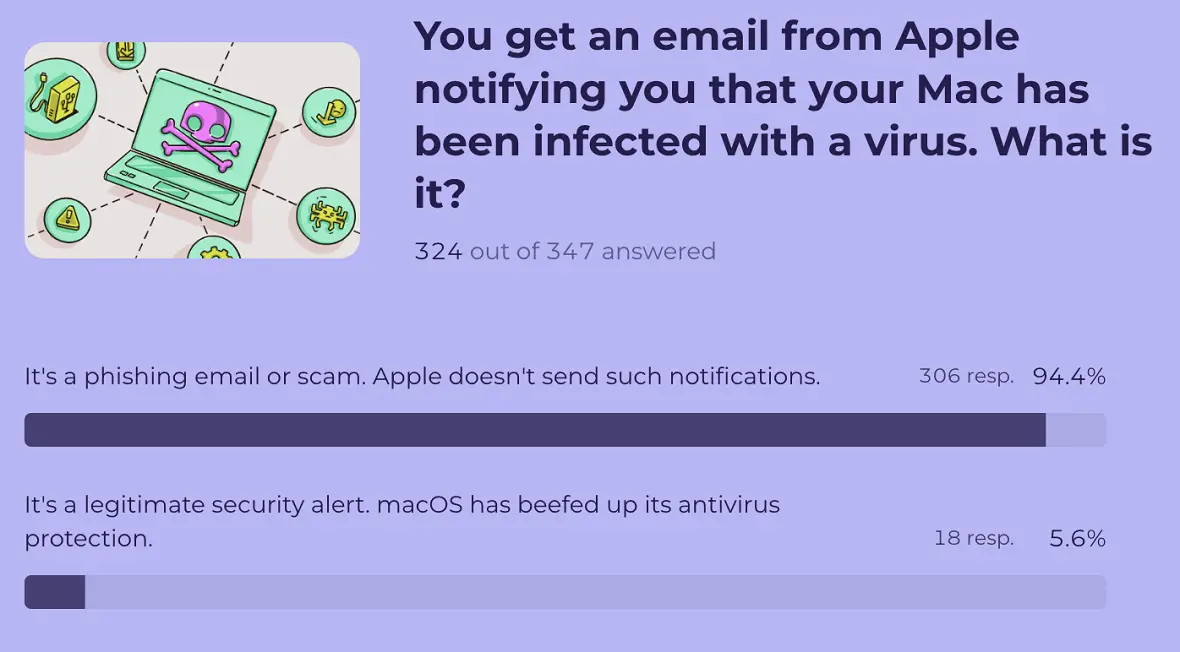
Most cyberattacks start with a simple email. Whether it targets high-level executives or just regular folks, phishing is the weapon of choice for bad actors.
But what happens when you get an email from Apple saying that your Mac computer is infected? Should you trust it or not?
Fortunately, a staggering 94.4 % of users know the correct answer to that question.
Apple does not send emails notifying users that their Macs have been infected with viruses. Such emails are typically phishing scams designed to trick users into revealing personal information or downloading malware.
More awareness work still needs to be done, as 5.6% still believe that Apple sends security emails about macOS. However, it’s a big win to see most users getting this key issue right and closing the door on phishing.
3. 95% know that a strong password is not enough to stop hackers
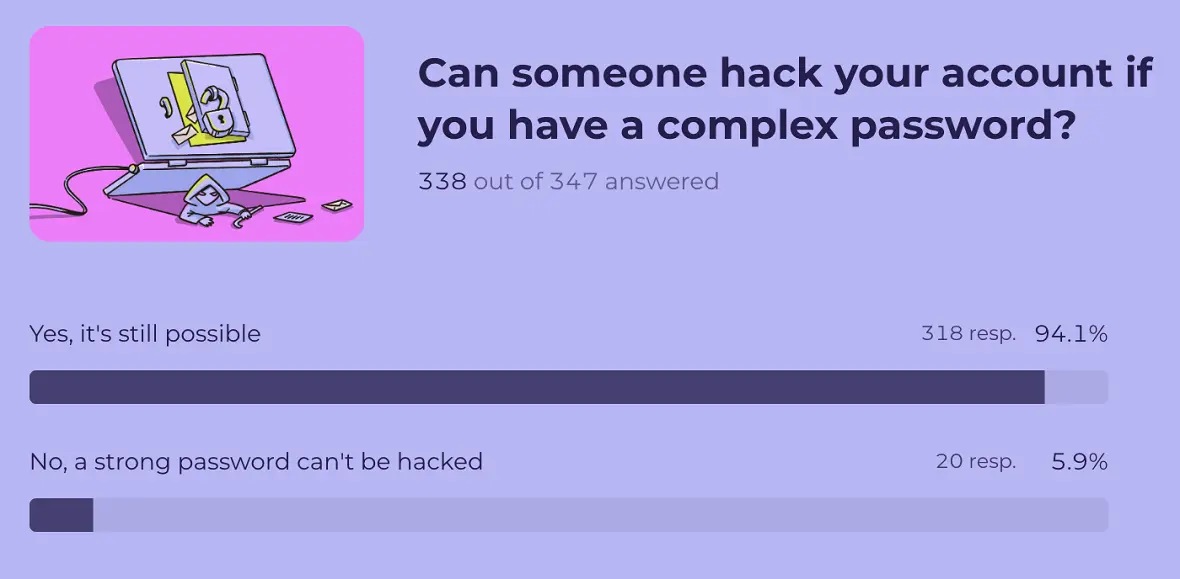
Can someone hack your account if you have a complex password? That’s what we asked our quiz participants. While for some, the answer to this question may seem obvious, the fact that passwords are sold every day online on the dark web, driving credential stuffing attacks to new levels, proves that users are not that aware of this issue.
Those who took our quiz rightfully said that a complex password is not enough to stop a hack. As mentioned, your password may be unknowingly leaked or compromised in an unrelated attack, which means it could be used to breach your account.
Fortunately, even when attackers have your password, there is still a way to stop an attack. By adding a layer of security, 2-factor authentication (2FA), or better yet, multi-factor authentication (MFA), users can prevent anyone from taking over their password-protected resources.
If you are in the 5.9% who still think a password is enough, you can learn more about password security in our video.
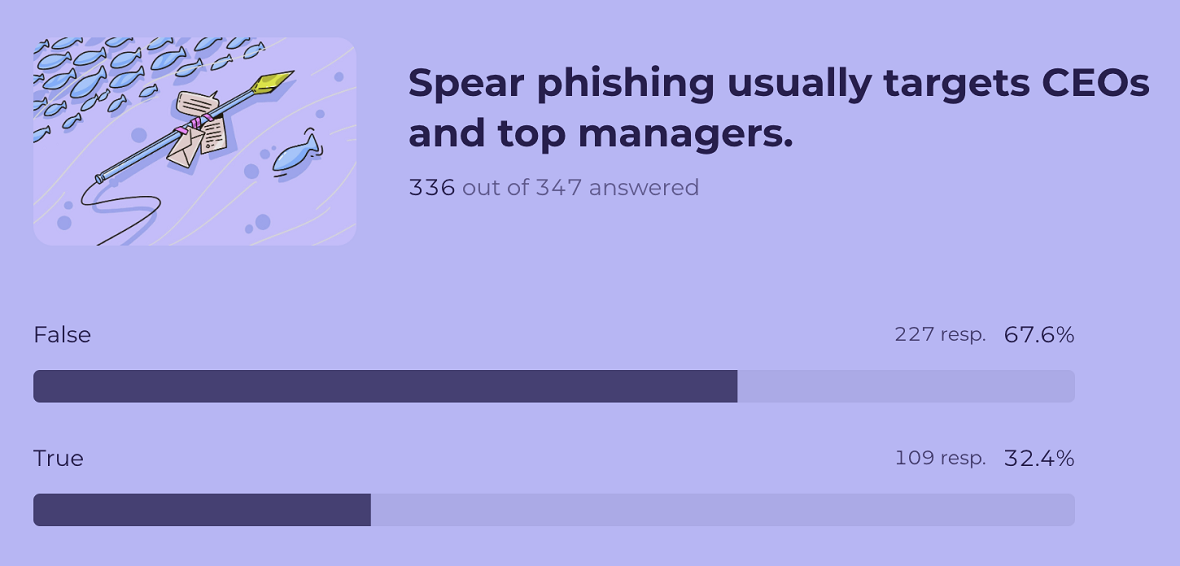
4. A third of respondents don’t understand who spear phishing targets
Perceptions in cybersecurity matter. For example, a person might believe that they will not be targeted via sophisticated emails because they aren’t a CEO or someone “important enough.” They might be under the impression that because the company they work for is “small,” they don’t need to take steps to protect themselves. Consequently, they may easily mistake a malicious email for a legitimate one.
If, however, that same person knew that there are many different types of spear phishing, including whaling, CEO phishing, employee phishing, and even espionage phishing, they would probably take preventive action.
A majority of respondents (67.6%) said it is false that “Spear phishing usually targets CEOs and top managers,” answering correctly. In contrast, 32.% answered incorrectly, which could mean they are leaving open doors for cyber-attackers to exploit.
Remember, while spear phishing can certainly target CEOs and top-level managers, it’s not limited to them.
To learn more about types of spear phishing — including new tactics targeting, for example, the blockchain and crypto industry — read our extensive guide to spear phishing.
5. Only 7 of every 100 iPhone users know how many times they can enter the wrong passcode
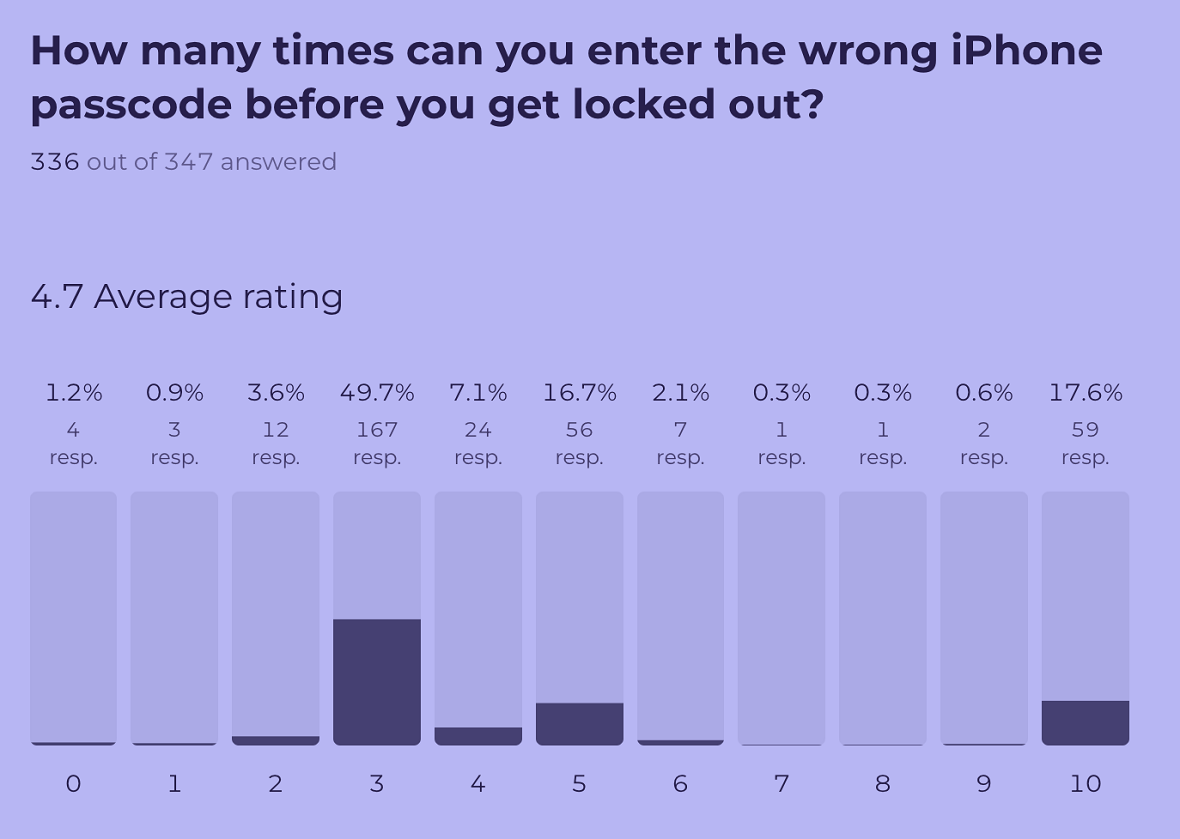
Knowing exactly how many attempts you have to enter the right passcode on your iPhone might be difficult for even the most tech-savvy user. Many of our quiz participants (49.7%) wrongly assume the answer is 3 times.
Some (17.6%) even say 10 is the number of times you can enter an incorrect passcode. Naturally, for security purposes, this number is far too big and would give attackers too many opportunities to crack an iPhone.
The correct answer in this case is 4. That is the exact number of tries anyone has before being locked out.
As Apple explains, “If you enter the wrong passcode 4 times in a row, you’ll be locked out of your device, and you’ll receive a message that says iPhone is disabled.”
6. The majority of users correctly understand end-to-end encryption in messaging
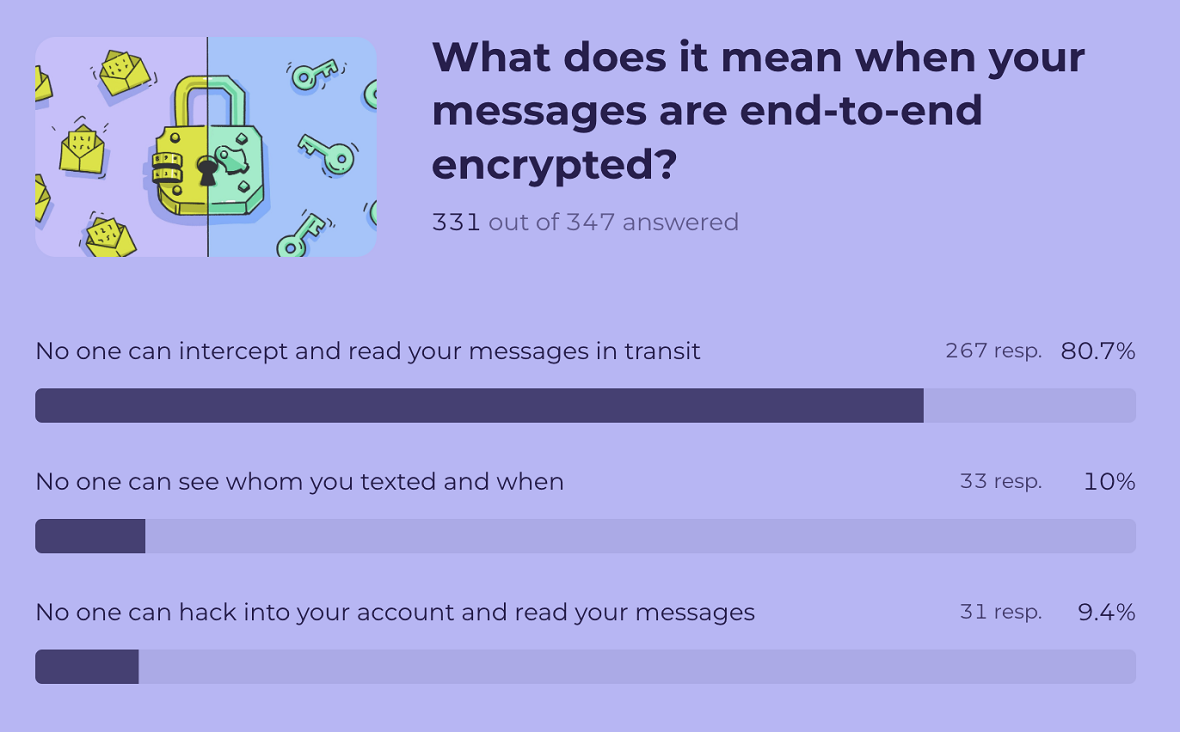
For our end-to-encryption question, 80.7% correctly said that messages that are end-to-encrypted mean that “No one can intercept and read your messages in transit.”
End-to-end encryption (E2EE), according to our detailed encryption explainer, is a highly secure method of communication where only the sender and the intended recipient can read messages. The messages are encrypted on the sender’s device and only decrypted on the recipient’s device, meaning that no one in between, not even the service provider, can access the content.
This does not mean the message cannot be hacked (as 9.4% said) or that no one can see who you texted and when (10%).
7. Most know that accessing data on Macs without a password is possible

We have all heard the stories of how difficult it is to access a Mac or an iPhone if it’s password-protected. Law enforcement has even requested numerous times that Apple create a backdoor so they can read the data on devices that belong to suspects of a crime.
However, as most users correctly answered, if your MacBook is password-protected, the data on it can be accessed in many ways. The password protects the account on your MacBook, but the data on its hard drive can still be read without logging in.
Additionally, black hat hackers or criminals might take a guess and strike it lucky if your password is extremely weak. Not only that, but criminals can take things further by trying to access the hardware directly or brute-forcing their way in. Users should also be aware that law enforcement can sometimes get into a computer through court orders.
Whether it’s cybercriminals or law enforcement officers doing the hacking, accessing the data on your Mac is a tricky thing to do without a password. But it’s not impossible.
8. 9 out of 10 people know why security experts recommend regular updates
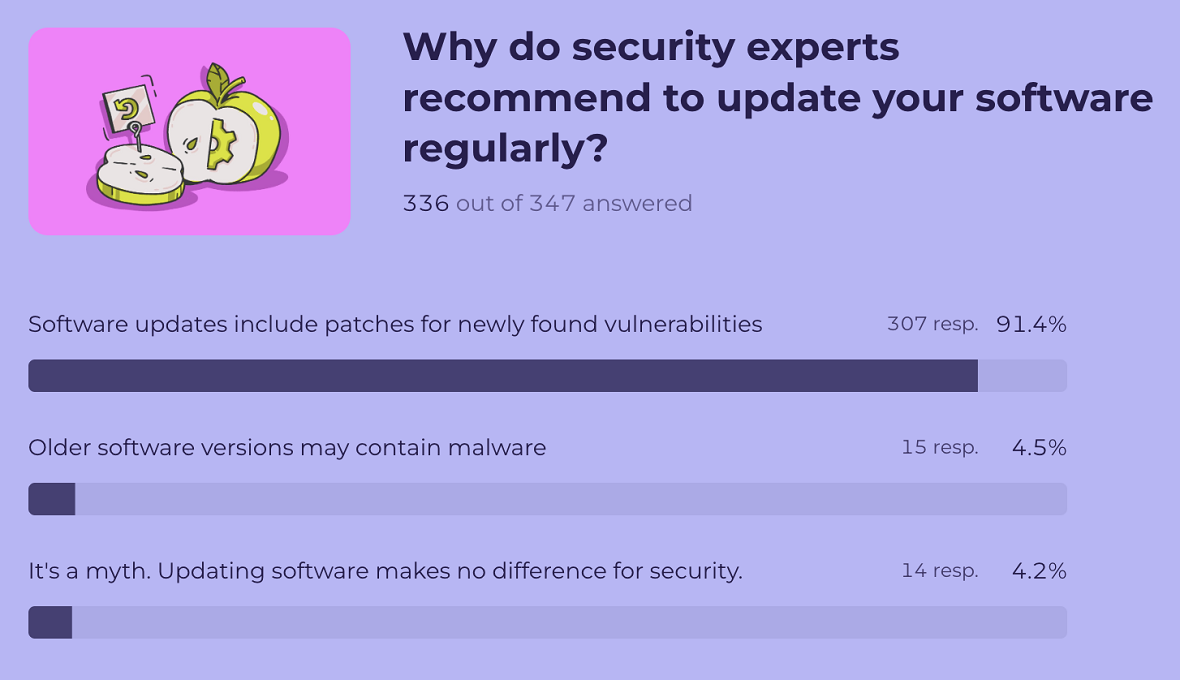
Besides strong passwords, MFA, and “never click on or download suspicious links and files,” there’s one piece of advice that cybersecurity experts bring up over and over again: Regularly update your software.
We wanted to know not only if users are getting the message but if they understand why this particular recommendation comes up time and time again, no matter what threat is being discussed.
Most of those who took our quiz (91.4%) got the answer correct. Regular updates are vital because they include patches for newfound vulnerabilities. Under 9% got the question wrong, answering that older software may contain malware or that the practice is a myth and software updates make no difference.
9. 12% believe Private Browsing or Incognito mode protects them from malware

Private Browsing, or Incognito mode, protects you from quite a lot, including someone accessing your browsing history, cookies, data, credentials, geolocation, and IP address.
However, these private browsing modes do not provide malware immunity.
We asked users whether they thought the statement “Using Private Browsing or Incognito mode protects you from downloading malware by accident” was true or false.
Most respondents (87.9%) correctly answered that the statement was False, while a notable 12.1% said the statement was True.
This highlights the importance of understanding that while private browsing modes offer some privacy benefits, they do not provide comprehensive security. It’s crucial to remain vigilant and employ additional security measures, such as reputable antivirus software and cautious browsing habits, to safeguard your device and personal information.
To learn more about safe browsing, read our Safari Private Browsing tutorial.
10. Bluesnarfing vs. bluebugging: Most people know there’s a difference
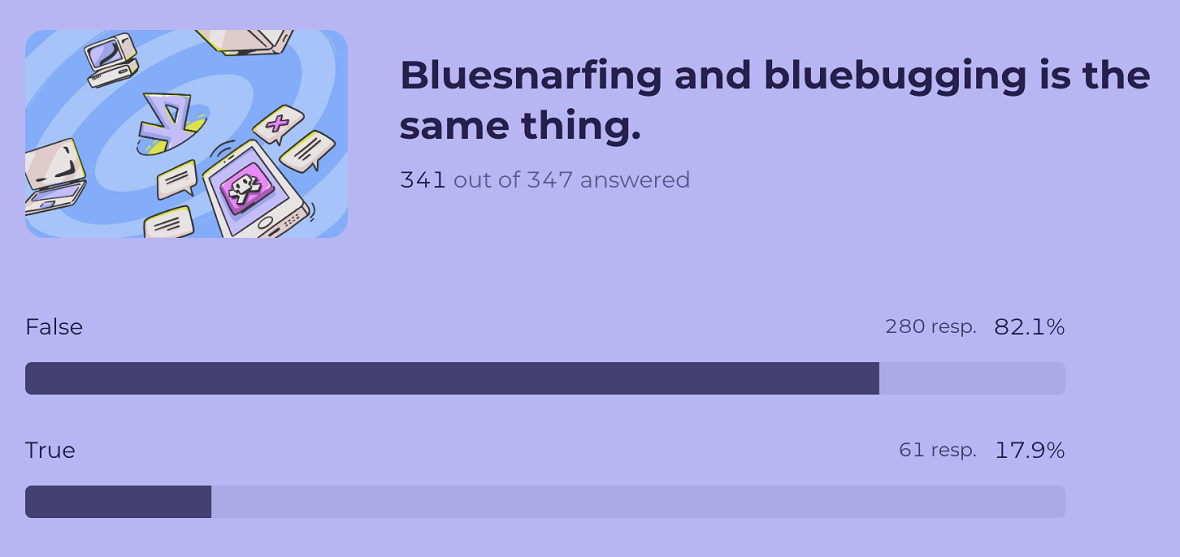
Our quiz also explored users’ understanding of Bluetooth vulnerabilities by including a statement about bluesnarfing and bluebugging. Here, 82.1% correctly identified the statement “Bluesnarfing and bluebugging are the same thing” as False. This indicates a relatively good grasp of the distinction between these Bluetooth attack methods.
For those who answered incorrectly (17.9%), here’s a bluesnarfing explainer that details the difference.
Final thoughts on the state of cybersecurity awareness
An entire “army” of researchers, advocates, organizations, and security experts is working hard every day to build cybersecurity awareness. Sometimes, the threats are easy for everyone to understand. Other times, they are extremely technical and complex, driving global cyberattack trends.
It’s true that building cybersecurity awareness isn’t easy for users, nor for experts. It can be frustrating to see that despite all their efforts, the threat landscape is not de-escalating at all. However, results from our cybersecurity quiz offer hope.
The majority of those who took our quiz (75.4%) scored between 7 and 9 (which is good!). While only 4.1% scored 10 out of 10 and 20.4% scored 0 to 6, the state of cybersecurity awareness in 2024 seems stronger than ever before. This is an undeniable win for cybersecurity — and a setback for attackers.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and iPhone are trademarks of Apple Inc.






