Although Apple’s iOS system is built for privacy and security, any device, system, and network can be hacked — even an iPhone. As alarming as that sounds, don’t worry. There are ways to tell if your phone is hacked. And even if it is, it’s not the end of the world.
In this guide, we’ll outline the signs of a hacked iPhone, how to check if your phone is hacked, and what to do about it.
Can an iPhone be hacked?
A question people often ask when their phone isn’t working optimally is, “Is it possible that my iPhone has been hacked?” The short answer is yes — it is possible. While iPhones are known for their strong security, it’s important to remember that no system is ever foolproof. Despite what Apple (and fans of Apple) may say, it is possible to hack an iPhone.
It’s true that iPhones are some of the most secure smartphones on the market, but that doesn’t make them completely immune to being hacked.
At the end of the day, an iPhone is just a computer connected to the internet, making it open to all sorts of attacks and exploits. That’s why it’s important to always keep your iOS and applications up to date, as new security patches are constantly being rolled out to circumvent online hackers.
One of the highest-profile incidents of iPhone hacking was the Pegasus affair in 2020. Pegasus is a piece of spyware developed by an Israeli company called NSO Group, although it’s generally acknowledged that the real perpetrator was most likely the Israeli government.
Noticed suspicious activity? Check your Mac, too
Another notable example of hacked iPhones was the intriguingly named Operation Triangulation in 2023. Again, an iMessage vulnerability was to blame for several thousand devices being infected with malware, leading to conversations being recorded and devices’ movements being tracked.
While these incidents are generally exceptions to the rule, you may nevertheless one day find yourself the victim of a hacked iPhone. This could be the result of a phishing scheme you fell for or a more sophisticated, zero-click attack brute-forcing its way past the iOS security measures and precautions. That’s why Apple has recently been urging users to update from older iOS versions.
Even iOS 18 security patches may no longer be enough to protect against emerging spyware threats in 2026. If your phone supports the latest updates, install the newest iOS version available to fix vulnerabilities and stay protected against emerging threats.
How can someone hack my iPhone?
While iPhones are secure, cybercriminals are constantly developing new methods to exploit vulnerabilities and gain access to your device. This can result in a hacked iPhone or, as some users describe it, a “tapped iPhone” where your data or communications are intercepted. Here are some common methods used by iPhone hackers.
Method 1: Phishing attacks
Phishing attacks are deceptive tactics where hackers try to trick you into clicking on malicious links or opening attachments that contain malware. These links or attachments might be disguised as emails or messages from legitimate sources like banks, social media platforms, or even friends.
Once you click on the link, your iPhone can be hacked through the link, or malware can be installed to steal your login credentials
Method 2: Stealers
Another way iPhone hackers can compromise your device is by installing stealer malware. These apps can disguise themselves as legitimate ones on the App Store, but once downloaded, they operate in the background to steal your data.
Method 3: Spyware
While less common, a more sophisticated method employed by iPhone hackers involves spyware. This type of malicious software infects your device and runs undetected, often without any visible signs. Both stealers and spyware targeting iPhone users are becoming more common every year.
Like stealer malware, spyware can access and exfiltrate a wide range of data, including:
- contacts
- messages (including SMS, iMessages, and even content from messaging apps)
- call history
- browsing data and history
- photos and videos
- keystrokes.
In some extreme cases, spyware can even activate your iPhone’s microphone or camera, allowing hackers to eavesdrop on conversations or capture your surroundings.
Method 4. Jailbreak
It used to be fashionable to jailbreak an iPhone, as it removed all of Apple’s restrictions on the device, allowing users to make their own customizations. However, that also opened the door to malware of all descriptions.
Users may chafe at Apple restricting what they can do on their devices, but removing the security safeguards that stop malware is just going to allow malware to come in. For this reason, jailbreaking an iPhone is not recommended.
How to tell if your iPhone is hacked: 7 common signs
The last thing you want to believe is that some stranger has hacked your iPhone and is spying on your texts, emails, and phone calls. An even worse thought is that they are using a keylogger to steal your passwords and access your private accounts.
Unfortunately, an iPhone can be hacked when it is used on insecure Wi-Fi networks or through man-in-the-middle attacks. Other ways hackers can get inside your iPhone are through social engineering or if you make a mistake as simple as downloading and installing an unsafe app.
If you’ve ever wondered, “Is my iPhone compromised?” use the signs below to check.
1. Battery life and performance drop
Is your iPhone not running well? If your phone is taking longer than usual for an app to open or close, or your battery is draining fast, it could indicate that your iPhone has been hacked. If the iPhone starts overheating, it could be a sign that a nefarious program is running in the background.
2. Contacts say you are spamming them
If your friends and colleagues complain that you are sending them messages or spam you know nothing about, your iPhone might be hacked. Check your record of sent messages.
3. Messages sent
If, upon checking your record of sent messages on your iPhone, you discover messages that you did not send, it may indicate that someone else has control over your device. The same may be true of outgoing calls.
4. Higher-than-normal device usage
If your data plan shows higher-than-normal usage and you haven’t been using your iPhone any more than usual, it’s possible that your phone has been hacked and is being used by an intruder.
5. Unrecognized apps and pop-ups claiming your iPhone was hacked
The top two examples of iPhone hacking signs are apps that you didn’t install and a sudden influx of intrusive browser pop-ups.
Unrecognized apps serve as the central HQ for malware to do its tasks, and the browser pop-ups often claim that your device has been hacked through fake security alerts designed to scare you.
Hackers often attempt to funnel their victims toward “antivirus software” to fix supposed security problems. This, of course, is a scam. Not only does the useless software not fix anything, but falling for the trick could compromise personal information such as your credit card number.
If you get fake security alerts, notice unknown apps, and see lots of browser pop-ups on your iPhone, it’s possible that your device has been hacked. Shut the phone down immediately and start to take preventive measures.
6. You’re getting 2FA codes you didn’t ask for
2FA codes are the second step when logging into an account, usually after a successful login via the username and password. If you’re receiving 2FA codes in your text messages or notifications that you didn’t request, it could be a sign your iPhone has been hacked or that someone already has some of your logins and is trying to access your account.
7. Unexpected microphone or camera activation indicators
Normally, your microphone and camera should only be recording while you’re actively using them. This is crucial for maintaining your privacy and security at all times. So if you start getting camera or microphone activation indicators out of nowhere, a malicious application or third-party might be trying to listen to you through your iPhone.
What can happen if my iPhone gets hacked?
Unfortunately, the consequences of an iPhone hack can range from inconvenient to downright dangerous. Let’s explore some of the potential risks that can arise if your iPhone is compromised:
- Data theft: Hackers can steal a wide range of personal information from your phone, including your contacts, messages, photos, videos, browsing history, and even financial data if it’s stored on your device. This information can be used for identity theft, fraud, or even blackmail.
- Financial loss: If hackers gain access to your financial accounts or credit card information, they can steal your money or make unauthorized purchases.
- Loss of privacy: A hacked iPhone can compromise your privacy in a big way. Hackers can steal your messages and photos, and even listen to your conversations through a compromised microphone. This can be a major invasion of privacy.
- Device damage: In some cases, malware can damage your iPhone’s software or even render it unusable.
- Spam and phishing attacks: Hackers can use your compromised device to send spam or phishing attacks to your contacts. This can damage your reputation and put your friends and family at risk.
Here’s how to check if your iPhone has been hacked
If you’re getting strong indications that your iPhone may be hacked, you need to know for sure. So, how can you tell? In this section, we will cover proactive ways to check to see if you need to remove a hacker from your iPhone.
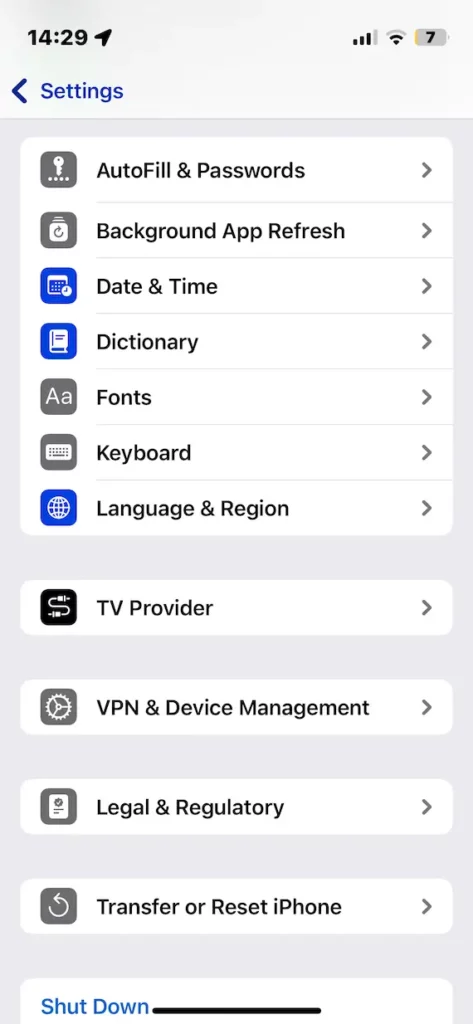
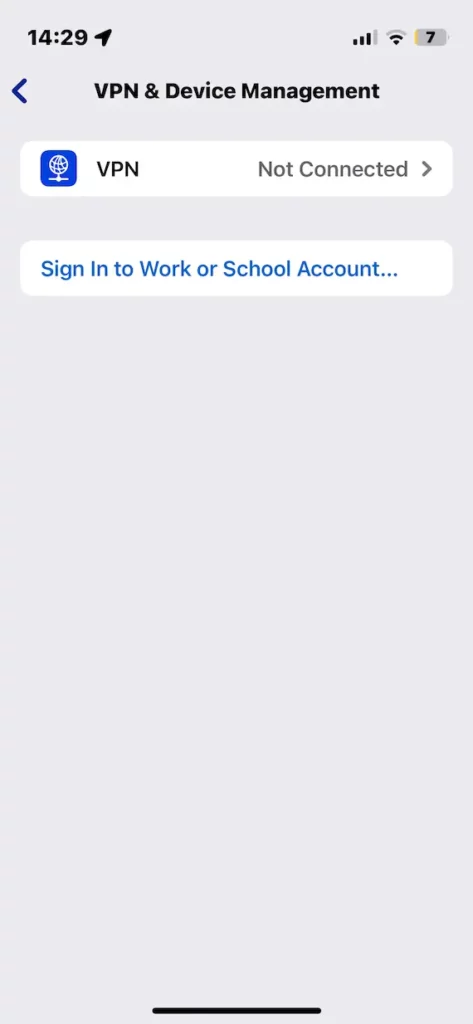
Review installed configuration profiles
The quickest way for a hacker to obtain higher user privileges on a compromised iPhone is to install a configuration profile. These installed malicious configuration profiles can be found under Settings > General > VPN & Device Management.
If there are any configuration profiles there that you don’t recognize, you could have a hacker problem.
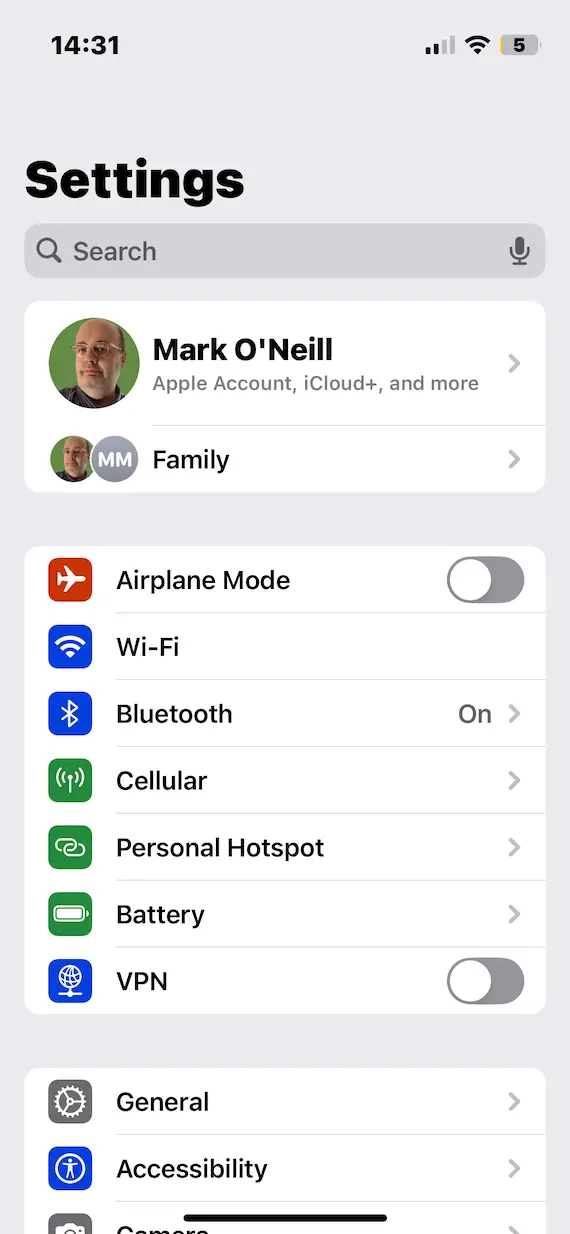
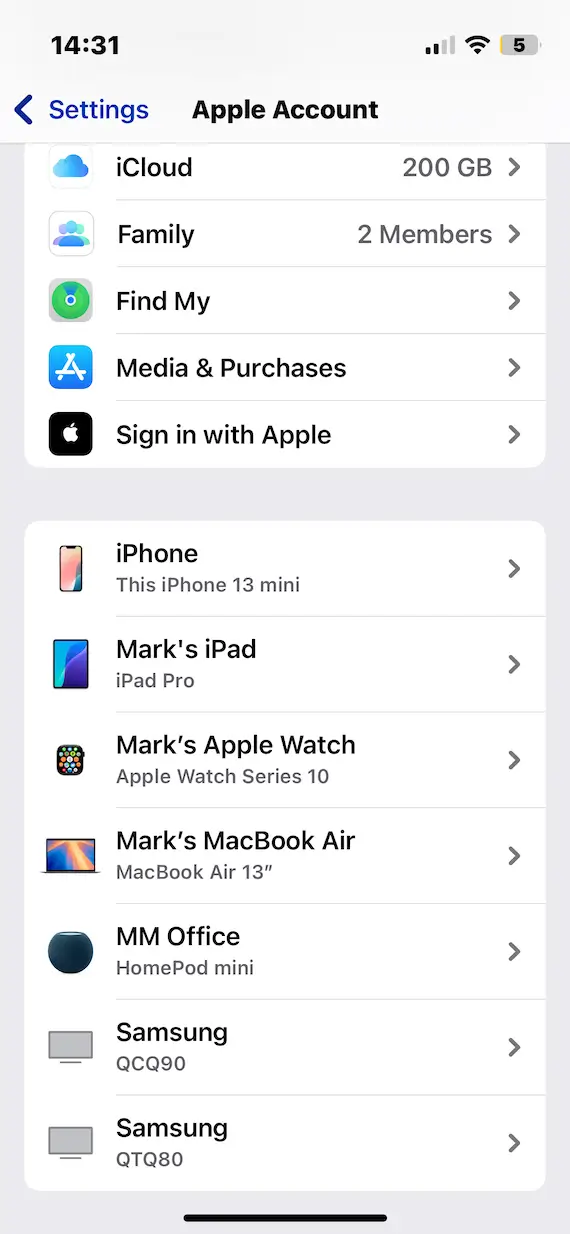
Look for unknown devices connected to your Apple ID
Your Apple ID lists all the connected devices on that account. This list should be reviewed regularly because any unknown devices listed there could be a sign of a big problem.
You can see this by going to your Apple ID in Settings and scrolling to the bottom of the screen.
Use Apple’s Safety Check to review and control shared information
You don’t have to manually check the access permissions of every app on your iPhone. Apple’s Safety Check puts all the relevant information in one place.
So, if you’re ever in doubt, quickly navigate to your iPhone’s Settings, select Privacy & Security, and tap Safety Check to find out which apps and contacts your phone is actively sharing information with.
Check your Apple ID for unfamiliar devices or access
Your Apple ID is the master key for all your Apple devices and services, so if you find a connected device that shouldn’t be there, it’s a clear sign your iPhone may have been hacked, or someone has managed to sneakily log into your Apple ID from elsewhere.

If you’re locked out of your Apple account due to hackers changing your password or Apple detecting suspicious activity, you’ll need to send a request to unlock your Apple ID. Normally, you’ll get a pop-up notification telling you that your account is locked, and you just need to tap Request Access. In some instances, however, you may need to contact customer support.
To minimize the risk of your Apple ID getting hacked, you might want to enable two-factor authentication (2FA). Simply go to Sign in & Security and turn on 2-factor authentication by following the instructions on the screen.
Check your installed apps and their permissions
You should check your installed apps on a regular basis to see if any unknown ones have appeared. But don’t stop there. Check their permissions, too.
Apps can often award themselves necessary permissions to carry out tasks that are not needed. Many iPhone users install the app but don’t bother to review what privileges have actually been granted.
Go to Settings > Privacy & Security and scroll down to the list that starts with Accessories. There, you’ll see different phone features and the apps that have access to them. Check each one and ask yourself if the app truly needs access to your microphone, camera, etc.
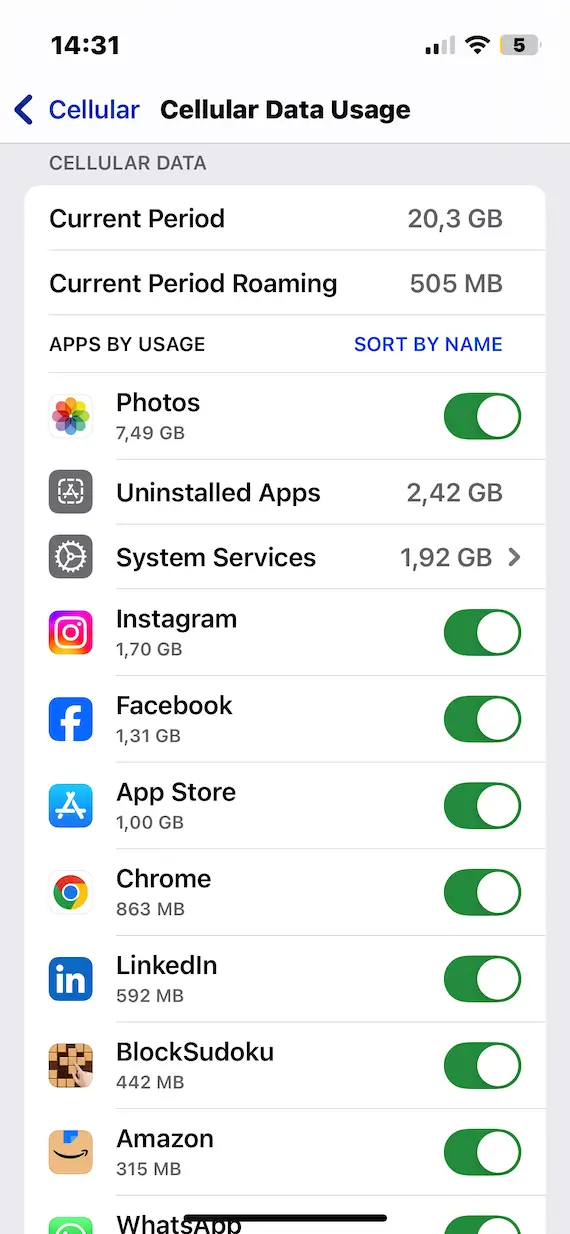
Check your data plan usage
When a hacker installs malware on your iPhone, that malware is going to be very high-maintenance, eating up your data plan usage when you’re not connected to Wi-Fi. Why? Because an internet connection is malware’s route for exfiltrating your stolen data.
If your data plan is rapidly being chewed up, you need to pinpoint where the issue is. Checking what apps are using your data plan will provide important clues.
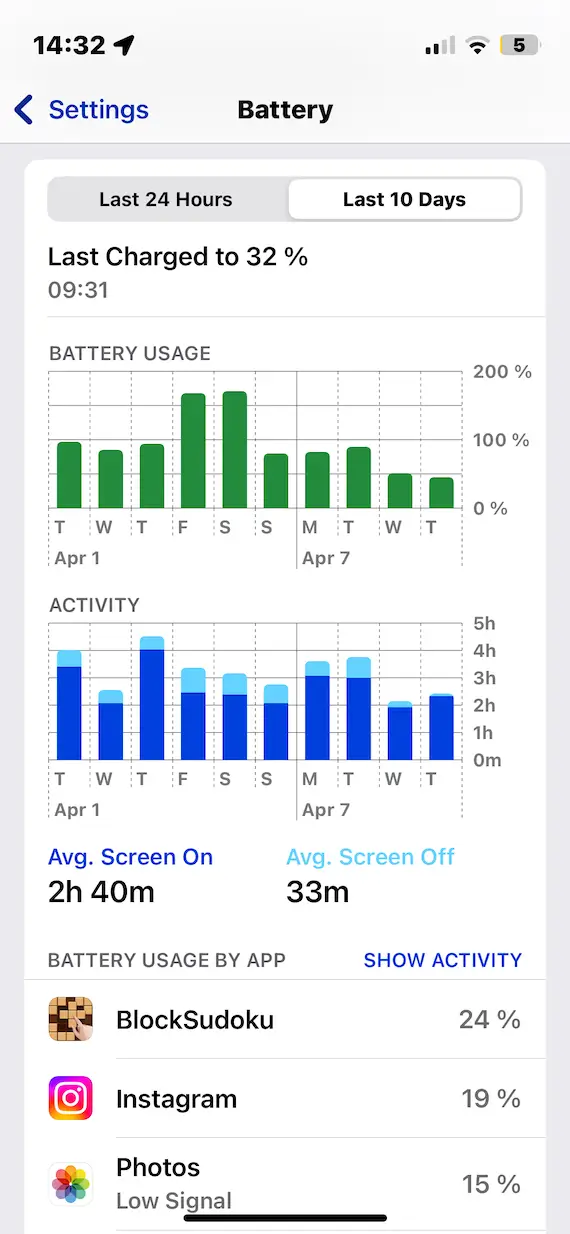
Look at your battery usage
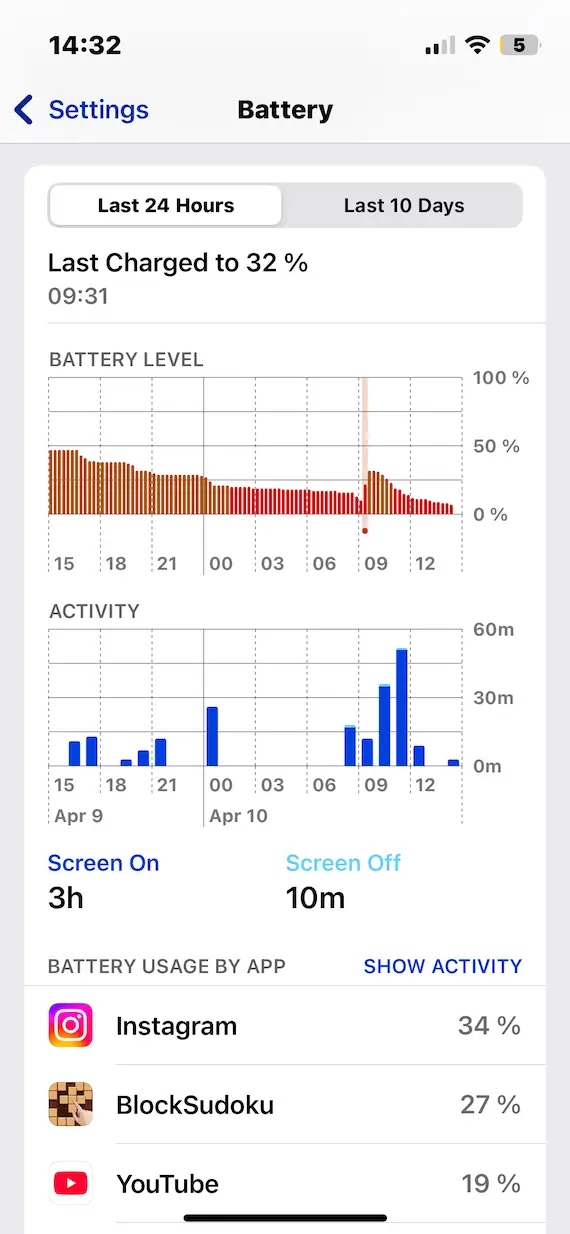
Speaking of high-maintenance malware, something else it needs a lot of is battery power. This means your battery is going to rapidly deplete and overheat.
If you see your battery rapidly draining and your phone is getting uncommonly warm, go to Settings > Battery and identify the perpetrator.
Find out if your iPhone is hacked with these codes
Using the Unstructured Supplementary Service Data (USSD) system, you can use special codes and receive information from the Global System for Mobile Communications (GSM). These codes can help you determine if your iPhone has been compromised.
- Redirection code. If you aren’t getting calls and texts from your contacts, they could be getting redirected to another location. You can check this by typing in: *#062# on your phone’s keypad and tapping the Send button. The resulting phone number is where all your calls and texts are being directed — or redirected.
- Redirected missed calls code. If someone has hacked your iPhone, they could be forwarding your missed or busy calls to another number. To check on this, dial *#61#. If this leads you to discover that your calls are being forwarded without your permission, you can turn that feature off by dialing ##61#.
- Calls being tracked code. If you fear that someone may be tracking your iPhone, you can quickly check by dialing *#21#. If you see a number you don’t recognize, change it by dialing *#21#.
- Reset forwarding settings code. The code ##002# is a universal reset for turning off forwarding and erasing any forwarded messages, calls, and data. It also resets all the forwarding settings on your iPhone.
- Complete reset code. If you suspect that your iPhone is hacked, you can perform a factory reset by using code *2767*3855#. This will restore all original settings and wipe out all the data and apps on your phone. Just be sure to back up your data first.
My iPhone is hacked: What do I do?
Although it’s not a great feeling to discover that your iPhone is hacked, don’t fret. Follow the tips below to fix the problem and move on.
1. Install and run antimalware
Install and run a trusted cleaning software to scan your phone for issues. If it finds any, you can automatically clean it up. You may have to factory reset your phone to undo all the damage.
2. Change all your passwords
If a hacker has gained access to your phone, you should immediately change all your passwords (from a computer, not from the infected device).
3. Delete suspicious apps
It may help to delete any unwanted/suspicious apps you find on your phone, especially if you did not install them. That said, skilled cybercriminals can hide malicious software where you won’t find it.
4. Clear Safari cache and history to remove malicious scripts after an iPhone hack
If you’ve visited a malicious website or clicked on a bad link, you may have infected your Safari browser with malicious scripts. While not always enough, clearing the browser’s cache and history can delete any remnants of a hacking attempt and is a useful step if you want to check if your iPhone is hacked.
Here’s how to delete the cache and history on iPhone:
- Open Settings and navigate to Apps > Safari.
- Tap Clear History and Website Data.
- You can also choose to clear the cache without removing your browsing history by navigating to Apps > Safari > Advanced > Website Data and selecting Remove All Website Data.
5. Enable Lockdown Mode on your iPhone
Lockdown Mode protects your iPhone from spyware and more sophisticated threats. However, enabling it limits the functionality of your iPhone due to the added security. This feature is directed at individuals working in highly sensitive professions and, in most cases, isn’t necessary for regular users.
Here’s how to turn on Lockdown Mode on iPhone:
- Open Settings. Select Privacy & Security.
- Tap Lockdown Mode, then confirm by tapping Turn on Lockdown Mode.
- Tap Turn On and Restart. You will be asked to enter your passcode.
6. Restart your iPhone regularly to remove memory-resident malware
Restarting your iPhone gets rid of malware that isn’t stored in persistent memory and can’t relaunch itself. The NSA recommends that you power down your iPhone at least once a week as a precaution, even if you haven’t noticed any signs of an iPhone hack.
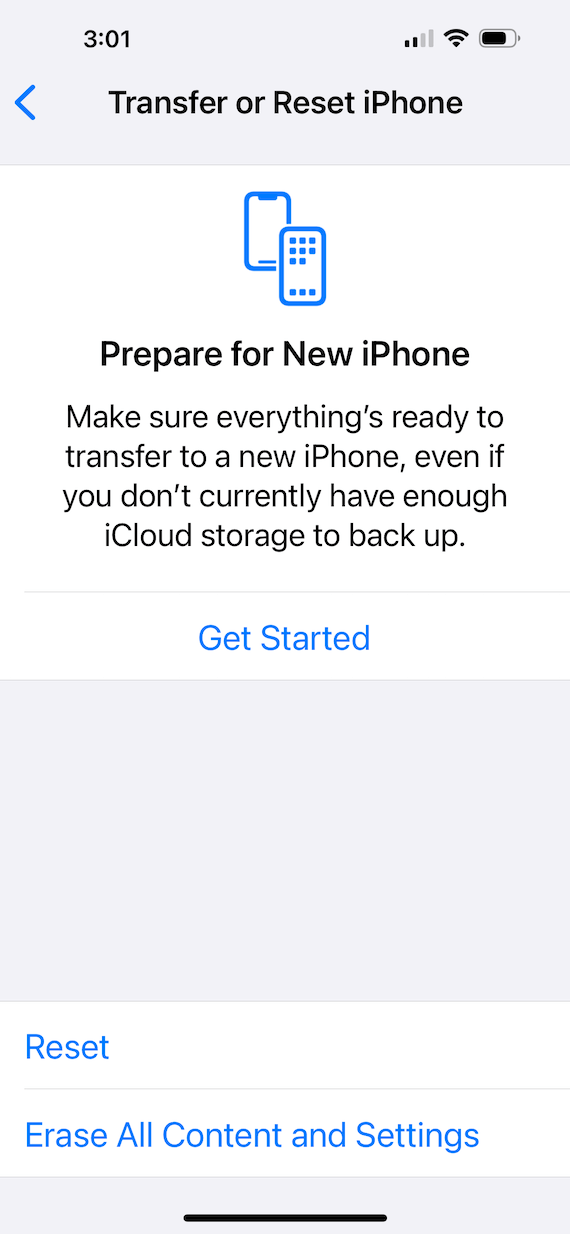
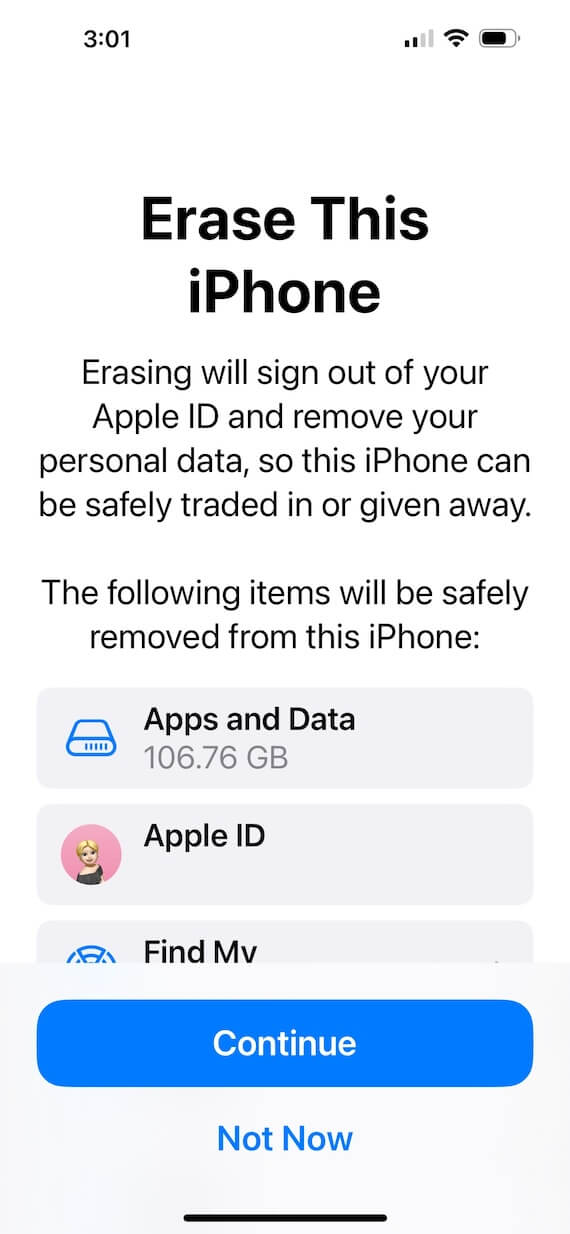
7. Factory reset your iPhone
To clean up everything at once, you can perform a full factory reset of your iPhone. To do this, navigate to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings. Then tap Continue to factory reset your phone. You can restore your iPhone from a recent backup to avoid losing any of your data.
8. Change your cybersecurity habits
Moving forward, you should bolster your cybersecurity habits to avoid any further intrusions. Here are some tips to help you stay safe:
- Never click links in suspicious emails.
- Do not install anything on your iPhone except verified apps through the App Store.
- Keep a close eye on all your passwords.
- Use long, strong passwords, and do not share them with others.
- Never use the same password on multiple websites.
- Never connect to an unsecured Wi-Fi network (like a coffee shop or hotel) without a VPN to keep intruders out.
FAQ: Common questions about iPhone hacking and security
You should never leave your iPhone unattended, especially if it’s unlocked or doesn’t have a passcode. Someone could install spyware or change access and share permissions while you’re not looking.
You’ll get a notification when your Apple ID is signed in to a different device. However, be on the lookout for fake notifications, messages, and emails claiming that your iPhone was hacked or that someone logged into your Apple ID.
If you’re experiencing any security issues with your iPhone, you should contact Apple Support and explain your situation. They should be able to help you secure your iPhone and mitigate future attacks.
Face ID uses highly advanced algorithms to identify your face, including making sure that it’s not a picture and that you’re not asleep or have your eyes closed. This ensures that no one but you can unlock your iPhone.
iPhone users must be diligent when it comes to keeping their devices safe. Monitor your phone for any strange activity or performance issues. Overall, if you notice anything odd, it’s best to immediately perform a factory reset on your phone, change your passwords, and turn on encryption for an added layer of security.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iPhone and iOS are trademarks of Apple Inc.







