Businesses and individuals alike face a lot of threats online, and one of the greatest threats is a menace known as ransomware, a very serious form of malware that locks down and encrypts the files on a computer and network.
Read on to find out what ransomware is, how it works, and how to recover from it.
What is ransomware?
As the name implies, attackers who use ransomware demand payment (usually in the form of cryptocurrency) in exchange for a decryption key once the malware has encrypted your files. The threat is that if the ransom is not paid, the files will never be decrypted and, therefore, lost forever.
If payment isn’t made by the given deadline, a hacker may increase the ransom. In some cases, they may go so far as to delete everything on the target system in retaliation.
Why is ransomware so harmful?
The FBI defines ransomware as harmful, dangerous malware. The following are just a few of its very serious real-world effects:
- Businesses can be paralyzed: Without access to essential files and business functions, a targeted company can be rendered useless. This happened during the NHS ransomware attack in June 2024 — emergency services, medical operations, and hospital care were severely disrupted, and lives were put at risk.
- Individuals and businesses alike can face financial losses: If individuals or businesses lose access to files, it can lead to financial losses — not to mention the cost of paying the ransom. People can lose their jobs as a result, causing them to face potential hardships.
- Files can remain damaged: Even if a decryption key is provided, it may not work properly. Files could damaged, and if a backup hasn’t been made, this could have serious ramifications.
- Confidential data could be stolen: During the above-mentioned 2024 NHS ransom attack, sensitive patient data was stolen. In the case of a business, proprietary product data and employee information can be stolen and decrypted by the hacker.
Should you pay the ransom?
Although your first inclination might be to pay the ransom, law enforcement generally advises against this.
For a start, you have no guarantee that the hacker will honor the agreement and provide you with a decryption key. They could just take the money and disappear. Even worse, they could ask for a second payment.
Also, getting the ransom money will encourage the hacker to come back in the future to try again. It will also embolden them to target others, as you have just confirmed that the tactic works.
How ransomware works
Once ransomware manages to penetrate your Mac, it starts searching your files. Files on the system are then encrypted with an encryption standard that is extremely difficult (or practically impossible) to break, even by IT department standards.
It may be possible for law enforcement agencies, with their more advanced tech tools, to decrypt the files, but this takes time. And usually, time is not on your side, as the hacker will likely impose a time limit on payment.
How ransomware gets installed on your device
So, how does ransomware get installed on a target network? It happens the same way all malware tends to breach computers and networks. The following are just a few examples.
Malware-infected links
The most common way that ransomware gets onto a target computer is via a malicious link. A hacker may impersonate a company’s employee, a coworker, or a client.
The link may be in an email, an SMS message, or a chat message. When it is clicked, it will lead to a malware-infected website, or it will initiate the download of a malicious file, which will start installing ransomware on the victim’s device.
Installing apps or software from unknown developers
In some cases, ransomware may be secretly bundled with legitimate software. The malware installs itself silently in the background when you install the legitimate software, or it may appear as a fake security patch or app upgrade.
Infected USB drives
One of the reasons — perhaps the main reason — that company IT departments often forbid the use of USB drives on business computers is that they can contain malware.
Someone posing as a potential client may hand over the USB drive, claiming it has essential files on it for the company to look at. Before you know it, ransomware is plaguing the system.
Misconfigured networks
A ransomware attacker may also scan a company network to find security vulnerabilities to take advantage of. Once a vulnerability is found, they can remotely send the ransomware through a misconfigured firewall or a network without a password.
Who is most vulnerable to ransomware?
Any individual or company is theoretically vulnerable to ransomware attacks. However, there are some categories that hackers seem to target more than others:
- Hospitals and other healthcare providers: Any medical facility is likely to pay up fast since doctors, nurses, and surgeons rely heavily on patient files in the affected system. This makes them a prime target for ransomware.
- Small and medium-sized businesses: Usually, small- and medium-sized businesses don’t have the budget for advanced security measures on their networks. This makes them more susceptible to malware, including ransomware.
- Government officials: Government officials, especially those involved in local government, don’t have the budget for advanced security features. With a great deal to lose if sensitive information were to be lost (or made public), a ransomware attack could be devastating. Plus, many small, local governments also use outdated versions of operating systems and software, meaning that there may be unpatched security vulnerabilities.
- Schools and universities: Educational institutions have access to a great deal of sensitive information, such as students’ personal data, as well as financial information.
Types of ransomware and examples of attacks
Although the effects of any malware attack can be disastrous, in the case of Mac users, ransomware usually only targets specific folders and files. It will rarely lock down an entire Apple ecosystem. This means that the damage may be mitigated if the device can be restored from a recent backup. Nevertheless, users should educate themselves on the common types of ransomware.
Different types of ransomware
Most ransomware falls into three categories:
- Crypto ransomware: This is the most common and involves encrypting your files and demanding a cryptocurrency ransom.
- Locker ransomware: This type locks down an entire computer or network, making it totally impossible to use.
- Doxware: Instead of encrypting your files, the attacker steals them and threatens to release them publicly if the ransom isn’t paid.
Notable examples of ransomware attacks
We previously mentioned the attacks on Britain’s NHS, but there have been other notable ransomware examples:
- WannaCry (2017): WannaCry infected more than 200,000 computers in 150+ countries, costing $4 billion in damage.
- NotPetya (2017): This one targeted Ukrainian businesses but soon went global, causing $10 billion in damages. It’s widely considered to be the worst ransomware attack in history.
- British Library (2023): In 2023, the British Library in London received a ransom note demanding 20 Bitcoins (at that time, worth $500,000). They refused to pay, which led to data being leaked. The resulting damage cost almost $10 million to fix.
How to recover from a ransomware infection
If you have become the victim of a ransomware attack, the first step is to stay calm. Then, do the following.
Disconnect from the internet
First, disconnect from the internet. Ransomware requires an internet connection to communicate with its home base. By disconnecting from Wi-Fi, you’re depriving it of the fuel it needs to run.
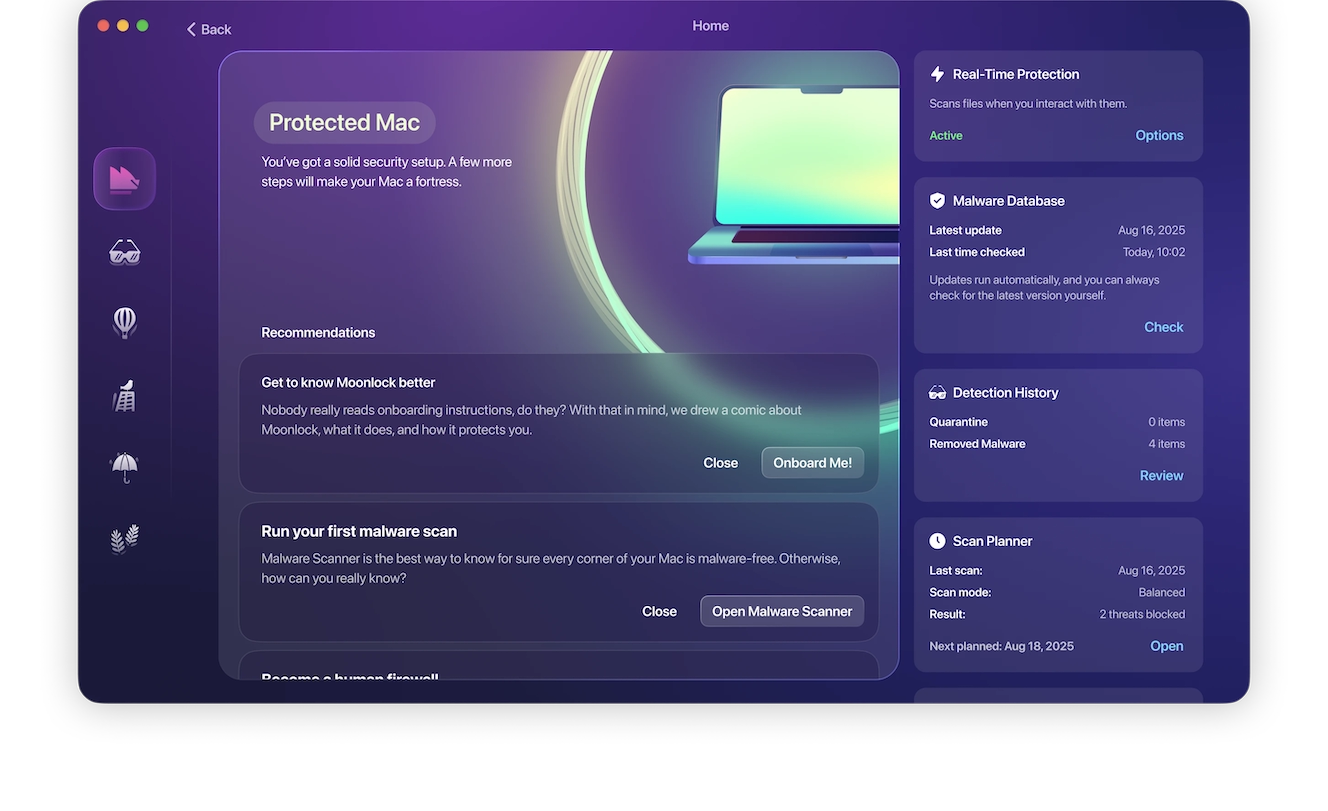
Run a scan with Moonlock

Next, you’ll need to locate and remove the ransomware from your device. While you can try to trace back your steps and do it manually, you might miss a file or two and continue endangering your files as soon as you reconnect to the internet.
The best way to completely remove ransomware from your Mac is to sign up for a free trial of Moonlock and run a comprehensive malware scan to identify the ransomware. Here’s how you do it:
- Open Moonlock, then click on the Malware Scanner tab from the left-hand sidebar (it’s the sunglasses icon).
- From the drop-down menu, choose between a Quick, Balanced, and Deep scan. We recommend you go for a Deep scan, especially the first time, to give Moonlock the best chance at finding all threats that might be lurking on your Mac.
- Finally, click Scan.
The process might take a few minutes, but by the end of it, Moonlock would have scoured through all corners of your Mac, inspecting files such as archives, disk images (DMG), and packages (PKG).
Once it finds the ransomware, it’ll immediately lock it up in Quarantine, isolating it from the rest of your device and stopping it from snooping through your files. You can then safely and securely allow Moonlock to remove the ransomware from your Mac.

Consider wiping and resetting your MacBook
Keeping regular backups through a tool such as Time Machine can be your best line of defense if a system gets infected. If no backup is available, or in the unlikely event that a full system lockdown occurs, utilize macOS Recovery Mode for a system restore or a factory reset.
How to avoid and prevent ransomware attacks
To avoid becoming a victim of ransomware, follow these tips.
Never click on links from unknown senders
Infected links are the favored tactic of hackers everywhere. They can be sent out at high volumes, they require very little effort to send, and there will always be victims willing to click them.
Never click on a link sent to you by an unknown person or someone you don’t entirely trust, whether it’s by email, through SMS, in a document, or in a chat message. Even if the person claims to be someone you know, double-check to make sure it really is them. Social engineering is an insidiously effective strategy.
Install Moonlock and run regular scans
You need a solution that stops ransomware from infecting your Mac in the first place, like Moonlock with its many built-in security features. In addition to comprehensive malware scans (which you can schedule to run on a regular basis using Scan Planner), it also has capabilities like real-time protection, which monitors your Mac around the clock, looking for anything suspicious or malicious.
With ransomware in particular, it’s important that you act as soon as you suspect that your Mac has been infected. Your highest chance of successfully removing it is before it starts encrypting your personal files. Once it starts, you risk losing access to some of your files for good. Moonlock can only remove the ransomware itself, but it can’t decrypt any files that have already been encrypted.
Avoid installing software from outside of the App Store
Since ransomware can be hidden inside other software, it’s not a good idea to buy software from unknown developers. You can reduce this threat by confining your software choices to apps and software available inside the Apple Store.
Apple thoroughly scans and vets all apps in their store, so the chance of ransomware is extremely small. However, there may be times when you’re forced to venture outside of the App Store to buy something from a third-party developer. Stick to trusted names with high profiles and good reputations.
Install all system and app updates right away
Ransomware will, without hesitation, take full advantage of security vulnerabilities in operating systems and software, so keep your macOS and apps updated at all times.
When you see that there is an update waiting, install it as soon as possible. It’s easy to ignore an update with the intention of installing it later, but later may be too late. Do it now.
Make sure your network is configured correctly
To prevent malware from entering your network, check your network thoroughly to make sure it’s configured properly. At the very least, this means password-protecting it.
You should also consider changing your network’s name to something nonspecific so the hacker may not be sure which network belongs to you. Then, go through the settings and ensure all security features are enabled.
Ransomware is an insidious threat to all businesses and institutions, and the problem is only getting worse. But, by learning some security measures and IT practices, the threat can be mitigated — and even removed entirely.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac, macOS, Final Cut Pro, and the Mac App Store are trademarks of Apple Inc.