A backdoor is a type of malware that establishes a presence in a system and allows hackers to connect with the infected device. You can think of it as someone adding an extra door to enter your house. The problem is that the door was never meant to be there. This entrance is created without your knowledge, and hackers and cybercriminals can use it to enter your home.
So, what are the different types of backdoors? And what can you do to stay safe from them?
The different types of backdoor attacks
One type of backdoor is found at the software level. This type of backdoor malware usually compromises a device or a network via phishing, downloads from malicious sites, fake websites (backdoor websites), or other common means of malware distribution.
The other type of backdoor is found at the hardware level. Hardware-level backdoors are deliberately integrated into the hardware of a device by a tech manufacturer or a company that has access to the supply chain or manufacturing operations. These ones are very difficult for normal end users to detect or remove.
How much damage can a backdoor attack cause?
Backdoor malware is the most flexible variety of malware. Once a backdoor has infected a device, it can be used to load other types of malware, such as ransomware, spyware, or stealers. They are created to persist in systems. This flexibility, along with its capability of persistence, makes backdoors very damaging.
Backdoors can lead to all kinds of damage. Thanks to backdoors, cybercriminals can spy on individuals and organizations, modify systems, and change configurations. They can access and steal files, load ransomware, encrypt and exfiltrate data by remote commands, and do much more.
Backdoors are usually associated with high-level attacks, such as nation-state threats and spyware. And while backdoors are not usually the preferred type of malware used by cybercriminals who target normal Apple end-users, there has been an increase in backdoor integration into macOS threat campaigns, especially with stealers.
Common types of backdoor attacks
It is vital that you keep informed on how to prevent backdoors and other malware attacks. So, let’s look at the different types of backdoor attacks to understand how this malware works:
- Malware backdoors: These are developed by black hat hackers for cybercriminal use. They are distributed to victims as malware and malicious software.
- Trojans: Backdoor trojans may seem legit at first, but they are ultimately malicious. These are generally distributed by cyber criminals through seemingly authentic sources. For example, bad actors may create fake websites that offer downloads of real software that they impersonate.
- Remote access trojans (RATs): A RAT is a specific type of trojan that enables an attacker to control a victim’s device remotely.
- Web shells: Scripts uploaded to a web server can provide attackers with remote access and control over the server.
- Rootkits: Software can be designed to gain unauthorized root or administrative access to a system while hiding its presence.
- Exploiting default credentials: Attackers may use default usernames and passwords to gain access to systems that have not been properly secured.
- Supply chain attacks: This type of attack involves compromising software or hardware during the manufacturing or distribution process to introduce backdoors.
- Insider threats: Resentful, disgruntled, or ill-willed employees or contractors can intentionally create backdoors for malicious purposes.
- Misconfigured systems: Poorly configured systems can allow criminals to load backdoors. This attack leverages security oversights.
- Firmware vulnerabilities: These exploit weaknesses in device firmware to install backdoors that can be difficult to detect.
How to get rid of a backdoor on your Mac

Backdoors are the type of threat that you want to get rid of fully. Any traces left behind could enable the hackers to reinstate themselves in the system, forcing you to start the cleanup process all over again. Not to mention, you probably don’t know where exactly the backdoor malware is hiding, if it has persisted, or if you’ve accidentally included it in one of your regular backups.
The best way to remove a backdoor from your Mac is to use Moonlock, a reliable and easy-to-use antivirus that’s capable of identifying and removing a wide variety of threats. Sign up for a free trial of Moonlock to access its full security capabilities.
Once you’ve installed and set up Moonlock on your Mac, here’s what you need to do:
- Open Moonlock, then click on Malware Scanner from the left-hand sidebar.
- Since this is your first scan, you’ll need to configure it for optimal results. From the drop-down menu, click Configure.
- In the new window, under “Scan type,” choose between Quick, Balanced, and Deep scan. The Speed, Depth, and Purpose of each type is listed right below it. We recommend that you select a Deep scan and enable all optional files: archives, disk images (DMG), and packages (PGK).
- Once done, exit the settings page. Your preferences will be kept for all future scans.
- Back in the Malware Scanner tab, click Scan.
Moonlock will search through all the files and system configurations on your Mac, looking for the backdoor malware.

Once Moonlock finds the virus, it will immediately isolate it in Quarantime, stopping it from interacting with your system and preventing the hackers from continuing to remotely access your device. Then, with a single click, Moonlock will completely remove the backdoor virus from your Mac, leaving no trace behind.
Real-life examples of backdoor attacks
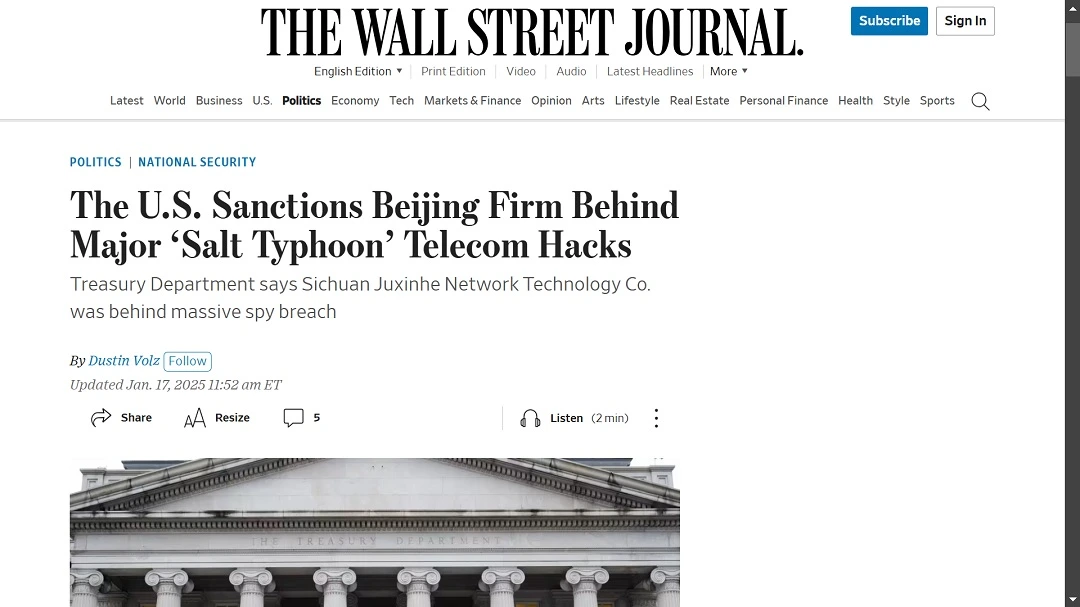
Backdoor malware is not theoretical. Backdoors have been used extensively to launch cyberattacks, and they are very much still at play. Let’s look at some real-life examples.
The Dridex RAT
2023 saw increases in remote access trojans targeting macOS environments. A new variant of the Dridex, a banking malware that used to exclusively target Windows users, pivoted to target macOS.
The trend of malware being updated to be cross-platform, infecting users no matter what OS they are running, is on the rise. The Dridex RAT was coded to steal as many credentials as possible.
AMOS and other Mac stealers
The most notable cybercriminal trend targeting Apple users today is undoubtedly the use of stealers, particularly AMOS, the most popular on the dark web.
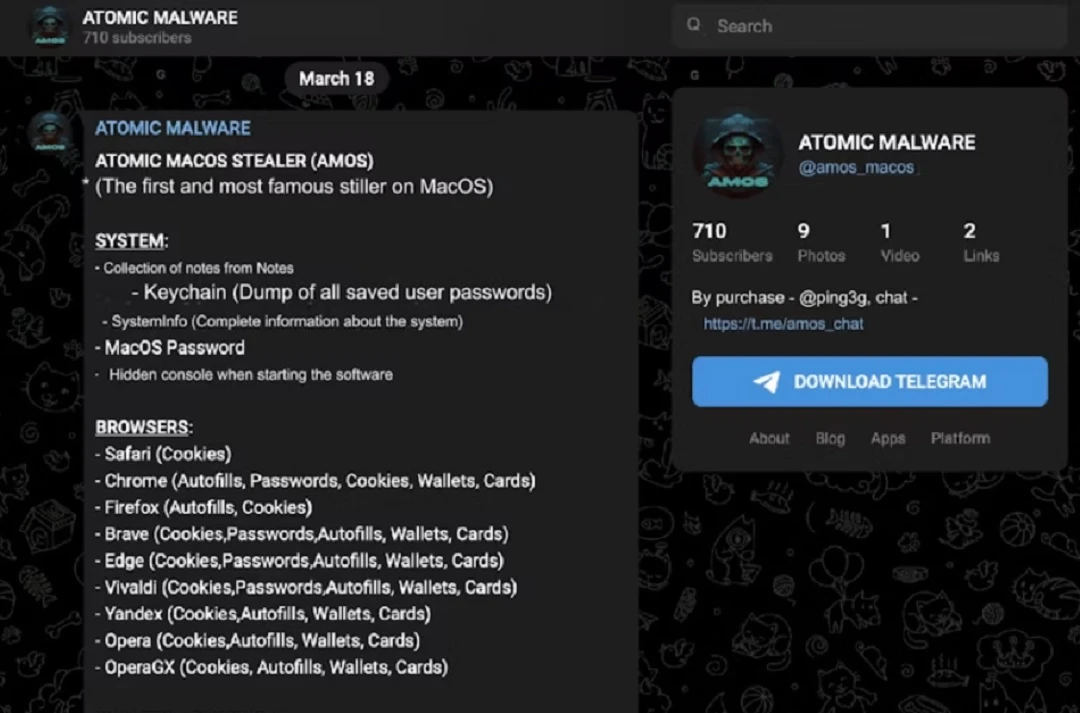
Stealers often include backdoor malware. They present themselves to victims as legitimate downloads like Slack, Zoom, or other impersonated and abused brands. These impersonations make the malware a trojan.
To learn more on how to remove trojans from your Mac, read our trojan removal report.
Web Shells
A recent malware campaign is a perfect example of how cybercriminals are using illicit scripts to bypass Apple security. Mac computers come with integrated cybersecurity that can detect most known malware in real life, but cybercriminals are convincing macOS users to copy, paste, and run malicious scripts.
Moonlock reported on a campaign that did exactly this. In January 2025, Apple developers who used Homebrew were targeted with illegal scripts offered during fake download processes.
Another piece of malware known as Spectral Blur also uses web shells. You can read Moonlock’s full analysis on Spectral Blur to learn the techniques that are used in the wild.
Other types of backdoors
Other real-life backdoor examples include:
- Rootkits: The Sony BMG rootkit incident involved the installation of a rootkit on users’ computers through music CDs. This created vulnerabilities that attackers could exploit.
- Supply chain attacks: The SolarWinds attack involved attackers inserting a backdoor into the company’s software updates, which were then distributed to thousands of customers, including government agencies
- Misconfigured systems: In 2019, Amazon Web Services (AWS) experienced a significant breach due to misconfigured S3 buckets, which allowed unauthorized access to sensitive data, effectively acting as a backdoor.
- Firmware vulnerabilities: The VPNFilter malware targeted routers and network devices, exploiting firmware vulnerabilities to install backdoors that allowed attackers to intercept traffic and launch attacks.
How does a backdoor get onto devices and take control?
As mentioned, the infection vector for backdoors is similar to other types of malware. The most popular include:
- Exploitation of known vulnerabilities: These include weaknesses in systems, software, updates, services, apps, APIs, or other resources that criminals use as an entry point.
- Exploitation of zero-day vulnerabilities: Cybercriminals may find unknown weaknesses in updates, software, or new apps before security teams do and can use these as entry points. These are commonly patched via over-the-air security updates rolled out frequently by vendors. Zero-day vulnerabilities are very common today, especially after the release of a new operating system (OS) version.
- Phishing: This category refers to the classic con of tricking humans — via email, SMS, social media, and phone calls — into downloading and installing malware, clicking on links, or giving away credentials and sensitive data.
- In-factory backdoors: These backdoors exist at the hardware level. They are integrated intentionally by manufacturers or those who have access to the manufacturing supply chain. These backdoors are stealthy, remote access backdoors, and as malware, they are very hard to remove. These hidden backdoor accesses are factory-reset tolerant.
- Authorities: Legal court warrants, governments, or law enforcement agencies can, in some cases, request the deployment of backdoors. These court-authorized backdoors are usually deployed to mitigate threats or advance criminal investigations. Most cloud services, messaging apps, and social media services have agreed-upon backdoors with different governments.
How do hackers exploit backdoors to launch attacks?
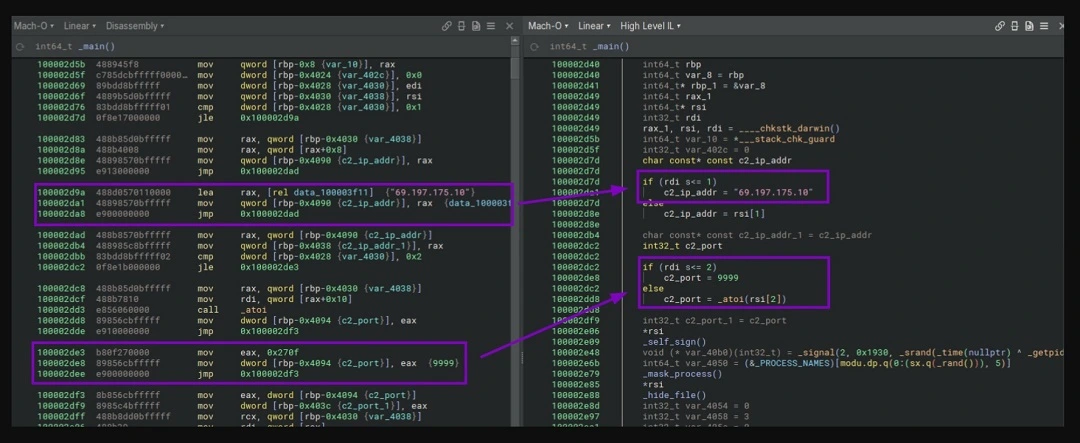
Once a backdoor breaches a system, it reads the location to which it will write and then copies itself to that location. The processes that follow, used to gain full control of an infected device, vary from attack to attack. However, the backdoor usually then creates a channel of communication with an attacker-controlled C2 server.
The communication channel will be used by the attacker to send commands to the backdoor and to receive data from the infected device. Commands sent to backdoors also vary. They often include loading additional malware, looking for and exfiltrating a particular resource or file, making system changes, and even self-deleting for increased stealth.
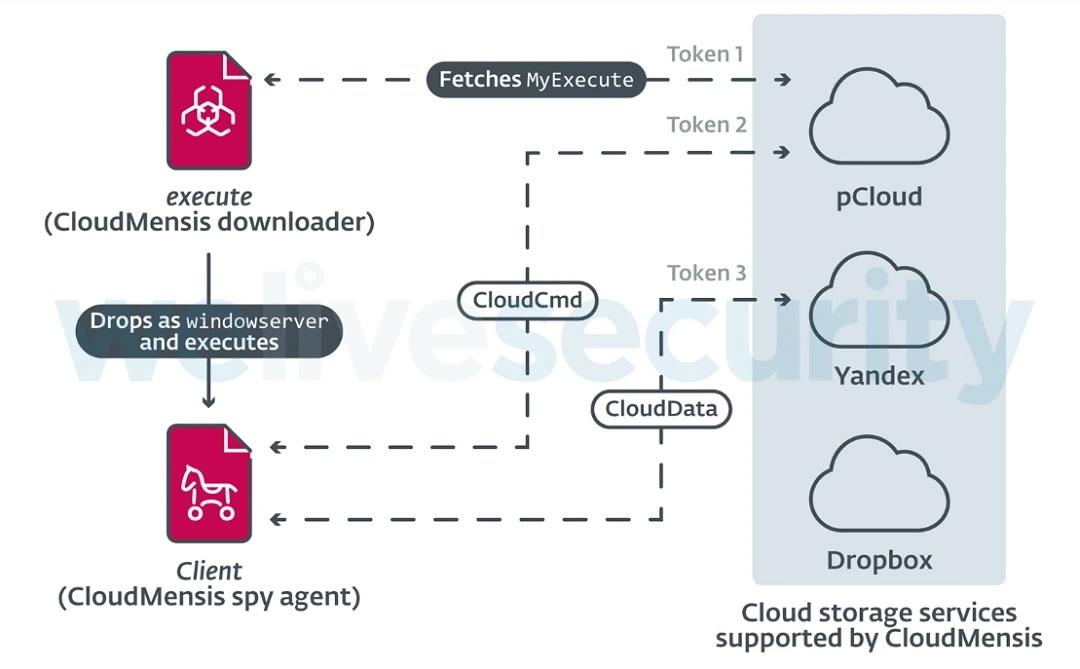
Additionally, a backdoor will also code its way into the most hidden elements and core of a system. It does this to make sure it will persist on reboots or wipes done on the victims’ side to mitigate the threat.
The risks and consequences of backdoor attacks
Because backdoors can be used to launch any type of cyberattack, the risks and consequences are widespread:
- Unauthorized access: Backdoors allow attackers to bypass normal authentication processes, granting them unrestricted access to systems and networks. This can lead to further exploitation of sensitive data and resources.
- Data breaches: Once inside a system, attackers can exfiltrate sensitive information, including personal data, financial records, and intellectual property. This can result in significant financial losses and reputational damage for organizations.
- Malware: Attackers can use backdoors to install additional malware, such as ransomware or spyware, which can further compromise the integrity of the system and lead to more extensive damage.
- System manipulation: With backdoor access, attackers can manipulate system settings, alter configurations, or even disable security measures, making it easier for them to maintain control over the compromised system.
- Disruption: Backdoors can be used to launch denial-of-service (DoS) attacks, disrupting services and causing downtime for businesses. This can lead to loss of revenue and customer trust.
- Compliance violations: Organizations that experience backdoor attacks may face legal and regulatory consequences, especially if sensitive data is compromised. This can result in fines, lawsuits, and increased scrutiny from regulatory bodies.
List of potential backdoor impacts
Backdoor attacks pose significant risks to organizations and individuals alike. The potential impacts of these attacks can be far-reaching, affecting not only the immediate victims but also their customers, partners, and the broader community.
Understanding the risks of backdoor attacks is crucial for developing effective cybersecurity strategies. They can include:
- Financial loss: Direct costs associated with remediation, legal fees, and potential fines
- Reputational damage: Loss of customer trust and brand reputation due to data breaches or service disruptions
- Operational disruption: Downtime and loss of productivity as systems are compromised or taken offline for investigation
- Legal consequences: Potential lawsuits and regulatory penalties for failing to protect sensitive data
- Intellectual property theft: Loss of proprietary information that can be exploited by competitors
- Increased security costs: Need for enhanced security measures and ongoing monitoring to prevent future attacks
Signs of backdoor attacks and how to detect one
While backdoors are by nature evasive, hard to detect, persistent, and stealthy, they can be detected by some of the signs that they are at work.
Signs of backdoor attacks
Here are some clear telltale signs that a backdoor has infected your system:
- Traffic network: Backdoors are designed for web traffic. This means that a computer infected with a backdoor will be sending out data and receiving data from the attacker-controlled server. You can monitor your traffic and sources of traffic (services and IPs) to check for anything suspicious.
- Slow connection: Given what we explained in the point above, backdoors use more bandwidth than a victim’s system uses on average. If your connection is slow, and your computer is struggling to process things it used to do in an instant, it is a clear sign that something is off. A backdoor could be to blame.
- Modified, hidden, or missing elements: Backdoors can modify configurations, hide files and folders, make copies, or delete elements of your system. Keep an eye on anything that looks suspicious on your computer, as it may be a backdoor in action.
- Unusual account activity: If you notice strange login attempts or unauthorized access to accounts, it could indicate that a backdoor is allowing attackers to control your system remotely. Monitor your account activity for any signs of unauthorized access or change.
- Unexpected software installations: If you find software on your system that you did not install or authorize, it could be a sign of a backdoor. Regularly review installed applications and remove anything suspicious.
- Frequent crashes or errors: If your system experiences frequent crashes, freezes, or error messages, it may be a sign of malware interference, including backdoors. These issues can arise from a backdoor’s attempts to manipulate system processes or resources.
- Alerts: Has your anti-malware, system, or firewall been acting up and popping up with security notifications? Never underestimate or ignore security notifications, as these are signs that something is not right.
How to prevent backdoors from infecting your system
Let’s dive straight into three tips to mitigate, shut down, and remove backdoors from your system and devices.
1. Use Moonlock
Moonlock does more than get rid of backdoors for you. It protects your Mac from getting infected in the first place.
With built-in real-time protection, Moonlock will continuously monitor device activity, checking new files and downloads for anything malicious. If it catches someone trying to load a backdoor on your system, it’ll immediately stop it and alert you to the threat.
To enable real-time protection, install and set up Moonlock on your Mac. Then, simply click on Explore from Moonlock’s home page. This will take you to all the security features and capabilities that Moonlock offers.
From the right sidebar, under real-time protection, click Options. In the new window, under Continuous monitoring, tick the box labeled Turn on real-time protection.
2. Keep your software updated
Regularly updating your operating system and all installed applications is crucial for security. Software updates often include patches for known vulnerabilities that attackers may exploit to install backdoors. Enable automatic updates whenever possible, and make it a habit to check for updates manually if necessary. This practice helps close security gaps and reduces the risk of infection.
3. Implement strong security practices
Employing strong security practices can significantly reduce the likelihood of backdoor infections. Use complex, unique passwords for all accounts and enable 2-factor authentication (2FA) wherever possible.
Be cautious when downloading software, especially from unverified sources, and avoid clicking on suspicious links or email attachments. Additionally, consider using a reputable firewall and antivirus software to provide an extra layer of protection against potential threats.
Preventing backdoor infections requires a combination of proactive measures and vigilant monitoring. Use Moonlock’s Security Advisor to make sure your system settings are configured for optimal protection and all apps and software are updated. Even those quick tweaks are enough to significantly reduce the risk of backdoors compromising your systems.
Staying informed on how to check for malware on your Mac and up-to-date on the latest cybersecurity threats will help you maintain a proactive approach to security. Overall, you can protect your devices and sensitive information by strengthening your backdoor cybersecurity.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.