Malware is no longer a threat that Mac users can ignore. In fact, it has grown from a fringe problem to a major security concern. As macOS continues to acquire more users, attackers who use malware are investing much more time into making their attacks more deceptive in order to bypass Apple’s built-in security protections. Today’s malware steals credentials, monitors activity, installs persistent backdoors, and quietly exfiltrates sensitive data.
For anyone using a Mac for personal use, work, or anything else, malware prevention and protection is an essential part of your protection plan. You cannot assume that everything is locked down securely by relying on the default settings. If you do not have a proper protection strategy in place, there are numerous security breaches you could fall victim to.
Building your foundation of knowledge around how malware actually works and how it infiltrates your device is the first step in protecting your information. This guide focuses on practical, real-world defensive measures against malware attacks, helping you reduce risk, recognize threats early, and maintain long-term protection against malware.
What malware is and the kinds you might encounter
Malware is often designed to steal your information and resources. Its purpose is to gain access to your device and take what it has been designed to look for. Today’s malware functions stealthily as possible, actively evading detection. Therefore, it is imperative that measures are put in place to defend against it.
Common malware types include:
- Adware: Injects ads, redirects traffic, and tracks browsing behavior, often bundled with free software
- Spyware: Monitors activity, logs keystrokes, and collects sensitive information without user consent
- Credential stealers: Targets saved passwords, browser sessions, crypto wallets, and authentication tokens
- Ransomware: Encrypts files and demands payment for recovery
- Trojans: Disguise themselves as legitimate applications while performing malicious actions in the background
- Browser hijackers: Modify search engines, inject scripts, and control browser behavior
- Backdoors: Provide attackers with long-term remote access, even after reboots or partial cleanup
How to prevent malware attacks
The following is a handy checklist of things you can do on a regular basis to help keep malware at bay. Obviously, there’s no guarantee that you’ll never get any malware infections, but doing the following will lessen your risk.
Use Moonlock
Apple’s security is good, but when combined with Moonlock, it creates an almost impenetrable barrier to any malware like spyware, ransomware, remote access trojans (RATs), and more.
With the real-time protection and deep scanning abilities that Moonlock has, you have a security system that protects your device 24/7. It quarantines any detected threats immediately to stop them causing any more harm and locks them down until you’re ready to delete them. Try Moonlock for free, and you’ll see how much it can do to protect your Mac.

Enable the Mac firewall
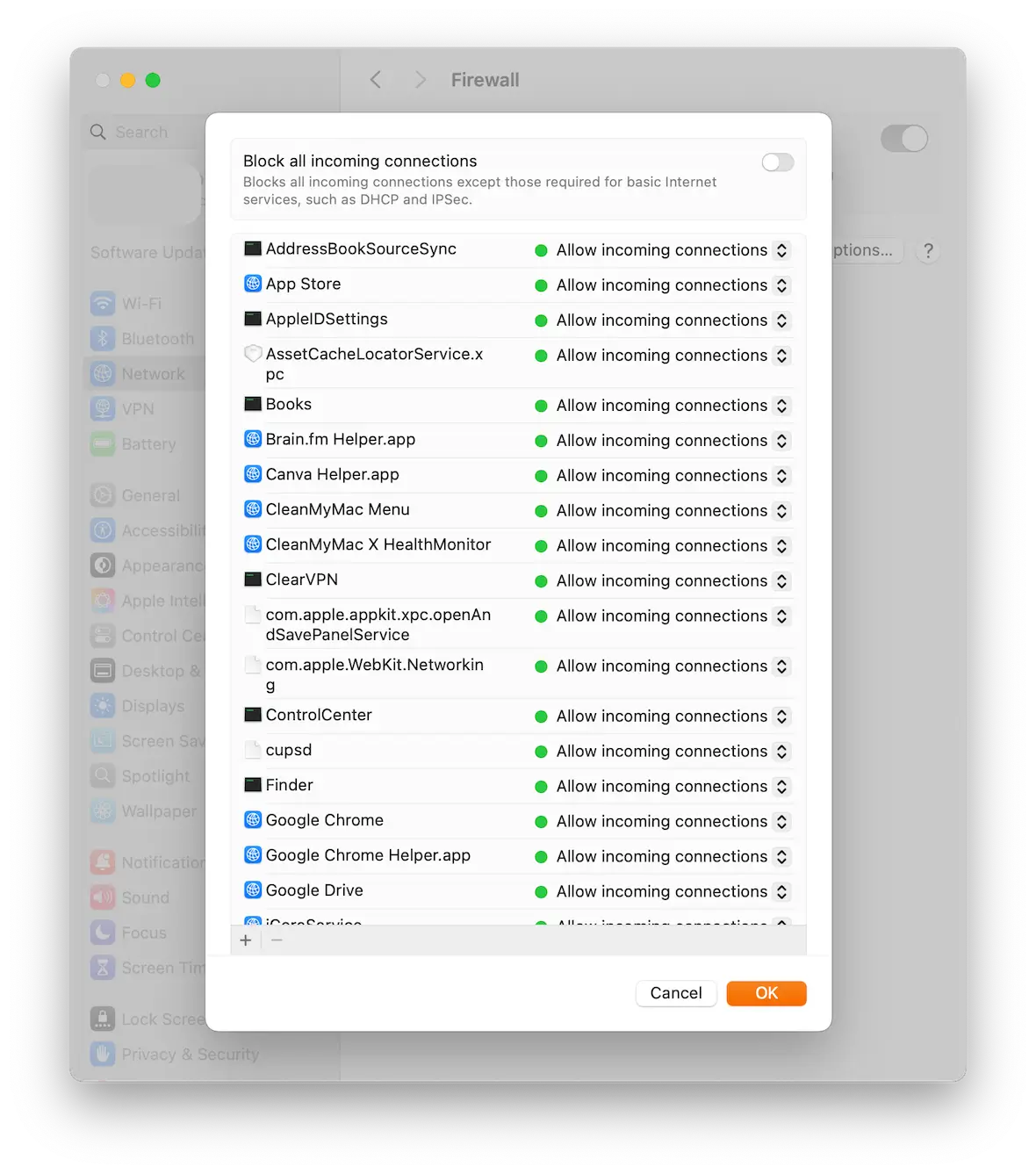
A firewall comes built into your MacBook, and switching it on will stop any unwanted visitors from infiltrating your device.
There’s no complicated setup involved. Simply go to System Settings > Network > Firewall, and toggle it on. That’s more or less all you need to do, but you can always fine-tune app access in the Firewall settings.
Install all system and app updates
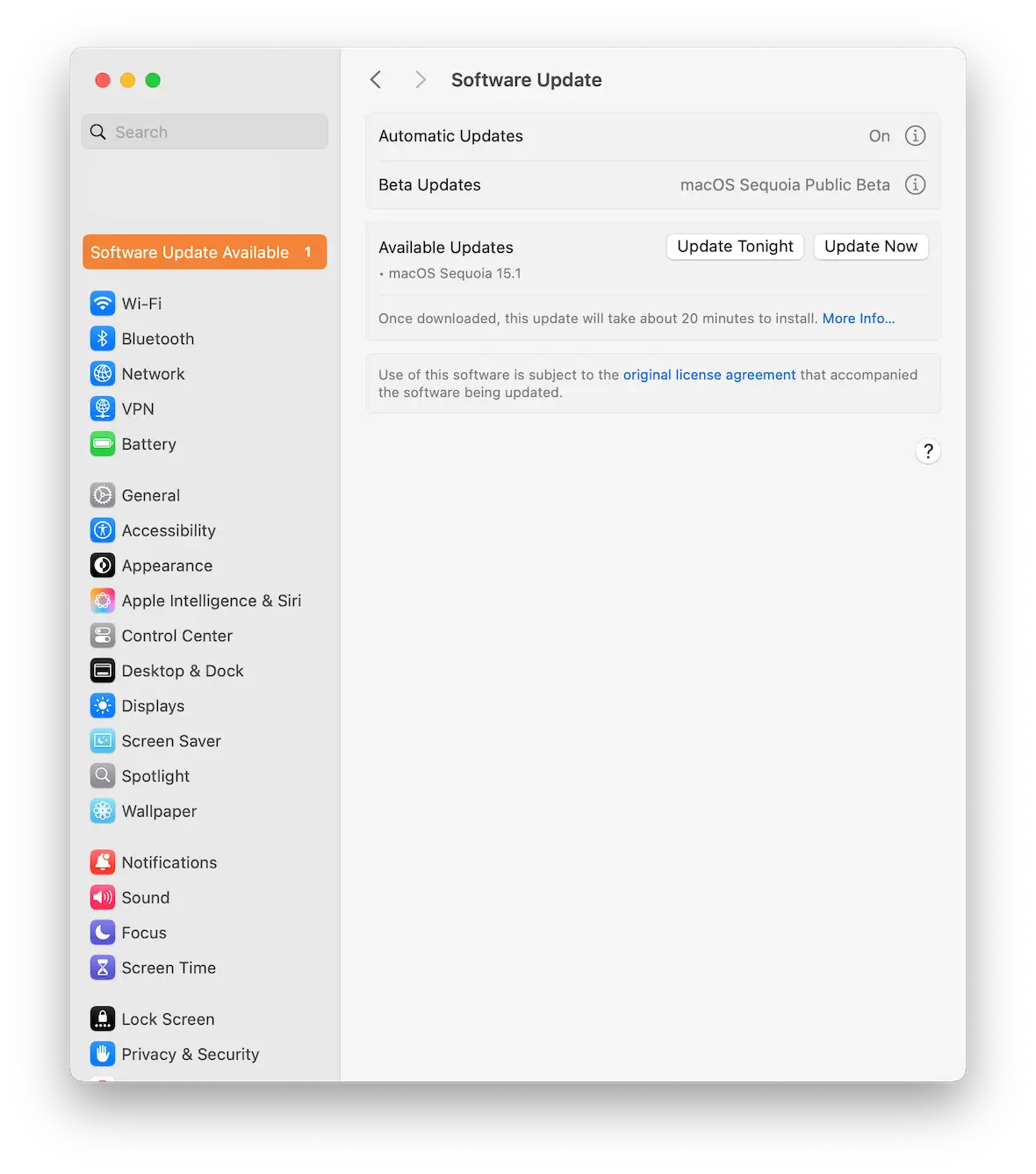
New forms of malware appear every day, and Apple does a top-rate job of keeping up with new threats. Unless a cyberattack utilizes a zero-day exploit (a previously unknown vulnerability), updates from Apple and app developers will address threats.
Updates will ensure that all security vulnerabilities are fixed, making it more difficult for malware to gain a foothold on your Mac.
Be very cautious when clicking links and email attachments
The easiest and fastest way for attackers to get malware onto your device is by getting you to click an email link or download an attachment. Malicious links will lead you to software and malicious scripts or to websites that are infected with spyware.
Always show extreme caution if you are sent a link by someone you don’t know or don’t entirely trust. There may be a nasty hidden surprise waiting on the other end.
Use a VPN
We should stress that using a VPN is not an absolute guarantee against malware. However, it can help in a few ways.
First, A VPN can encrypt your internet connection, so hackers find it impossible to inject malware into your connection.
Second, a VPN will mask your IP address, again making it difficult to target you with malware.
Third, some VPNs have additional features, such as blocking malicious websites.
Our recommendation is Moonlock’s VPN, powered by ClearVPN. Choose a country and server, and have your internet browsing instantly protected.
Limit your app installs to the Apple Store
There are lots of third-party developers out there making exciting and useful software and apps for the Apple ecosystem. However, some of these developers are not trustworthy, and downloading their software will result in malware on your machine.
The best way to avoid this trap is to limit your software and app downloads to the Apple App Store. Apple has a very rigorous set of protocols and checks that all apps must pass before they can be listed in the App Store.
If you feel you can trust a third-party developer, you can override the protection in System Settings. But you should try to avoid it if you can.
Review app permissions regularly
A common weak point exploited by malware is excessive permissions. Plainly speaking, this means apps that have access to the full disk of the computer, full accessibility permissions, or rights to record your screen or microphone.
It is recommended that you review all app permissions in the System Settings and remove access to apps that you do not recognize or trust. You should also assess the permissions of apps that you do trust. Making sure that the permissions available to apps are limited to what is absolutely necessary is crucial. This will reduce the risk of and prevent malware attacks that rely on persistence and surveillance.
Daily habits that make a big difference
Consistency is the most important factor when it comes to malware prevention. Getting into good habits every day can reduce your risk exposure and generally increase your online safety. This applies to threats outside of malware as well. Take your time when going through security prompts, take care when downloading apps, and maybe even read a security policy or two!
There are Security Advisors available within Mac antivirus applications like Moonlock that will identify any risky behavior, check for any malware, and give warnings in real time when suspicious events occur. This helps you avoid malware infections and ensures that you are protected now and in the future.
Watch for unusual system behavior
Malware doesn’t announce itself. But it will give you small signs and warnings that something untoward could be going on in the background. If you notice things like reduced performance, increased pop-up ads, processes in your Activity Monitor that you don’t recognize or haven’t seen before, or more network activity than normal, there is a good chance malware could be the problem.
Paying attention to signs like these will help you identify and hopefully remove threats before any serious security breaches can occur.
Maintain reliable backups as a safety net
In the battle for protection against malware, backups come to the rescue in terms of damage control. If the worst-case scenario occurs and there is ransomware or destructive malware on your system, restoring a recent backup can help you remove the malware and eliminate the threats while preserving your data and information.
Regular, automated backups ensure that even if prevention fails, recovery is fast and secure, a key component of comprehensive malware protection.
Advanced malware protection methods that go beyond basic prevention
Basic prevention reduces exposure, but advanced threats require stronger countermeasures. High-risk users, remote workers, and anyone handling sensitive data should adopt additional safeguards.
Behavioral threat detection
Advanced malware often avoids signature-based detection. Behavioral monitoring identifies suspicious actions instead of known files, allowing it to catch new and evolving threats to help prevent malware infections.
Persistence and privilege monitoring
Some malware focuses on long-term access rather than immediate damage. Monitoring for unauthorized persistence mechanisms and privilege escalation blocks these attacks early.
Continuous security assessment
Security isn’t a one-time setup. Ongoing assessment, alerts, and remediation help ensure that protection remains effective as threats evolve.
How can malware infect your device?
Let’s now take a look at the methods for how malware infects your device. Understanding these infection methods will help you be proactive about stopping them in their tracks.
Web links and email attachments
As we said earlier, web links and email attachments represent some of the fastest ways for malware to spread. These links can be downloads or malicious scripts.
It’s the classic definition of “low effort, high reward.” Cyber attackers can fire out millions of spam emails and chat messages with links and wait for some people to bite. Even if only 1% of the recipients fall for it, it’s still a big victory for the cybercriminals.
The best way to avoid this? Only click on links if they are sent by family members, friends, and trusted colleagues. Ignore the rest.
Website domains
A web link may lead to an innocuous-looking website where spyware is secretly waiting for the unsuspecting visitor. Simply hitting the wrong button or accidentally clicking an ad will be enough for your machine to become infected. The malware will then redirect you to an infected website after you type in the URL of a safe website.
This is an area where a VPN can really help you out, as the best ones will also block malicious websites. Major browsers like Chrome and Firefox also offer very strict protections that block non-HTTPS websites.
Bundled software
If you buy what you consider to be legitimate software, you will most likely trust anything else that’s bundled with it. But malware coming bundled with legitimate software is also an increasingly common method of spreading malware.
This could be a program that is in plain sight and persuades you to install it. It could call itself an updater or an antivirus program. Or it can be something that is secretly installed in the background.
This is why you should always try to confine yourself to App Store downloads or reputable big names.
Network misconfigurations
One particularly nasty form of malware is the remote access trojan (RAT). You really don’t want these on your MacBook. Not only are they hard to completely destroy, but they also burrow deep into your operating system, change its settings, and steal your data.
If your network doesn’t have a password or is misconfigured, a hacker can easily gain access to your Wi-Fi network and, from there, infect other devices attached to that network.
Make sure your network has a strong password and that all firmware is updated to the latest version. You can usually get firmware download links in your router settings.
Infected USB drives
If you find a USB drive lying around, there could be malware hidden on it, just waiting to be released. Hackers are counting on your curiosity being too intense to resist checking it out.
So if you ever find a USB stick out “in the wild,” leave it where it is.
Best tools for malware prevention
Let’s finish by giving you a list of the best tools for malware protection.
An anti-malware app: Moonlock
Having an antivirus software that is specifically designed for your particular operating system is invaluable. That is what Moonlock brings for Mac users. The built-in security tools on a Mac are good, but having 24/7 real-time protection software protecting your system at all times brings your security to the next level.

Moonlock’s Malware Scanner will search far in wide in your system, even checking dormant files that have been hidden in your device for years! If it detects a threat, it moves it to Quarantine immediately and waits for your review and deletion.
With further features like System Protection and Security Advisor ensuring your Mac is set up for the highest level of security, you can effectively protect your Mac. Moonlock has a free 7-day trial, so you can see what it does without breaking the bank.
A firewall: The native macOS firewall
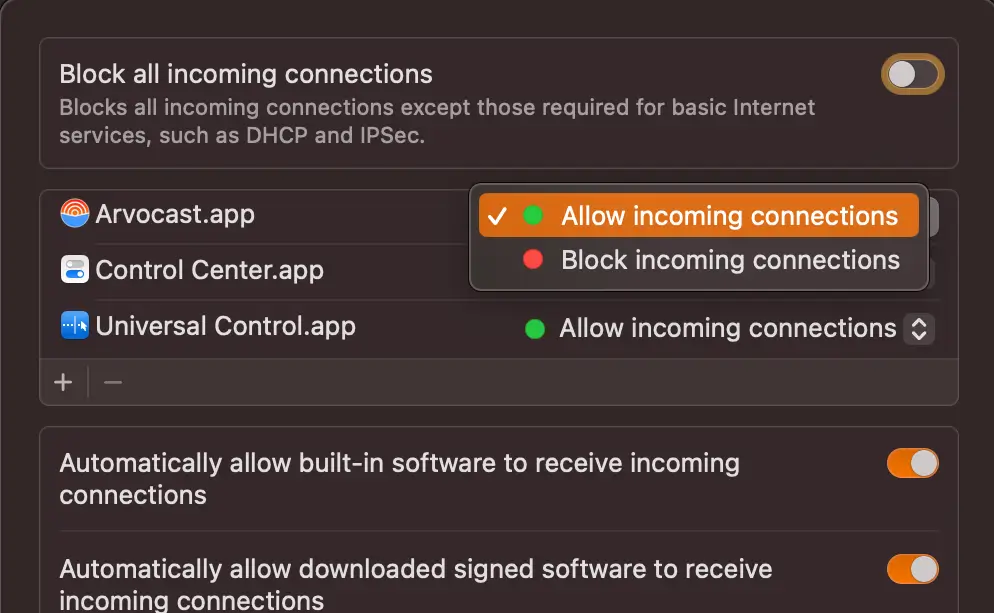
The Mac Firewall comes with every Mac computer, but you have to remember to enable it. It isn’t turned on by default when it really should be.
Thankfully, for those who like quick, easy solutions, it’s one click to turn it on, and then it’s a “set it and forget it” affair. If any malware tries to come through your firewall, it’ll be repelled.
A reliable VPN
There are countless VPNs out there, but Moonlock’s VPN, powered by ClearVPN technology, is the clear choice. You can easily choose from a multitude of servers and countries.
Once enabled, the VPN will encrypt your website traffic and mask your real IP address, making it very difficult for a hacker to introduce malware into your internet connection.
A secure browser: Firefox, Safari, Brave
If you use any of the major browsers, such as Chrome, Firefox, and Brave, you can increase their protection against malicious websites. Just go to your browser settings and access the security and privacy settings. On Chrome, it’s called Enhanced Protection.
Malware is becoming a more serious problem every day, but big tech and third-party developers are helping consumers beat malware with new malware protection features.
Some other measures simply come down to logic and common sense. By exercising caution with links, email attachments, downloads, and the sites you visit, you’re already doing more than most users.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. MacBook and macOS are trademarks of Apple Inc.