Viruses and malware have been around since the early days of technology. The intention of malware has always been to disrupt, steal, mislead, pressure, extort, spy, and cause damage. But what are the most dangerous viruses? And is there a difference between viruses and malware?
While the first viruses were an opportunity for hackers to show off their talent, malware today is a multi-million-dollar cybercriminal industry sector. The goal remains the same, but the skills and abilities of cybercriminals have vastly improved, and so has the potential danger. Preventing malware attacks is, therefore, critical.
Why is malware so dangerous?
Malware is merely code that has a malicious intent behind its design. The potential for it to cause danger is when cybercriminals leverage this code to their advantage.
Malware becomes dangerous in the hands of hacktivists, cybercriminal groups and gangs, scammers, fraudsters, criminal syndicates, scammers, and advanced nation-state threat actors.
Malware is used heavily in various areas of cybercrime, from simple financial fraud campaigns to financial stealers. This is why malware is so dangerous. In the hands of bad actors, it becomes a tool that enables their criminal or illegal agenda — whatever that might be.
The best and most effective way to stay protected online is by using software specifically designed to stop malware. Moonlock is designed to work seamlessly with macOS and makes sure that your computer stays protected 24/7. Some of the features it provides are:
- Real-Time Protection: Moonlock constantly monitors and stops any threats the moment they try to enter your Mac.
- Malware Scanner: This tool does what it says on the tin — the Deep Scan is particularly effective at finding malware that is hidden or lying dormant.
- System Protection: This improves your system security settings by checking for any weak spots in your system, so you can fix the issue.
- VPN/Network Inspector: The VPN hides your IP address and keeps you hidden, while the Network Inspector allows you to stop your data from being sent over suspicious internet connections.
Try Moonlock for free for 7 days to stop malware from causing damage to your Mac.
How malware has evolved into an increasingly common threat
Viruses have always been very popular, widespread, and global. They had their glory days early on, though some, like adware viruses, are still trending. In contrast, malware entered later in the digital global revolution.
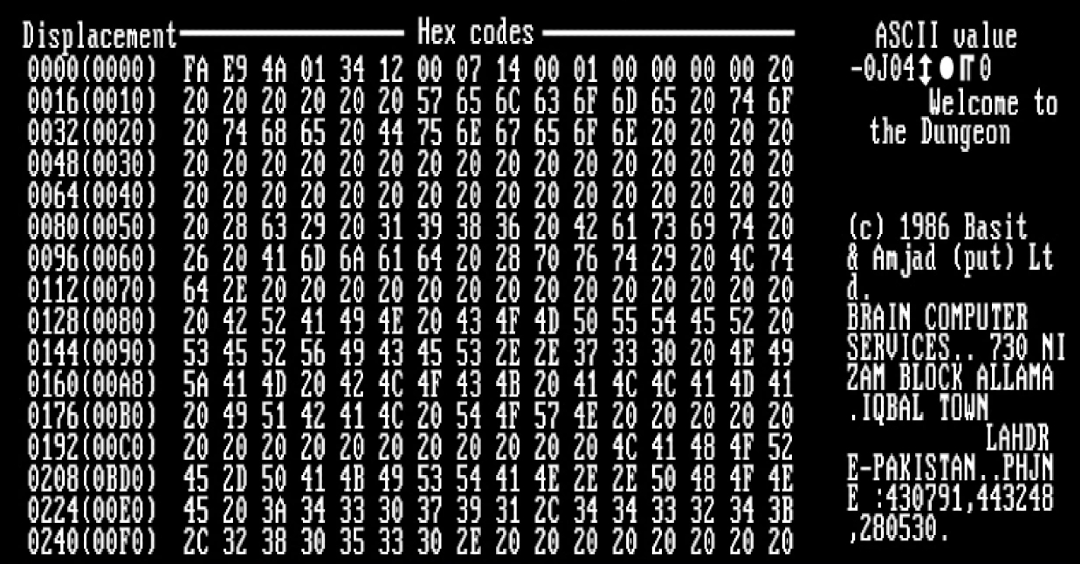
Viruses faded away mostly due to their lack of focused capabilities. Instead, malware offering specific functions became more commonly used by criminals. While viruses have strange and rare qualities, such as the ability to spread and scale at a massive global rate, they are not as advanced as the malware used by cybercriminals today.
For example, identity theft via digital means requires a precise type of malware that can steal personally identifiable information (PII). Ransomware is even more focused. It can breach systems, encrypt with speed, and exfiltrate data. Specific features like these are what drove the criminal boom in malware development.
You can read our detailed report on how to remove malware from your Mac to learn more about malware.
What is the most dangerous virus?
Some malware may be considered more dangerous than others. However, there really is no “most dangerous” malware or “worst” computer virus; all efficient malware is dangerous in its own way.
For example, scam threat actors may use GenAI malware to script convincing scams and then use Voice AI malware to simulate calls with a potential victim. This type of classic scam is dangerous for the victim. At scale, if a campaign like this is global, it can be potentially very dangerous to a lot of individuals and companies.
On the other hand, a nation-state cyber incident, like the alleged breach of United States telecoms by China-supported hackers, may seem widely damaging to national security, but on a global scale, the damage done to individuals internationally is not that high.
Likewise, ransomware wipers may be used to delete the data of large international corporations. That sounds nasty, but is it more damaging than a stealer malware used to steal the social media credentials of many individual users to take over accounts and distribute illegal content?
These examples prove that determining which malware is “most dangerous” requires in-depth knowledge of the real level of damage caused by a piece of malware. A lot of factors must be evaluated.
Real-world examples of viruses and malware
Let’s look at some real-world examples of famous computer viruses and malware:
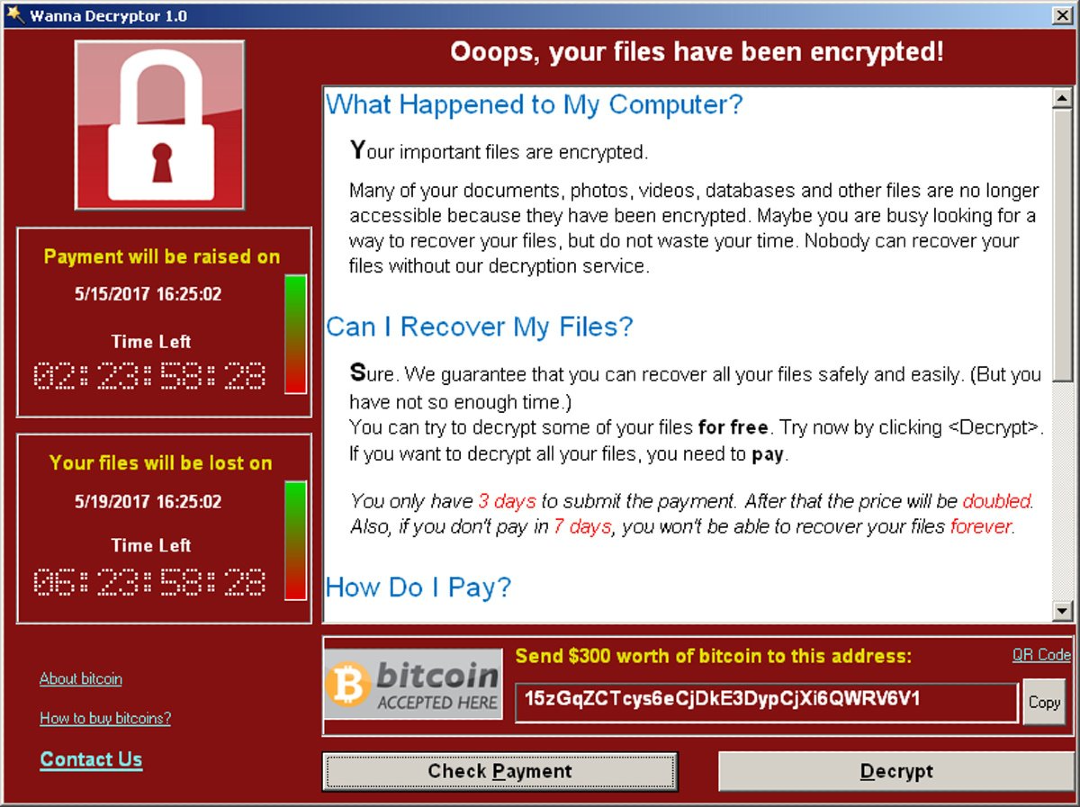
- WannaCry ransomware: This ransomware attack in 2017 affected hundreds of thousands of computers worldwide, encrypting files and demanding ransom payments in Bitcoin. It exploited a vulnerability in Windows, but its impact highlighted the risks of ransomware across all platforms.
- Pegasus spyware: Developed by NSO Group, this spyware can infiltrate iOS and Android devices alike, allowing attackers to access messages and calls and even activate the microphone. It has been used to target journalists and activists, raising significant privacy concerns.
- KeyRaider: This malware specifically targeted jailbroken iOS devices, stealing Apple ID credentials and allowing attackers to access users’ accounts and purchase apps without authorization. It affected thousands of users before being discovered.
- Emotet: Originally a banking Trojan, Emotet evolved into a malware delivery service, distributing various payloads, including ransomware. It has targeted organizations globally, causing significant financial and operational damage.
- XcodeGhost: This malware infected legitimate apps in the App Store by using a compromised version of Xcode, Apple’s development environment. It affected numerous apps and highlighted vulnerabilities in the app distribution process for iOS.
- Ransomware-as-a-Service (RaaS): This model allows cybercriminals to rent ransomware tools, making it easier for less-skilled attackers to launch ransomware attacks. It has led to a surge in ransomware incidents across various platforms, including Apple devices.
- Adware and spyware on macOS: Various adware and spyware programs have targeted macOS users, often bundled with free software. These programs can track user behavior, display unwanted ads, and compromise user privacy, demonstrating that Apple devices are not immune to malware threats.
These examples illustrate the diverse nature of malware and the potential risks they pose to individuals and organizations alike.
New computer viruses and malware trends in 2025
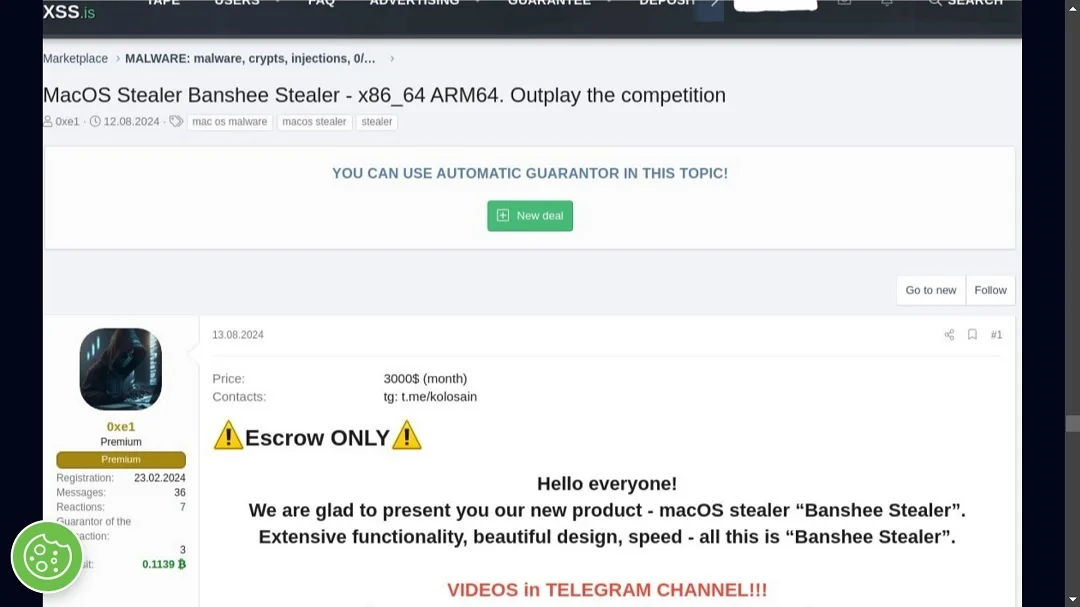
2025 promises to be a year like no other when it comes to malware development and new trends thanks to the establishment of the malware-as-a-service industry (MaaS), the expansion of the global digital attack surface, which creates opportunities to exploit vulnerabilities, and the emergence of AI-powered malware.
Malware trends for 2025 can be categorized into 4 groups: AI threats — which include everything from deepfakes to AI-coded or AI-powered malware, ransomware-as-a-service (RaaS), stealers-as-a-service, and nation-state-supported gangs, which are expected to play a leading role in global cybersecurity. Plus, data leaks, which fall under the category of stealer malware, will continue to grow larger.
Examples of new malware
Let’s look at 3 real-life malware examples in 2025:
- AMOS Stealer: The AMOS Stealer has emerged as one of the most notorious credential-stealers this year. This malware is specifically designed to target Apple users and harvest sensitive information, including usernames, passwords, and credit card details from infected devices. What sets AMOS apart is its ability to target a wide range of applications, including web browsers, email clients, and even cryptocurrency wallets. With its stealthy operation and effective data exfiltration techniques, AMOS Stealer poses a significant risk to users’ privacy and financial security.
- Hidden Risk and other North Korean crypto-malware: North Korean hackers are escalating their crypto attacks in a widespread global campaign to use the illegally stolen crypto they hack to fund internationally sanctioned North Korean weapons and government programs. Under the umbrella of the infamous Lazarus group, North Korean hacker subgroups operate malware like Hidden Risk that’s coded to steal crypto and empty digital wallets. North Korean hackers are also infiltrating top-paying tech jobs, targeting blockchain developers, and deploying a wide range of malware and techniques, including deepfakes, to conduct crypto hacks and heists.
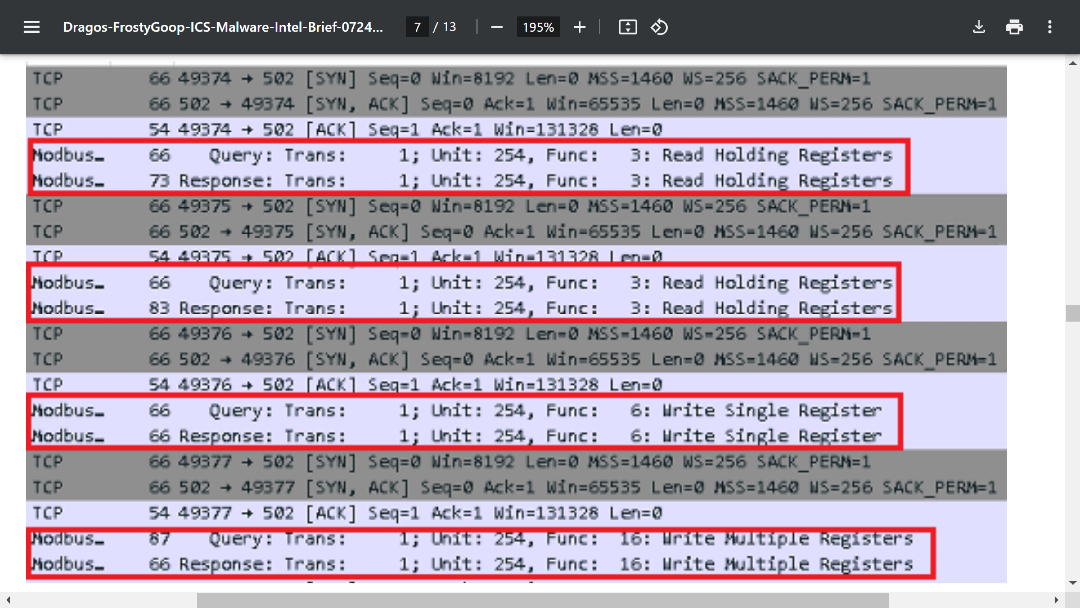
- FrostyGoop, a nation-state critical infrastructure OT-centric malware: In 2024, one of the most notable malware strains was FrostyGoop. This malware is coded to breach, disrupt, and damage critical infrastructure that includes sectors like energy, health, government, logistics, and military. The malware can interact with industrial control systems (ICS). It was used in cyberattacks against Ukraine and is nation-state supported. Similarly, malware from Chinese-linked threat actors of the Typhoon family has wrought havoc, breaching many industries of the US critical infrastructure sector.
How to keep your Mac safe from viruses and malware
Despite the intense global cybercriminal threat landscape, there are still several things you can do to stay safe from malware and viruses. Here are some effective tips to enhance your Mac’s security.
Use Moonlock to protect your Mac from malware

Moonlock is built to stop any and all threats trying to infiltrate your Mac, including viruses, ransomware, spyware, and more. It utilizes real-time protection, scheduled scans, and constant updates to lock down your device 24/7.
To take the possibility of malware issues out of the equation, try Moonlock.
Here’s how to get started:
- Sign up for 7 free days with Moonlock.
- Find the Malware Scanner and run a Deep Scan.
- Turn on real-time protection and background monitoring.
- Review and delete all results from the scan.

Keep your software up to date
Whether it is your OS, an app, or software you are using, always make sure that it is up to date. This cybersecurity tip may sound simple, but it is incredibly effective.
Cybercriminals developing new malware and viruses exploit vulnerabilities in software, but the security teams of the vendors that develop that software swiftly respond with security updates. When you are updating your Mac and your software, you are staying ahead of current threats and malware.
Be cautious with new contacts, downloads, and links
Except for a few sophisticated and highly advanced types of malware that can breach a device without the user doing anything at all (zero-click attacks), all malware needs the user to be installed.
Be suspicious of new contacts, never download untrusted files, and be wary of websites. Check URLs and do not click on links — even if they are ads. Remember, whether or not malware infects your Mac depends on whether cybercriminals manage to trick you into installing it.
Adjust your Mac settings for better security
Not everyone is a tech genius and knows how to set their system up properly for maximum security. Fortunately, Moonlock takes care of that for you with its System Protection feature. This will evaluate how your Mac is set up (security-wise) and identify any potential risks, including file sharing being left on, loose privacy permissions, or disabled encryption.
Then it will walk you through how to simply fix all of these issues, ensuring your Mac is secure going forward.
Use strong passwords, enable MFA, and use biometrics
Creating strong, unique passwords for your accounts is essential for keeping your Mac secure. Combine uppercase and lowercase letters, numbers, and special characters to make your passwords harder to guess. Additionally, enable multi-factor authentication (MFA) whenever possible to add an extra layer of security.
For Apple users, utilizing biometric features like Touch ID and Face ID can significantly enhance your security. These features allow you to unlock your Mac and authorize purchases with your fingerprint or face, making it much harder for unauthorized users to gain access.
Keeping your Mac safe from viruses and malware requires a proactive approach. By using tools like Moonlock, keeping your software updated, installing reliable antivirus programs, being cautious with downloads, and enabling firewall protection, you can significantly reduce the risk of falling victim to cyber threats.
Stay informed and vigilant, and your Mac can remain a secure and efficient tool for your daily tasks.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.