When checking for viruses, we naturally tend to focus on our computers and phones. But what about the network those devices use every day? Specifically, what about the router? How often do we check for router malware?
If you suspect that there may be malware on your network, maybe it’s time to focus your attention on the device that provides you with your internet connection. In this article, we’ll cover how to scan your router for malware and secure your network.
Can a router get infected with a virus or other malware?
Can a router get a virus? Yes, routers can indeed get infected with a virus or other malware.
Statistically, router malware isn’t as common as malware on a MacBook, for example. It can happen, however, so you should check for router malware on a frequent basis.
Router malware can be particularly dangerous, as it can intercept and redirect your browsing without you even realizing it. It can intercept and steal your data, reroute you to its own websites, or, at the very least, slow down your internet connection.
How to tell if your router has a virus: Common symptoms

Here’s a quick list of common router virus symptoms. Do you recognize any of the following?
- Your internet speed has slowed down to a crawl. Check with your internet service provider (ISP) first to see if they have any speed issues.
- Your Wi-Fi is constantly being disconnected.
- You’re being redirected to websites that you didn’t ask to visit. This may be an indication of a pharming attack through domain name services (DNS) hijacking.
- You’re getting a large number of pop-up ads.
- You’re unable to download antivirus updates.
- Your DNS settings, router password, and firewall settings have been changed.
- Your router starts acting strangely, such as rebooting or overheating.
- Your data usage is spiking. This could indicate that your device is part of a botnet taking part in a distributed denial of service (DDoS) attack.
How common is router malware, and should you be concerned?
Router malware is a rapidly growing problem. In fact, in 2023, there were over 6 billion router malware incidents, a 10% increase over 2022.
Here are some of the most infamous examples of recent router malware incidents:
- Mirai (2016) infected 100,000+ routers and IoT devices.
- VPNFilter (2018), a particularly nasty one, affected 500,000 routers worldwide. They were capable of spying and destroying hardware.
- Mozi (2020-2022) infected routers to use them for large-scale DDoS attacks.
- Chalubo (2023), in what was probably the worst router malware attack ever, made 600,000+ small office and home routers inoperable in the United States.
Fortunately, the risk is higher if you’re using an older router with outdated firmware or a weak (or missing) password. However, newer router models aren’t completely immune, as malware can still emerge over time.
How to check your router for malware
There are certain things you need to do to check your router for malware. Every router model differs somewhat, but the tips we cover here apply across the board.
Log in to your router settings
If you don’t already know your router IP address, try one of the following ones:
- 192.168.1.1
- 192.168.0.1
- 192.168.100.1
If these don’t work, do the following:
- Do a web search for the router name, such as “[name of brand] router address login.”
- Some routers — like Deutsche Telekom — have specific domains you need to visit.
- Look at the box or any documentation that came with the router.
- Contact your ISP and ask for the router login.
Once you have the address, log in. If you don’t know the password, the default password is usually listed on the back of your router.
If you’ve changed your password and have since forgotten it, you can reset the router. Normally, this involves holding a Reset button at the back of the router to reset it to its factory settings.
Check the following router settings
Once you’ve logged in, check the following:
- Connected devices: Are there any unknown devices attached? If so, disconnect them.
- DNS settings: If these settings have been changed, change them back, either to your ISP’s default settings or to a trusted set of DNS settings.
- Port forwarding/virtual servers: Check for any suspicious entries here. If you see any, remove them.
- Remote management/remote administration: If this is enabled, disable it.
How do you remove malware from your router?
To remove malware from your router, first disconnect the router from the power and shut it down. The fastest way to do this is to simply pull the power cord. Leave it off for a minimum of 5 minutes, then reconnect it and let it boot up again.
Now, change the password. Look for any settings that may have been changed (referenced above). Change them back.
Run a router virus scan with anti-malware tools
There are lots of different router tools out there. One option is to do a web search to determine which router anti-malware tool is best suited to your router model and let it run to see if there is any malware on your Wi-Fi router.
If, however, the router tool finds nothing, you’ll need to refocus your efforts onto your Mac device, as the threat may be there. In this scenario, Moonlock is your best option. Moonlock is free to try for 7 days, so it’s worth giving it a shot.

Factory-reset your router
To completely wipe everything off your router, you can simply factory-reset it. This process may vary depending on the make of the router. In general, you’ll need to hold a Reset button for 10-15 seconds (until the light goes out), release your finger, and wait for the router to do its thing.
When the router is reset, the password will be changed to its default setting, so be sure to change it!
How did my router get infected with malware?
So, how does malware get into your router in the first place? Well, it can be due to the following:
- Compromised updates: You should always download firmware updates from the router manufacturer’s official website. If you download them from anywhere else, they may be compromised by router malware.
- Unpatched security vulnerabilities: Security vulnerabilities can expose your router to attacks. Be sure to download and install all new updates.
- Weak and default passwords: Many people don’t bother to change the default router password that was set at the factory. Others use weak and predictable passwords that attackers can easily guess. This doesn’t directly cause malware infections, but it can allow attackers to break into the router, which may later lead to malware being installed.
Using public Wi-Fi — such as hotel Wi-Fi, which is notoriously insecure — puts you at increased risk of router malware.
Keep everything up-to-date with the right encryption protocols, and your risk is greatly minimized.
How to strengthen your network’s malware protection
Even if you are using the latest router model, the latest firmware, and a strong password that is a combination of uppercase letters, lowercase letters, and bird noises, you should still be careful. Complacency is never good.
Fun through these security checks on a regular basis to prevent malware attacks and run a network virus scanner.
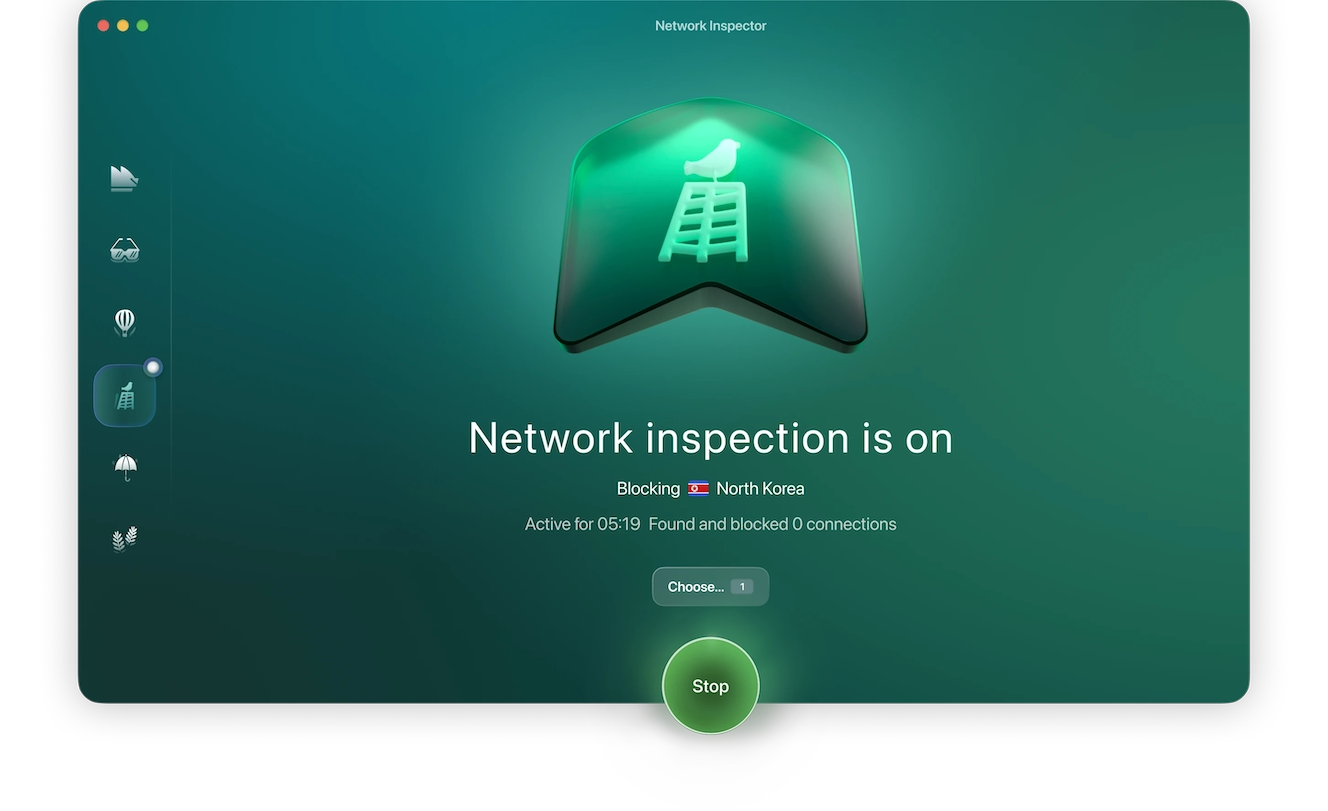
Improve your network security with Moonlock
Firewalls filter incoming and outgoing traffic within a network and block suspicious connections. With Moonlock, you can restrict connections from countries associated with malicious activity.
Although this might seem like overkill, remember that hackers often use computers and routers belonging to unsuspecting citizens to launch high-scale attacks.
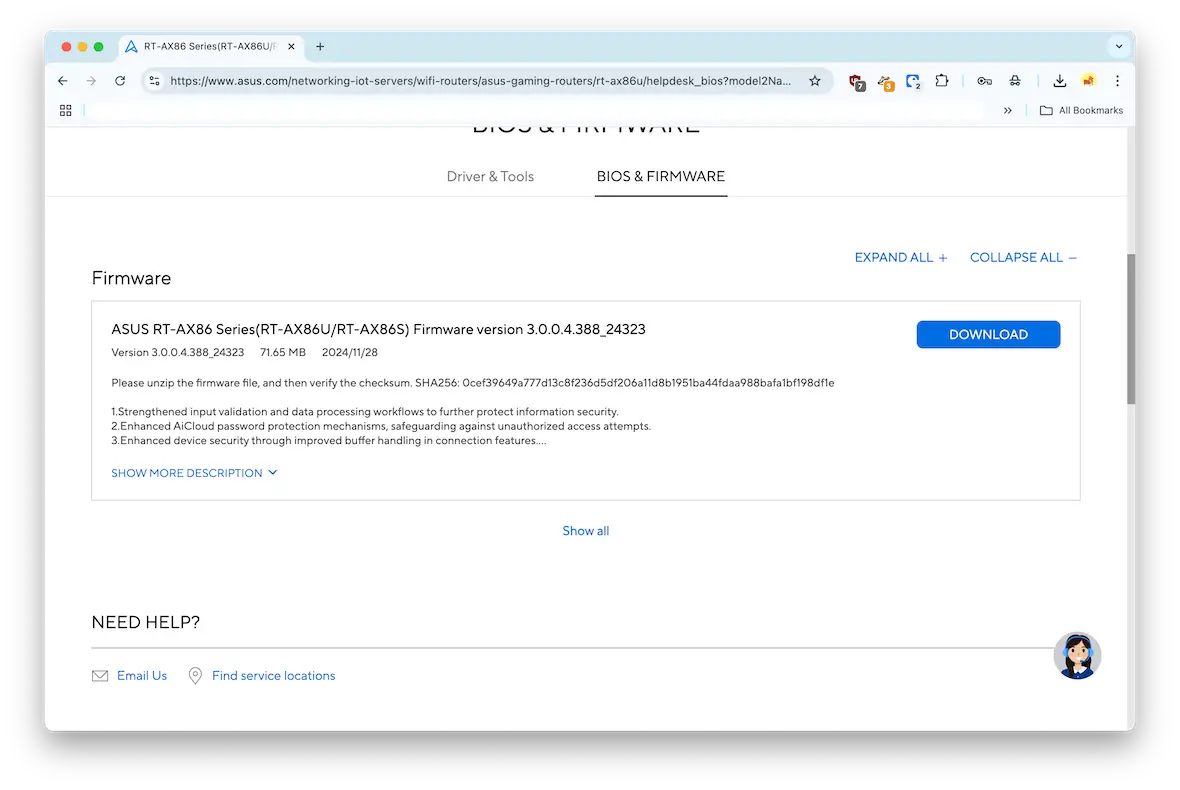
See if your router has new firmware
Firmware is the name given to router software updates. Your router should have a firmware section with available updates. If you see any, install them right away.
Some routers will install the firmware automatically. See if your router offers this setting.
Another option is to download the firmware from the router manufacturer’s website.
Change the default login credentials
When you buy a new router, the factory will often set the username and password to something such as admin/admin or admin/password. If you don’t change them, hackers can easily get into your network.
Change the username and password or network security key. Ideally, these details should be changed once a month through the router settings.
Change the name of your router
If someone wants to attack you personally, putting your name on your Wi-Fi network removes the guesswork for them. Instead, name your network something that keeps your identity anonymous, or you can keep the one given to it at the factory.
Upgrade your encryption
For the most protection, your encryption should ideally be WPA3 or WPA2, which is the most secure. If it’s WEP or WPA1, upgrade them immediately. You can do this in your router settings, usually with just a couple of clicks.
Use WireShark to check for suspicious web traffic
This is rather advanced, so it’s only for people who know what to look for. WireShark is a free network monitoring tool that you can use to see who is on your network. It’s a good option for determining if there is potentially unwanted traffic on your network.
Make your Wi-Fi network invisible
If you don’t want anyone outside to see your Wi-Fi network, go into the router settings and disable SSID broadcasting. A hacker can’t attack what they can’t see!
When you suspect a virus or other malware may be on your network or MacBook, it can be easy to overlook the router as the source of the problem. But this is your gateway to the internet. Therefore, it’s a major target for hackers. Include your router in your security checks. You may find something in there you didn’t expect.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac, MacBook, and iPhone are trademarks of Apple Inc.






