If you’ve ever heard the term “logic bomb,” you may be a bit confused about what it actually is. Is a logic bomb a threat? Is it malware or a virus? And where does logic enter into it?
Logic bombs describe a specific type of functionality that exists within malware. In short, the term refers to triggering events that set certain malware behaviors in motion. But how exactly does this work, and what does it mean for the average user? Read on to learn more about logic bombs, including why you should be extra vigilant in looking out for them.
What is a logic bomb?
What is a logic bomb? First, let’s clarify that a logic bomb is not a piece of malware itself. Rather, it is a malicious function set in motion by a piece of code that lies dormant inside a device or network until certain conditions are met to set it off.
Possible conditions for a logic bomb include:
- A certain date arrives.
- The victim deletes a file.
- The victim opens a file.
- The user logs in to the infected device.
Basically, any condition can be programmed to set off the logic bomb virus. It can then set in motion a chain of events leading to a cyberattack.
How a logic bomb works and what happens when it’s triggered
Let’s analyze the effects of logic bombs in cybersecurity and break down how they work:
- The logic bomb code is put into the network or device. This has to be done by someone with physical access.
- The logic bomb sits dormant inside the network or device until the specific condition arrives.
- Once that condition is met, the logic bomb code activates and executes a predetermined behavior.
Is a logic bomb malware, or is it a virus?
In a previous article, we explained the difference between malware and a virus, but where does a logic bomb fit in?
A virus is a form of malware designed to self-replicate and infect as many computers and networks as possible. Malware, meanwhile, is a broader category covering a wide range of different malicious attacks, including adware, spyware, trojans, and ransomware, not all of which are replicating or designed to spread to other devices.
A logic bomb is not designed to jump from MacBook to MacBook. Technically, it isn’t even a category of malware. Instead, a more accurate logic bomb definition would be to call it non-replicating code, usually associated with malware, that only activates when a specific event occurs.
Logic bomb vs. time bomb: What sets them apart?
There’s more than one “bomb” in the world of cybersecurity. In addition to logic bombs, there are also “time bombs,” and we don’t mean the kind that need the red wire or the blue wire cut to defuse them.
Whereas a logic bomb is triggered by a specific event, a time bomb is malicious code set to only go off at a predetermined time and date. This makes it a category of logic bomb. However, no other conditions apply.
Why logic bombs are more dangerous than you think
Logic bombs are more serious than they may at first appear. Consider the following:
- Logic bombs require direct access to a device and/or network, meaning that individuals with personal grudges, such as disgruntled employees or angry exes, can be attackers.
- Malware like trojans and spyware can be detected once they enter a system. Logic bombs, however, can evade detection by lying dormant.
- Logic bombs can be coded to target specific systems or specific data formats.
- Since logic bombs can lie dormant for a long time until the right conditions are met, they are extremely difficult to detect until they activate.
Malware that operates on a logic-bomb basis is also nearly impossible for the average user to detect on their own, even after it activates. You need a reliable security tool, like Moonlock, to keep an eye out for any suspicious activity on your Mac.
Types of logic bombs and famous examples
There are 3 types of logic bombs, which we will analyze below. We’ll follow up with some real-world logic bomb examples to show you how insidious they really are.
Logic bomb types
The term “logic bomb” can refer to any of the following:
- Time bombs: As previously mentioned, time bombs are considered a type of logic bomb, as they are triggered at a specific date and time.
- Event-triggered bombs: These logic bombs require that certain conditions be met, either by the user or the operating system.
- Hybrid bombs: Whereas event-triggered bombs operate on a single, specific condition, hybrid bombs require that multiple conditions be met before they are triggered.
Examples of logic bombs
To give you a better idea of the real-world harm logic bombs can cause, here are some famous logic bomb attacks that took place.
Roger Duronio (2006)
After becoming unhappy about a lower-than-expected bonus, a systems administrator at UBS PaineWebber named Roger Duronio planted a logic bomb in the company’s network. It was set to activate at a specific date and time.
When the bomb went off, it caused a catastrophic amount of damage to 2,000 networks and to the company itself. The recovery process cost the company millions of dollars in lost revenue. Duronio, meanwhile, got 8 years in prison.
Fannie Mae (2008)
In 2008, a contractor at Fannie Mae named Rajendrasinh Makwana lost his job. Before he left, he put a logic bomb in the company network that would have deleted data on over 4,000 servers on January 31st, 2009. Luckily, another engineer found the logic bomb first and was able to remove it. Makwana was sent to prison.
South Korea (2013)
In what was suspected to be a North Korean cyberattack, South Korean banks were hit by malware logic bombs. These ones had time-based conditions attached and caused over 30,000 servers to be completely wiped, shutting down ATM and banking services across all of South Korea.
Sony Pictures (2014)
Again attributed to North Korea, Sony Pictures in Los Angeles was subjected to massive logic bomb attacks that erased data, released movies, and wiped servers. These logic bombs were specifically timed to activate when IT departments were either empty or working with a skeleton crew.
Key signs to watch out for in logic bomb malware
Unfortunately, it’s rather unlikely that a victim will detect a logic bomb until it’s too late. However, if you notice any of the following, it’s possible you may have a logic bomb on your device:
- Be on the lookout for unusual system behavior. This encompasses a wide range of symptoms, such as your operating system slowing down, sudden crashes, issues that require rebooting, or strange error messages appearing.
- You may notice that critical system files have been altered. This should be a red flag.
- If your MacBook’s antivirus or firewall has been changed without your permission, it’s worth investigating further.
- Suspicious processes may start running in Activity Monitor, consuming a large amount of your MacBook’s CPU.
Because logic bombs are so difficult to detect, manual inspection is usually a waste of time. Instead, specialized malware detection tools are highly recommended.
How to remove malware with logic bomb functionality
If you’re convinced that a logic bomb — or any type of malware — is on your computer, here’s what you need to do to remove it.
Disconnect from the internet
An internet connection is the lifeblood of malware. Malware needs a line to the outside world to transfer its stolen data. Therefore, cutting the Wi-Fi connection instantly cripples it.
Reboot the Mac in Safe Mode
The next step is to boot into Safe Mode to stop the logic bomb from activating. How you boot into Safe Mode depends on what type of MacBook you have.
Mac Apple Silicon
- Reboot the Mac and hold down the power button until you see Loading Startup Options.
- Select the startup disk, hold down the Shift key, and click Continue in Safe Mode.
- Your Mac will restart and enter Safe Mode.
Mac Intel
- Restart your Mac and hold the Shift key. Release Shift when you see the login window.
- Log in. That’s it.
Get rid of the malware with Moonlock

Manually removing any type of malware, spyware, adware, or Trojan is tricky and doesn’t always work out, especially if you’re not particularly good with tech. Use Moonlock to run a system-wide scan to find and get rid of malware with a logic bomb that might be lurking in your files.
Moonlock is a powerful security tool designed specifically for macOS. A Deep Scan can search through your Mac for known threats, including malware that hasn’t started messing with your device yet, exactly like a logic bomb.
With a 7-day free trial of Moonlock, you’ll gain access to Moonlock’s Malware Scanner, in addition to many other security features to help you catch logic bombs in the act.
Here’s how you run your first anti-malware scan:
- Open Moonlock and click on Malware Scanner from the left sidebar.
- From the drop-down menu, click Configure. If this is the first time you’re running a scan with Moonlock, it’s best that you take a couple of minutes to configure it based on your needs.
- A new window with additional security settings will pop up. Under “Scan type,” you can choose between a Quick, Balanced, and Deep scan from the menu. Information about each scan type’s Speed, Depth, and Purpose is listed right below.
- We recommend you opt for a Deep scan and include all optional file types: archives, disk images (DMG), and packages (PKG). Once you’re done, close the settings window.
- Back in the Malware Scanner tab, click Scan.

Moonlock takes a methodical approach, searching through your Mac to make sure it doesn’t miss any corner where malware with logic bomb functionality could be hiding. If it finds anything, it’ll immediately lock it up in Quarantine, isolating it from the rest of your device.
Once the scan is complete, Moonlock will present you with a list of all the threats it found. From there, you can safely inspect and remove them.
Completely restore your files from a backup
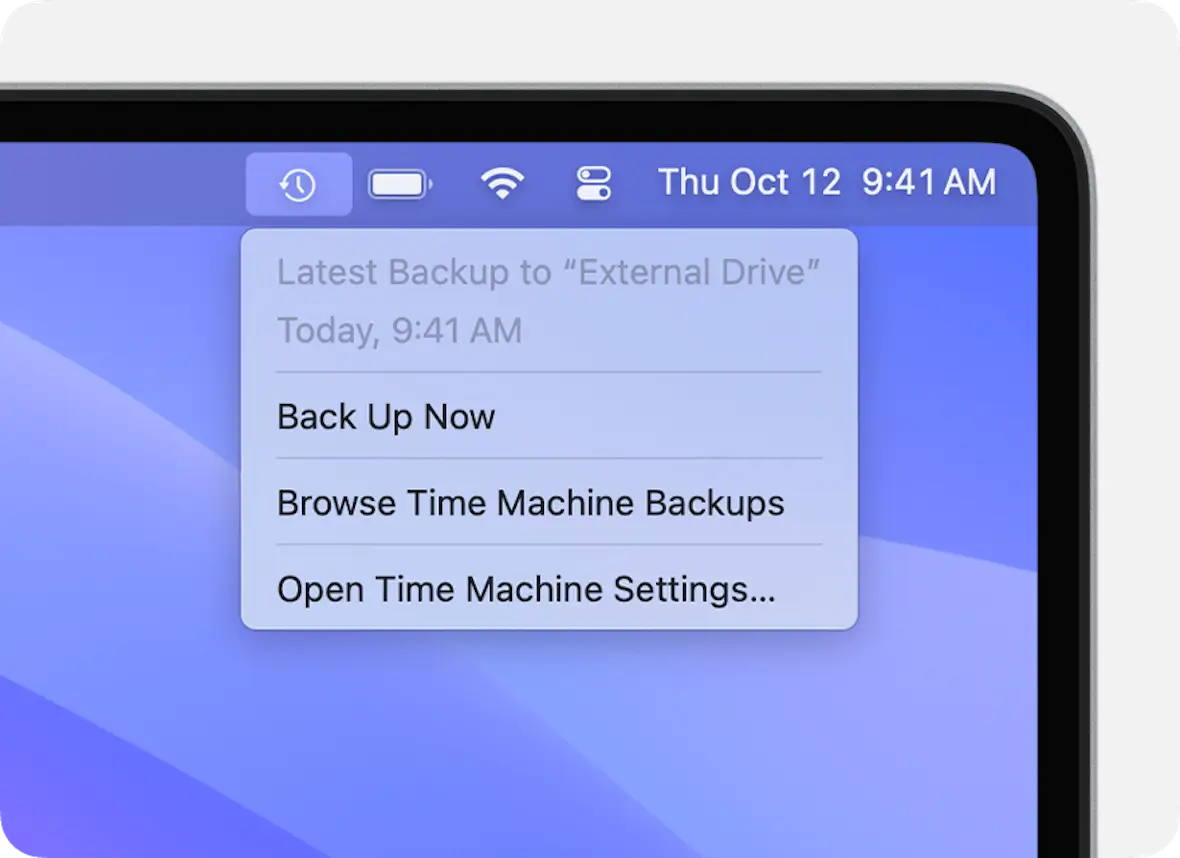
The next step is to overwrite the current files with your latest backup. Obviously, this should be a backup from before the logic bomb activated and released its malware payload.
Backups can be from Time Machine (the easiest method), iCloud backups, or files stored on an external device.
Ensure that macOS and installed apps are all updated
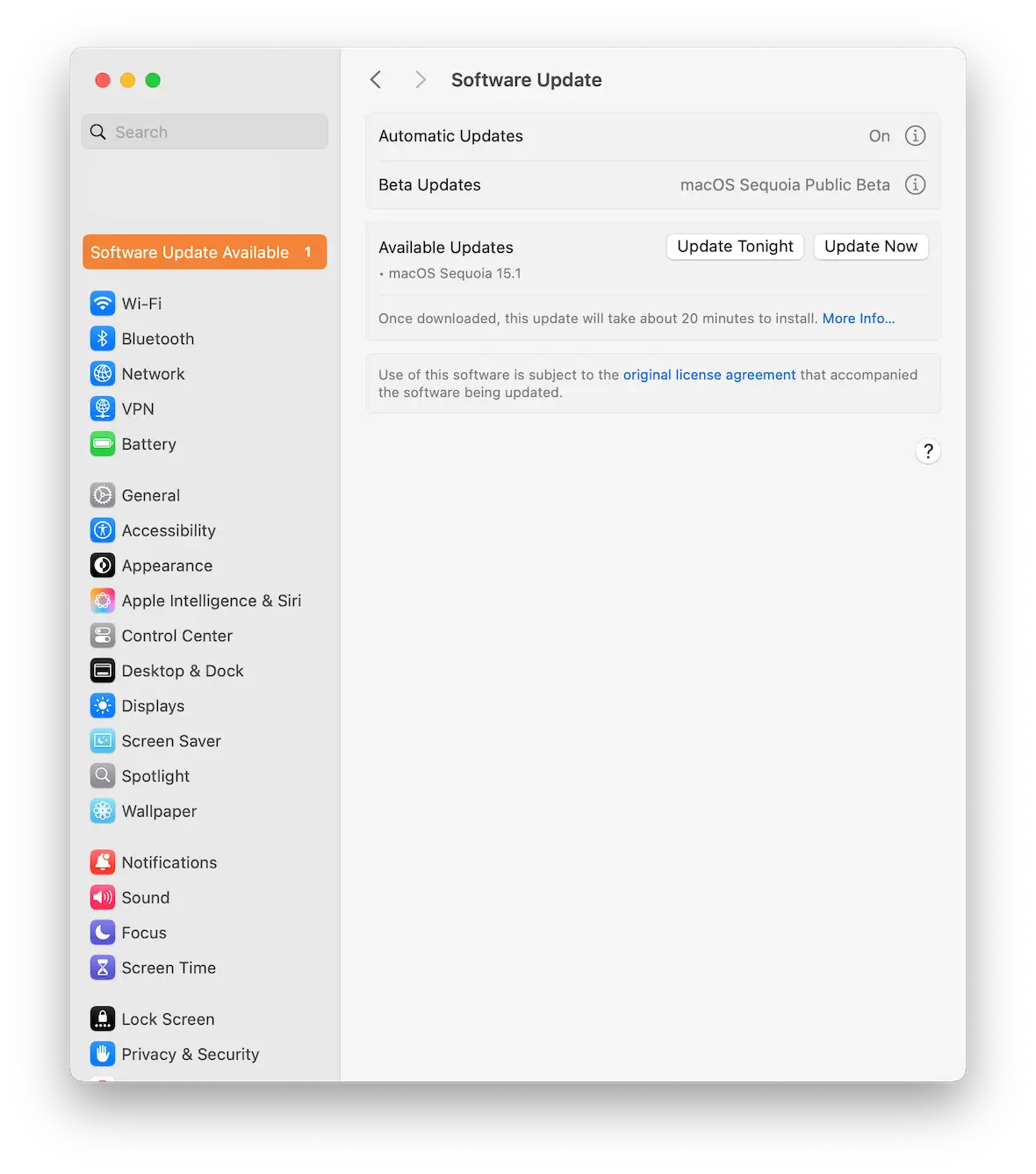
Malware is designed to take advantage of vulnerabilities in operating systems and software. Therefore, make sure you install all updates and security patches in a timely manner.
To update macOS, go to System Settings > General > Software Update.
To update your installed apps, open the App Store and click the Updates tab.
How did a logic bomb infect my device?
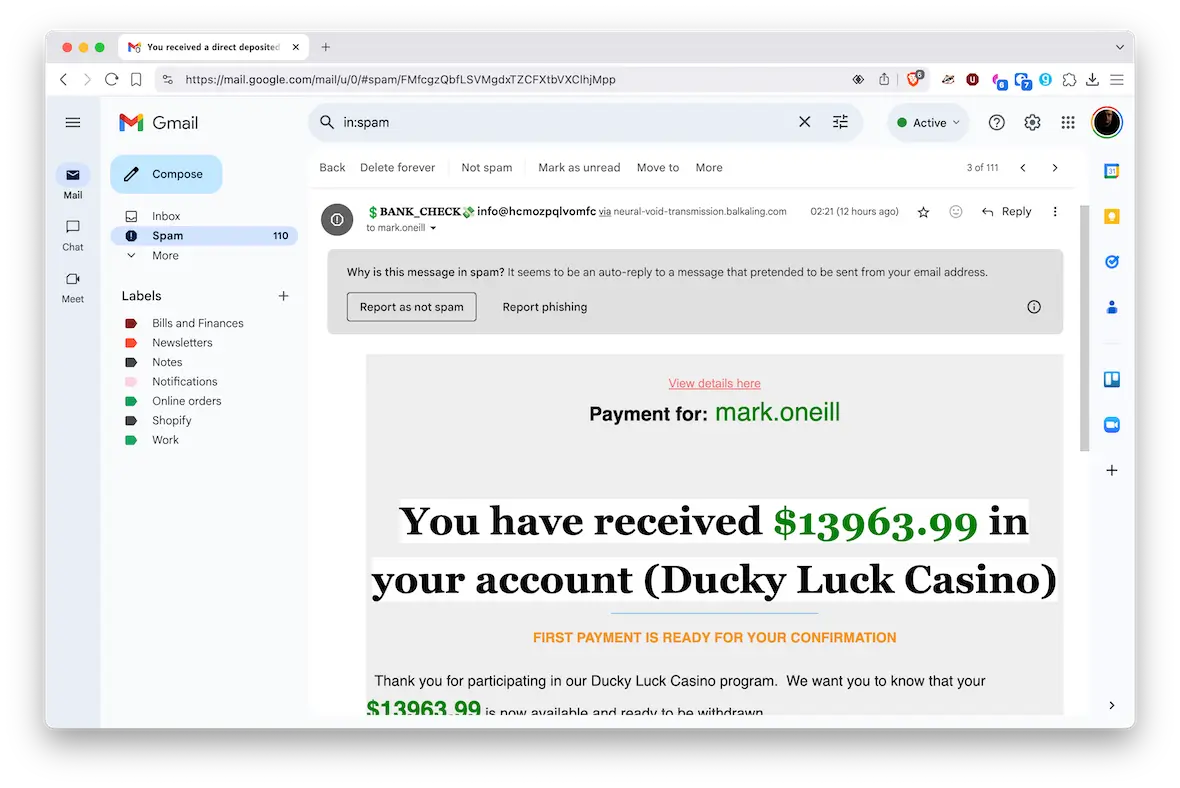
Malware containing a logic bomb infects devices like any other malware, so be certain you don’t fall into any of these traps:
- Phishing emails containing infected web links and malicious attachments represent the most common method of malware infection. Emails can be sent out instantly by the millions, and only a small number of recipients need to click the link or download the attachment for the attack to be successful.
- Infected software and apps are the next favorite method. Installing apps from inside the App Store or from recognized developers is usually safe. But installing something from outside of the App Store or recognized developers has the potential for disaster.
- As we’ve previously mentioned, a lot of logic bombs are planted on networks and devices by disgruntled employees with physical access. Be aware of circumstances that might lead a person to take such action.
- Unpatched operating systems and software often lead to malware. This is why using outdated operating systems and/or software is a bad idea.
How to protect your Mac from logic bomb attacks
We’ll conclude by giving you a list of tips to protect your Mac from a logic bomb attack.
Use Moonlock for regular scans
Regular scans are a must if you’re looking to be proactive in catching threats with a logic bomb as soon as they set foot on your Mac. With Moonlock, you don’t have to keep running your own scans and setting up regular reminders on your calendar. You can use the built-in Scan Planner to schedule scans in the background, choosing your preferred frequency, time of day, and scan type.
You can take your security a step further and enable real-time protection to continuously monitor your Mac for suspicious activity.
To switch this function on, sign up for a free trial of Moonlock, then, from the Home tab in the app, click Explore. From the right sidebar, under Real-Time Protection, click Options. In the new window, under “Continuous monitoring,” tick the box for “Turn on real-time protection.”
Always back up your files
If a logic bomb hits, some or all of your files could be damaged. Therefore, you should ideally have regular Time Machine backups. Failing that, store backups on iCloud or on a removable hard drive.
Keep macOS and all software updated
If there are any vulnerabilities on your Mac, security patches will fix them and close up the holes.
Keep an eye on Activity Monitor
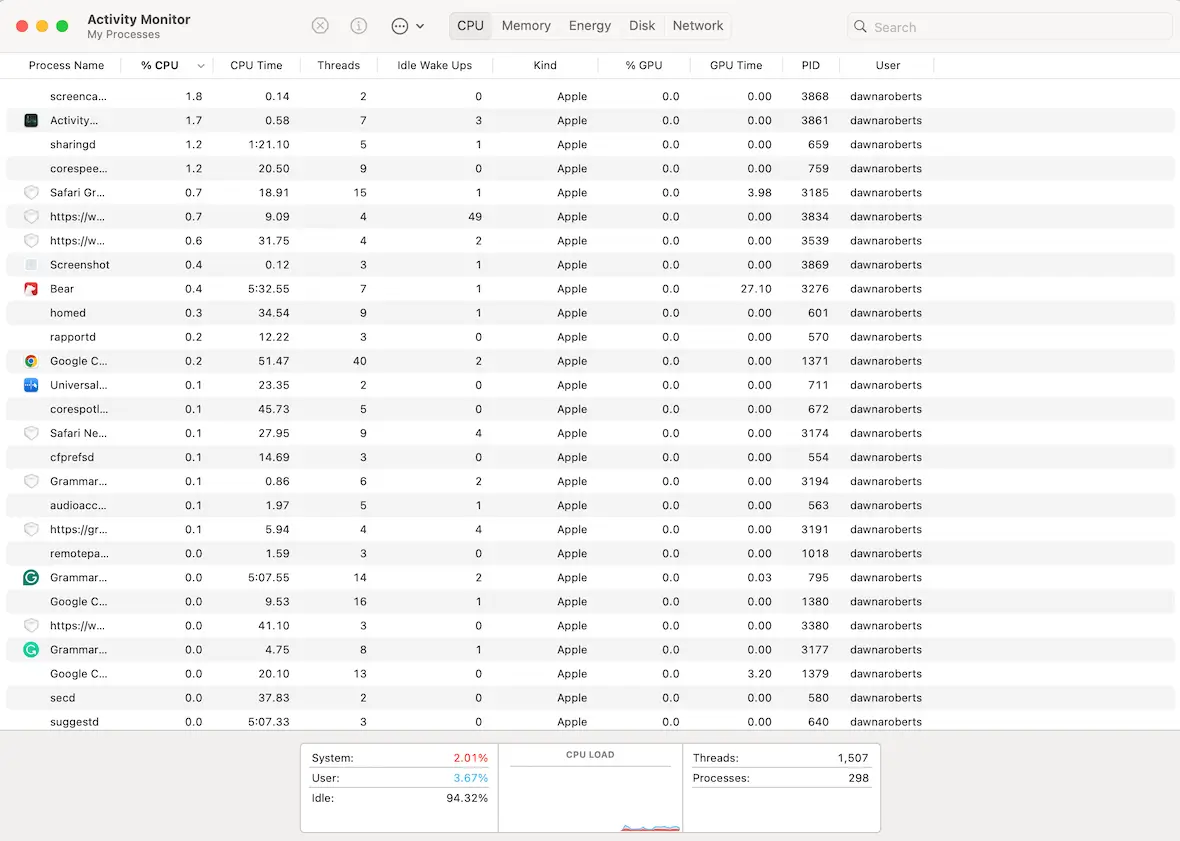
We mentioned Activity Monitor earlier, but it bears repeating. Malware tends to consume excess CPU, thus slowing down your system. If you see any running processes consuming large amounts of CPU, you may have an unwelcome visitor.
Protect your MacBook with a password
To prevent others from physically accessing your device, set up a password on the main login screen. If you have to step away from your laptop for a moment, either close the computer to put it into Sleep mode or shut down the Mac entirely.
Just like fileless malware, a logic bomb is difficult to detect — and tricky to stop. Fortunately, by using Moonlock and employing some common-sense cybersecurity techniques, you can radically reduce your risk.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac, MacBook, and macOS are trademarks of Apple Inc.