How many devices and accounts do you use every day? From personal social media to work-related email accounts and messaging apps, the digital landscape continues to expand. And with this expansion, your data’s security and privacy face new challenges. You can take note of simple hacking signs to stay one step ahead and keep your online life, computer, tablet, or smartphone safe.
Can hackers really access your personal information without you knowing?
It is possible for hackers to access your device and take your personal information, and you would be none the wiser about it. Whether it’s your Gmail or your TikTok account, hackers have ways of getting in.
Here are some ways a hacker can have a snoop about your system behind your back.
Malware
This one is an oldie but a goodie. Removing your information from your device requires a transportation method to carry it through your Wi-Fi network and off to the external server belonging to the hacker.
That’s where malware comes in. Whether it’s in the form of a virus-infected link, software carrying a nasty surprise, or an infected email attachment, malware can quickly rampage through your operating system.
The moral of the story here is never to click email links or message links from unknown, untrusted sources. Don’t open email attachments from them either. And be cautious about where you download your software from.
Malware is still one of the most effective ways of hacking your computer. That’s why it is so important to have a system in place that immediately detects malware and neutralizes it. Moonlock is designed specifically for macOS, and with its real-time protection, background monitoring, and Malware Scanner, it makes sure that your Mac is completely secure.
It will find and quarantine any existing malware on your system and help you improve your security settings to keep you protected going forward. Start a free trial of Moonlock and give it a test-drive on your own Mac.
Data breaches
It seems that not a week goes by without news of yet another data breach at a major company, in which customers’ details are stolen and moved to an external server. This information can be names, addresses, dates of birth, login names and passwords, and much more.
If the passwords are hashed, that will slow the hacker down (maybe even deny them the passwords). But everything else would be in plain text and there for the taking.
Public Wi-Fi
While you’re sitting in Starbucks, sipping your cappuccino and writing your screenplay, the guy at the next table could be monitoring your internet traffic every time you hop online. In this way, they can see what sites you go to and what your login details are for each site.
It doesn’t have to be at a café, though. This can happen anywhere with public Wi-Fi, such as a hotel. And don’t be lulled into a false sense of security just because the network has a password. That can be bypassed with a bit of work.
The best way to avoid this problem is to not use public Wi-Fi, period. But if you really need to use it, turn on Moonlock’s VPN first. This diverts all your internet activity through an encrypted, impenetrable tunnel, meaning there will be nothing for the hacker to see.
Why does outdated software increase the risk of hacking?
There’s a very good reason why Microsoft doesn’t support Windows 95 anymore. Or why Apple has stopped pushing Mountain Lion. They’re outdated and, therefore, full of new security vulnerabilities. We now have more modern versions that are patched to keep up with the latest malware threats.
Outdated software doesn’t get those same security patches anymore. They are coded differently than today’s versions. Since these older versions don’t have patches to account for the latest threats, they become prime targets for hackers to try to break in. Upgrading to the current versions will slam the door right in the hacker’s face and make it much harder for them to get in.
How to tell if your social media account has been compromised
No matter what social media platform you use, your Facebook, Instagram, TikTok, or Snapchat can be hacked. Social media presents cybercriminals with the opportunity to steal data or financial information, spam and release malware, spy on you, and even create highly personalized phishing campaigns. Here are five main hacking signs for breached accounts.
1. Getting locked out
If you try to log in to one of your social media accounts and find out that your password is no longer working or that your account has been suspended or blocked, this is a clear sign that your account has been hacked. The first thing cybercriminals do when they breach an account is change your password and recovery options, including two-factor authentication. This locks you out of your account and gives them full control.
2. Unsolicited login notifications
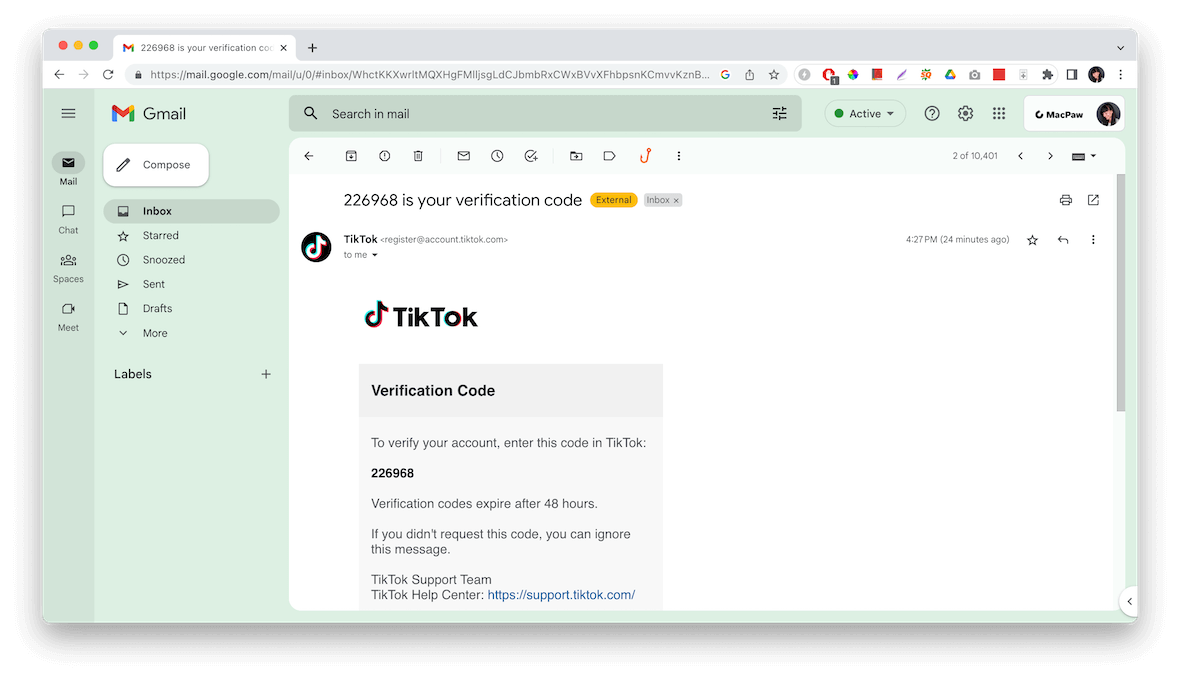
You might notice that you’re getting unsolicited push notifications asking you to verify access or emails warning you that someone is trying to log in to your accounts. These are all signs of hacking. Take immediate action, change passwords on other services, try to recover the account through official channels, and report the incident to support teams.
3. Strange and suspicious activity
Have you ever logged in to your social media and found strange messages or notifications? If that is the case, you should not ignore them. Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. If you see messages you did not send, new friends and contacts you do not know, or any activity you do not recognize, you should take these hacking signs seriously.
Signs your messenger account has been hacked
Slack, WhatsApp, Telegram, Zoom, and Microsoft Teams: the hybrid-work world has most of us living and working online at least part-time. Know the hacking signs to keep your messenger account safe.
4. Noise in the background
If you are making a call or attending a virtual team meeting and you hear static noise or other strange sounds in the background, it could indicate that someone else is on the line. However, not all spyware works perfectly, and some can create interference, revealing the bug. You should be asking yourself, “Am I hacked?”
5. 2FA requests from “friends”
Often, cybercriminals will spread through an entire network. They first hack one messenger account and later move on to hacking all the contacts in that account. To do this, they employ a simple but effective social engineering trick. They will contact you using an account of your friend or a close family member, which they hacked, impersonating them. Then they might ask you to accept a push notification, enter multi-factor authentication, make a call, download a link, or something else. Do not fall for clear hacking signs.
When a contact asks or approaches you with these types of messages, try to speak to them in person, face-to-face, or at least call them to confirm the story.
6. Random logouts and disappearing data
If you notice that you keep having to log in to your account, it could be a sign that someone else has been logging you out in an attempt to gain access. It’s also possible that you’re just having one of those days when the network glitches and your messenger app logs out repeatedly. But if you log in and see missing messages, files, or contacts, this should raise a red flag. Secure your account.
7. Spam messages and calls
Your account is sending out a massive amount of spam. You’re seeing calls you did not make. And strange, unknown contacts are talking to you. This is about as clear as hacking signs get. Don’t just write this off as the app “acting weird.”
How to tell if your phone has been hacked
Many users still wrongly believe that cybercriminals hack only computers. But these days, nothing could be further from the truth. As smartphones have become increasingly woven into our everyday activity, attacks on phones have increased exponentially.
8. Malfunctioning after a system, security, or software update
While you should always keep your smartphone’s operating system and software up to date, cybercriminals will often try to mimic official-looking update requests to install malware and viruses on mobile phones. If you recently installed new or updated software, and your phone is malfunctioning after it rebooted, take a close look at what you installed. You might be in for a surprise.
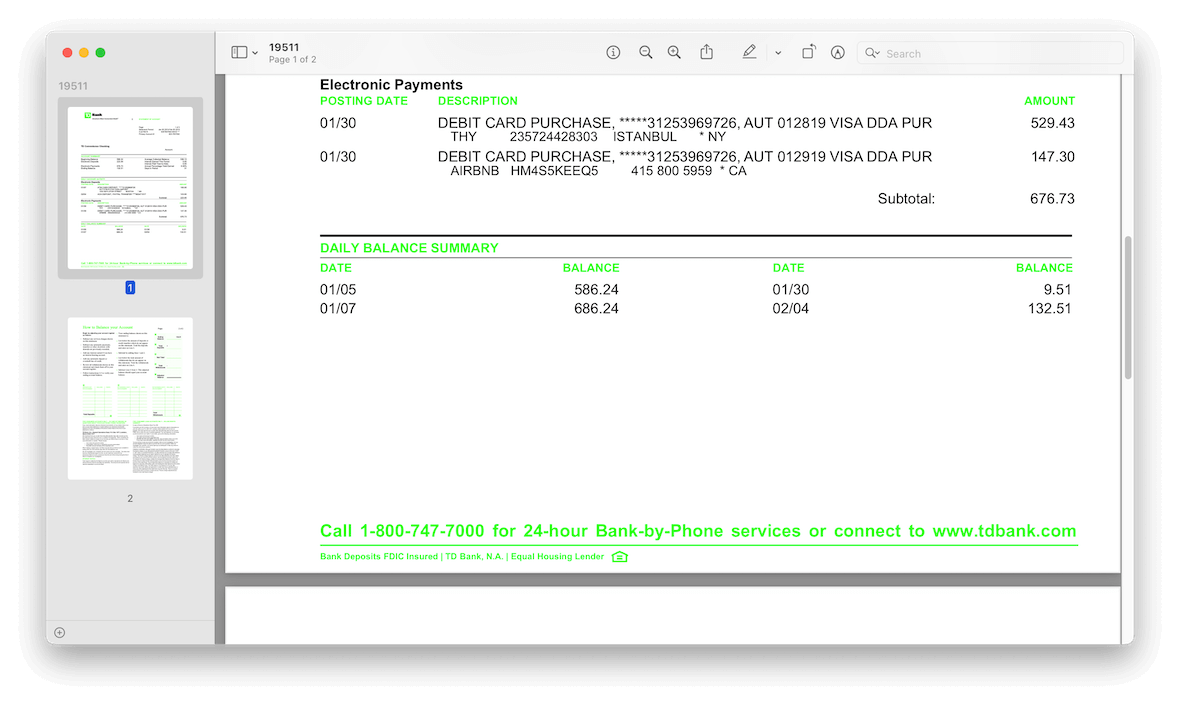
9. Unfamiliar payments on your bank statements
Did you get notifications about payments you did not make or see strange financial movement in your bank account, digital wallet, or credit card? Assume that a criminal has hacked your phone and stolen your financial information. And if this is the case, immediately notify your bank and digital financial services organization and try to shut the hacker out of your accounts. Always keep financial services information and passwords safe, and never store them on your phone or share them with strangers.
10. Overheating battery
The process of malware, spyware, or a hacker remotely using your phone will push its processing power beyond the limits. And when that happens, your battery will begin to heat up as if it’s been left in the sun. So always be cognizant of your phone’s battery. Is it hot? Has it been depleting more rapidly than usual? Does it take longer to charge? All of these issues could indicate that there’s some hacking going on behind the scenes.
11. Annoying pop-ups that won’t stop
Cybercriminals code adware to infect any kind of device, including your smartphone. The main goal of this type of malware is to show you a lot of ads. Meanwhile, the attacker reaps the economic benefits of distributing those ads. Not only is adware annoying, but it can be difficult to remove. Plus, it can affect your phone’s performance and even damage it or cause it to crash.
12. Messages and calls forwarded to an unknown number
A sophisticated and trending attack technique on smartphones is the use of International Mobile Equipment Identity (IMEI) codes. These codes can be used to forward your calls or SMS, receive your verification codes, and reset passwords on your accounts. If you notice that you haven’t gotten any calls or SMS messages in a while, or if you have been recently convinced to dial a code on your phone by a stranger, check your forward phone status. Simply dial *#004# to learn the status of all existing forwards on your phone number. If a forward is there that shouldn’t be, dial ##004# to erase all forwarding configurations for calls and SMS.
13. Unwanted browser redirects
Are you constantly redirected to sites you didn’t want to visit while surfing the web on your phone? You might mistakenly pass this off as an error at first. But it could also mean your phone is infected with a browser hijacker. While browser hijacking malware attacks used to be limited to computers, they now can infect Android and iOS systems too. There are several ways to solve this, including the use of antiviruses or doing hard resets. Always check the extensions and apps running on your phone, as one of them could be the culprit.
How to know if your computer has been hacked
Desktop computers and laptops are where most users tend to keep their personal and work information. They are the most powerful devices for working, creating, and sharing content and have the most storage capacity, so it’s easy to lose track of what is happening with your computer until it’s too late.
14. All of the above
All the aforementioned signs and methods used to tell if a smartphone, messenger app, or social media account has been hacked also apply to computers. If it crashes, the fans randomly turn on, the battery depletes quickly, or you notice suspicious messages, a hacker may be hitching a ride on your completer.
15. Ransomware messages
Nothing says “you have been hacked” like getting a ransomware message. If you think this can’t happen to you, you might want to check the latest stats on ransomware. CISA asserts that a ransomware attack occurs on average every 14 seconds. And the targets aren’t just small, medium, and large businesses — individuals are at risk too.
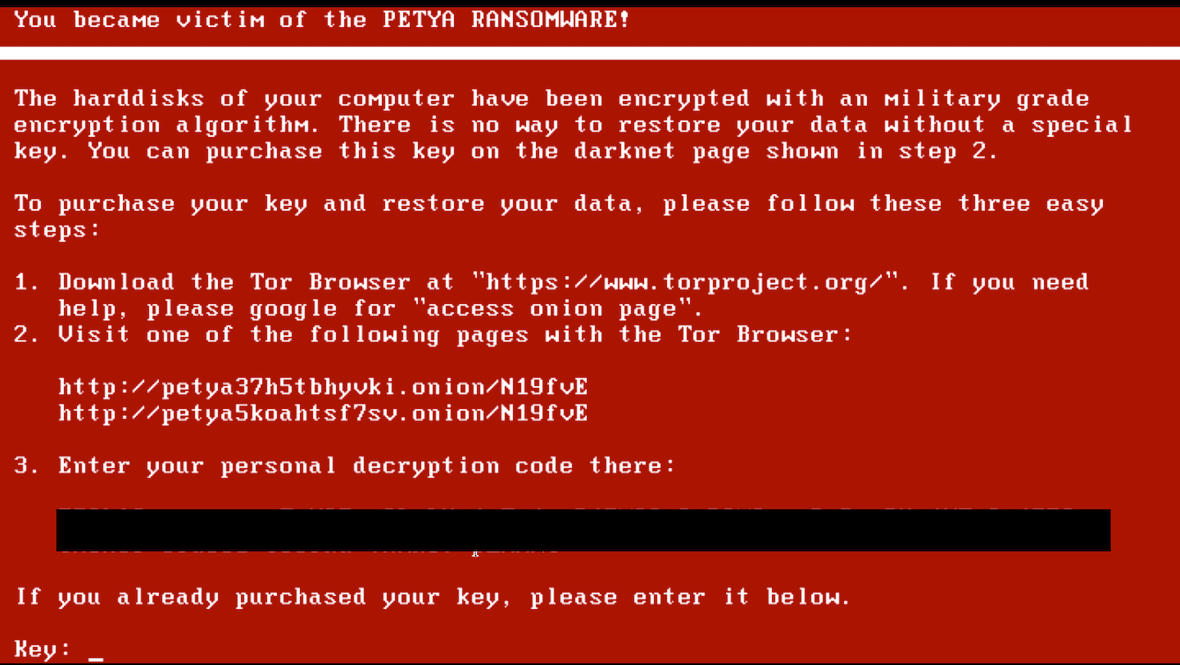
You should never pay the ransom, as it doesn’t guarantee that your data will be recovered, nor does it prevent hackers from leaking or selling your information. The best protection is prevention, a good malware solution, and recovery and backup.
This is where Moonlock can save the day. Its powerful scanning and protection capabilities can stop ransomware before it can encrypt any of your files. The System Protection feature will help you reinforce any weak points in your system, and the Security Advisor will give you hints and tips on how to build good habits around security.
16. Ads pretending to be antiviruses
As mentioned before, it’s common for users who have already been breached by adware to see an excess of online ads. Some ads will even pretend to be helpful antiviruses. They simulate a fast scan and give users warning messages claiming that the computer has been infected. If you are seeing an ad like this, it’s likely that you have already been hacked and that the malware installed on your computer is directing you to this site. Never believe messages from an antivirus you have not installed, no matter what it says. The solution? Use a trustworthy antivirus program to scan your computer for adware malware and clean up your browser extensions.
Signs your device camera or microphone might be hacked
Your device camera or microphone are 2 areas where you are the most vulnerable. But many people don’t realize this. They are so focused on the email and software threats that they fail to see easier ways right in front of them.
17. The camera light is on
If you’re not using the device camera/webcam but the light is on, then that means someone else/something else is using it. However, the light being off is no guarantee either. Hackers can now access your camera/webcam without triggering the light.
The answer to this is to have a webcam cover on the camera. So even if they do manage to gain access, all they’ll see is a black screen.
18. Unexplained photos and videos on your hard drive
If someone is indeed using your camera/webcam, then they could end up unwittingly activating the camera to take photos and videos. These may be sitting on your hard drive.
If you see any photos or videos that you definitely didn’t take, then get your device checked immediately for malware.
19. Your device slows down
Any kind of malware tends to slow your device down. This is because malware needs a lot of CPU and battery power to be able to function, which comes at the cost of your other apps.
In a way, this is good because an extremely slow device is the classic symptom of malware. So, in a way, the hacker is introducing themselves and letting you know they’re there. Now, proceed to show them the door.
20. Weird noises during calls
One symptom that the microphone is compromised and that your iPhone may be listening to you is weird noises. If someone else is on the line, eavesdropping on your conversations and background ambient noise, then they won’t be able to avoid making some background noise themselves.
How to tell if your email account has been compromised
Your email account is likely going to be the first port of call for a hacker trying to gain illicit access to your device. So, you should always keep one eye on your inbox to stamp down on any threats lurking about.
21. Your Gmail tells you there’s another login
Gmail has a helpful feature that tells you if your Gmail inbox is being accessed in another location. Just look at the bottom of the Gmail inbox, and you’ll see “Open in 1 other location” (or however many instances Gmail can detect.) By clicking on Details, you will be given information on the other connection.
It used to be that you could remotely sign out of these other sessions. But now, you have to change your email password to kick out whoever else is there.
Be careful, though. If you’ve authorized a third-party app to access your account, that will show as another visit. If you’re logged in on your iPhone or iPad, that will show as someone else, too.
22. Emails are showing up as being read
The whole point of a hacker gaining access to your inbox is to read your emails and see what useful information they can take from you. That means opening unread emails.
If you see emails that are opened but you haven’t read them, then you may have someone peeking over your shoulder reading them for you.
Of course, if the hacker has any sense, they will mark the emails as unread again. But they may forget to do it.
23. Emails are being deleted
Emails are only likely to be deleted by a hacker if they want to hide activity inside your account. This could be things like accessing your other accounts and deleting emails that arrive to tell you about that account access. Or maybe they’re impersonating you on Twitter, and they want any incriminating emails destroyed.
It’s easy to ignore your trash folder, but every now and then, sift through it. Is there anything there that looks suspicious?
24. New email filters are being created
If the hacker wants to hide any new emails arriving, they have another option other than manually deleting them. They can instead set up filters to automatically delete them or forward them to another email address.
So, as well as watching your trash folder, check your list of filters every few days. You can access Gmail filters here.
How hackers hide their presence on your device
Once on your system, hackers have to stay one step ahead of you and your antivirus software. Given how good antivirus software is these days, it’s a challenge for them to stay on your device for any reasonable period of time. But here are a few ways they manage to do it.
Zero-day exploits
A zero-day exploit is when there is a security vulnerability in the operating system, an app, or a piece of software that hasn’t been discovered yet. If nobody knows about it, then the antivirus software won’t be able to detect it. That makes a perfect hiding place for malware trying to keep a low profile.
Rootkits
Rootkits are insidious sets of malicious code that burrow their way into the core of the operating system and attach themselves to important files necessary for the system to function properly. Once that has happened, it is extremely difficult for antivirus software to find them.
VPNs
It’s ironic that we recommend a VPN to protect yourself, but a hacker can also use one to protect themselves! If you manage to find malware on your computer, tracing it back to the source is impossible if the hacker used a VPN to mask their real IP address.
Pretending to be a trusted app
One of a hacker’s favorite methods of helping malware evade detection is to name it after a piece of trusted software on your computer. Then, when you look at Activity Monitor and see something like gchrome36789, you may think it’s a legitimate Chrome process and ignore it.
What to do if you suspect you’ve been hacked
If you suspect that you’ve been hacked, there are some things you must do immediately. Put down the coffee and stop texting your friends. Do the following.
Disconnect from the internet
The first step is to cut the head off the snake. This means preventing the malware on your device from communicating with headquarters — in this case, the external server that your data is being sent to.
By disconnecting, you’re stopping any further information from leaving your device.
Run antivirus software

You will now want to scan your Mac in depth to make sure that you remove any existing threats that may have found their way onto your computer. With Moonlock, a Deep Scan will find any hidden or dormant threats and quarantine them immediately.
Use a Deep Scan to protect your Mac with Moonlock. Here’s how:
- Start a free trial of Moonlock and download the app.
- Find the Malware Scanner.
- Run a Deep Scan.
- You can run a one-time scan or set a schedule for scans in the future as well.
- Once the scan is finished, review the results.
- Everything that was found was immediately quarantined, so you don’t have to rush to delete anything.
- Try to see if there are any clues in file names, etc., that could point to where the files came from.
- Delete everything that the scan found.
- Enable real-time protection and background monitoring to stay protected.

Change your passwords — on another device
While the antivirus is running, hop onto another device (preferably one that’s not on the same network in case the entire network is infected) and start changing your passwords. For example, if you think your email is compromised, change that one. And enable 2-factor authentication if you haven’t done so already.
If you don’t know what has been infected, hold off on changing the password for the moment.
Wipe and reset your device to factory settings
Once the antivirus has found what was on your device, quarantined it, and dealt with it, you may be OK. Then again, you may not be. How do you know that Moonlock Engine got it all? It likely did, but what if it didn’t? Many new sophisticated viruses appear all the time, and one of them may have outwitted the antivirus software.
For complete peace of mind, it would be best to wipe the device and reset everything to factory settings. Granted, it’s a huge pain to do it, but you can be sure that every single trace of the malware will be gone afterward.
Before you hit that button, though, make sure you create backups of important files. Once the wiping process starts, you won’t be able to get those files again.
Hacking is becoming a more and more serious problem. But with the right amount of reliable information out there, computer and smart device owners can educate themselves on what to look out for and how to take decisive action.






