A rootkit might sound like something you would need to consult a dentist about. But in fact, it’s actually a form of malware that can steal your data, make a mess of your computer, and ruin your day. That’s why we’re going to show you how to detect a rootkit — and eliminate it.
What is rootkit malware in cybersecurity?
A rootkit is a form of malware that buries itself deep into the inner workings of your device. By delving down to the kernel of your Mac (the component that manages the Mac’s hardware), it gets its claws into all the functions of your machine, making it difficult to detect.
How it gets onto your Mac can vary. It can be part of a trojan, or you may unwittingly download it yourself via an infected link or other malware, which then introduces the rootkit to your machine.
What is the purpose of a rootkit, and how do hackers use it?
What is a rootkit’s “mission,” and how do their owners use it?
- Soon after jumping onto the target device, the rootkit buries itself deep inside the Mac’s hardware. It’s deliberately designed to be elusive.
- It then escalates its user privileges so it has administrator privileges, giving the hacker complete control over your machine.
- Once it’s taken control, it can do a lot of damage to your system, such as taking remote control of your system, installing more malware, stealing your data, logging keystrokes, and serving up ads.
How to detect rootkit malware
In order to detect rootkit malware, you should ideally use a specialized rootkit scanner. A rootkit attack is not something you want to happen to you, so detecting it and knowing the signs of one is an important priority.
Check for a rootkit using a rootkit scanner
You’ll need to use a rootkit detector to find this type of insidious malware. This is the only way to guarantee a thorough and effective rootkit scan that will flush out any threats hiding inside your Mac.
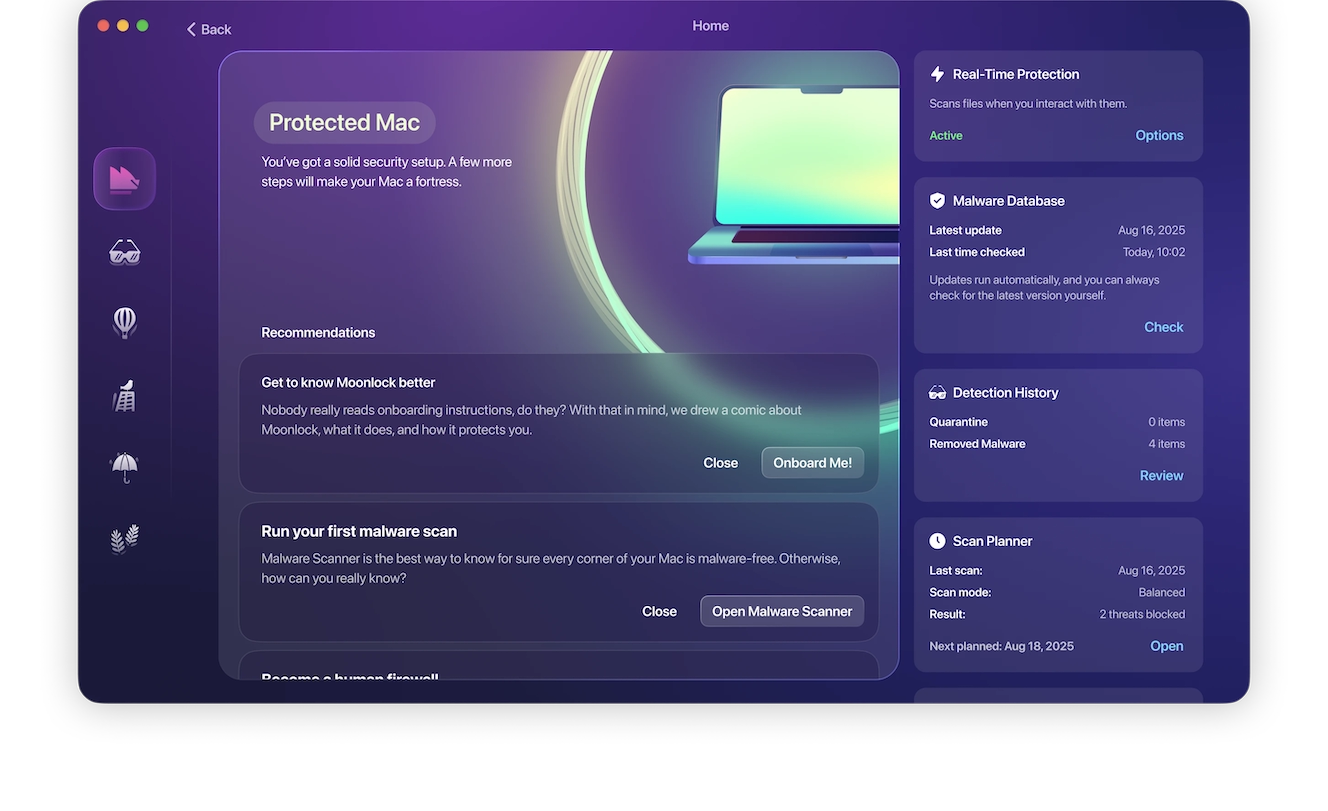
One example of a rootkit scanner is Moonlock. It’s a powerful, lightweight, and fast malware detection tool that will leave no stone unturned.
Later in the article, we’ll dig deeper into how to use Moonlock.
How to identify the signs of a rootkit attack
Before you start using Moonlock, you should learn how to identify a rootkit attack on your device. Here are a list of signs to look out for:
- Your computer is slowing down: Check the Activity Monitor to find the programs that are consuming the largest amount of CPU and memory.
- Your computer is overheating: Any type of malware will overtax the Mac’s battery. This will lead to it heating up. This should not be ignored, as prolonged heat will eventually damage the battery.
- Your Wi-Fi network is starting to crash: A spotty Wi-Fi connection is usually nothing to worry about. Maybe you’re in a dead zone, or your internet service provider is experiencing some downtime. But, on the other hand, it could also indicate that rootkits have taken over and are moving your data out to third-party servers.
- The device settings have been changed: Upgrading to administrator permissions means a hacker can do a lot with your Mac. They can install apps, disable the firewall, disable Gatekeeper, turn off FileVault, and much more. If you notice that things have been changed, don’t shrug it off. Check it out.
- Strange system events: This can be anything from the mouse cursor moving, files appearing and disappearing, new user accounts being set up, and so on.
How to remove a rootkit manually or with a rootkit remover
Now, let’s get down to rootkit removal. The best and fastest way to do this is to use a rootkit scanner and remover like Moonlock.
How to remove a rootkit using a rootkit removal tool
Moonlock is the best option because, as we said, a rootkit virus is designed to be elusive. By digging deep into your system, it makes itself extremely difficult to remove manually.

- Sign up for a free trial of Moonlock.
- Download the app and launch it.
- Select Malware Scanner on the left. This opens the antivirus removal tool.
- Before scanning, select Configure in the dropdown menu. This will open up the scan settings. Make sure every feature is enabled.
- Set the scan mode to Deep. This will help Moonlock reach all the nooks and crannies of the kernel.
- Close the settings window and click the Scan button. Moonlock will methodically scan all areas of your Mac, looking for the rootkit and any files associated with it. It may very well find other threats you were not aware of.
- When the scan is finished, everything it’s found will be neutralized and locked away in Quarantine. Select it all and click the Remove button.

But it’s not over yet. We recommend that you schedule regular deep scans that will run automatically. Make sure no stealthy rootkit hides among your files in the future.
By this stage, the rootkit should be gone. Restart your Mac and make sure everything boots up as it should.
How to manually remove a rootkit from your Mac
Choosing to wing it is not the best way to get rid of a rootkit. There are just so many areas of the device where it can be, and identifying each malicious file can be long and tedious, with no guarantee of success at the end.
This is why we strongly recommend that you use a dedicated rootkit removal tool. But if, for any reason, you can’t use a software option, here’s how you would do it manually.
Boot into Safe Mode
Booting your Mac in Safe Mode limits the system to the bare essentials. This prevents the rootkit from operating.
To enter Safe Mode:
- Turn off your computer.
- Hold the power button down until you see Loading Startup Options.
- Select your startup disk.
- As the Mac is booting up, hold down the Shift button. Now select Continue in Safe Mode.
Use Activity Monitor to find suspicious programs
Open Activity Monitor, filter the largest running processes to the top, and force-quit any that look suspicious. If you’re not sure, run a web search for the name of the process.
Run 2 commands in Terminal
Open Terminal and enter:
/Library/LaunchDaemons/Look for any suspicious names and delete them. Again, run a web search for any names you’re not sure of.
Now type:
/Library/LaunchAgents/If you find anything that looks suspicious, delete it.
Make sure System Integrity Protection (SIP) is on
If SIP is disabled, it gives the rootkit the power to change system files, so you need to make sure it’s on.
Open Terminal and type:
csrutil enableNow, restart your Mac normally to exit Safe Mode.
Consider wiping and reformatting your Mac
If you still see signs that a rootkit may be present on your system, the only other option is to wipe and reformat your Mac back to factory settings.
How dangerous can rootkits be?
Besides being very difficult to find, rootkits can be very dangerous. Here’s why:
- They take full control of your system: Rootkits give themselves administrator rights and remote access to hackers. Among other things, they can spy on you through the webcam.
- They will steal your data: Data stolen by rootkits can easily lead to identity theft and credit card fraud.
- Your computer can be used for espionage: By controlling your computer, a rootkit can make your machine part of a botnet to launch distributed denial of service (DDoS) attacks. Rootkit attacks on company networks can steal trade secrets.
How to prevent rootkits from infecting your Mac
Here’s a list of tips to stop rootkits from getting onto your Mac.
Think before clicking weblinks
Malware-infected weblinks represent the main way hackers get you to install malware onto your device. Never click on links in emails or SMS messages sent from people you don’t know or don’t fully trust.
Keep antivirus running at all times
Moonlock, for example, checks every file and app you click, open, or download, immediately recognizing and isolating malicious ones. Such protection in real-time nips malware advances in the bud, so it’s essential to keep your antivirus on at all times.
Keep macOS and apps updated
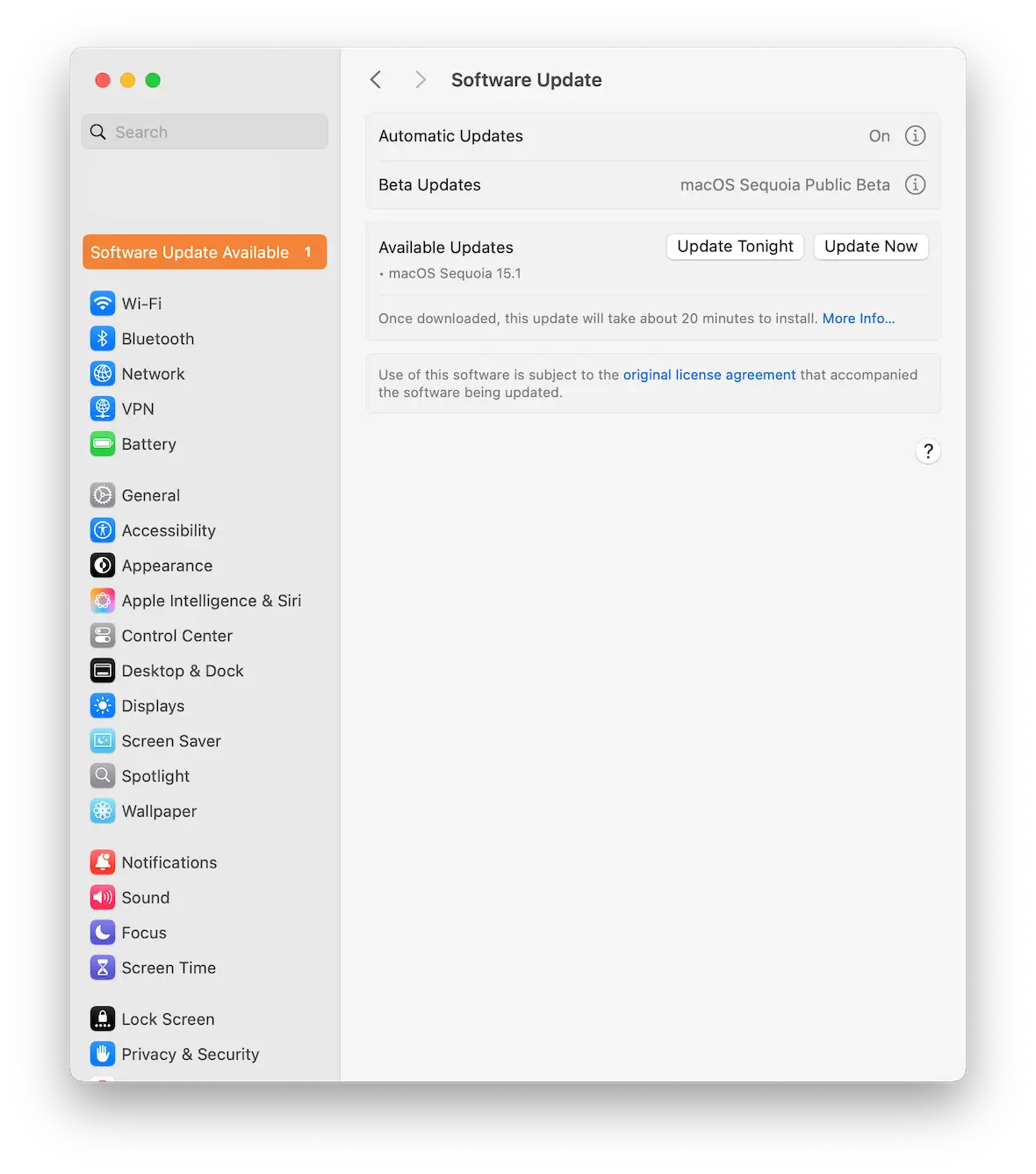
Always update your macOS and apps with the latest security patches. Just go to the General tab in Settings and select the Update section.
Avoid downloading anything from outside of the App Store
Try your best not to download software or apps from outside the Mac App Store or a trusted third-party developer. Doing so increases your chance of downloading software with a rootkit or other malware hiding inside, just waiting to get out.
Turn on 2FA
Turn on 2-factor authentication on all your accounts for an added layer of security. Prioritize your Apple ID account and your email. Use an authenticator app on your phone instead of text messages. Texts can be easily intercepted.
Change your account passwords
If the hacker has managed to get inside your machine, they will more than likely have installed a keylogger. This means that your login details for online accounts will likely be known.
In addition to 2-factor authentication, change all your passwords. Yes, all of them. And don’t store them in your browser password manager. Instead, use an offline password manager such as 1Password or LastPass.
A rootkit, like other types of malware, can cause immense havoc and steal your personal data. But by knowing what a rootkit is and what it looks like, you can be ready to deal with one before it can strike.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.