One thing you can say about cybercriminals is that they never stop innovating. Bad actors are well aware of how antivirus platforms work, and some are now shifting their tactics when it comes to malware. In response to the increasing effectiveness of antivirus platforms that track malware-infected files, attackers are pivoting to fileless malware.
So, what happens when the malware doesn’t rely on infected files? How can you find malware if there’s no infected file to track? In this article, we look at fileless malware, how it works, and how to remove it before it spreads.
What is fileless malware, and how does it work?
When it comes to a fileless malware definition, unlike regular malware, it spreads without the need for an infected file to get onto the target computer. This makes it extremely difficult for antivirus platforms to find the malware because there is no infected file to look for.
Therefore, this type of malware relies on non-file methods, trusted tools that the victim won’t suspect and will usually open without a second thought. It will then bury itself in the system’s RAM.
Fileless vs traditional malware: What sets them apart?
Traditional malware, such as trojans, RATs, adware, and ransomware, only work if the hacker can persuade someone to put the infected file on their computer.
Fileless malware doesn’t rely on the victim downloading a file. Instead, attackers use trusted programs with embedded malware to get inside the target computer. When someone uses the infected program, it opens the door for the malware to jump in and do its work.
In other words, fileless malware is the complete opposite of traditional malware. This requires that antivirus platforms radically change how malware is detected.
What makes fileless malware so difficult to spot?
Detecting fileless malware is difficult because it doesn’t play by the same rules as traditional malware. As we’ve said, traditional malware relies on a file of some kind to transport it onto the target device. That can be an infected PDF, cracked software, or a malicious app.
Fileless malware requires none of the methods listed above. This means that when the antivirus starts scanning system files, it can’t find any malware because the malware isn’t connected to a file.
By piggybacking on a trusted app or software, there’s no indication that malware even entered the system in the first place because it stays in the device’s RAM and not on the disk.
How to detect fileless malware before it spreads
So, if fileless malware is so good at hiding from antivirus tools, what’s to be done?
Dealing with fileless malware is tougher than usual — especially on a Mac, since the areas where it hides are places where Apple’s security tools don’t look at very closely.
Fortunately, there are fileless malware detection methods if you know what to look for. The issue is that a lot of them involve scripts, which may be a bit too complicated for casual Mac users.
Keep an eye on script tools
As we’ve indicated, scripts such as AppleScript are big favorites for fileless malware attacks. In order to catch the malware in the act, you need to monitor all running scripts.
A major red flag is if a script called osascript (AppleScript) is started by Terminal. If this happens, you have a serious fileless malware problem.
Apart from osascript, other scripting processes affected include:
- Bash, zsh, curl, wget, scp, and sh (Terminal commands)
- Python, Ruby, and Perl programming languages
- Open (a command used to launch app bundles and scripts)
These processes and commands can be monitored by the LuLu firewall, which is arguably better than the macOS standard firewall.
Watch outbound network connections on the firewall
If you use LuLu, you can see all outbound connections attempting to connect to the outside world. If any of them are script-based (curl, wget, python, or osascript), these should be stopped.
Suspicious Automator workflows and app files
Sometimes, the malware can be attached to Automator workflows and app files. Keep watch for new app files and new .workflow files appearing on your desktop. If you’re unsure of them, run this code in Terminal to check them.
codesign --verify --deep --strict --verbose=4 [path to app]Monitor LaunchAgents and LaunchDaemons for changes
The other major thing you need to monitor as much as possible are the LaunchAgents and LaunchDaemons at /Library/LaunchAgents/ and /Library/LaunchDaemons/ in Finder.
If the malware hides inside a corrupted plist file, you should see malicious ones with Base64-encoded strings and mentions of osascript, bash, or curl commands. Those should be nuked immediately.
Check Activity Monitor for strange CPU surges
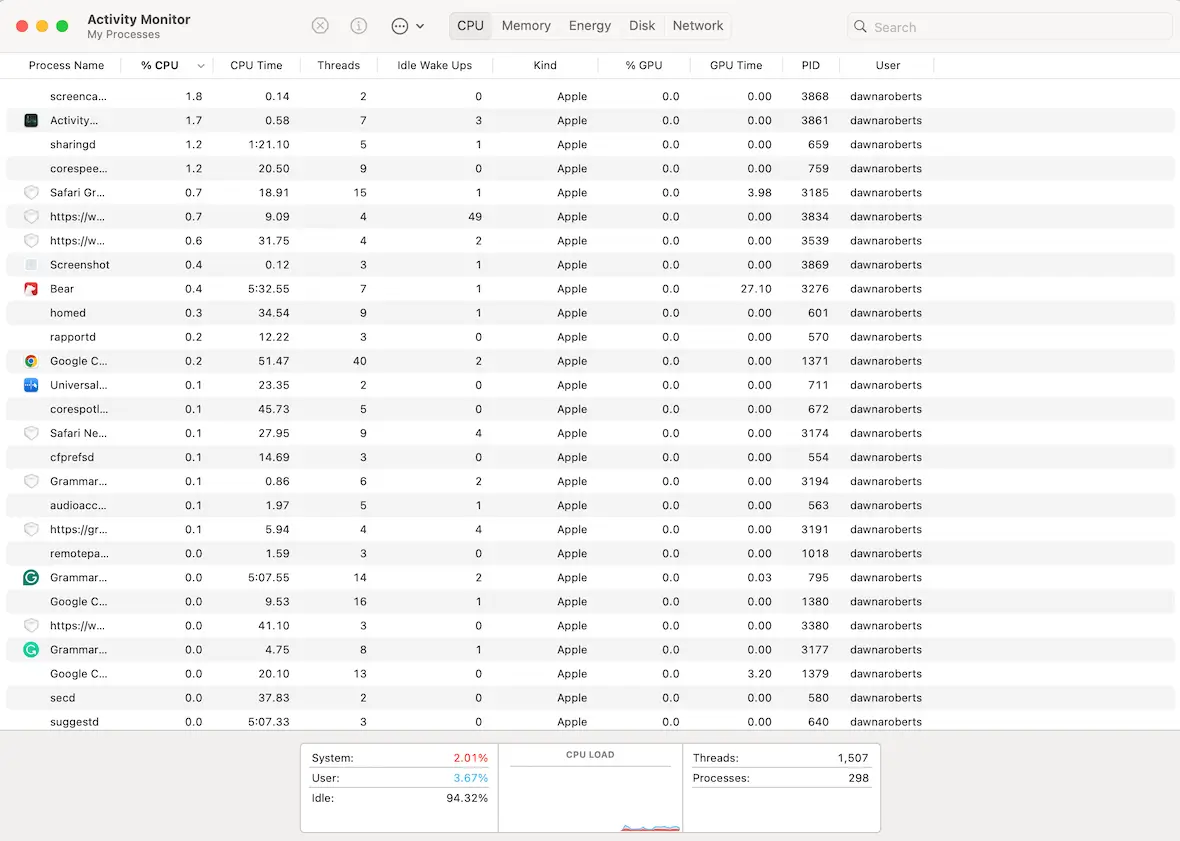
Scripts will appear in Activity Monitor, along with the amount of CPU they are taking up. If any script is running at a high level (70% or up), run a web search for its name to learn more.
If it isn’t a legitimate script, force-quit the script in Activity Monitor.
How to remove fileless malware from your system
If you’re absolutely certain that you have fileless malware on your Mac, you need to act without delay to remove it. After cutting off your internet, here are your options.
Find active scripts running certain processes
Run the following command in Terminal.
ps aux | grep -E 'osascript|curl|python|bash|sh|ruby|node'This will show you any scripts running with those processes. If anything looks suspicious, force-quit them.
Next, check the LaunchAgents and LaunchDaemons folders. You can do so by navigating to these folders in Finder.
~/Library/LaunchAgents/
~/Library/LaunchDaemons/
~/Library/Application Support/Look through them. If any are unrecognizable, have weird names, or have strings of numbers, delete them.
Use security tools
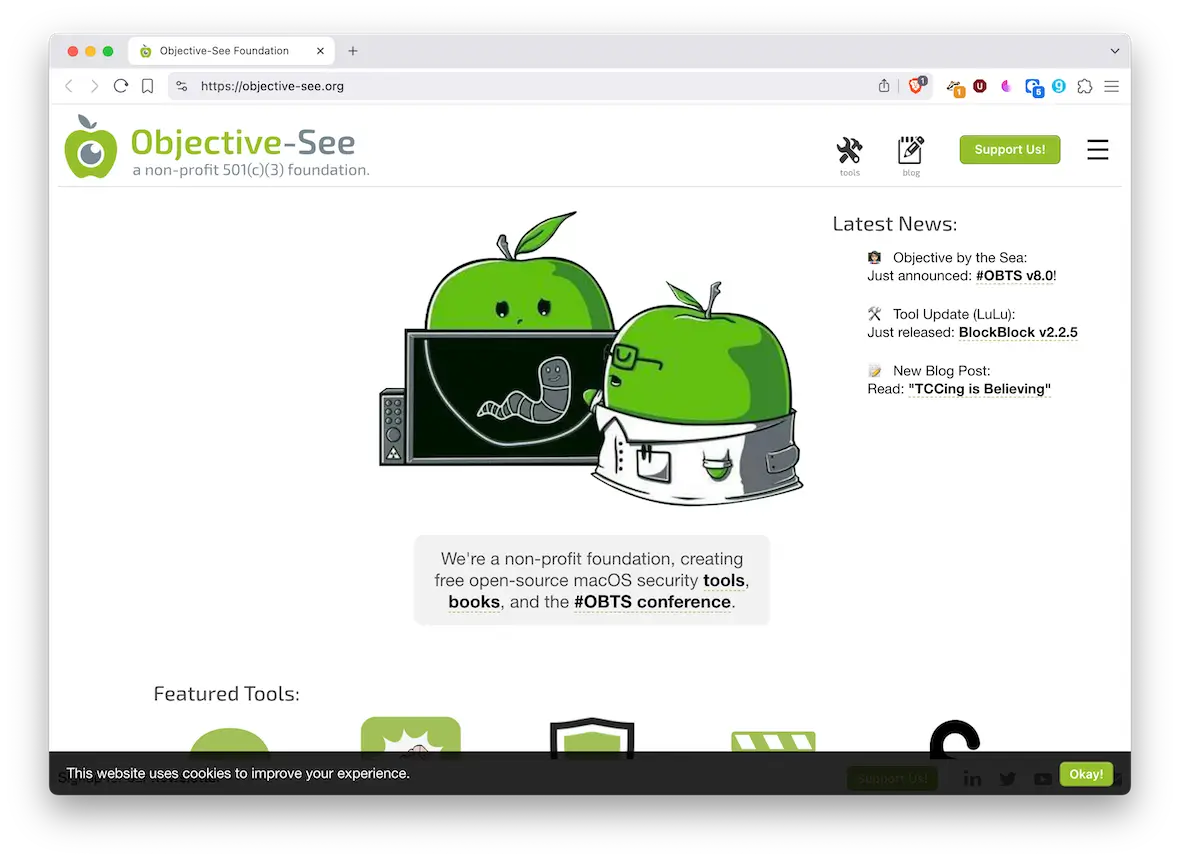
Go to Objective-See and download BlockBlock and KnockKnock. The former detects auto-start malware, and the latter gives you a complete list of startup items.
Wipe and reformat your Mac
The last resort — and possibly the best option — is to simply wipe and reformat your Mac. Luckily, Apple has streamlined and simplified this process.
Check out our complete guide to wiping and reformatting a MacBook.
Types of fileless malware, techniques, and real-world examples
Let’s now dive into fileless malware examples, types, and techniques.
Injection techniques of fileless malware
Fileless malware injections commonly happen when they hijack another process. In this way, they can be compared to trojan horse viruses, which hide inside other programs.
Here are a few of the places where fileless malware usually hides:
- The most common place is macros, such as in word processing tools. They emerge through the use of scripts like AppleScript or the “bash” command on Terminal.
- AppleScript can be abused in other ways, such as automating infected system events to open infected web links and download malware.
- JavaScript for Automation (JXA) is what Apple uses to connect JavaScript with macOS. This can put keylogging malware on your device.
- Users can be tricked (otherwise known as social engineering) to go to websites such as GitHub or Stack Overflow and run a Terminal command on that page. This downloads malicious scripts that go straight to the machine’s RAM.
- Launch agents and launch daemons can hide inside an infected plist file inside the Finder library.
So, in other words, the top 3 Apple apps and processes that are targeted are Terminal, Automator (for Apple Scripts), and launch agents/daemons.
Examples of real-world fileless malware in action
All of this may sound abstract and academic, so we’re now going to show you 3 macOS fileless malware attacks that actually happened. Most instances are Windows-based, but we’ll focus solely on Mac incidents.
We should note, though, that these incidents are not 100% fileless. In many cases, attacks utilize hybrid malware, as they use fileless techniques to spread but exhibit some traditional malware techniques as well:
- DarkHotel (2007–present): Targeting high-profile targets in Asia who are staying in hotels, this malware uses insecure hotel wi-fi networks and attaches itself to operating system and app updates.
- Cobalt Strike (2012–present): This is actually a legitimate piece of Windows software for ethical hacking and penetration testing. However, hackers have adapted it for Mac, using SSH and AppleScript. The attacks must first be made on a Windows machine, and then they use remote Windows tools to jump onto the Mac.
- OSX.Dok (2017–present): OSX.Dok passed around infected zip files that, when opened, released malware. It had a valid Apple developer certificate, which meant it wasn’t stopped by Gatekeeper. It then disguised itself as a system update prompt, where it stole the user’s administrator login credentials.
How to effectively prevent malware attacks
There are various things you can do to prevent fileless malware attacks from happening or at the very least reduce the risk.
Run anti-malware scans

Malware comes in all shapes and sizes, and it often hides in your system and personal files, making it hard to find using manual means. If you suspect your Mac is infected with malware, your best bet is to run an anti-malware scan.
You can sign up for a 7-day free trial of Moonlock and run a Deep Scan to clear up your Mac of all sorts of threats:
- Open Moonlock, then click on the Malware Scanner tab from the left sidebar.
- From the drop-down menu, click Configure. This is only necessary for your first scan, helping Moonlock understand which files you’re looking to check.
- In the new settings window, under “Scan type,” you can choose between Quick, Balanced, and Deep scan. You’ll find each scan’s Speed, Depth, and Purpose outlined right below it.
- If you choose Deep Scan, which we highly recommend, you can opt to include archives, disk images (DMG), and packages (PGK) in your scans.
- Once you’re happy with your scan configuration, exit the settings window.
- Back at the Malware Scanner tab, click Scan.

Moonlock will carefully and methodically search through your Mac, looking for any threats that might be lurking. If it finds anything, it’ll immediately isolate it in Quarantine, stopping it from interacting with your system. Once the scan is complete, Moonlock can fully remove any malware it finds from your device.
You can also schedule regular Deep Scans using Moonlock’s Scan Planner. That way, you won’t have to worry about remembering to manually conduct the scans yourself. After all, your best defense against malware is to act quickly and early.
Enable System Integrity Protection (SIP)
System Integrity Protection (SIP) locks down the most sensitive areas of the Mac to stop you — and malware — from accessing and tampering with them. Malware would have to disable SIP before it could damage core aspects of macOS.
It’s important to note that SIP is enabled by default on all Macs but can be disabled, so it pays to check.
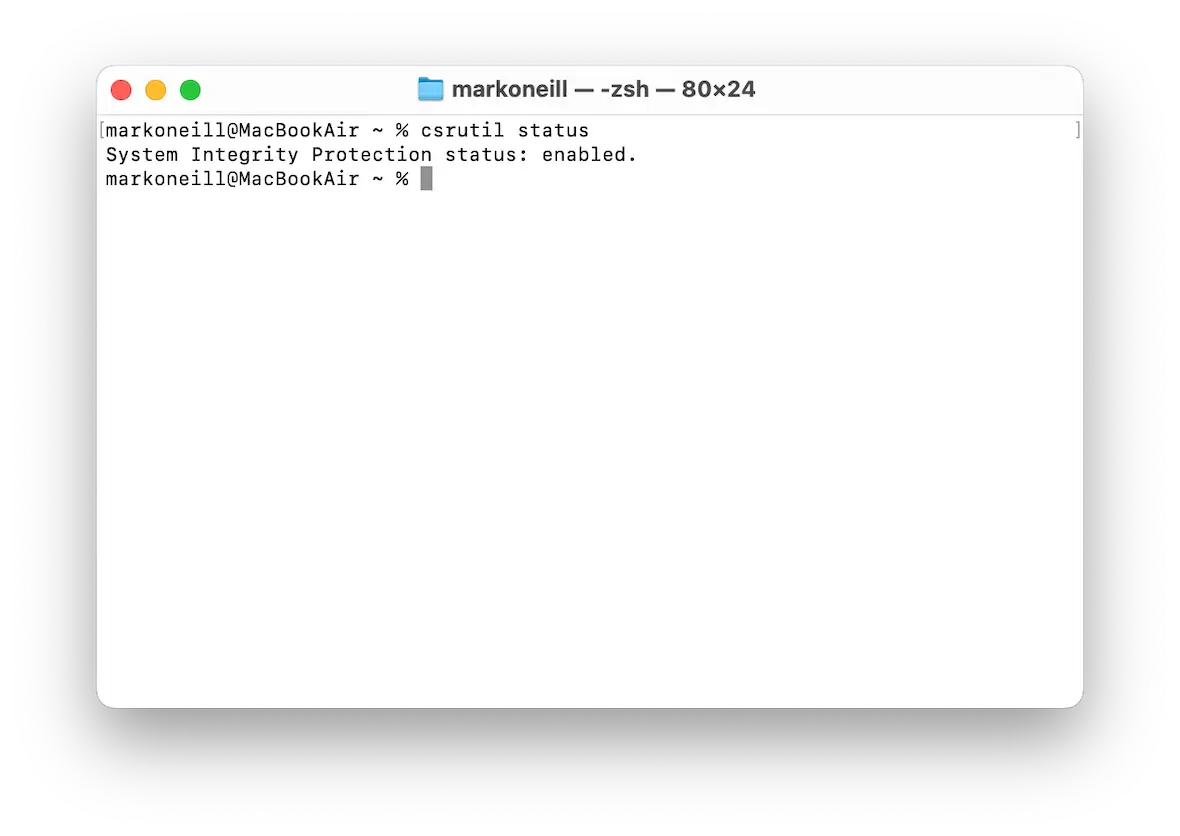
To see if SIP is enabled, open Terminal and type:
csrutil statusIt will then say either “enabled” or “disabled.” If it’s disabled, enable it again immediately by booting the Mac into Recovery mode. Then open the Terminal and type:
csrutil enableNow, reboot the Mac, and SIP will be enabled.
Make sure all Mac security tools are enabled
Mac provides free, robust security tools for your device. Some are enabled by default, but others, such as the firewall, need to be enabled:
- To enable the firewall, go to System Settings > Network > Firewall.
- To tighten Gatekeeper, go to System Settings > Privacy & Security > Security and choose your preference for what apps are allowed.
Check your security settings using Moonlock’s System Protection
Being part of the Apple ecosystem, you automatically have access to a wealth of built-in security tools and features designed to keep your Mac safe from threats.
If you’re not particularly tech savvy, you can sign up for a free trial of Moonlock and use its System Protection module to configure all the settings for you, optimizing them for maximum protection and privacy.
Be wary of macros
Macros perform valuable functions by automating various tasks, but they are also used by hackers to hide malware.
You can download macros from the internet, but we strongly advise against this. You don’t know where they came from or what they contain.
Create a malware radar using AppleScript
By utilizing a helpful script, it’s possible to create your own “malware radar.” This is done by creating an AppleScript in Automator that will scan your plist files for any suspicious changes. Fortunately, it’s easy to make.
Open Terminal and copy/paste:
mkdir -p ~/MalwareRadar
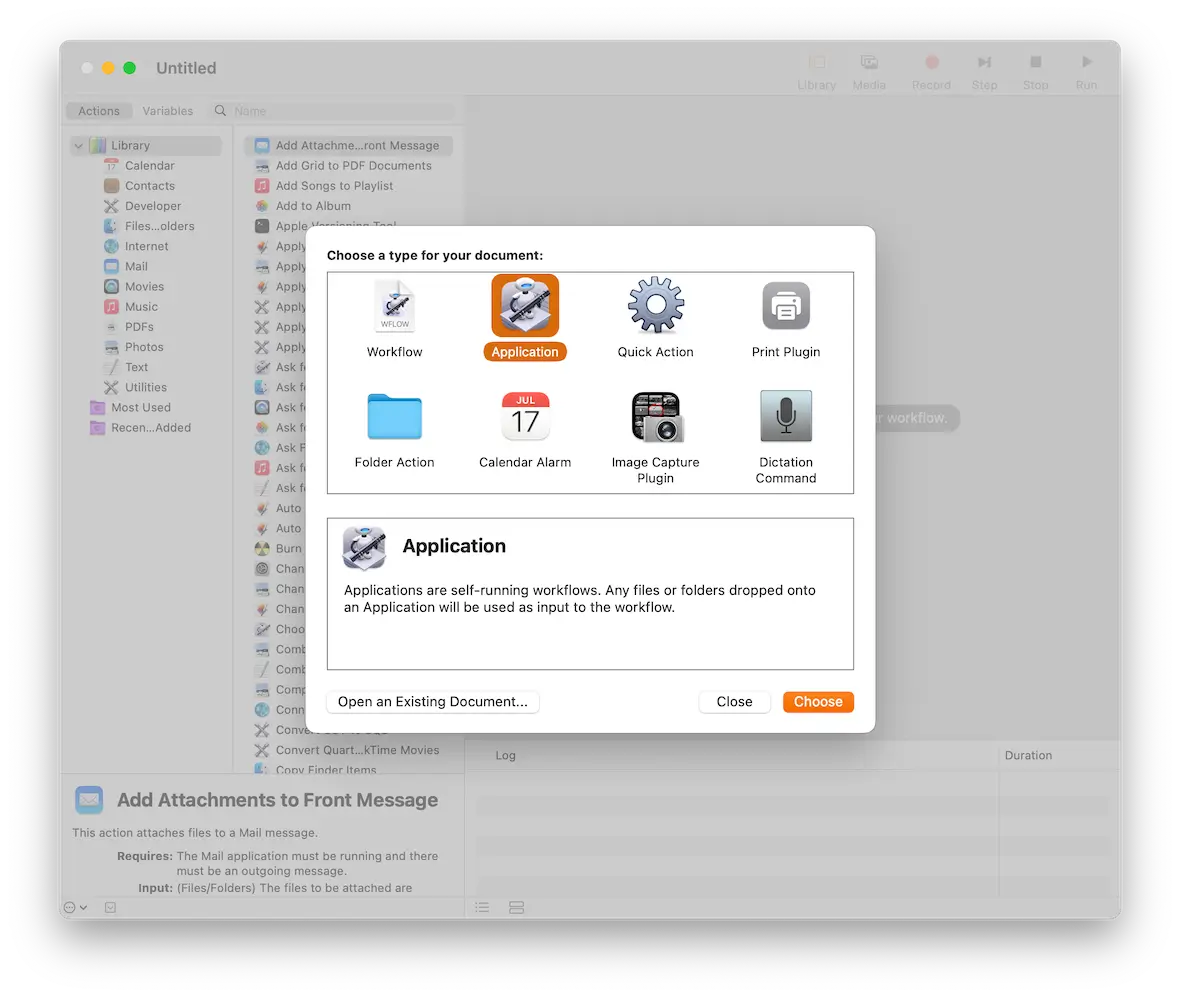
launchctl list | awk '{print $3}' | grep -v '^-|Label' | sort > ~/MalwareRadar/baseline.txtNow open Automator (in your Applications folder). When it opens, select Application.
In the left-hand sidebar, look for Run Shell Script. Then drag it over to the main window.
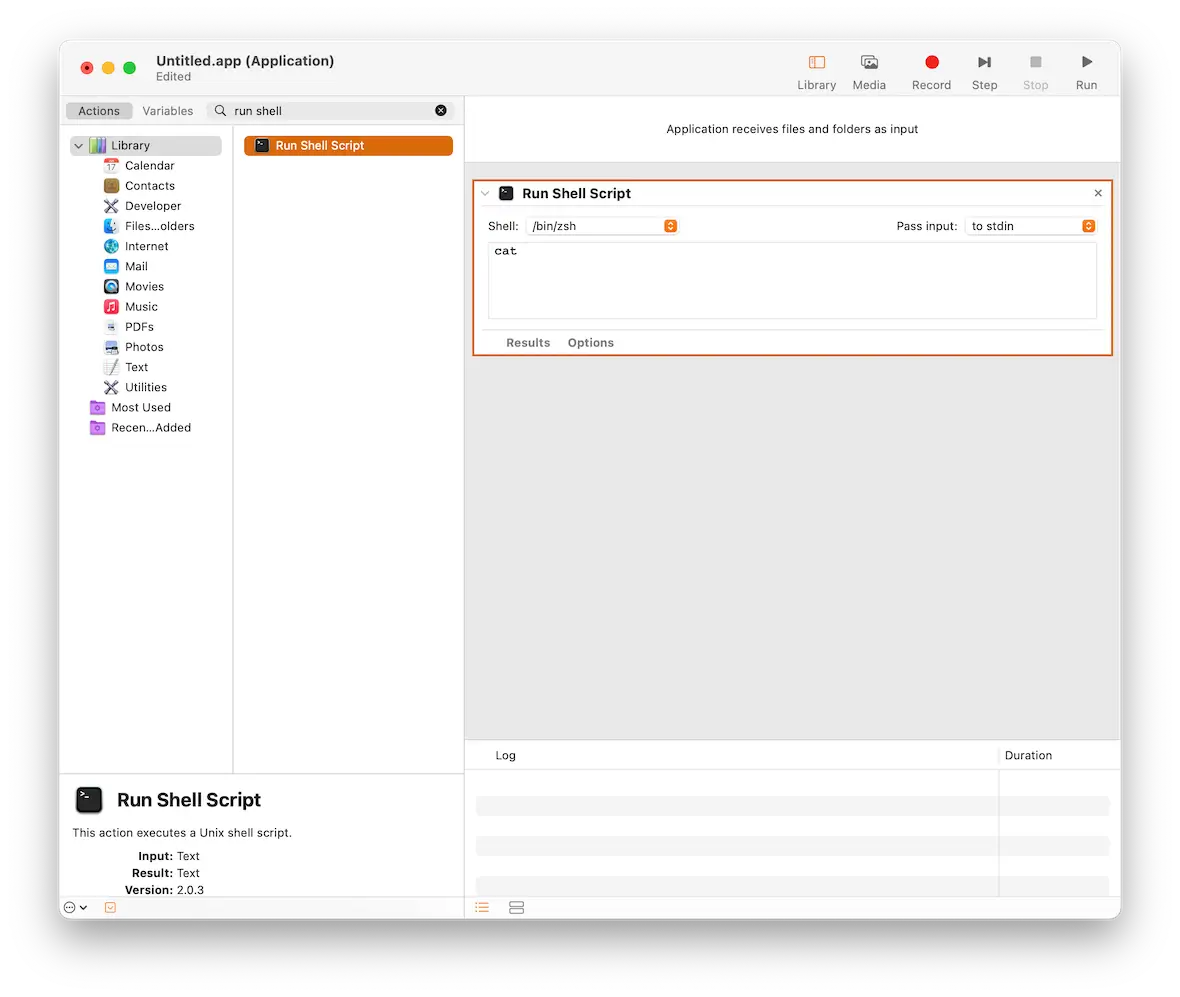
In that box, copy/paste the following text:
#!/bin/bash
baseline=~/MalwareRadar/baseline.txt
current=/tmp/current_launch_items.txt
log=~/MalwareRadar/malware_radar_alerts.log
# Create MalwareRadar folder if missing
mkdir -p ~/MalwareRadar
# Get current list
launchctl list | awk '{print $3}' | grep -v '^-|Label' | sort > "$current"
# Compare with baseline
diff=$(comm -13 "$baseline" "$current")
if [[ ! -z "$diff" ]]; then
echo "[ALERT] $(date)" >> "$log"
echo "$diff" >> "$log"
echo "------------------" >> "$log"
osascript -e 'display notification "New launch item detected!" with title "Malware Radar Alert"'
else
echo "$(date): Clean scan." >> "$log"
fi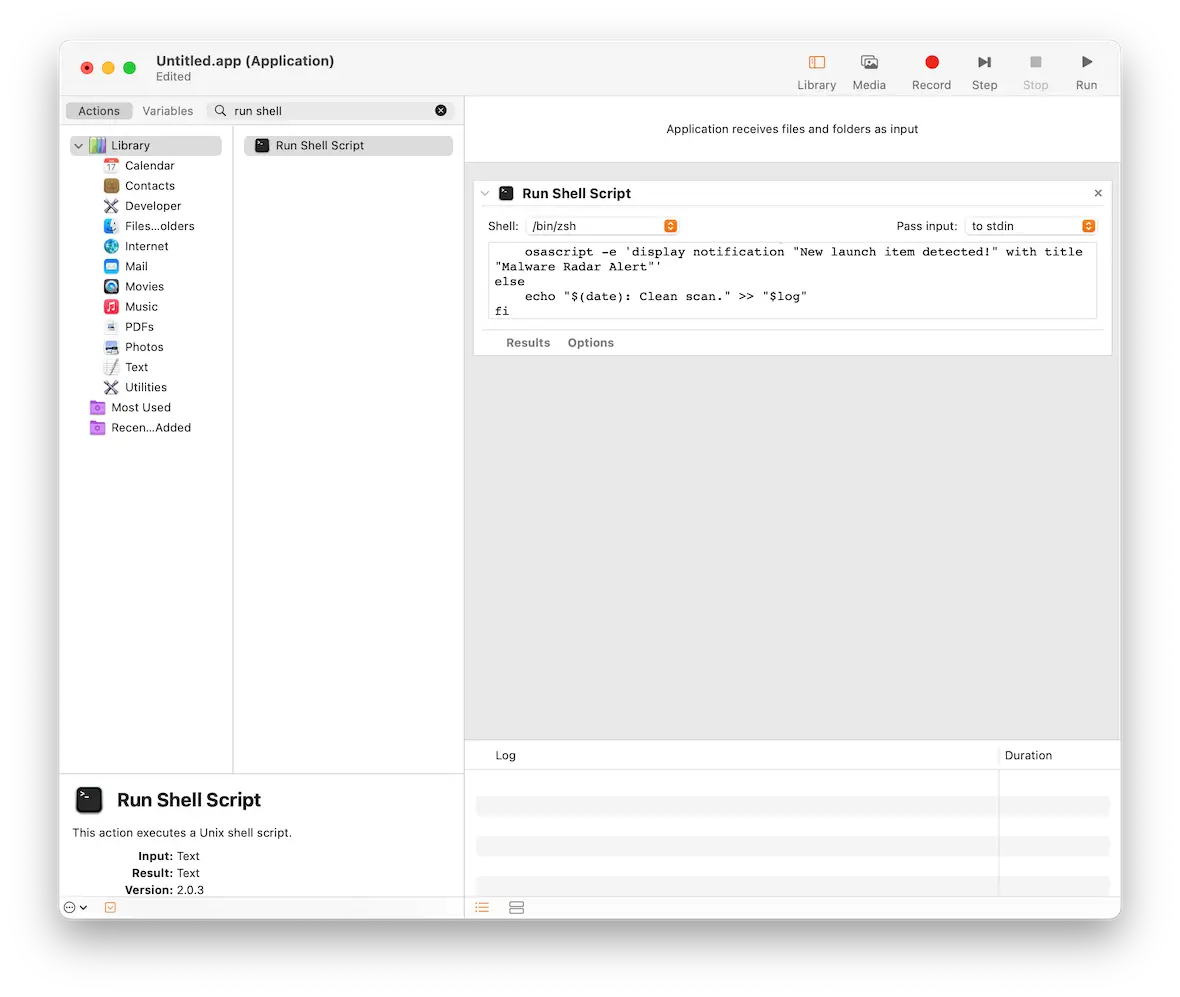
Save the script as Malware Radar.app and put it on your desktop.
Now, all you need to do is double-click it. It will check your plist files and write the results to a log file in /Users/yourMacName/MalwareRadar.
When it comes to fileless malware, the usual cybersecurity rules also apply. Don’t click unknown links and don’t download any unrecognized software or macros.
The steps to detect and remove fileless malware are causing a major headache for antivirus platforms. However, there are methods to track them, and new techniques will likely evolve in the future.
Scripting may be off-putting to Mac users who are not tech-minded, so it may help to have a knowledgeable friend or relative to help out.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac, MacBook, and macOS are trademarks of Apple Inc.