Have you ever been browsing the internet when suddenly a pop-up came out of nowhere telling you in bold that your computer was “infected”? Or have you ever come across a site that triggered an “automatic virus scan,” assuring you that it has detected dozens of pieces of malware in your computer? If so, welcome to the world of scareware.
What is scareware? Everything you need to know
Scareware is not malware, spyware, or a virus, but it is potentially an open door to all of them. It is a technique used by cybercriminals and black hat hackers to trick you into taking an action you should not take.
By creating sophisticated pop-ups, notifications, well-crafted emails and messages, and even simulating antivirus operations, criminals try to trick users into clicking a link, buying a fake antivirus, or downloading malware. In this way, it is similar to phishing; both approaches use social engineering that preys on human behavior.
The main goal of scareware is to infuse fear into users by falsely claiming that a computer, phone, or device is infected with malware, or stating that a device is locked, slow-downed, or damaged. Those who fall for this scam click on the pop-up and open the door for real malware and harm to come into their lives.
Clicking on a link or downloading a file from fake scareware messages can undoubtedly have serious consequences — these range from ransomware to identity or financial theft, browser hijackers, adware, and more. Scareware can be integrated into malicious sites that hackers design to rank high in organic search results. It can also spread through email, social media, and messaging apps. Criminals may also make scareware phone calls, impersonating security experts.
Why scareware is more harmful than it looks
If you start browsing one day and suddenly encounter a pop-up that appears to tell you that your computer has a virus, you may start to panic. This is a perfectly understandable reaction. It’s also precisely the behavior that scareware attackers are counting on.
Scareware preys on human psychology and attempts to get its victims to stop thinking long enough to drop their defenses. Before they know it, they’ve opened the door for malware to enter their computer.
You may think that scareware is just an irritating pop-up that hassles you to buy software. However, scareware is a lot more than that, for the following reasons:
- A scareware attack is usually just the introduction to bigger and more serious malware threats, such as trojans, keyloggers, remote access trojans (RATs), and backdoors to install ransomware.
- Scareware isn’t a one-trick pony. Scareware on your MacBook could lead to an attack that disables your antivirus and hijacks your browser settings.
- Scareware may attempt to trick you into paying for fake antivirus tools. If you do, it steals your personal details, including your credit card number.
- Attackers may attempt to trick you into calling a fake tech support number. This opens the door to giving a hacker remote access to your computer.
- Your identity could also be stolen, or your device could become encrypted, with the attackers demanding a ransom in return for restored access. The financial damage of these kinds of cyber attacks can be catastrophic.
- Finally, the scareware will change your DNS settings so your web traffic will be routed through their own proxies. This will lead to malware-infected websites where more threats are waiting.
Who created scareware?
Scareware evolved in the early 2000s from malvertising, a form of malware distribution done through online advertising. The culprit behind the first scareware program remains unknown, but the first famous scareware attack came in 2006, when Microsoft and the Washington state attorney general filed a joint lawsuit against the software vendor Secure Computer, alleging that it peddled Spyware Cleaner to Microsoft users that was actually scareware.
By 2009, the trend was already defined and well-established. By 2010, it had affected millions of users. Despite the efficiency of modern pop-up blockers, it is still a popular technique among cybercriminal organizations. And while some scareware can affect Mac and PC users alike, others are developed to work on specific operating systems.
Examples of scareware on Mac
In 2010, the Minneapolis Star Tribune newspaper served Best Western ads, which directed readers to malicious sites that ended up infecting their computers with malware. This was one of the first large scareware campaigns to unfold from pop-up ads. Users were told that their devices had been infected, and the scareware then tried to convince them to download an antivirus that cost $49.95. The campaign ended up with the attackers’ arrest, but they still managed to make off with $250,000 by scaring users. This type of campaign, integrated into websites, can affect both PC and Mac users.
The first scareware specifically coded to target Mac users, and still famous today, is the Mac Defender case. Also known as Mac Protector, Mac Shield, and Mac Security, this scam first appeared in early 2011, when Mac users were redirected to fake websites that informed them that their computers were infected with a virus, offering an antivirus as the solution.
The main goal of Mac Defender was not to sell a fake antivirus but to obtain credit card information from users to use fraudulently. The extent of the campaign was so big that in 2011, Apple released a security software update to find and remove Mac Defender from computers.
Another infamous Mac-specific scareware was ChronoPay. In 2009, ChronoPay, a Russian online payment processor, targeted Mac users with scareware to trick them into buying fake antivirus software. Investigations later revealed that ChronoPay was a significant player in the fake antivirus and scareware global market.
How scareware works
As previously mentioned, scareware works by instilling fear into users by presenting an urgent and grave problem and later “selling” the solution. There are several techniques for scareware. These include ad pop-ups, push notifications, and phishing.
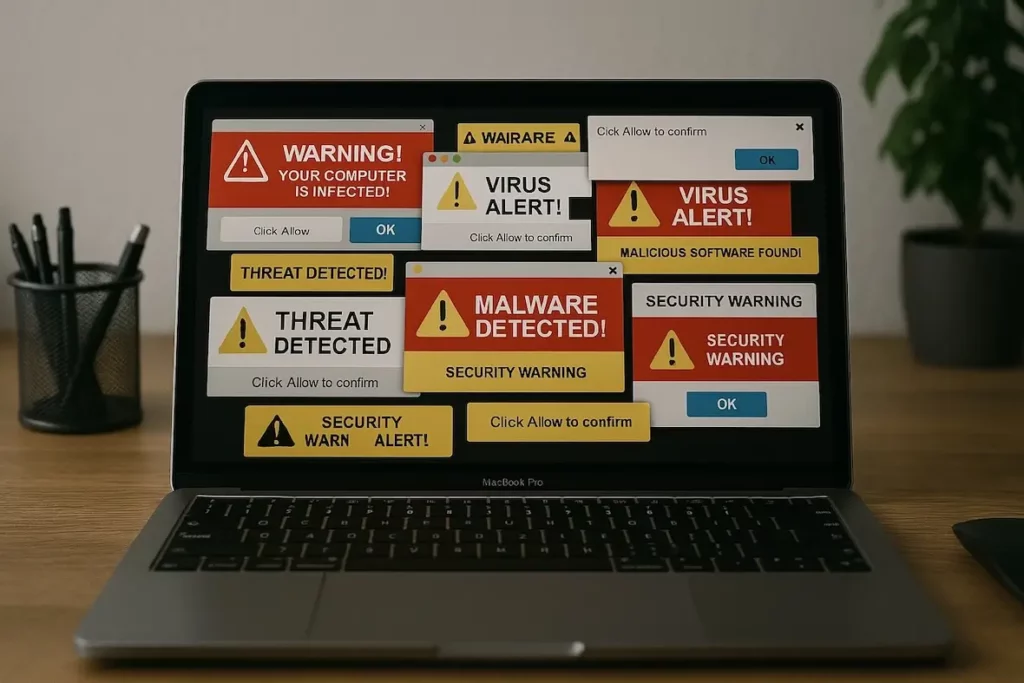
Pop-up scareware notifications usually look like trusted antivirus software that you have installed on your computer. This makes it difficult for users to discern whether they are getting a notification from their security solution or something foreign. Plus, the close button in these pop-up notifications is usually well hidden.
Scareware push notifications mimic trusted sources, such as Google, but do not appear to have originated from a website. Hackers can code these notifications to look like they are scanning for viruses when they are not, often using countdowns as an additional method of creating a sense of urgency.
Finally, scareware can reach you through emails or messages on social media. These direct messages may try to convince you that your computer has malware, viruses, or other serious threats. They may also be drafted to direct you to a site that triggers scareware notifications or pop-ups.
How does scareware get on your computer?
After finally removing scareware from your computer, you may find yourself wondering how it got onto your device in the first place. Here is a list of common methods that hackers and cybercriminals use to infect your MacBook:
- The most common method is sending emails with phishing links. These emails are designed to look realistic enough to convince people to click on them. The links can lead to malware downloads or to websites where malware and scareware pop-ups await.
- In addition to phishing links, hackers send emails with infected attachments. These attachments will have authentic-sounding names such as payslip, invoice, contract, etc. Once the attachment is opened, however, the scareware will download itself and start infecting your MacBook.
- It’s not just suspicious websites you need to worry about. Legitimate websites can also be compromised. Ad networks can be sent infected advertising, known as malvertising. No website is immune to this — even The New York Times and CNN have been known to become targets. This is why installing an ad blocker is essential.
- Free software is also another favourite method of delivery for scareware. The usual suspects include free PDF editors or YouTube video converters. These may contain a browser hijacker, scareware, or another more serious malware, such as a trojan.
- If you’re on the lookout for tech support, you may encounter a Google-sponsored ad and decide to phone them. In some cases, that tech support website is fake. The attackers, posing as tech support, will ask for remote access to your computer. From there, they can steal your personal information or install malware.
- Finally, hackers and cybercriminals will take advantage of your trust in notifications on your MacBook. This could include installing system updates or updating software. By the time you realize that the alert is a fake, it’s too late.
The warning signs of scareware
As the name suggests, scareware is designed to scare you, so a computer issue that gets your blood pressure up, your heart rate beating faster, and your anxiety shooting through the roof could be scareware. This is done in several strategic ways.
It implies a sense of urgency
If you get a pop-up box on your screen telling you that you must take immediate action, stop for a moment. Any reputable piece of software is not going to demand action within the next minute or 2. The sense of urgency you’re feeling could be a form of social engineering trying to convince you to make a mistake.
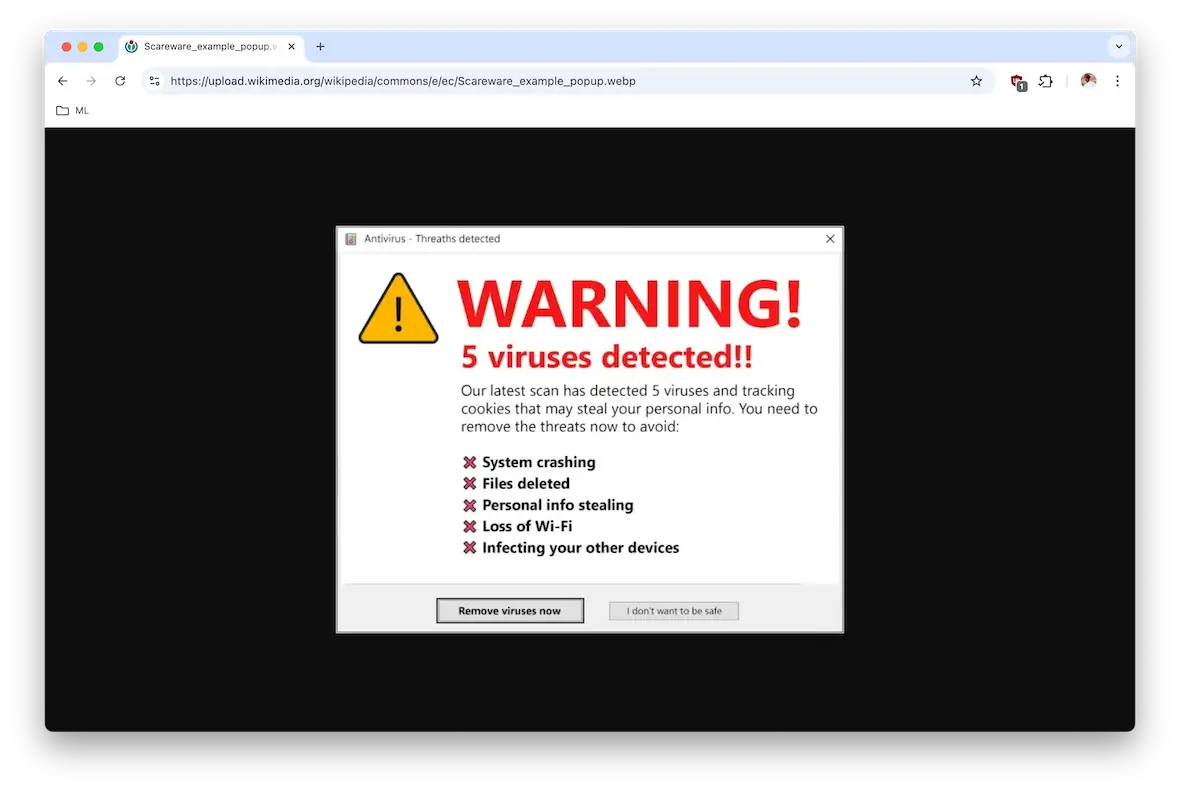
It’s using language designed to scare
If a pop-up tells you “your computer is at risk!” or that your device has a “critical virus alert!” and follows up with a command to take immediate action, be wary. There may be bold text, flashing lights — anything to get you to panic.
It tries to urge you to buy something
If a pop-up informs you of an issue and quickly follows up by telling you to click a link and purchase the solution to all your problems, that is definitely a huge red flag. That “solution” is likely a malware-infected link and should never be clicked.
It’s badly designed, with typos and terrible grammar
If the pop-up or the site it leads to has bad grammar and typos, all may not be as it seems. Professional, reputable companies have teams of copywriters checking everything, as they know that typos and poor grammar can damage their reputation.
How to remove scareware pop-ups on your Mac or iPhone
You can do several things to stop this threat and keep your Mac, iPhone, or iPad safe.
These include:
- Keep your device updated.
- If you get a pop-up, close the browser window. Do not click on the pop-up’s close button.
- Avoid browsing sites that look suspicious.
- Don’t click links from sources you do not know, and don’t download files from unverified sites or people.
- Keep your browser updated and set to a high level of privacy and security.
- Use a trusted pop-up blocker.
- Use trusted search engines and browsers only.
- Make sure your firewall is active and updated.
- Run regular antimalware scans.
How to get rid of scareware on your Mac
Although you can remove any unwanted app from your Mac manually simply by trashing it, scareware can affect your computer configuration. It can also create temporary and registry files and is good at hiding.

Moonlock has a Malware Scanner feature, powered by the expertise of real Mac malware investigators. It can detect and remove scareware from your computer.
To remove scareware with Moonlock:
- Start your free trial and download Moonlock.
- Open the app.
- Choose Malware Scanner from the sidebar.
- If this is your first time using Moonlock, select Configure in the dropdown menu to define what the app should scan for.
- When everything is ready, press Scan.
- If any malware or viruses were found, go to Quarantine, check all checkboxes, and click Remove.

Moonlock can also give you more details and information on the type of malware it found during the scan. To get this information, click the ‘i’ icon next to the malicious item placed in Quarantine. It also has continuous malware monitoring, so you don’t have to search for threats manually. Enabling it is extremely easy.
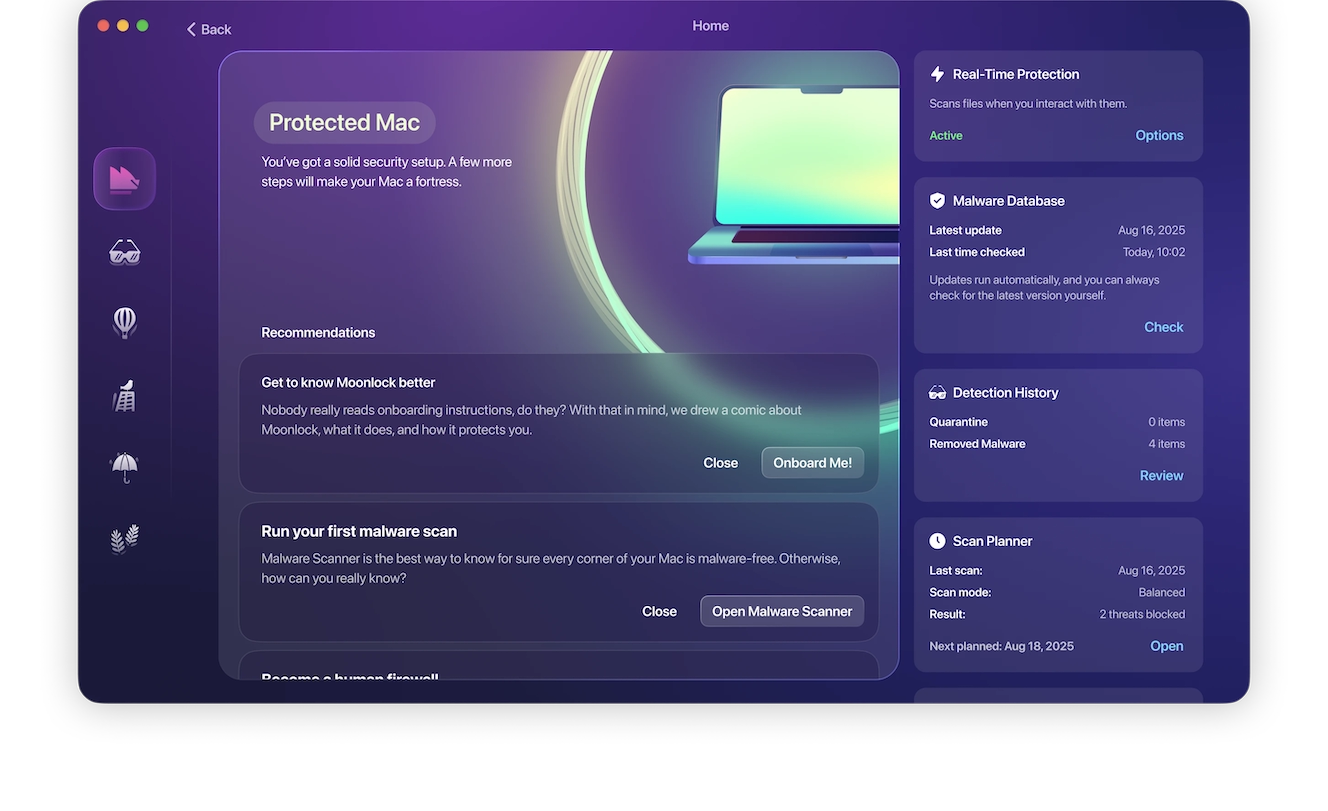
- Open Moonlock.
- Click Explore.
- Find Real-Time Protection in the top right corner and check if it’s active.
- If not, click Options.
- In the window, check the box next to “Turn on real-time protection.”
Moonlock will now run in the background and monitor malware activity, alerting you if any action is necessary.
How to remove scareware from your iPhone
There are several processes you can utilize to remove scareware from your iPhone. The first step you will want to take is to delete any unwanted apps from the App Library.
To delete unwanted apps on your iPhone:
- Go to the App Library and tap the search field to open the list.
- Search for any app that is suspicious or that you did not intend to download.
- Touch and hold the questionable app icon, then tap on the Delete App (trash can icon).
- Tap Delete again to confirm.
You will now want to restart your iPhone and update your system’s software. Additionally, you should clear your browser data.
To clear data in Safari:
- Open Settings.
- Select Safari.
- Select Clear History and Website Data.
- Tap Clear History and Data.
If you still have a problem after doing all this, you can restore your phone to a previous backup.
To restore a previous backup of your iPhone:
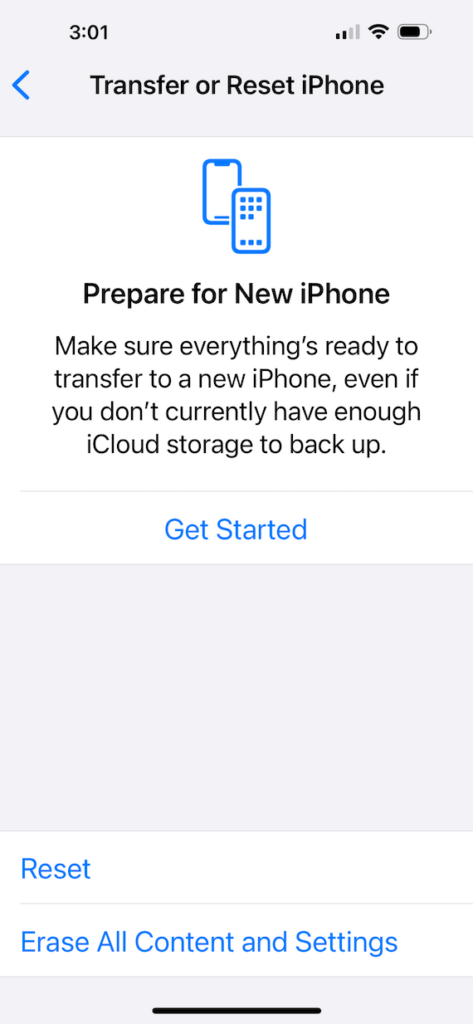
- Go to Settings and tap General.
- Scroll to the bottom and select Transfer or Reset iPhone.
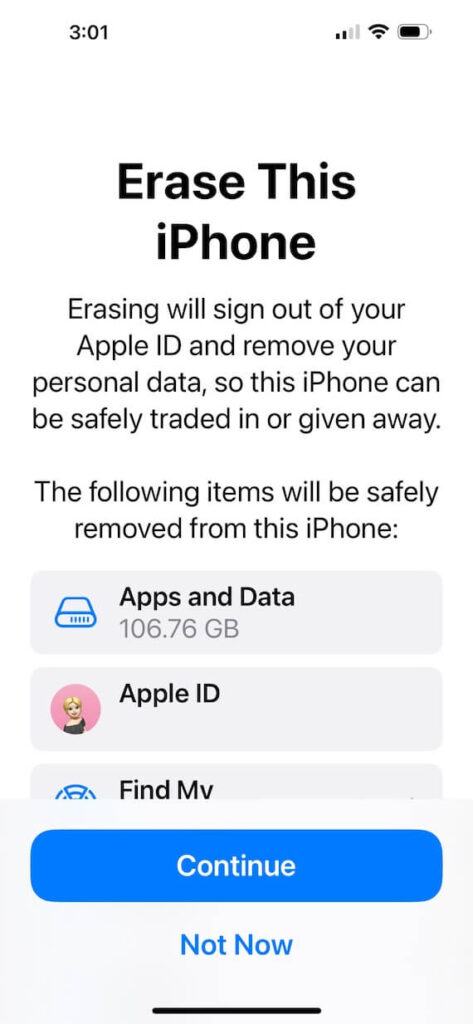
- Choose Erase All Content and Settings.
- Select Erase Now or Backup Then Erase.
- When the Apps & Data screen appears, select Restore from iCloud Backup.
- Sign in to iCloud and select the backup you’d like to use.
What to do if you fall victim to scareware
It’s hard to stay calm if you are a victim of scareware, so it may sound rather disingenuous of us to tell you to stay calm. But really, this is critical. Try to keep a clear head, take a few deep breaths, and do the following.
Take screenshots of everything
The first step is to collect as much evidence as possible for the authorities to investigate. Take screenshots of all the scareware and all the websites you were sent to. Compile a list of the links you clicked on. Do this quickly because you’ll want to move to the next step as soon as possible.
Turn off your computer
The next step is to turn off your computer and keep it off. If you clicked on a link or provided sensitive information, your device may now be infected with malware. Turning off your computer will help prevent it from potentially spreading. You don’t want your friends going through the same experience. It may also be advantageous to disconnect your internet router.
Contact the relevant people
If you have given the scammers the login details for a website, inform that website’s customer support team immediately. Use a different device than your own to do this. If you have paid for something on the infected website, have the payment card frozen and contact your bank’s security department.
Contact your friends and family
The next step is to inform your friends and family that you may be a victim of malware. If they receive an online message purportedly from you, they should be extremely wary and should perhaps contact you via other means to double-check.
Wipe and reformat your infected Mac
Many pieces of malware are quite sophisticated at burrowing themselves into your operating system. It may be wise to wipe and reformat your device to ensure that all traces of malware are truly gone. Then, use Moonlock’s protection to make sure.
How is scareware different from other malware?
In a nutshell, scareware capitalizes on the natural human tendency to react irrationally when faced with a potential danger. In these situations, sound reasoning may be temporarily paused as the brain frantically tries to assess the risk and figure out how to resolve it. This can lead to bad decision-making.
With other types of malware, potential victims may stop for a moment, think about the situation, and come to the conclusion that things are not on the up and up. Scareware tries to bypass that process by rushing the person into making a snap decision. More often than not, that snap decision will be the wrong one.
Scareware vs. ransomware
While scareware works on the principle of hitting a person suddenly and confusing them, ransomware is fiendishly straightforward.
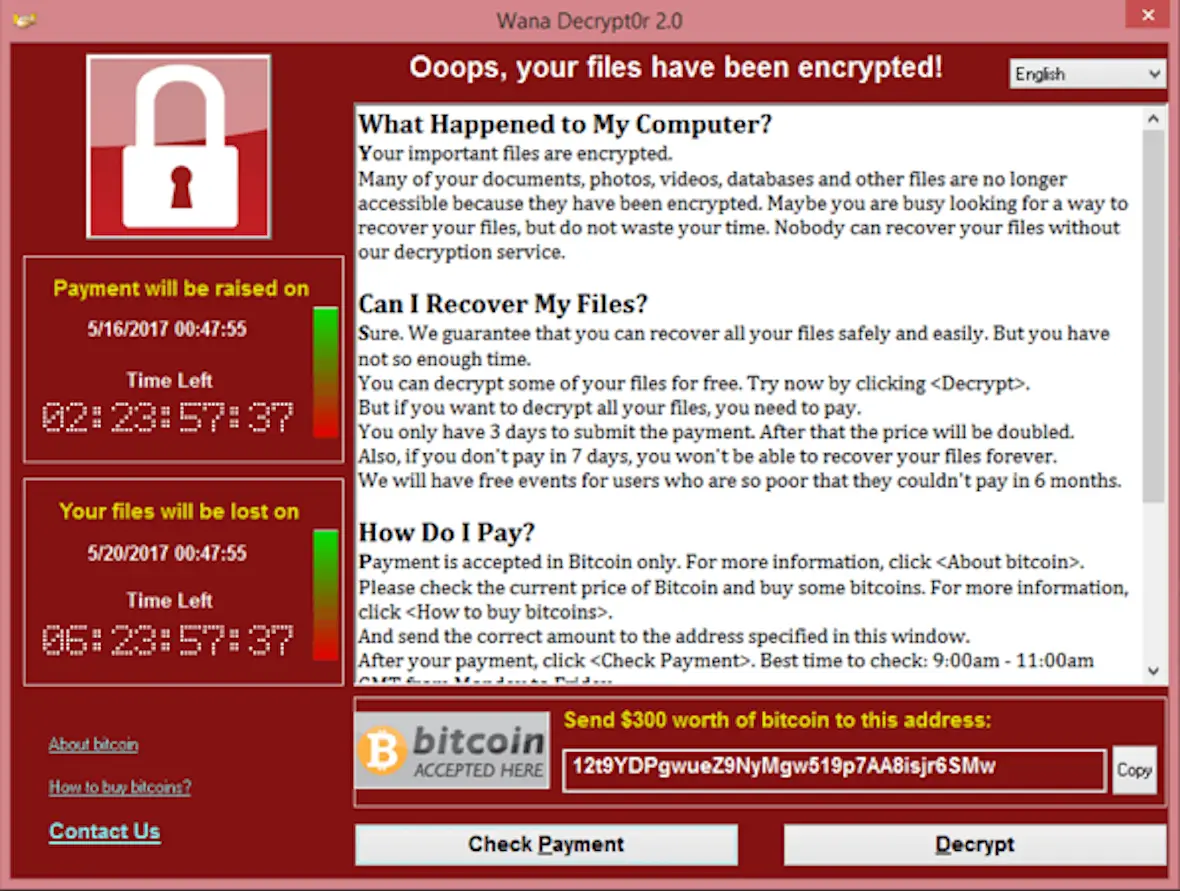
Ransomware is when a computer or server is taken over and locked down by a hacker. The hacker then demands payment — usually in the form of Bitcoin — before handing over the code to unlock the affected files. Sometimes, they don’t even bother to hand over the code once they’ve been paid.
Ransomware can take days to resolve. The victim first has to agree to pay the ransom payment, the Bitcoin transfer has to take place, and they then have to wait and hope that the hacker will provide the key.
Ransomware gives the victim plenty of time to think and assess their options. Scareware, on the other hand, makes you feel that your digital world is falling down all around you and an immediate decision must be made.
Scareware vs. adware
Adware is a rather more subtle form of malware. While scareware is a sledgehammer approach, adware is more like someone gently whispering into your ear, trying to convince you to click on that enticing-looking ad.
Adware serves up unwanted ads on your screen. It may also redirect you to unscrupulous search engines or malware-infected websites where even more advertising will be thrown at you.
How to prevent scareware from infecting your device
Your best defense against scareware is to prevent it from ever happening to you in the first place. The following is a list of tips on how to prevent malware threats from infecting your device.
Run regular scans with Moonlock
The most important thing you can do is run regular malware scans. The most powerful and efficient solution in this area is Moonlock with its Scan Planner. This powerful malware detection tool will detect any malware on your MacBook and remove it immediately. You can sign up for a free trial and test it for yourself.
To set up regular automatic scans in Moonlock:
- Open Moonlock and click Explore.
- Find Scan Planner on the right of the screen.
- Click Plan a Scan and configure everything you need: type, frequency, and time of your scans.
- Hit the Save button.
Now, you’ll have round-the-clock protection from hidden malware without lifting a finger.
Don’t click any links from unknown people
As we said, one popular method that hackers and cybercriminals use is to send emails with phishing links. Therefore, if you receive a link from someone you don’t know, do not click it. The same goes for email attachments.
Don’t visit unsecured websites
Check the address bar of your web browser. The first part of a secure URL is HTTPS, a security certificate showing that the website is secure. Although this is not a total guarantee that a site is safe, it goes a long way.
Your browser will usually block sites that don’t use HTTPS, but you can override this setting, which we don’t recommend. If you happen to visit a website that does not have HTTPS in the URL, leave the site immediately or risk the consequences.
Don’t install free software
Scareware pop-ups and other malware often originate from free software that comes bundled with hidden threats. You can stop this from happening by refusing to install software from outside of the Mac App Store or software from unrecognized developers. And do not disable Gatekeeper on your Mac.
Avoid unknown USB sticks or removable drives
If you find a USB flash drive in the street, leave it where it is. A classic trick employed by hackers is to place malware on a USB stick and leave it lying around for someone to find. The same also goes for removable hard drives. If you don’t know what’s on it, don’t plug it into your Mac.
Install an ad blocker
The best way to ensure that ads don’t appear on your screen is to install an ad blocker. A strong solution is ClearVPN, which also has an ad blocker installed.
Keep in mind that one unfortunate side effect of ad blockers is that some websites don’t work properly if ads are blocked. You’ll have to weigh the risks and decide whether to disable the ad blocker for those websites.
Scareware is one of the oldest tricks in the hacker’s book, and it can be more convincing than you might think. Overall, always keep updates set to automatic, avoid interacting with strange messages, websites, or links, and never download unverified files or attachments. And if you ever see a scary pop-up or notification message, think twice before clicking it.






