The threats just keep coming. It seems like every time you turn around, there is another type of cybersecurity danger to worry about. But fret not; we’ve got you covered.
Just as the title suggests, we are talking about a type of malware with the ability to hijack and take control of your internet browser. Keep reading to find out what a browser hijacker is, explore real examples, and understand how they work and spread.
What is a browser hijacker?
So, what would be an accurate browser hijacker definition? Simply put, it’s when malware takes over your internet browser.
A browser hijacker aims to collect as much information about you as possible, steal your personal data, and redirect you to websites controlled by the hacker or cybercriminal. The ultimate aim of a browser hijacker is to make as much money from you as possible before it is detected and removed. A classic example of search engine hijacking is the Yahoo redirect virus, which will send you to Yahoo.com, where the attacker will get money from your searches.
Some people may consider a browser hijacker nothing more than an irritant. But it is much more than that and should not be ignored. In fact, it should be removed from your Mac as soon as possible. But you shouldn’t go poking around your browser hoping to find the hijacker. You need a dedicated protection tool, like Moonlock, to do it for you.
Moonlock can also protect your Mac from becoming infected with a browser hijack by warning you if you have downloaded a malicious browser extension or email attachment. The built-in Security Advisor can also help you with safety tips when it comes to browsing the internet.
How a browser hijacker works
Compared to other malware, such as trojans and RATS (remote access trojans), the effects of a browser hijacker are mild. It is also easier to remove than other malware. However, as we’ve said, you still shouldn’t underestimate a browser hijacker.
Since the attacker’s ultimate goal is to make money, they accomplish this by changing your browser settings and DNS settings to redirect you to their preferred search engine. They will also send you to websites under their control that are infected with other malware. Quite often, this malware will be much more dangerous.
A browser hijacker will also often change your browser security settings by either downgrading them or disabling them entirely. It may also install an app on your MacBook or install a malicious extension in your browser.
Once they’ve gotten hold of your browser, attackers will monitor all of your browsing activity. They will steal your personal data, such as your name, your date of birth, and your credit card number.
They will also attempt to capture your login details for as many accounts as possible, such as your email platform, social media, and online banking sites.
Finally, you can expect to encounter lots of other malware, such as fake virus notifications.
Can browser hijackers steal passwords or personal information?
One reason why browser hijacker software shouldn’t be considered a mere nuisance is that it can also steal passwords and personal information. It can accomplish this by the following methods:
- Some browser hijacker malware will come with keyloggers. These will capture all of your keystrokes, which can give the attacker your login details, emails you’ve written, and chat messages. These messages will likely contain personal information that can be used against you.
- A browser hijacker virus can also capture what you enter into an online form, such as login details for your email, social media, and bank accounts.
- One factor that many people don’t think about is that a browser hijacker can also steal your browser cookies. This means that when you log in to a website, the malware steals the cookie, meaning it can access the website without even needing your password.
- We’ve previously said that a browser hijacker can redirect you to an attacker’s webpage by changing your DNS settings. This means that you could be directed to a fake login page that looks like the real thing. Once you enter your login details, the attacker has them.
- One other method to steal your passwords and personal information is by taking advantage of the browser’s autofill feature. This usually stores your passwords, credit card numbers, addresses, and phone numbers.
Symptoms of browser hijacking
Thankfully, armed with our list of browser hijacker symptoms, you can detect an infection early and clean it out. Some of the most common symptoms of browser hijacking include the following.
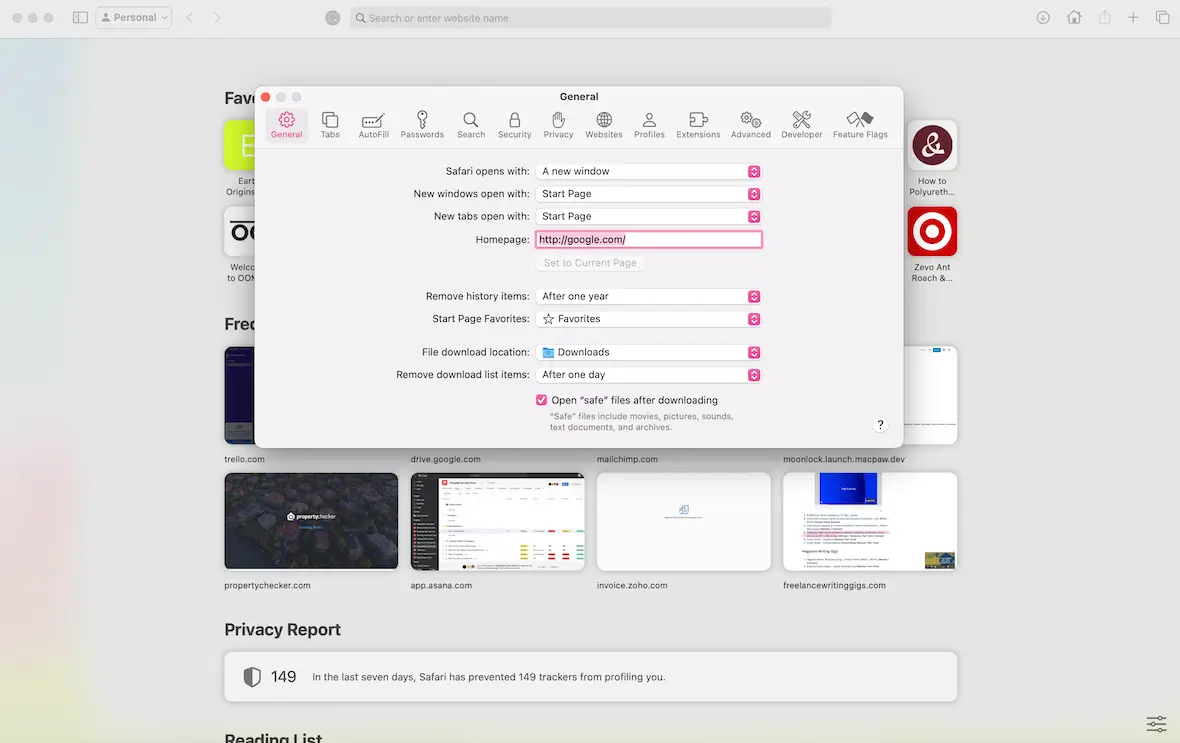
Your default homepage has been changed
If you notice your default browser homepage has changed and you didn’t change it, that is a strong sign that you may be dealing with a hijacked browser.
Pop-ups!
If you suddenly start seeing tons of pop-ups and advertisements every time you try to surf the web, don’t ignore it. This, too, is a big red flag that someone may have made changes to your software.
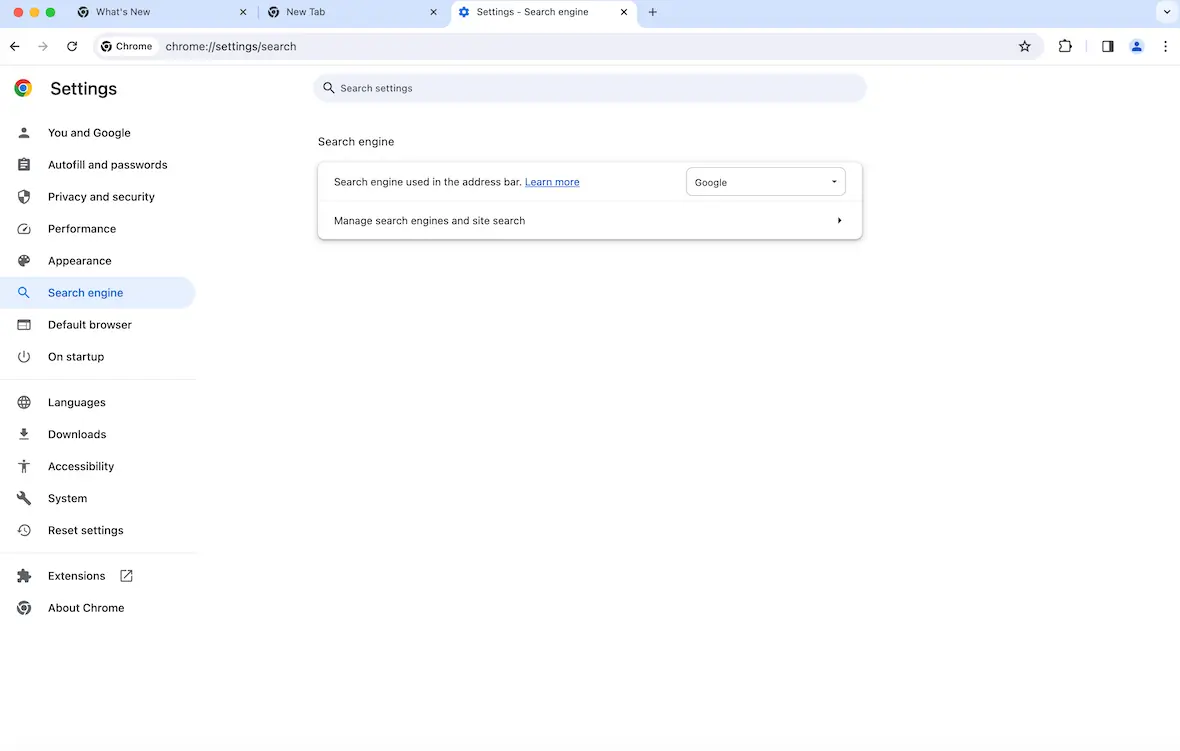
Your search engine is altered
You have your choice of search engine when using various browsers. But if yours has been changed from your usual default search engine, it could indicate foul play.
Constant redirects
If you attempt to visit websites only end up on other pages you didn’t intend to visit, proceed with caution. You could be dealing with an infected browser.
New toolbars or extensions
Have you found add-on toolbars and extensions that you don’t remember installing? There is a good chance that your browser has been hijacked and someone has changed these settings.
Performance issues
Browser slowdown isn’t always normal. If it suddenly takes much longer than usual to load pages, it could be because your web browser has been compromised by a browser hijacker.
Your sensitive/personal information is leaked
In some cases, the first sign of a problem is discovering that your sensitive information or data has been leaked online. When that happens, it’s time to check for malware. Sometimes, these programs steal personal information and send it back to a central server.
Examples of browser hijackers
Browser hijackers are nothing new. There are dozens of variants out there with silly names, including a few you might recognize.
Ask toolbar
Many victims who downloaded freeware (free software) got an added surprise: the Ask toolbar, which pops up with annoying ads and redirects to sites you don’t wish to visit.
Browser hijackers are nothing new. There are dozens of variants out there with silly names, including a few you might recognize.
Trovi
Trovi is another example of Safari browser hijacking, which redirects searches to trovi.com. The attackers benefit from this by receiving advertising revenue for every search that is made.
Attackers may also install additional software such as Search Protect, which will automatically reinstall the hijacker if you attempt to remove it.
Search Marquis
Then there is Search Marquis. This one is slightly different in how the attackers receive ad revenue from searches. Their search engine hijack will redirect you through their own network, eventually taking you to Bing. Then, when you search on Bing, the attacker will receive money.
Search Baron
The next bad boy in the browser hijacker category is Search Baron. Like Search Marquis, Search Baron will redirect your online searches through its own network of malware-infected sites and eventually place you on Bing. Then, as before, they earn money from any searches you make.
We should stress that the ad revenue program on Bing is legitimate and is used by many honest people. But, like many things in life, hackers and cybercriminals take full advantage of it and exploit it.
QSearch
Another browser hijacker that takes advantage of Bing is QSearch. This one is no different than any other browser hijacker. It will redirect your searches to make money, as well as steal your personal data. You can also expect to see an increase in the number of ads you see. Unfortunately, this one is quite difficult to remove.
Some other browser hijackers to be aware of include Babylon Toolbar, Conduit Search or Search Protect, SourceForge Installer, OneWebSearch, Snap.do, and Sweet Page.
How to delete a browser hijacker from a Mac

While removing a browser hijacker can appear to work on the surface, doing it manually risks leaving the same vulnerability open to future exploits. Your best option is to use Moonlock to make the process of cleaning your device easier, quicker, and more efficient.
To scan and clean your Mac, follow these steps:
- Sign up for your free trial and download Moonlock.
- Open the app.
- Click on Malware Scanner in the left sidebar.
- From the drop-down menu, choose between Quick, Balanced, or Deep scan.
- Click the Scan button.

If Moonlock finds anything suspicious lurking in your device, it’ll immediately quarantine it to keep it separate from the rest of your files. You can then opt to either inspect the suspicious file or have Moonlock delete it for you.
Not only is browser hijacking annoying, but it can also leave you vulnerable to other online threats and result in identity theft or fraud. Use common sense and follow our cybersecurity best practices to keep you and your data safe.